Intel Anti-Theft Special Forces

Every 53 seconds in the world steal a laptop. In American airports alone, the number of stolen laptops reaches 12,000 a week. About half of them contain sensitive data in unencrypted form. Such an interesting statistic leads the company Intel on the official website.
In my note, I will talk about what steps Intel has taken towards altering this sad statistic.
For starters, some loud headlines about losing confidential or even secret government information.
- “Fidelity Investments investment company laptop stolen in Boston. The computer contained confidential data on almost 2 thousand accounts of its clients. ”
- “From the car of an employee of Ameriprise Financial Inc. a laptop was stolen with personal data of more than 2 thousand people. "
- And even this:
"Agent MI5 (British counterintelligence service) lost a laptop containing secret government information."
Intel AT or Anti-Theft Technology is designed to end this disgrace.
Its support is already implemented on Intel platforms with Core i3, i5, i7 processors. Currently, the technology receives an active advancement in connection with the advent of ultrabooks - lightweight and convenient for work on the road devices. Since these are mostly compact and expensive gadgets, security issues are critical here.
So how is security enforced?
A computer that supports Intel AT technology can be deactivated by the so-called “poison pill”. This is an encrypted sms message that is transmitted through the 3G network. In addition, in the lock mode, the laptop reports its geographic coordinates at specified intervals.
For this additional tracking function, when purchasing a device, you need to check in advance the availability of a compatible 3G / GPS module. The photo shows such a module from Sony-Ericsson.
')

The interaction between the chipset and the 3G module occurs at the hardware level. Thus, reinstalling the operating system and even replacing the hard drive (which is, in fact, a little more difficult than replacing the SIM card in a mobile phone) cannot disable laptop protection.

Intel Anti-Theft hardware support is embedded in the chipset unit called the Management Engine (ME). ME controls the laptop before the operating system loads and, in particular, controls the operation of the power supply system. He is also responsible for storing the keys of the data encryption system. If the computer locks up, the system does not pass POST .
It is important that the owner of the computer receives confirmation of its blocking. The deactivation process is reversible. If you manage to return the laptop, it can be easily reanimated.
A number of other functions:
- The administrator can send a message to the stolen laptop, which the attacker sees when turned on.
- Repeated failed authorization attempts result in system lockout. The number of allowed attempts is set by the administrator.
- You can pre-set the geographical area beyond which the laptop is blocked.
- Another interesting feature is the mandatory “check-ins” or “rendezvous” with the central server at predetermined intervals. If the computer misses them, it is blocked until the administrator reactivates it.
This is the screen of the locked computer:
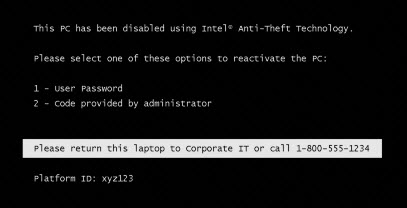
Already on the market are solutions with the support of this technology from all major players in the laptop market: Acer, Asus Dell, Fujitsu, HP, Lenovo, Sony, and others. The full list can be viewed at the link.
In order to protect your laptop, you need to go to the page atservice.intel.com and create an account using the activation code from the card that comes with the laptop.
Then the computer is linked to the account using a special application. After the computer is registered in the system, the user can adjust the rendezvous with the server through the web interface, change the message that is displayed in blocking mode, and finally, at any time declare the system to be wanted.
Intel AT works worldwide, including in Russia. Unfortunately, at the moment the web interface has only the English version.
Conclusion

It would seem that this technology is of interest only to large companies that need to ensure the safety of their confidential data. However, it is unlikely that any ordinary user would want their private correspondence, photos and videos, along with the saved passwords, to be shared with the intruders. Therefore, technology is highly demanded, and its widespread introduction will reduce the attractiveness of a laptop as an object of theft. After all, a stolen device with such a built-in service will in the worst case turn into a useless brick; at best, it will lead directly to the robber.
Source: https://habr.com/ru/post/137529/
All Articles