Tor has released an obfuscated proxy to disguise traffic in Iran
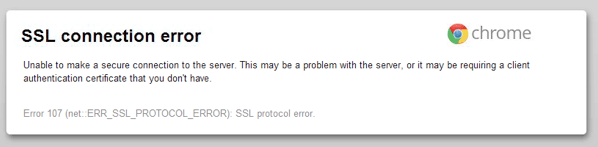
According to users from Iran, on Thursday, January 9, some of the country's Internet providers began filtering Internet traffic by signature ( deep packet inspection ), blocking almost all SSL / TLS packets. Thus, HTTPS services, including Gmail, Google search and sites of other Internet companies, have stopped working for users. SSH tunneling on the Iranian Internet has been blocked a few months ago.
Tor experts analyzed how local authorities block HTTPS, apparently, this is done in three ways:
- deep packet inspection for SSL
- selective blocking of combinations of IP addresses and TCP ports
- keyword filtering
SSL lockout is not complete and nationwide. Until now, most users have HTTPS running. In other places, apparently, the system recognizes packets at the beginning of the SSL handshake and simply stops the procedure for establishing a secure connection.
')
Judging by the statistics of direct connections from Iranian IP , so far HTTPS blocking is not particularly used, although there is some reduction in traffic. However, Tor experts believe that in the near future, filtering will spread to the whole of Iran. Therefore, they offer such a solution .
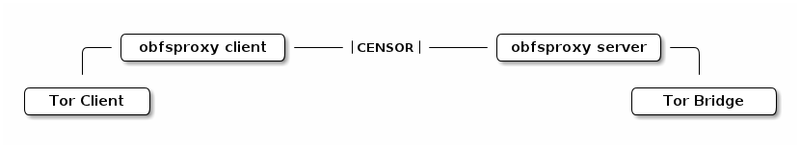
Operators of private network bridges are invited to install a special obfuscated bridge that will mask HTTPS traffic - especially for Iran. See instructions for installing such a bridge here . On the other hand, users will also need to install obfsproxy in their obfuscation of traffic.
Private bridges are not listed in the general directory of Tor nodes, but are reported only upon request from a particular network segment . Thus, users from Iran will be able to use your network bridge, if necessary. Obfuscation of traffic, theoretically, will allow to bypass the blocking by signatures from the Iranian authorities.
Source: https://habr.com/ru/post/137994/
All Articles