"Money for free!" For fans of social networks
One of the most risky elements for criminals of any criminal cyber scheme is the withdrawal of stolen money. As a rule, states establish strict control over all cash flows. Therefore, in order to preserve their own security, attackers offer other people to take all the risk in exchange for a portion of the profits. Such volunteers are called “drops” or “mules.” One of the most common criminal schemes in Russia is as follows: stolen credit card dumps are poured onto “white plastic” - the so-called “blanks” of credit cards without any identifying marks. Then this card is sent to the “drop” for withdrawing money, of course, with a preliminary agreement on how much the person keeps and how much to transfer to the customer. Since most people are interested in the long-term “money-for-free” scheme, then, as a rule, the terms of the contract are not violated, and the attackers end up with cash.

As you can see, this way of earning does not require any outstanding abilities from a person and can be performed even by a child. That is why such a simple criminal scheme attracts lovers of "freebies" around the world. Far from everyone is thinking about the illegality of the actions being carried out, and meanwhile they are the ones who fall into the hands of the police in order to subsequently bear the responsibility established by the legislation.
Announcements about such a side job can be found everywhere without any problems: on ad sites, in spam , social networks. Social networks are of particular interest, because they are a priori more personalized and cause people more confidence. In addition, the applied methods of social engineering in this case are limited only by the fantasy of intruders. The study will conduct a comparative analysis of the state of networks for September 2011 and now.
')
To begin, consider the most popular social network in the CIS - vkontakte. Variants of such proposals in it are quite diverse:
Until recently, the existing service enjoyed increased attention from intruders. Searching for keywords like “ATMs”, “withdrawals”, “cashing out” gave out a lot of offers for every taste about “freebies”, “earning up to 90 thousand rubles at a time”, “working for disciplined responsible guys”:
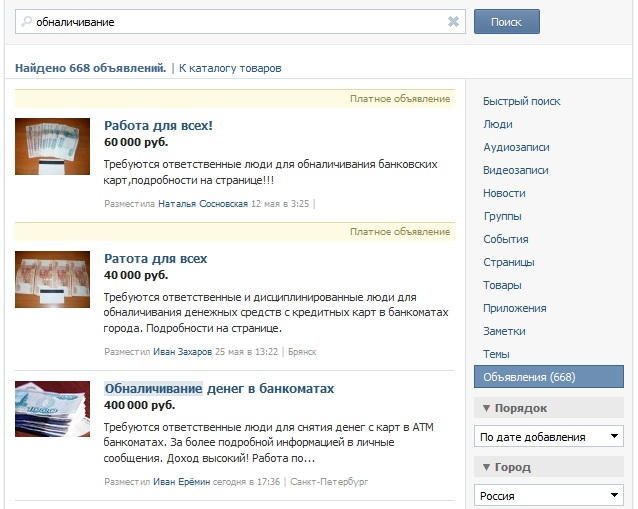
And search for contacts from these ads:

pointed out that the attackers are trying not to be limited to one source of recruiting:
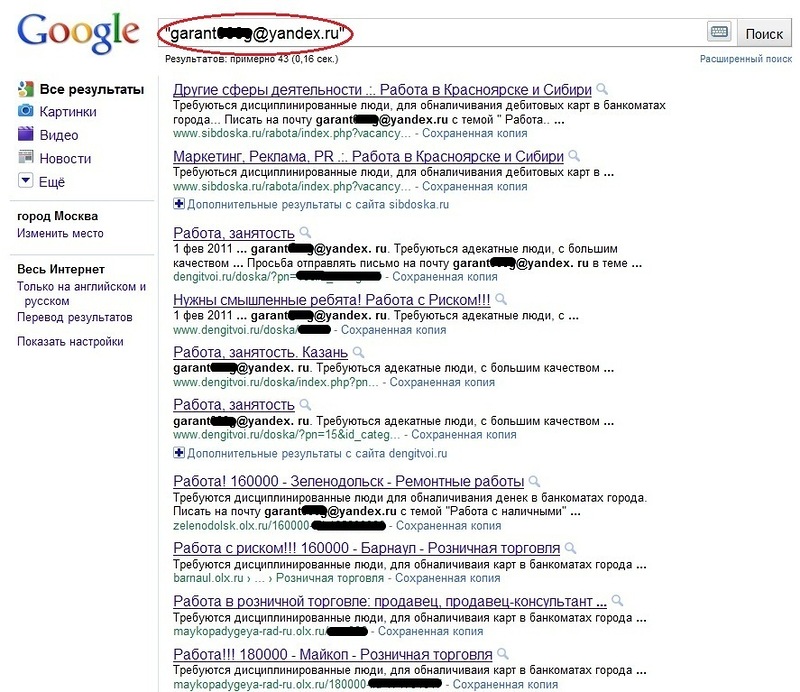
Since the specificity of “work” is such that not only does it not require people from a specific geographic location, but, on the contrary, welcomes their distance from each other, the same ads are often duplicated for various cities:

