Download without haste
Good day to all! Today, our senior virus analyst Vyacheslav Zakorzhevsky will tell you about how he tried to find a guide to transistors on the Internet, and what came of it:
I think that the overwhelming majority of users use the Internet to download this or that content, sometimes legal, and sometimes not. This is used by intruders. To illustrate how this happens, I conducted a little research in combat conditions.
I started by deciding to try to download the “Transistor Reference”, for which I used Google. There are many expected search results.
')
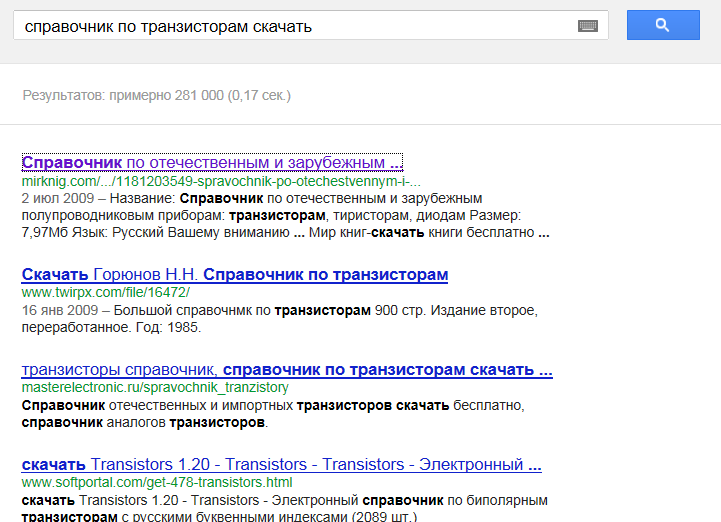
I follow the first link ...
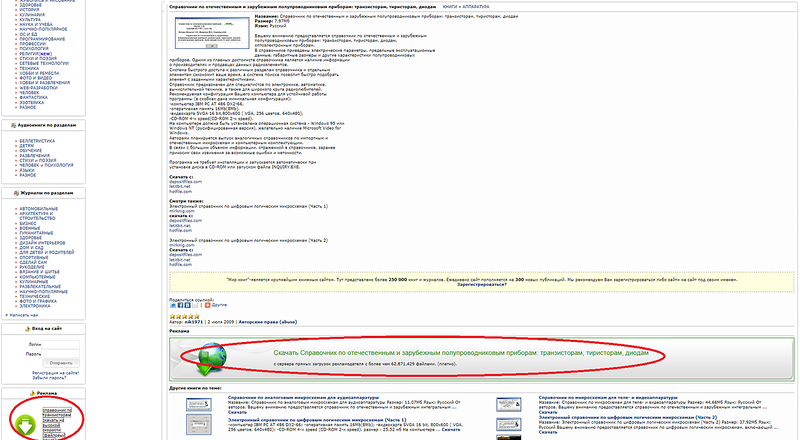
I see on the page some bright inscriptions with the suggestion to download. I decided to start by clicking on the banner in the lower left corner. A window opened in front of me, which at first glance contained the real page of the famous service “Answers@Mail.ru.”

However, if you look closely, you can see that this page is not located on the official page of the otvety.mail.ru service, but on a domain with a somewhat suspicious name (the beginning of the domain has been deliberately erased). Here, allegedly, the girl asks a question about where you can find the “guide to transistors”. According to the structure of the sentence, it can be assumed that instead of the phrase “reference book on transistors”, anything can be contained there. And indeed - to this place is inserted what is transmitted in the parameter “key” through the address bar (see the screenshot above). If you score something random there, you’ll get something like this.

In general, the page is definitely fraudulent. And in response to the girl's question, there is “advice” to go to the site, where you can download what you need. And, of course, a lot of positive "reviews". If you click on the link in the answer, then you can contemplate the proposal to download a file called “directory of” t`t., 4a, 4`c.zip ”, but on a different domain.

