NeoQUEST - summing up
 As planned, on March 14, 2012, we completed NeoQUEST-2012. Total points are calculated, the winners are named; In the next few days, we will definitely contact them and determine when and where they will receive their honestly deserved prizes (including our main prize, the very MacBookPro, which appeared in the quest).
As planned, on March 14, 2012, we completed NeoQUEST-2012. Total points are calculated, the winners are named; In the next few days, we will definitely contact them and determine when and where they will receive their honestly deserved prizes (including our main prize, the very MacBookPro, which appeared in the quest).Now you can summarize the quest, tell about how we did it and about what difficulties we encountered. And, of course, thank all those who took part both in the quest itself and in its creation and debugging.
Final results
At the date of the official quest closing results, the number of registered participants reached 1,480 people. Much or less - you decide. A separate pleasant moment for us was the fact that many participants registered after the start of the competition; This means that information about the quest spread and interest was not only in the first days.
Prizes were taken by:
- More Smoked Leet Chicken
- BECHED & Andrey1800.
- ki11obyte .
The team More Smoked Leet Chicken not only completed all the tasks, but also did it in the shortest time. They are awarded the main prize of our competition. The participants of BECHED & Andrey1800 and killobyte are awarded prizes for the second and third places of our competition. In addition, all participants who completed the first stages of the quest will receive memorable gifts from us. From the very beginning of the quest, we were amazed at your activity in finding bugs and vulnerabilities, cracking everything hacked and unbreakable. You found such moves, which we had no idea, and enthusiastically understood those areas that we had not encountered before.
')
Passage Notes
Despite the fact that the quest is officially completed, two more weeks of assignments will be available for completion. If you want to try to go through it yourself, then this section is better to skip.
Of course, the described methods of passing tasks are not the only possible ones. How many participants - so many options for passing.
When creating NeoQUEST, we pursued the following goals:
- find a compromise between complexity and time of passage. The quest must be successfully completed not only by teams of experienced professional players, but also by qualified computer security specialists, including advanced students of relevant specialties. The net time for the completion of all tasks, according to our calculations, should have been about 10-12 hours;
- move away from the prevailing web security quest;
- to bring tasks to those situations that we all often face in our professional activities. Quest should not be "art for art's sake";
- cover various aspects of information security: from the protection of SCADA-systems to the elements of steganography and social engineering;
- Combine tasks with a common exciting plot, create a holistic interesting game.
Let's see what came of it. Quest is logically divided into 5 sections:
- Web application security (tasks 1, 2).
// - ! - Cryptography (task 3).
// , ? - Security SCADA-systems (task 4).
// … - Windows security (tasks 5, 6).
// … - Search for information in the container (tasks 7, 8).
// …
Section 1 (tasks 1, 2). Web server:
To complete the tasks in this section, it suffices to be able to identify and use vulnerabilities in web applications, in particular, with SQL-injection. As a web server, the Mint + lampp combination is used, where there are several php-skipts for working with the database and outputting the contents of the tables. Some of them contain errors, for example, a vulnerable query to the database:
$id = str_replace( array('_', ']', '[', ')', '(', '$', 'http://', 'ftp://', '/', '.', '+', '=', 'data', 'base64', 'cmd', 'phpinfo()', 'union', 'select', 'from', 'where', 'UNION', 'SELECT', 'FROM', 'WHERE' ), '', $id ); $id = htmlspecialchars($id); $query = "SELECT * FROM news WHERE id=$id"; The simplest query that solves the problem is as follows:
http: //***/news/comments.php? id = 1 unNion sElect 1, name, pass, 4 fRom users
Also on the server is a pseudo-admin panel, which is visible to only one user and allows you to download an image from the FreeBSD virtual machine. The path to the admin panel can be obtained from the robots.txt file, the contents of which look like this:
User-agent: *
Disallow: /cgi-bin/
Disallow: /administrador/
Section 2 (task 3). Decryption logs. FreeBSD + proxy:
This task required participants to know the cryptographic algorithms RC4 and RSA, the specifics of the choice of encryption parameters and the fundamentals of cryptanalysis.
On a FreeBSD virtual machine, the logs pre-encrypted with the RC4 algorithm are stored on the key, which is subsequently encrypted with RSA. The value of the open exponent for RSA is chosen minimal (equal to 3) so that the messages can be decrypted in a couple of seconds. To obtain the expansion of the number N (the key module in the RSA algorithm), it is necessary to apply the attack using the keyless decryption of the message: http://algolist.manual.ru/defence/attack/rsa.php#RSA1 . Having obtained the key of the symmetric cipher, it is necessary to decrypt the logs with the RC4 algorithm, for example, here: http://www.crypo.com/tools/eng_rc4.php .
The logs contain records of two addresses: reactor and hider.
Section 3 (task 4). SCADA. Default password:
Choosing WinCC as a scud, we are faced with some problems that, however, are not unique to this system. WinCC categorically did not want to take part in NeoQUEST, in particular, completely refused to pick up operating system updates, which left some “very obvious” vulnerabilities open. Some participants used these vulnerabilities and "broke" us scud, but we expected this and were ready for such a development of events.
A scheme is deployed on WinCC (according to the legend, the LNPP reactor), when accessed via the web interface, the necessary flag is issued. Web access has a default password, which can be found in the WinCC documentation.
