An iOS application can access device photos without notifying a user.
The recent mention that iPhone apps may have access to the entire address book of a smartphone without any notice to the user, as a result of which Apple even received a request from the US Congress, received an unexpected continuation. (Moreover, the problem with the iPhone was one of the reasons for changing the data privacy agreement for mobile applications, which was changed by Google, Apple, Microsoft and a number of other large companies under pressure from the California Attorney General).
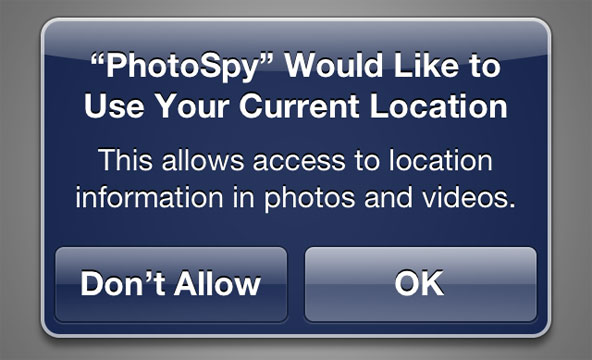
Guided by unclear motives and a source of information, the New York Times journalists asked unnamed developers (it’s only reported that they work for a well-known company) to write the PhotoSpy application, which requests access to the location information, having received that, it is able to copy the user's photo and , in fact, the location data themselves on the remote server, without in any way informing the user about it. Permissions to place in the AppStore PhotoSpy not received; Apple itself has not yet commented on the actions of journalists.
The problem exists for iOS versions, starting with the 4th, when the system was able to access the user's photos in order to create more flexible applications. One of the developers advised users who are worried about privacy to disable the location capabilities of their smartphones, which, in his opinion, would exclude the possibility of the potential exploitation of the discovered loophole. For the sake of justice, journalists notice that Apple does not explicitly prohibit copying photos from the device, relying on developers on this, however, in fact, no one can prevent any of them from creating an appropriately "curious" application.
')
Also recently it became known that the password-protected iPhone can be accessed using simple SIM-card manipulations.
[ Source ]
UPD: Apple has officially recognized the error and are working on fixing it in a future iOS 5.1 update. The company claims that "any program wishing to gain access to contact information should require explicit distribution from users, this will be implemented in future versions of the software."
Source: https://habr.com/ru/post/139079/
All Articles