Political spam about the rally on Pushkin Square "kills" users' computers
Urgent news! Friends, take care of computers.
Despite the fact that before the all-Russian presidential election in mail traffic there was practically no spamming on political topics, the attackers managed to activate after the end of the voting.
On March 5, 2012, Dr.Web specialists recorded a mass mailing list containing appeals to take part in an opposition protest rally on Pushkin Square in Moscow.
')
Post messages with the topic “Rally Fair Elections” or “All to Rally” contain a short text, for example: “Carefully read the instructions on what to do at this rally”, “Rally against Putin.
Carefully read the instructions "or" It is very important that you study the instructions, at this rally everyone will act according to this scenario, "and the attached file, which is a Microsoft Word document named Instructions_mitting.doc.
This document includes several macros that at the time of opening the file in a text editor save to disk and launch the Trojan program Trojan.KillFiles.9055, designed to disable the infected Windows system.
An example of a message in a Microsoft Word document named Instruction_daming.doc, sent in spam mailing:
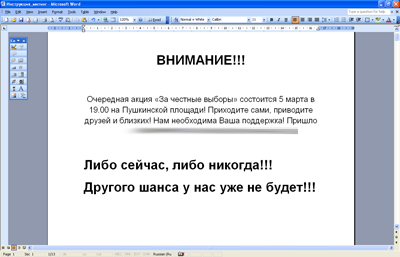
Having launched on the victim's computer, the Trojan Trojan.KillFiles.9055 copies itself to a temporary folder, writes itself to the registry branch responsible for automatically launching applications. At the same time, the Trojan changes the contents of all the files found on the C drive (with the .msc, .exe, .doc, .xls, .rar, .zip, and .7z extensions) to “digital trash” and marks them for deletion after the system is rebooted, resulting in Windows comes to an inoperable state (a normal restart of the computer does nothing to help). Trojan.KillFiles.9055 changes the properties of its process in such a way that it becomes critical for the system, and its termination causes the appearance of a BSOD ("blue window of death") or a restart of the computer.
Then the Trojan sends a message to the remote server of the attackers that the operating system has been successfully "killed".
In the event that the processing of macros is disabled in the settings of the Microsoft Word text editor of the potential victim, the user will not be able to read the text contained in the infected file. Infection of the system also will not occur. In this case, the contents of the document will look like this:
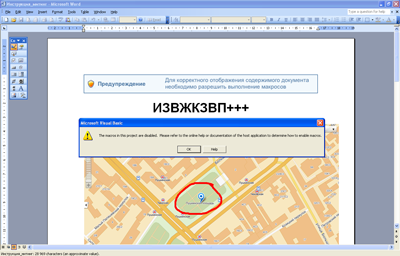
It is hard to underestimate the malicious potential of this threat, the signature of which has been added to Dr.Web virus databases.
Experts of Doctor Web recommend that users not open attachments to emails received from unknown senders, if possible not disable the built-in security system in Word that blocks the execution of macros, and also keep the antivirus software database up to date.
Despite the fact that before the all-Russian presidential election in mail traffic there was practically no spamming on political topics, the attackers managed to activate after the end of the voting.
On March 5, 2012, Dr.Web specialists recorded a mass mailing list containing appeals to take part in an opposition protest rally on Pushkin Square in Moscow.
')
Post messages with the topic “Rally Fair Elections” or “All to Rally” contain a short text, for example: “Carefully read the instructions on what to do at this rally”, “Rally against Putin.
Carefully read the instructions "or" It is very important that you study the instructions, at this rally everyone will act according to this scenario, "and the attached file, which is a Microsoft Word document named Instructions_mitting.doc.
This document includes several macros that at the time of opening the file in a text editor save to disk and launch the Trojan program Trojan.KillFiles.9055, designed to disable the infected Windows system.
An example of a message in a Microsoft Word document named Instruction_daming.doc, sent in spam mailing:

Having launched on the victim's computer, the Trojan Trojan.KillFiles.9055 copies itself to a temporary folder, writes itself to the registry branch responsible for automatically launching applications. At the same time, the Trojan changes the contents of all the files found on the C drive (with the .msc, .exe, .doc, .xls, .rar, .zip, and .7z extensions) to “digital trash” and marks them for deletion after the system is rebooted, resulting in Windows comes to an inoperable state (a normal restart of the computer does nothing to help). Trojan.KillFiles.9055 changes the properties of its process in such a way that it becomes critical for the system, and its termination causes the appearance of a BSOD ("blue window of death") or a restart of the computer.
Then the Trojan sends a message to the remote server of the attackers that the operating system has been successfully "killed".
In the event that the processing of macros is disabled in the settings of the Microsoft Word text editor of the potential victim, the user will not be able to read the text contained in the infected file. Infection of the system also will not occur. In this case, the contents of the document will look like this:

It is hard to underestimate the malicious potential of this threat, the signature of which has been added to Dr.Web virus databases.
Experts of Doctor Web recommend that users not open attachments to emails received from unknown senders, if possible not disable the built-in security system in Word that blocks the execution of macros, and also keep the antivirus software database up to date.
Source: https://habr.com/ru/post/139515/
All Articles