Obviously, this is a fraud, because here the user is asked to send an SMS or connect a subscription for downloading a deliberately non-existent file . Since a normal file-sharing service, obviously, would verify the existence of that or an object.
With one link, everything is clear. When you click on the link in the center (second screenshot), through a series of redirects, the browser will go to the page labeled “Google Files”. The domain in this case is already Indian, which also does not inspire confidence. I immediately decided to check whether there is a real search here. To do this, I typed in the search string the phrase "non-existent file."
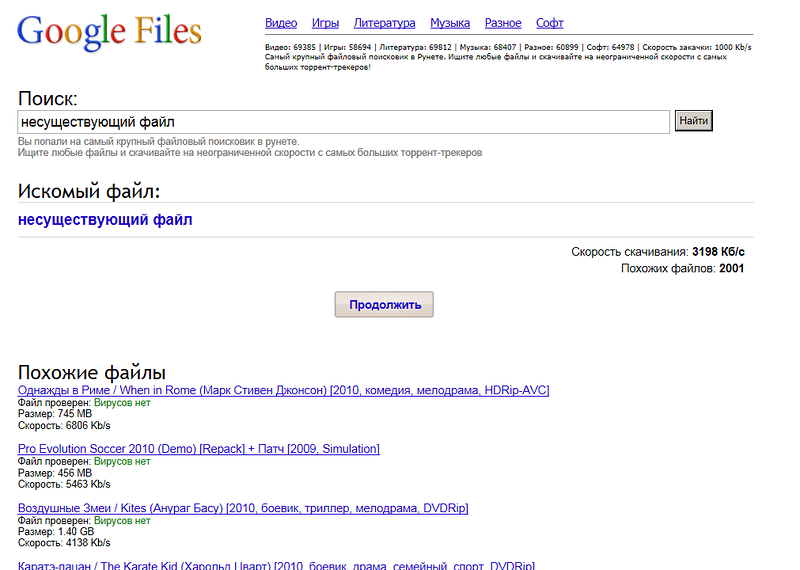
Incredibly , but such a file was found. The file name here is also contained in the address bar, as in the previous example. I immediately downloaded the “Searched File” with the funny name “nesushchestvuyushchiy_fayl.zip.exe” and launched it on VmWare.
It is no coincidence that the name ends with “.zip.exe”. This is done so that users who have hidden extensions enabled are shown “nesushchestvuyushchiy_fayl.zip”. Again, to generate more confidence.

The attackers used the well-known brand WinZip to convince users of the legality of such an archive. As usual in such programs, after clicking the “continue” button, an animation will be drawn, ostensibly reflecting the unpacking process. And at the end there will be an offer to send SMS. Since it is clear that there is no “non-existent file” in the archive, it is obvious that it will either be empty or will offer some instructions for using the torrent tracker.
The file itself takes 4 MB and is written in Borland C ++ Builder. After some analysis of the file, it was found that developers actively resist detection by antivirus programs. In this case, the cryptor or protector is not used, but the lines are only changing.

In the screenshot, I highlighted a few lines that have been modified specifically. For example, in the code instead of “smstariffs.ru” is indicated “sm st ari ffs. Ru”, instead of “SMS” - “S M_S”. It should be noted that the products of Kaspersky Lab successfully detect and bans such files.
As with most frauds in runet, affiliate programs are behind this scheme. Below I have posted a screenshot of the affiliate program responsible for distributing the disassembled malware.
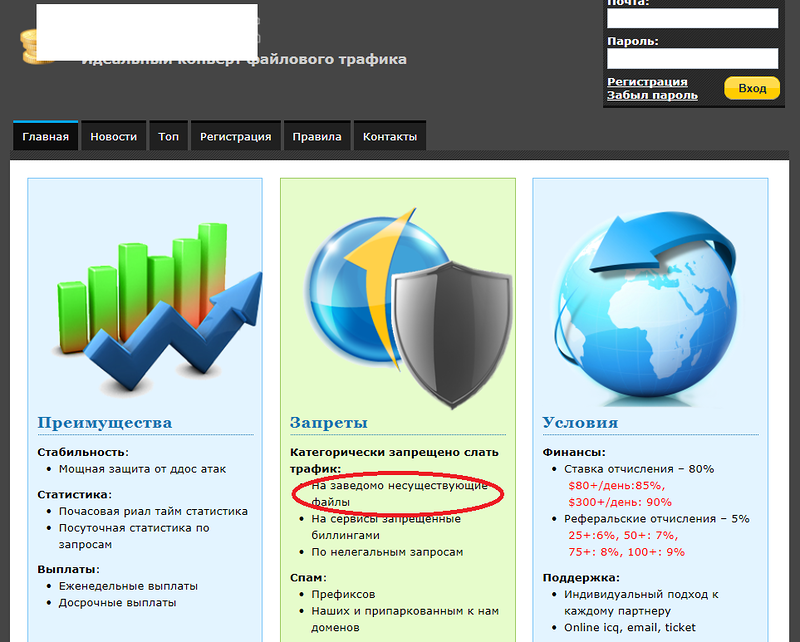
Particularly pleased with the ban on the distribution of archives to obviously non-existent files. In my experience, it is violated in the vast majority of cases.
What more can be said? Indeed, you can find absolutely any desired information on the Internet and even download it. But one should not think that the worldwide network will kindly present everything on a silver platter. You need to be careful and not be led to the tricks of intruders: bright colored banners, which indicate high download speeds and the ability to find any files. As always, do not forget to tell your parents or sister who is looking for an essay. Good luck!
I think that the overwhelming majority of users use the Internet to download this or that content, sometimes legal, and sometimes not. This is used by intruders. To illustrate how this happens, I conducted a little research in combat conditions.
I started by deciding to try to download the “Transistor Reference”, for which I used Google. There are many expected search results.
')

