The history of computer viruses

Startup StopTheHacker completed the first round of funding and announced the launch of commercial SaaS security services for websites.
The size of investments amounted to 1.1 million US dollars from public and private investors, including Runa Capital and Brian Nesmith , the former president of Blue Coat .
')

We are so used to viruses that it is difficult to even imagine the Internet without malicious software. But few people are aware of what scale the problem has reached.
“We invested in StopTheHacker because they represent the future of the security services market ,” said a representative of the fund Runa Capital. - StopTheHacker technology is a new type of website protection that is vital for most modern businessmen. They will be absolutely sure that their sites, online stores and customers are constantly under reliable protection. At the same time, no additional programs or equipment are needed. ”
Today, more than 75% of sites are quite vulnerable. Every day, six thousand sites are blacklisted by Google due to unintentional malware infection. In total, they infect from 2.5% to 5% of all websites, which coincides with data on computer infection by viruses ten years ago. Existing anti-virus solutions can neutralize only 40% of malware spreading on the network: the situation in the area of online threats is constantly changing, and more than 100 million sites do not have sufficient protection.

“Website protection is the future of information security, ” said Brian Nesmith , former president of Blue Coat. - I invested my money in StopTheHacker, because their technology is a breakthrough in my field. It does not use standard signature-based protection methods; artificial intelligence system (AI) constantly monitors new types of malware and builds a profile of emerging threats. Today, in the face of constantly changing Internet threats, this is an urgent need . ”
The StopTheHacker artificial intelligence system was created after four years of research at the University of California and was initially funded by the United States National Science Foundation. It independently adapts to the situation, constantly tracking new malware and creating a profile of emerging threats. This allows StopTheHacker services to detect zero-day attacks undertaken by previously unknown programs. This simple, effective and cost-effective SaaS model requires neither hiring specialists, nor installing additional programs or equipment.
“The number of web servers is growing very fast, and, accordingly, the number of hackers, both experienced and inexperienced, is increasing in order to cash in on weak points in the protection of websites. This is a very common problem. The damage to the brand, reputation and customer relations means serious losses for cloud and online businesses , ”said Peter Jensen, the startup manager. “ By collaborating with StopTheHacker, web hosters and service providers will be able to reduce the costs associated with hacker attacks on data centers and technical support, as well as maintain infrastructure security for their customers.”

Viruses, worms, trojans and botnets evolve with incredible speed, and systems of protection will become smarter. But in general, the whole network today is the front line. While sitting at the armor plate of firewalls and antiviruses, you can overlook this. But try to access the network on a system at least a year ago and take a good look at the network - very quickly your computer will be hacked and infected, your personal data will leak into the network and moreover you will also take part in spamming and dos-attacks.
According to statistics, more than a third of all computers connected to the Internet are infected with viruses, worms or botnets. It is useless to fight this - the open architecture of the Internet is ideal for viruses, and this problem will be solved radically in the future - each user will keep a local copy of the Internet, and go online only if necessary in an armored suit.
The threat is so great that in May 2011, US President Barack Obama signed a decree formalizing and regulating cyber attacks as a type of military action. Disabling computers with viruses and terrorist special forces equated to military aggression. Accordingly, the enemy’s cyber attacks are equated with a military attack and can now be recognized as the basis for the start of a full-scale war.

According to experts, in 2013, Washington will have to spend $ 10.7 billion to protect against cyber attacks. In 2008, $ 7.4 billion was spent on these goals. In the very near future, the White House will have to allocate almost the same amount cyber defense of electrical grids and other objects of national infrastructure of civilian use.
This is the result of the half-century history of the Internet - it was created in 1969 to protect against military attack, and in 2011 this network itself became the main target of the enemy. Most of all on the topic of "Internet war" the Germans succeeded - not having their own army, most of the defense budget of Germany was directed to the development of information technology.

