Congratulations! We are all under the hood
A few words for the introduction ...
First I want to say hello to everyone. Hello, dear readers Habrahabr! Hello everyone from Belarus. This post has already been published earlier, in my blog, but because of the dislike of PS Yandex and others to google sites, it was completely out of the search, all 200 pages, but not about that now. I decided to publish it here, already in my favorite habre.
There is no more silence, knowing that each of us is under close supervision. Why, there is observation, under total control, as in Soviet times, but then no one hid that.
My next post will be devoted to control in our calm and peaceful time, where freedom and independence are the most important rights. Please do not stomp your feet, everything I have stated below will be confirmed and substantiated by real facts. "Truth and only truth, and nothing but truth!"
The discussion now is, of course, about collecting information, and somewhere else, monitoring based on information technology.
 We will not talk about video surveillance devices in public toilets and other places with large crowds. All of these devices, with the exception of those intended for protection, are equipped with signs such as “for your safety, video surveillance is conducted” and the person knows that he is under control.
We will not talk about video surveillance devices in public toilets and other places with large crowds. All of these devices, with the exception of those intended for protection, are equipped with signs such as “for your safety, video surveillance is conducted” and the person knows that he is under control.I would like to tell you about hidden surveillance systems and how to control them.
And the greatest attention is paid to the world wide web. Yes, my dear, the Internet.
')
According to the recently published information from Akavita in the Republic of Belarus, 3.2 million people use the Internet, this is a third of the country's population. This includes all and even those who are online every six months and less.
The number of Internet users in Russia is already more than 60 million people. Such data leads in its blog monitoring company Pingdom, citing Internet World Stats.
The internet penetration rate worldwide is 28.7 percent, and now I think it is already more. Thus, every fourth inhabitant of the Earth has access to the Network. I think these numbers will make you think about the importance of my post. Imagine every fourth person on Earth. Here you can envy only mobile communication with the connected half of the inhabitants of the Earth. Everyone uses it for his own purposes, the use of the Internet is so wide that I have to enumerate all its functions for a long time, but I will not go to the end.
It was not only me who was interested in, but also organs that care about what the people do and say on the world wide web. These bodies exist in each country, only their name changes. I think this information did not surprise you. Go ahead…
Ways to track the user on the Internet.
And so let's start modeling the situation. A person pours a cup of coffee or tea, sits at the monitor of his beloved computer, or picks up his mobile phone, connects to the back office, visits the site of interest, and waits for the server to respond. Then everything happens out of his sight.
A curious chain is built :
Tracking, information gathering, espionage, etc. from the browser side - further from the provider side - and of course not without the participation of the Internet provider, then everything goes cyclically but in the reverse order. It was about this chain that I wanted to tell you today. Be patient. We go further.
1. Spying by the browser
Well, on this occasion you can write books, for each browser has its own book. Most recently, I began to wonder about spying from the browser, but for the first time I managed to collect a lot of interesting information for you.
My description today will get the following browsers:
- Google Chrome
- Internet Explorer
- Opera
- Firefox
well, go ahead ...
How many I have not heard about this creation of Google. He is called the king of espionage. Let's see if this is so.
It is safe to say that the information transmitted is divided into two types:
Information associated with this installed product - its version, last update date, frequently used browser functions, etc.
Personal information - resources you visit, search queries, programs installed on your computer, DirectX version, etc. the company itself does not deny this, continuing to assert that no analytical processing is done with this information, but uses it only to develop new functions for its browser. And if not too much information not related to their products?
And it is no secret to anyone that insurance companies, personnel agencies and other potential advertisers have long shown a special interest in this data. So far, the chances of getting this information from business representatives are practically nil, which is not the case with the secret services. After all, the antiterrorist laws in the United States now oblige companies whose activities are related to the provision of Internet services to provide data that aroused the interest of the government or special services. Directly, Google through courts so far successfully resists attempts to declassify its database. However, how much is enough for him is unknown. And what's more, the fact that such large amounts of information are concentrated in the hands of one company makes it at the very least alert.
