“Anatomy of anonymous attacks” - how does Anonymous work?
The American company Imperva , which develops data protection solutions, has published its 17-page report on the work of the well-known hacktivist group Anonymous. One cannot say that the report reveals the terrible secrets of the underground organization of intruders, but, nevertheless, it is very convenient as a systematic picture.
So, according to the report, Anonymous is not a group of super-genius hackers capable of hacking any server in a matter of hours or days and stealing any information. Although there were precedents with successful attacks on such reputable organizations as StratFor and a number of others, the success of the attack is due more likely to the carelessness of resource managers, and not to any super-ingenious technique of attackers. So the researchers believe that although Anonymous has some specific techniques, however, the group prefers widely known methods - first of all, these are SQL injections and DDOS attacks, moreover, Anonymous, as a rule, first try to steal data, and then if it is not crowned with success, organize DDOS on the victim's resource.
The group itself is divided into two unequal parts: skilled hackers ( Skilled hackers ) and volunteers ( Laypeople ). The first is a group of experts, the number of which does not exceed 10-15 people with a very high level of knowledge in various areas of IT and actual experience in hacking complex systems. Volunteers are a much larger group, the number of participants of which is estimated from a few dozen to several hundred people, the level of qualification and knowledge of which is most often average or below average and which are guided by the instructions of the first group - qualified hackers.
The typical attack of Anonymous on the resource of the victim is divided into three parts:
')
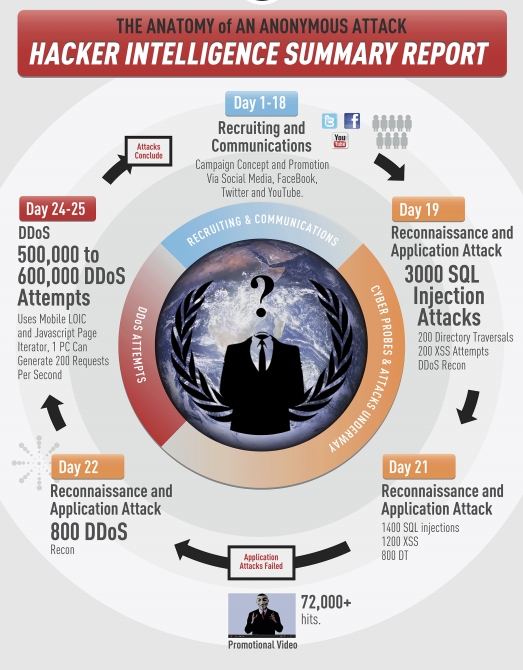
Infographics of typical Anonymous attacks are presented below.
What tools does a skilled part of intruders use?
It is curious that after analyzing the attacks of Anonymous, the author of the report also describes ways to protect against data theft and DDOS, and not least the Imperva tools play, which, however, is quite expected.
You can read more about Imperva's Hacker Intelligence Summary pdf report here .
So, according to the report, Anonymous is not a group of super-genius hackers capable of hacking any server in a matter of hours or days and stealing any information. Although there were precedents with successful attacks on such reputable organizations as StratFor and a number of others, the success of the attack is due more likely to the carelessness of resource managers, and not to any super-ingenious technique of attackers. So the researchers believe that although Anonymous has some specific techniques, however, the group prefers widely known methods - first of all, these are SQL injections and DDOS attacks, moreover, Anonymous, as a rule, first try to steal data, and then if it is not crowned with success, organize DDOS on the victim's resource.
The group itself is divided into two unequal parts: skilled hackers ( Skilled hackers ) and volunteers ( Laypeople ). The first is a group of experts, the number of which does not exceed 10-15 people with a very high level of knowledge in various areas of IT and actual experience in hacking complex systems. Volunteers are a much larger group, the number of participants of which is estimated from a few dozen to several hundred people, the level of qualification and knowledge of which is most often average or below average and which are guided by the instructions of the first group - qualified hackers.
The typical attack of Anonymous on the resource of the victim is divided into three parts:
- ( Days 1-18 ) Recruitment and Coordination. At this stage, using the capabilities of social networks, a group of managers gathers the future team and organizes it to coordinate actions.
- ( Days 19-22 ) Intelligence and, in fact, attack. During this period, a group of skilled hackers, carefully hiding traces of their activities, are looking for weak spots on a resource that has been hacked using tools such as Acunetix and / or Havij . If security holes are found, a group of intruders exploit them and steal the required data, disabling the attacked resource if it considers it necessary (for example, StratFor did not work for about two weeks after the theft of the correspondence).
- ( Days 24-25 ) DDOS attack. At this stage, which follows, as a rule, because data theft was not successful, Anonymous volunteers, using such means as Low Orbit Ion Cannon (LOIC), carry out a DDOS attack, using, for example, mobile browsers.
')
Infographics of typical Anonymous attacks are presented below.

What tools does a skilled part of intruders use?
- Havij Scanner - a tool for automating SQL injection, attributed to Iranian hackers
- Acunetix scanner - vulnerability scanner (SQL injection, XSS, etc.) in web applications.
- Nikto Web Scanner is an open source tool for finding web server vulnerabilities.
It is curious that after analyzing the attacks of Anonymous, the author of the report also describes ways to protect against data theft and DDOS, and not least the Imperva tools play, which, however, is quite expected.
You can read more about Imperva's Hacker Intelligence Summary pdf report here .
Source: https://habr.com/ru/post/138964/
All Articles