Just one example. In 1980, Richard Clark published a major study, Technological Terrorism. The book describes in detail, with great anticipation, all the directions of terrorism at the beginning of the twenty-first century. Much attention is paid to attacks on computers. This was written before the era of personal computers, when the concept of viruses did not exist. Ironically, the work of Clark played a large role in the dispersal of information storage devices and the creation of the Internet, which just created an ideal environment for virus attacks. A year after the book was published in Germany, the famous Chaos Computer Club appears, specializing in “working” with viruses.

SSS logo on the congress-house captured by hackers in honor of the 20th anniversary of the group.
The club gained international fame in 1989, when a group of hackers led by Karl Koch was arrested for penetrating the corporate networks of the US government. The prosecution alleged that hackers stole the source codes of the military operating system and handed them over to the KGB. However, the case was quickly hushed up due to the disappearance of the accused. Later, their charred remains were found in the woods near the town of Celle. The criminal case was not initiated, because German police immediately recognized the death of Koch suicide.

Karl Koch during his lifetime.
About SSS dozens of films have been shot and hundreds of books have been written, the club’s influence has no analogues - its members are members of government structures and have held prominent posts even in ICANN .
Specifically, the history of viruses began, as expected, an innocent experiment.
1988 - shots in the air
On November 2, the son of an NSA computer security expert, Robert Morris, decided to check what would happen if you added a bit of chaos to an ordinary virus and turned on the self-copying feature. Up to this point, the viruses did not copy themselves if they found that the machine was already infected. Therefore, the admins just slipped the virus to his dummy and he calmed down. Morris simply added a timer, by which the virus unconditionally copied itself and thereby continued to multiply unnoticed by the admins with their blanks.

Trololo-man in person.
It would be the usual self-replicating program if Morris were a diligent student, but ... A minor logical error in the program code would lead to a disaster. Computers were repeatedly infected with a worm, and each additional copy slowed down the computer’s work, quickly exhausting resources. Very quickly, the virus broke out of the walls of the native uni.
The worm used long-known vulnerabilities in the Sendmail mail server, Finger, rsh / rexec services with dictionary selection of passwords. The dictionary was small - only about 400 keywords, but at the end of the 1980s very few people thought about computer security, and the account name (usually the real user name) often coincided with the password.
The worm also used a disguise in order to hide its presence in the computer: it deleted its executable file, renamed its process to sh, and branched it every three minutes.
The epidemic struck about six thousand nodes ARPANET. The best computer security specialists of that time were invited to the Berkeley Institute from all over the country to counteract the effects of the harmful effects of the virus. But they never managed to figure out the author of a wonderful virus.

The Morris worm source diskette stored at the Museum of Science in Boston.
However, his father, a computer expert at the National Security Agency, clearly explained that his son had better admit everything. The court sentenced him to three years probation, 10 thousand dollars of fines and 400 hours of community service.
The Morris worm was the starting point for computer security. It was after him that the developers came up with / etc / shadow, as well as a pause after incorrectly entering the password.
It was these events that formed the basis of the film Hackers. The Internet from the rear service of the US Department of Defense has become a front line.
1998 - first attempt at writing
I remember the joy that the Internet this year was still a luxury, and I connected to it only in fragments and then after two o'clock in the morning. My less economical friends then seriously forked to buy new motherboards. I think many readers still remember the famous WIN.CIH. On the 26th of each month, it irreversibly damaged flash memory on the motherboard.
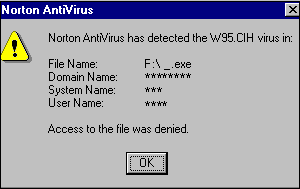
On April 26, 1999, on the anniversary of the Chernobyl accident, the virus intensified and destroyed the data on the hard drives. On some computers, the contents of the BIOS chips were corrupted. It is precisely the coincidence of the activation date of the virus and the date of the Chernobyl accident that gave the virus a second name - “Chernobyl”, which is even more well known among the people than “CIH”. According to various estimates, about half a million personal computers worldwide have been affected by the virus.
The virus was written in Taiwan by student Chen Inhao (born April 26, 1975) and sent to a number of electronic Internet conferences during May-June 1998. On June 27, reports of damage caused by this virus were received from Southeast Asia, from the United States and a number of other countries. We also found this virus in the middle of the summer of 1998 in Moscow and Novosibirsk.