Test:
When installing the browser, GoogleUpdate begins to transfer something to its homeland, and this is not surprising, the company must know where and by whom its offspring is installed. Go ahead…
When the browser works with Russian-language sites, the following picture is viewed:

Total:
I used the browser version 14.0.797.0, when the browser is running, the firewall shows the information sent to the western domains. Conclusions do you.
Who does not know Internet Explorer, Internet Explorer knows everything, the brainchild of no less famous than the browser, the company Microsoft. Browser 8 started calling yours even during its installation. In response to the question of why Internet Explorer collects data about users, Microsoft representatives responded by saying that this was due to the need to obtain information about the requested user functions. But why should they information about the hard drive, processor and RAM is not clear.
And the well-known feature “recommended sites” that provides the user with similar sites on the desired subject is not implemented without transferring information about the lists of entered addresses directly to Microsoft.
In addition, Internet Explorer 8 collects user information using the SmartScreen tool. This filter is designed to protect against phishing, but after it is activated, data about which sites you visit and how much time you spend on them begins to be transmitted to Microsoft. The corporation does not exclude that in this way the information entered by the user when filling out web forms, including passwords, can also be transmitted. And although Microsoft solemnly assures that this data is transmitted exclusively in encrypted form and do not carry any threat of confidential information leakage, experts still recommend disabling the SmartScreen filter and using special programs to protect against phishing.
Test:
Scheme of outgoing traffic when working with Internet Explorer. Particular attention I want to pay System Process. Everywhere USA. That's it ...
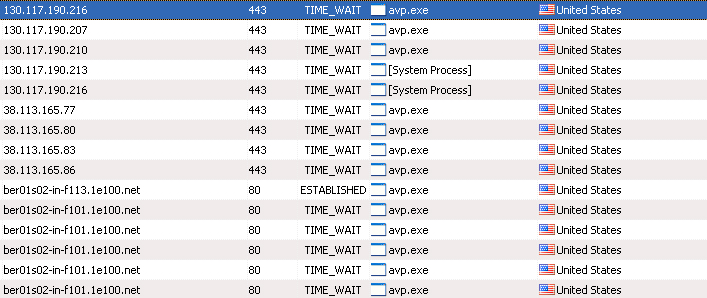
Total:
Another spy browser full of useful user features. Now we see how you have to pay for it.
Popular among the users of Runet browser from the Norwegian company Opera software. Spying with a bang begins when using technology Turbo. Its essence lies in the following: All traffic between the site and the user is passed through Opera software again. At the same time, no data encryption occurs, which also raises great doubts about the degree of confidentiality of this type of surfing. By default, this feature is turned off, and at will it can be turned off at any time, which cannot be said about Internet Explorer.
Test:
I am using a browser version 11.50 with attention, with the Turbo mode turned off. I would like to pay special attention to the Norwegian addresses sitecheck2.opera.com, the activity of the information sent to which increases, with each transition to a new address.
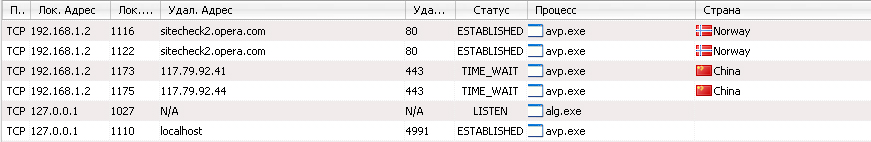
Total:
This time, let's say, it was more pleasant for me to see that the information is no longer going west, but the fact that it does not stay with me darkens the picture.
It is in last place in this review, because, compared with the programs already mentioned, it shows the least espionage curiosity. In general, I was very pleased with this browser, when installing it did not send the data to its homeland at all, and it was the only one that I suspected him of this when I first started the program. Well what can I say, and he is not without sin. This is clearly visible from two addresses.

Test:
When working on the network with Firefox, I have never noticed the data being sent to any unsolicited server. And it made me very happy. Bravo Mozila, Bravo Firefox.
Summarizing all of the above, we can observe a different policy of using confidential user data, each has its own, but one thing is clear that there is no need for normal browser operation to request the used sites each time you switch to a new address. You saw everything with your own eyes, analyze information and draw conclusions only to you.