Section 4th (task 5, 6). Windows:
The tasks in this section covered the security aspects of custom versions of Windows; for their passage, participants need to know how Windows defines access rights to files (in particular, which give owner privileges), how to increase the level of access in the operating system, using, for example, privilege elevation vulnerabilities. To distribute the image of virtual machines (800 meters!), It was decided to use a p2p network - torrents, so that the players were more comfortable, and we could maintain a normal speed in any conditions. In the first part, you need to open files from a folder that only system administrators have access to. It was planned that for this it is necessary to launch an exploit of privilege escalation, but there is another way (much easier) - to boot from the LiveCD or connect a virtual disk to another virtual machine. We tried in every way to complicate the second way (from the LiveCD) and push the participants to the first (with the exploit). To do this, disable the built-in administrator account; created an “Experienced User” for which the privilege elevation exploit is widely known; they made an encrypted TrueCrypt partition, removed it out of sight; have it be automatically mounted only when logged in as administrator; and even the source with the exploit (with some errors, of course, but it still significantly simplified the task) was thrown on the desktop.
After obtaining administrator rights, you need to play a little more with the set file permissions to get access to the container.
Section 5 (task 7, 8). Container Parsing:
For the passage of these tasks, you need to subassemble a little bit, and slightly touch on social engineering, and just logically speculate. The resulting flag produces an exe file that is hidden in the container. The figure shows the scheme of the container:
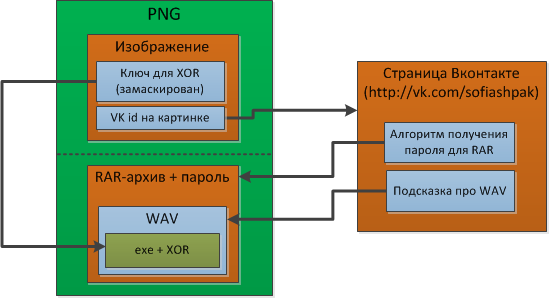
Inside the directory on the encrypted section is a PNG file that contains the user id from vk.com. On this page are a few tips. An archive is added to the end of the PNG, and if you change the file extension from PNG to RAR, it will open as an archive. The data is archived with a password, the algorithm for obtaining which is specified in the status of the user on the VK page. Inside the archive is a file that looks like a WAV file (you can even listen to it), but in fact, it is a clogged exe with a WAV header (a hint about this, too, in VK). The key for xor is in a PNG image in disguised form. The executable file accepts a key at the input and issues the last flag.
Organizational difficulties that could have been avoided
For our team, this was the first experience of organizing such an event, and now, based on the results of the work done, we can say what things had to be done differently. The main conclusions will probably be the following:
- No web-hosting (or time-tested). When we started developing NeoQUEST-2012, we decided that the registration form should be hung up on some hosting. They thought that there should be no problems with a simple website. This is where we made a mistake. The main overlays were connected with this problem. Hosting could not resist even a simple site registration. Failures he gave constantly, and when trying to quickly understand the problem, we received an endless bureaucratic chain of calls and approvals from various people on the part of the hoster, who did not want to take on any additional responsibility. "Only the administrator can restart the server, but it will not be until Monday." No, the company can also be understood, we are not their only clients, they still solve problems. It’s just that in situations when the result is of high quality and on time, it’s better to remember the ancient rule: “if you want to do something well, do it yourself”.
- You need a very careful approach to renting servers. Server rental has its pros and cons. Our site does not allow getting round-the-clock physical access to servers, so we decided to rent the server on the side. The advantages of such a solution seemed obvious - we do not depend on the difficulties that may suddenly arise at the main site (power outages at the weekend, for example) and we don’t have to be on duty around this server around the clock. But no, and here we were waited by unexpected surprises. For example, a sudden decision by a server vendor to reconfigure a network that was never reported to us. The conclusion is the same as in the previous paragraph.
Throughout the registration period, we carefully monitored the comments and comments made here on Habré and on other platforms, and tried to promptly correct the jambs. Many thanks to all who informed us about them.
Conclusions and thanks
Hack quests are rather a kind of recreation and entertainment for initiates. And, despite the stated loud goals (and ominous secret goals that were attributed to us by some commentators), for the whole of our NeoQUEST team first of all served as an opportunity to create an interesting hacker game. We hope that during the passage of the quest you received no less pleasure than we did when it was prepared. As we have already said, this was the first experience of such work for our company: the experience is unusual, useful and exciting, and we are not going to stop there.
On behalf of our company, we sincerely thank:
- Danila and Boson, who have devoted a large part of their time to creating and supporting the project;
- everyone who participated in the filming of our videos;
- our friends and colleagues on thematic network resources that were not indifferent to the fate of the quest and who (sometimes quite unexpectedly for us!) told about our quest on the Web;
- all responded here, on Habré, and on other resources, and to everyone who wrote us about errors and miscalculations in support - this helped us catch large shoals in time (collapse of the registration form) and promptly retouch small ones (such as a countdown timer). belt, or invalid characters in the city input field, etc.)
- and, of course, all participants and prize winners for being interested in NeoQUEST and not taking your time to solve our mysteries, for your perseverance and activity.
We have worked together nicely and invite everyone to further cooperation!
Thank you very much again and see you at the next NeoQUEST!
Source: https://habr.com/ru/post/139818/
All Articles