Chen Inhao at work.
When infecting files, the virus looks for “holes” in them (blocks of unused data) and writes its code in them. The presence of such “holes” is due to the structure of PE files: the position of each section in the file is aligned with a specific value specified in the PE header, and in most cases there is a certain number of bytes that are not used by the program between the end of the previous section and the beginning of the next. The virus looks for such unused blocks in the file, writes its code in them and increases the size of the modified section by the required value. The size of the infected files does not increase.
But the main difference between the virus was different. He was the first to learn how to infect not only computers, but also websites - namely, a lot of game servers in the USA, from where copies of games spread around the world. In the early autumn of the same year, pirated CDs with popular computer games infected with this virus came out and fled across the CIS.
Due to the infection of sites, the epidemic has become global - even computers not connected to the network were destroyed. The damage from Chernobyl was $ 80 million.
1999 - socialization
On Friday, March 26, 1999, W97M / Melissa became the main topic on the Internet and world media. According to rough estimates, the virus hit at least 20% of all business PCs. The virus spread so quickly that Intel, Microsoft and other corporations that used Outlook, were forced to disable their e-mail servers in order to at least prevent the spread of infection.

Developing the success of WIN.CIH, the virus used Microsoft Outlook to send itself to 50 addresses from the user's contact list. Thus, the victim herself provided the database for infection. The damage from the virus was $ 600 million.
However, Melissa taught little to users, just a year later the world saw the most destructive virus in history - ILOVEYOU. Also known as Loveletter and The Love Bug. The distribution was as simple as ingenious: email with the subject “ILOVEYOU” and the attachment “Love letter for you” - file TXT.vbs. After executing the script, like Melissa, the virus sent itself to Microsoft Outlook contacts.

The virus even hit the Guinness Book of World Records as the most destructive in history, hitting more than three million computers around the world and causing damage of $ 15 billion.
2001 - server attack
After the incredible success of “mail viruses”, antivirus companies close security holes and viruses are switched to public sites and servers. Actually since 2001, it is possible to count the modern era in computer security. One by one there are "server viruses":
Code red is a virus that exploits Microsoft Internet Information Server vulnerabilities. Also known as Bady, Code Red was meant to inflict maximum damage; all sites infected by it looked accordingly:

After that, the virus began to search for other vulnerable sites. In about 20 days, all the websites had to launch a distributed denial of service DDoS attack on certain IP addresses, including the White House Web server. In less than a week, the virus infected about 400,000 servers. The damage amounted to $ 3 billion.
2003 - infection sites
Immediately two worms begin a massive infection of Internet sites: Blaster and Sobiq. In the very first day, Sobik produces more than one million of its own copies. The purpose of the virus is to obtain all possible email addresses stored on your computer and give them your copy. Well, MSBLAST.exe doesn’t need to be presented, I think everyone remembers it in person:

