Interception sessions in wireless networks
On Habré, there was already an article about Intercepting user accounts on Wi-Fi networks with Android using the DroidSheep utility (a small Russian howto for the lazy ).
Using this program, I was faced with the question: how would I save captured sessions? DroidSheep allows you to send intercepted sessions by mail. But it is very inconvenient for me. I would like to save the session in the usual pcap format for further analysis on a stationary computer via WireShark (or through its counterpart on the android SharkReader ).
In fact, the task can be reformulated: we need arp-spoofing with the ability to log all intercepted packets into the pcap format. The proposed option does not claim to be optimized in any way. But it is quite efficient.
')
I decided that the issue is solved by a bunch (joint work) of 2 programs:
1. to organize an arp-spoofing attack
2. for logging into the usual pcap
The first question is solved automatically: DroidSheep allows you to organize arp-spoofing.
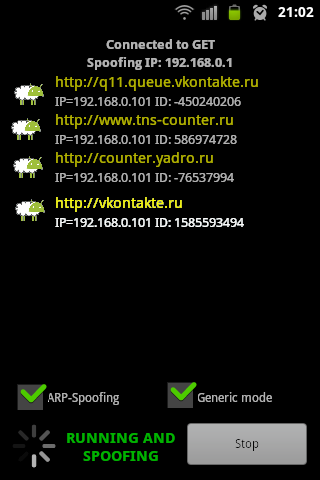
A cursory search for other programs of this class did not work.
The second question is solved using the Shark program.

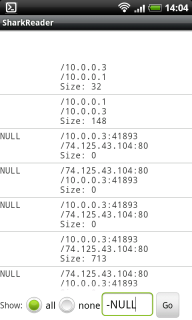
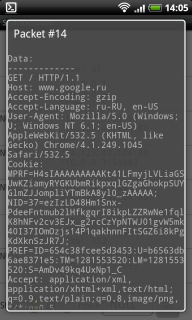
It would be more flexible to use passive traffic listening in wireless networks using aircrack-ng . But installing aircrack-ng for Android is non-trivial. But not so heavily attacking the network.
Using this program, I was faced with the question: how would I save captured sessions? DroidSheep allows you to send intercepted sessions by mail. But it is very inconvenient for me. I would like to save the session in the usual pcap format for further analysis on a stationary computer via WireShark (or through its counterpart on the android SharkReader ).
In fact, the task can be reformulated: we need arp-spoofing with the ability to log all intercepted packets into the pcap format. The proposed option does not claim to be optimized in any way. But it is quite efficient.
')
I decided that the issue is solved by a bunch (joint work) of 2 programs:
1. to organize an arp-spoofing attack
2. for logging into the usual pcap
The first question is solved automatically: DroidSheep allows you to organize arp-spoofing.

A cursory search for other programs of this class did not work.
The second question is solved using the Shark program.



It would be more flexible to use passive traffic listening in wireless networks using aircrack-ng . But installing aircrack-ng for Android is non-trivial. But not so heavily attacking the network.
Source: https://habr.com/ru/post/139176/
All Articles