Trusted loading and data protection during remote work at graphic stations
 The company DEPO Computers together with OKB CAD has developed a solution to provide trusted remote download and control the state of the data.
The company DEPO Computers together with OKB CAD has developed a solution to provide trusted remote download and control the state of the data.There are many software and hardware tools for protecting information and trusted boot, but now we’ll talk about the Accord-AMDZ module (hardware trusted boot module) integrated into the CAD systems consolidation solution . The Accord module is installed in a remote graphics station and intercepts the loading of the operating system. User authentication is performed on a PCoIP terminal with the help of personal cryptographic protection SHIPKA (Encryption, Identification, Signature, Authentication Codes), which can also be used for authentication at the entrance to the domain.
The hardware component of the server part of the solution
The Accord-AMDZ module is installed in a workstation located in the data center within the local network of the enterprise. The form factor of the graphics station may be different.
 For high-performance dual-processor stations, this can be a Blade version or 1U. The graphic station DEPO Race BladeG10 has a number of advantages and disadvantages compared to the 1U station DEPO Race C770R1U . One of the advantages is a high computing power density: 10 blades occupy only 7U in a 19 "rack. Also, Blade systems are highly resilient: the DEPO Race BladeEN710 chassis is equipped with four 2kW hot-swappable power supplies and n + 1 redundancy. Also in Blade -systems support redundant Ethernet switch and IPMI module.
For high-performance dual-processor stations, this can be a Blade version or 1U. The graphic station DEPO Race BladeG10 has a number of advantages and disadvantages compared to the 1U station DEPO Race C770R1U . One of the advantages is a high computing power density: 10 blades occupy only 7U in a 19 "rack. Also, Blade systems are highly resilient: the DEPO Race BladeEN710 chassis is equipped with four 2kW hot-swappable power supplies and n + 1 redundancy. Also in Blade -systems support redundant Ethernet switch and IPMI module.
The 1U platform, in turn, is less expensive, more reliable local disk subsystem and the ability to install up to two NVIDIA Quadro or Tesla cards.
As a 1-processor solution, a more budget model of rack-mount graphics stations was developed - this is DEPO Race C250S2U.
 About her, we would like to write a little more. The workstation is made in a 2U package with support for ATX power supplies, which significantly reduces the cost. The platform is built on a C206-motherboard with support for ECC-memory and Xeon E3 processors. The use of only low-profile expansion cards can be a significant limitation, which, in principle, does not prevent us from installing a professional entry-level video adapter, PCoIP host card and Accord trusted boot module in the workstation.
About her, we would like to write a little more. The workstation is made in a 2U package with support for ATX power supplies, which significantly reduces the cost. The platform is built on a C206-motherboard with support for ECC-memory and Xeon E3 processors. The use of only low-profile expansion cards can be a significant limitation, which, in principle, does not prevent us from installing a professional entry-level video adapter, PCoIP host card and Accord trusted boot module in the workstation. 
The cooling system of the case is implemented by two 80mm front fans and one 70mm rear. When operating the workstation in more severe temperature conditions, it is possible to additionally install two 40mm exhaust fans behind the casing.
The disk subsystem is built from 4 disks without the possibility of hot swapping - 2 at the front and 2 at the rear.
The power supply has a horizontal purge 80mm fan. PSUs with a 120mm fan in this case do not fit - this is due to the location of the unit in the case.
The front panel is equipped with a removable dust filter. There are also compartments for the installation of an optical drive and card reader.
')
The composition of SZI
 The Accord-AMDZ module has a low-profile design and a PCI-E x1 interface. The board has an RJ-11 connector for connecting a magnetic key identifier identification device. But, since in our case identification is performed using SHIPKA, this connector is not used in the solution.
The Accord-AMDZ module has a low-profile design and a PCI-E x1 interface. The board has an RJ-11 connector for connecting a magnetic key identifier identification device. But, since in our case identification is performed using SHIPKA, this connector is not used in the solution.The SHIPKA keys have a USB interface and are of two types: the first for trusted boot of the OS — it is used by the user and the second for administration and configuration.
Operating principle
The workstation is turned on remotely using a PCoIP terminal. Before loading the OS Accord intercepts control. At this point, the host card is activated and already provides full connection between the workstation and the terminal. The following prompt appears on the screen:
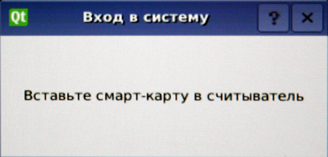
Next, you need to insert the SHIPKA key identifier into any USB port of the PCoIP portal.
The system will identify the key and ask for the password.
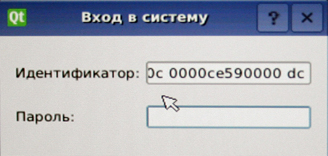
If a user key was inserted, then with correct authentication, the operating system will start. If we used the admin key, we will see the following window:
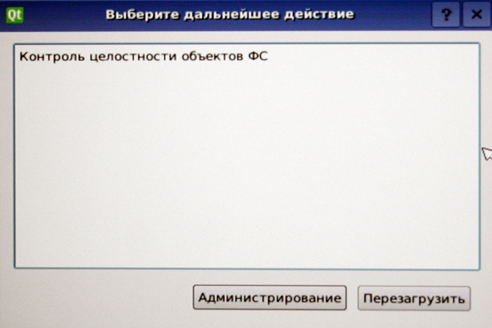
Selecting "Administration" we get into the setup menu of the Accord module.
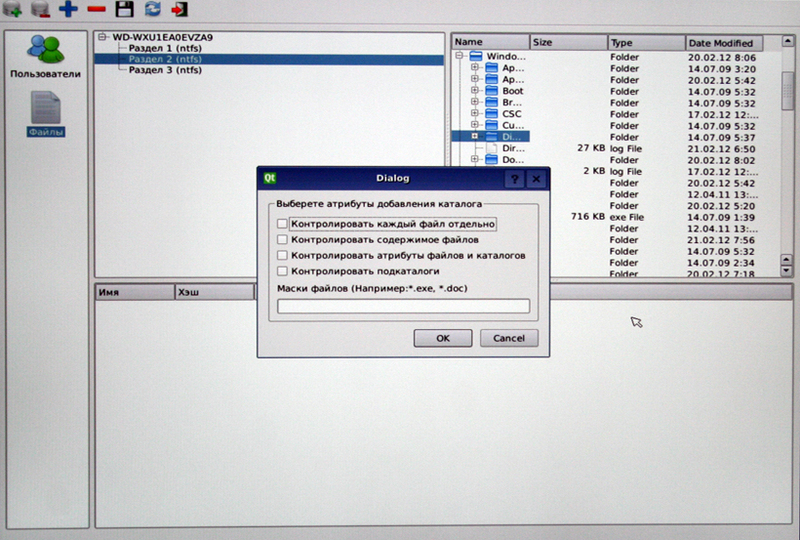
Here you can customize the monitoring of the integrity of both individual files and entire directories. The system saves the checksum of protected objects and checks it before each loading of the operating system. If a user accidentally or intentionally made changes in protected objects during the work, then the next time the OS workstation starts up, it will be possible to log in only with the admin key. Thus, the user will be forced to call the sysadmin and will not be able to hide the interference.
Usikoff ,
Technical Specialist DEPO Computers
Source: https://habr.com/ru/post/138725/
All Articles