The main task of MSLlast was the DDOS attack on windowsupdate.com - from the 16th of August all infected machines begin to continuously send requests for system updates and the site crashes, unable to withstand the load.
The total damage from worms was $ 20 billion. Microsoft announced a $ 250,000 reward for anyone who can provide information about the creator of Sobiq.F. Looking for so far. A side effect of both worms was the colossal growth of Internet traffic. This effect has been applied next year.
2004 - the Internet stops
An unknown group of hackers triggers a chain reaction of three insidious worms. On January 18, the Internet hits 100 modifications to the Bagle worm. It sends itself by mail just like Sobik, but at the same time, the infected computer opens access to the TCP port, which can be used to catch any information of interest to the attacker. All copies of the virus self-destruct on January 28, 2004.
And on January 26, the MyDoom epidemic begins. Distributed by mail and through the peer network Kazaa. But this time, the effect was felt not only by the affected machines - at the peak of the epidemic, the worm increased the load on the Internet by 10 percent, and the load time of Web sites by 50%.
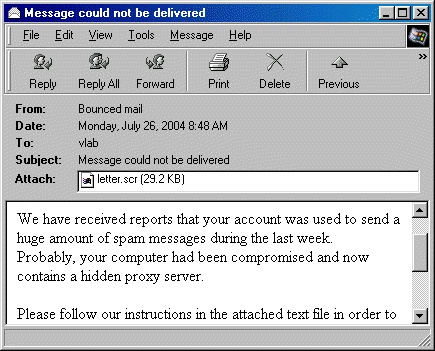
The result was so successful that in the first hours of infection for every 10 emails sent out there was one infected with this virus. MyDoom was programmed to stop its distribution after February 12, 2004.
On April 30, the third worm, Sasser, finishes the Internet. Using the vulnerabilities of Windows 2000 and XP, the virus has achieved significant success and has caused a shutdown of satellite communications for several French news agencies. Also, this virus caused the cancellation of several flights of Delta Airline and the shutdown of computers of many companies around the world. After successful copying, the worm began searching for other unprotected systems and copied itself. The computers infected with this virus were distinguished by the rare instability of work and frequent reboots caused by the failure of the lsass.exe process:

As a result of the investigation, the 17-year-old schoolboy from Germany was named the author of the viruses, launching the global epidemic as a birthday present. Because of the minority, he avoided any punishment.
From this point on, experts stop calculating damage from viruses, since amounts pass for tens and hundreds of billions of dollars.
In November 2004, the first worm appeared spreading only through websites. Santy was written in the Perl scripting language and using phpBB forum vulnerabilities. The virus simply sent a request to Google containing the string "Powered by phpBB", and thus received the addresses of the attacked forums. Then, having generated an incorrect request to the viewtopic.php file, I was able to execute arbitrary code on the server and replaced the contents of all files with the asp, htm, jsp, php, phtm, shtm extension with “This site is defaced !!! This site is defaced !!! NeverEverNoSanity WebWorm generation X ”, where X is the generation number of the worm.

Within a day since its introduction on December 20, 2004, the worm successfully attacked 40 thousand sites. On the second day, Google no longer conducted a search for the phrase "Powered by phpBB." After that, modifications of the worm using other search engines appeared.
2007 - the era of botnets
Now viruses do not just infect sites, they create botnets and protect them. The Storm worm appeared on January 17, 2007 and in the first week alone infected two million computers.
Storm «», , , , Storm Worm /, «DDoS-» — , DDoS-.

, . , , -«» . , , Storm, .
, - 1 50 . , Storm — . Storm .
19 2008 , , , Full Clip.exe, Full Story.exe, Read More.exe Video.exe.
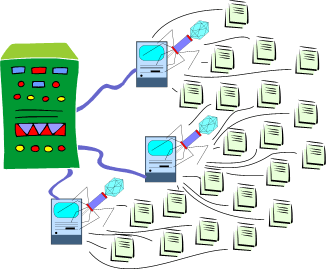
, , , . Storm , ( 30-45 ), . . , , .
, Storm : Win32.agent.dh, , DDoS-.
, IBM Internet Security Systems, Storm IP-, , DDoS- . , , - Storm, .
2010 —

Siemens.
, .. Stuxnet . Microsoft Windows, , — Simatic Step 7, . Stuxnet ( ), - . , . , , . 2009-2010 , .
. , ++. — . MicronJ RealTek. , . , - , , . -.

, XXI .
Source: https://habr.com/ru/post/138171/
All Articles