2. Collecting information on the side of the ISP
This control is the highest quality and complete, all Internet traffic passes through providers, not one kilobyte passes by unnoticed. Based on the decrees of state bodies, providers control the outgoing traffic and maintain the base of resources used.
For example, in my country there is one main Internet provider, to which the other, smaller ones are connected, such is the law, nothing can be done, a monopoly.
Here is an excerpt from Directive 60 of the head of state:
6. Internet service providers are obliged to identify subscriber devices * in the provision of Internet services, accounting and storage of information about subscriber devices, as well as information about Internet services provided.
* For the purposes of this Decree, a subscriber device is a technical device of an Internet service user intended to connect to a telecommunication line in order to provide access to Internet services.
Here's another:
The storage of information specified in the first and second parts of this clause is carried out within one year from the date of the provision of Internet services.
Want to know the principles and methods of regulation? I can open the veil, not such a mystery.
For each user of the Internet, an Internet passport or ID-card is provided. It contains a database of visited resources by a specific user. Binding is carried out to a specific phone, and the phone is the connection point. If binding to a person cannot be done, for example, in places of collective use of the Internet, then the user is taken his passport data. In institutions where the Internet is free, an internal record of visiting the Internet is kept, he personally participated in the implementation of automated systems based on the journal “accounting of Internet usage in the workplace”. In general, everything is done to ensure that in case of an offense on the network, it would be possible to find a defendant for this offense.
In other countries, I think everything is built according to this scheme, the difference is only in technology.
“No state will leave without any control any of the spheres of human life. Now there are various ways to monitor the processes that occur on the Internet, and people who are active there. And in the future new methods of control will appear. ”
3. Collecting information on the server side
Everything is simple here. Record information about the user, collecting all sorts of statistics about him, ip, along with him your location, monitor resolution, browser and version, and much more. Being a website developer myself, I wanted to get as much information about users as possible to make a portrait of the target audience. And believe me, what I just did not recognize, until the date of installation of the operating system.
Separate attention would be paid to social networks. In order to bring up to date, I would like to immediately insert a few quotes:
Everyone remembers the interview during which Julian Assange said: “Facebook is the most complete database of people, their names, addresses, places of residence, family ties, relationships and communication with each other. All this data is accumulated in the United States and is available to American intelligence. " He added that Facebook, Google, Yahoo! and other US-based internet giants have special online interfaces designed for use by American intelligence. “We are not talking about the execution of court orders - they have interfaces designed for intelligence. What if Facebook was created by American intelligence? No, it is unlikely. Just intelligence has the ability to exert political and legal pressure on the company. It is too expensive for them to give out personal information for each individual request, so they automated the process, ”Assange openly stated.
Facebook itself refutes this information. The conclusions are yours.
Forbes edition writes that today, justice uses all modern methods in the fight against criminals. Therefore, representatives of justice are increasingly turning to social networks and IT companies that store a huge amount of personal data as the source of evidence of the investigation. The telecommunications company Sprint has confirmed that it has a special interface for official requests for information, as it receives millions of such events every year and is forced to put their satisfaction on the conveyor.
About “VKontakte” I will not write so much about it, and I’ll prove that I’m having brain and logic will understand, for example, the latest innovation “You can become a VKontakte user at the invitation of one of the participants.” Who is a frequent user, he probably knows about it, having confirmed Mobile phone number is easy to identify and the person’s identity and location. Having the phone number of the user Vkotakte "by default" will not be difficult to organize additional paid services with payment by SMS, which can cover almost all actions of users. The well-known Mail.Ru Group has gone the same way.
Special services do not need your passport data and place of study, they need your personal characteristics, hobbies, hobbies, favorite movies and music, and search queries on the site? Ltd! Vkontakte knows more about you than your mom, I think many will agree with me! More recently, after the terrorist attacks in the country, with the help of VKontakte, people who were acquainted with the perpetrators of the incident were identified, who in turn wrote their testimonies, in general, everything they know about them. That's it ...
Thanks for attention. I hope I have not offended anyone.
And lastly anecdote to the topic:
Links to the topic: Everyone will listen
Source: https://habr.com/ru/post/139603/
All Articles