We protect the site from attacks on the example of HabraHabra
Early in the morning, Habr “rolled out” his new update, and with a clear conscience, I am getting this article from drafts.
Yesterday I had an epic fail and this topic partially, including the line about the update above, got into public for a couple of seconds. For these seconds, the topic managed to plus a few people.
Once again, now in public, I apologize to the administration!
Advice to the rest - NEVER store information like this in drafts.
Recently, on the Internet, you can find a lot of manuals for "Beginner hackers", which describe in detail all the basic methods of hacking sites. Do you think web developers are smarter from this and have taken all possible methods to protect? I do not think so.
')
In this article, I want to once again tell the developers about how to break websites, and so that you are not bored, I will simultaneously break Habr and describe in detail how I did it. We will look at such interesting things as “Active XSS in profile”, “Infinite zeroing of karma”, “Publishing topics with the Sandbox icon”, “CSRF via Flash and a hole in Internet Explorer 6” and much more.
All vulnerabilities have already been fixed. Or almost everything. Therefore, if you find another hole, write to support@habrahabr.ru - the myth that no one reads this mail is just a myth.
Instead of intro
I would like here, at the very beginning, to tell some very important things in my opinion.
First of all, who are the hackers and what do they need (let's not call “hackers” the word “hackers” because it’s wrong and hackers don’t break anyone) . I do not want to offend anyone, but in most cases they are teenagers aged 15-17, whose main goal is not to get much money, how much to just hack the system and get a feeling of some kind of self-satisfaction.
Often, the developer thinks that breaking his site to anyone will never enter his head, because there is nothing interesting there. But hackers of the type just described do not need this, so they easily find vulnerability and make a deface (as a rule, placing their message instead of the main page, the Black Lord already did this a couple of times with HabraHabr :-) . Sometimes they cannot even find a simple vulnerability, so they use ready-made exploits (they are also called “Script Kiddies”) . So, I can already give you some tips:
- Do not be lazy to filter the input data [this will be discussed further] , even if your site is “not needed by anyone”.
- It’s sometimes dangerous to install the latest software versions, but you shouldn’t even sit on the old ones, because anyone who knows how to use the search and download special programs “for hacking websites” can hack you.
Now let's imagine that our “character” grew up and started looking for work. What will he most likely do? That's right, burglary for money.
This type is no longer a particular danger for sites where in fact there is nothing interesting. Now he works mainly on an “order”, often in small groups.
In general, the advice is the same, only now you should spend a little on a person who will check your site for vulnerabilities for money and inform you about the results.
By the way, such “Experts” are, as a rule, the same hacker who retired and now earns his living in a completely peaceful way.
XSS or Cross Site Scripting
Very often used type of vulnerabilities. To use it, a hacker only needs to have a basic knowledge of HTML and JavaScript, which is why it is used by all types of “characters” described earlier. It should be noted that in this case no one is going to hack the server, and the attack, in fact, is aimed at the users of the vulnerable site.
The key error of the web developer in this case is insufficient filtering of data received from users.
XSS is divided into two main groups: “Active XSS”, which lies somewhere on the site and waits for its victim, as well as “Passive XSS”, which the burglar sends to the victim using social engineering.
Let's see how we can “rejoice” Habr. British scientists have found that 95% of hackers call themselves
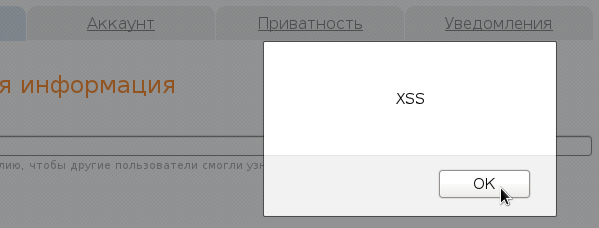
" onmouseover="alert('XSS')" style=" Go to the profile settings and enter this phrase in the "Real Name" field. Now click “Save” and refresh the page. We find the mouse and try to drive it near an empty field for some reason - a window appeared? Congratulations, we found a vulnerability!
Such vulnerabilities often crawl out when the system does not filter or filters partially incoming information from the user. If you are writing in PHP, then it has a very good
htmlspecialchars function that allows you to solve the problem almost completely.The meaning is that you do not need to give the user the opportunity to use all the tags, you also need to carefully check whether he has inserted something into the allowed tag and if he has gone out of the field, as in the example above.
I did not manage to find an example of passive XSS on Habré, therefore I will describe its essence in words.
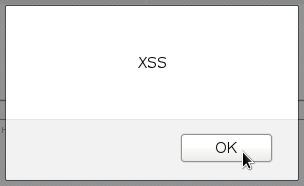
The most frequent place to find them is search. Try to “search” on your site for something like
<script>alert(1)</script> or
"> <script>alert(1)</script> <!-- If a window with the number “1” has jumped out, then your website is subject to such attacks. Now it is enough for a hacker to send you a special link, clicking on which you will give him full access to your account. The meaning is the same as in Active XSS, only now the hacker needs to feed you a link!
Checking other received information
You need to filter not only HTML tags and quotes, but also other information received from the user. It is especially important to follow the logic and never trust the user! You don’t need to go far for an example - the cherished dream of any troll on Habré, “Infinitely nullable karma”, was quite realizable to this day :-)
If you have already reset karma and want to do it again, then you need to use your browser’s “developer tools” to simply make the hidden form visible and click “Zero”!
For example, I created a “virtualchik”, merged his karma, nullified, merged again, nullified again, and so on ...


For the sake of fairness, it is worth noting that my dear virtual fellow was transferred to this in the “Read-Only” mode. It is good that the account itself has not lost.
Let me give you another very interesting example. When we publish a new article or edit an old one, replacing the “topic_type” field with “sandbox” allows you to get the “From the sandbox” plate.

Why do you need it? Well, I do not know, let's say, such topics are more often plus ...
What can I advise in this case? Well, of course, control what users send you! If you are sent a request to reset the karma, then check if the user has not reset it before, and if the user tries to publish the topic “from the sandbox”, then check if it really is from there.
SQL injections
Such vulnerabilities are very common in novice web developers. I couldn’t find one on Habré, but one habro-user claimed to me in PM that it exists. I repeated his experiment, but it didn't work out - they probably closed it.
For protection, you need to filter quotes and other special characters that may violate the logic of your request. Also, when you have a number, be sure to clearly bring it to a number.
CSRF vulnerabilities
If Bubmburum began his conquest of Habr with a super flash drive, then I got into the TOP5 users overnight thanks to the CSRF vulnerability I found last year.
You can read my topic here . Now I am writing this because I recently found another one the same and she could invite my virtualchik to Habr with the help of users who used Internet Explorer 6. It should be noted that there were not many of those.
To protect you, you need to insert into each form or an important request a special csrf-token that the attacker should not know. Some frameworks insert this token into your forms automatically.
Related Links
Wikipedia - XSS , SQL injection , CSRF .
Another interesting article that describes all the main vulnerabilities together.
Source: https://habr.com/ru/post/139940/
All Articles