I follow the first link ...

I see on the page some bright inscriptions with the suggestion to download. I decided to start by clicking on the banner in the lower left corner. A window opened in front of me, which at first glance contained the real page of the famous service “Answers@Mail.ru.”

However, if you look closely, you can see that this page is not located on the official page of the otvety.mail.ru service, but on a domain with a somewhat suspicious name (the beginning of the domain has been deliberately erased). Here, allegedly, the girl asks a question about where you can find the “guide to transistors”. According to the structure of the sentence, it can be assumed that instead of the phrase “reference book on transistors”, anything can be contained there. And indeed - to this place is inserted what is transmitted in the parameter “key” through the address bar (see the screenshot above). If you score something random there, you’ll get something like this.

In general, the page is definitely fraudulent. And in response to the girl's question, there is “advice” to go to the site, where you can download what you need. And, of course, a lot of positive "reviews". If you click on the link in the answer, then you can contemplate the proposal to download a file called “directory of” t`t., 4a, 4`c.zip ”, but on a different domain.

Obviously, this is a fraud, because here the user is asked to send an SMS or connect a subscription for downloading a deliberately non-existent file . Since a normal file-sharing service, obviously, would verify the existence of that or an object.
With one link, everything is clear. When you click on the link in the center (second screenshot), through a series of redirects, the browser will go to the page labeled “Google Files”. The domain in this case is already Indian, which also does not inspire confidence. I immediately decided to check whether there is a real search here. To do this, I typed in the search string the phrase "non-existent file."


Incredibly , but such a file was found. The file name here is also contained in the address bar, as in the previous example. I immediately downloaded the “Searched File” with the funny name “nesushchestvuyushchiy_fayl.zip.exe” and launched it on VmWare.
It is no coincidence that the name ends with “.zip.exe”. This is done so that users who have hidden extensions enabled are shown “nesushchestvuyushchiy_fayl.zip”. Again, to generate more confidence.

The attackers used the well-known brand WinZip to convince users of the legality of such an archive. As usual in such programs, after clicking the “continue” button, an animation will be drawn, ostensibly reflecting the unpacking process. And at the end there will be an offer to send SMS. Since it is clear that there is no “non-existent file” in the archive, it is obvious that it will either be empty or will offer some instructions for using the torrent tracker.
The file itself takes 4 MB and is written in Borland C ++ Builder. After some analysis of the file, it was found that developers actively resist detection by antivirus programs. In this case, the cryptor or protector is not used, but the lines are only changing.

In the screenshot, I highlighted a few lines that have been modified specifically. For example, in the code instead of “smstariffs.ru” is indicated “sm st ari ffs. Ru”, instead of “SMS” - “S M_S”. It should be noted that the products of Kaspersky Lab successfully detect and bans such files.
As with most frauds in runet, affiliate programs are behind this scheme. Below I have posted a screenshot of the affiliate program responsible for distributing the disassembled malware.

Particularly pleased with the ban on the distribution of archives to obviously non-existent files. In my experience, it is violated in the vast majority of cases.
What more can be said? Indeed, you can find absolutely any desired information on the Internet and even download it. But one should not think that the worldwide network will kindly present everything on a silver platter. You need to be careful and not be led to the tricks of intruders: bright colored banners, which indicate high download speeds and the ability to find any files. As always, do not forget to tell your parents or sister who is looking for an essay. Good luck!
Source: https://habr.com/ru/post/139439/
All Articles