However, since October 2011, the administration of vkontakte has closed the ad service, forcing the attackers to look for other sites to earn money. Some of them, however, chose not to part with the lived-in social network and gradually moved into groups.
In September, searching for similar keywords easily gave out dozens of relevant groups to users:
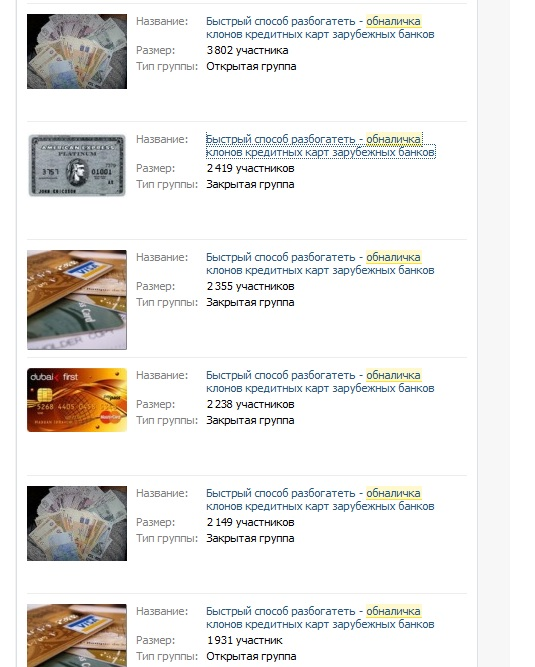
The number of participants in such groups may initially be puzzling, but, as a rule, a significant part of them are bots, consisting of several similar groups each. Often, many people simply automatically add to all the groups they offer, without ever visiting them. In addition, it is worth considering the probability of hacking and unauthorized use of pages of respectable users.

However, if we look at the current state of the problem, then we can observe dramatic changes for the better. So, the search for the end of January 2012 yields significantly less similar offers:
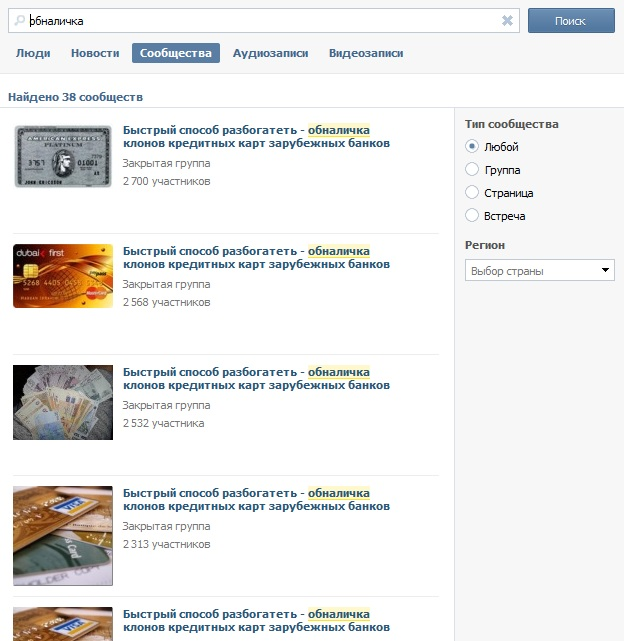
In addition, the administration of such groups in most cases banned:
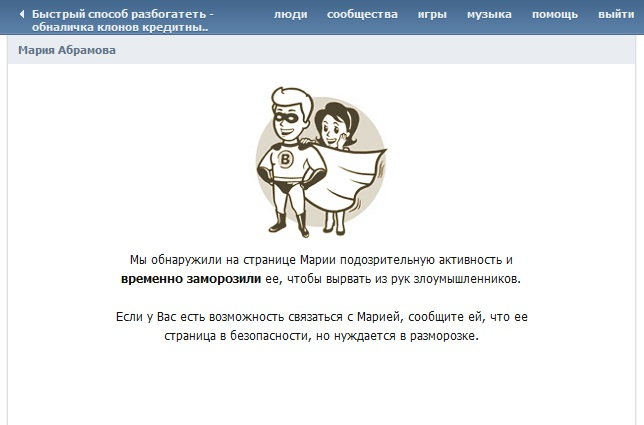
People who place ads in similar groups are not deprived of attention:
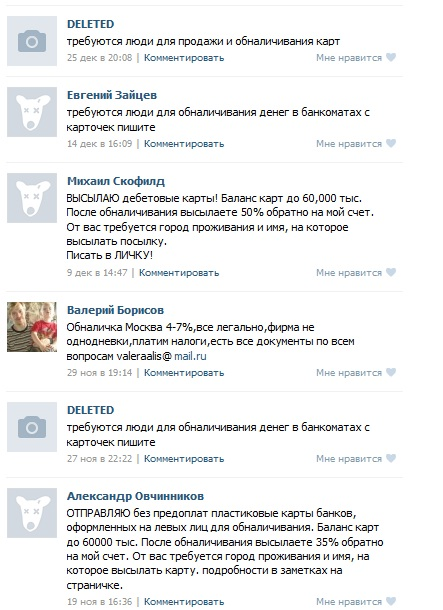
Here, much attention is paid to the design of a personal page in order to produce the maximum good impression for potential “partners”. Attention to detail in such a case - the key to success.
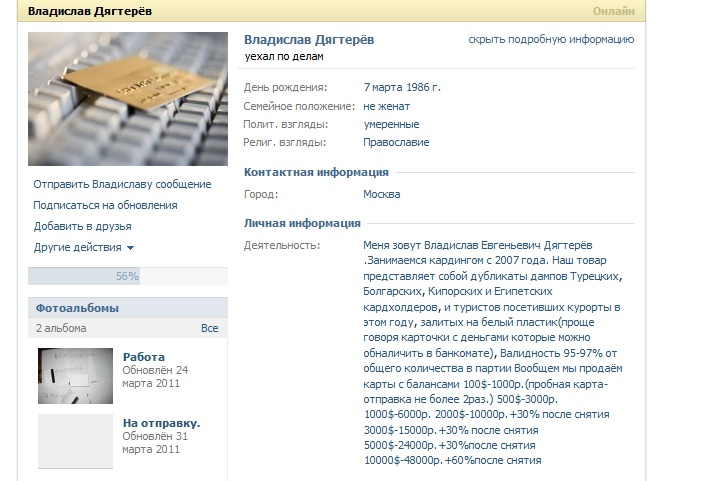
Often, on the walls of such accounts, you can see open discussions of people already involved in this business:
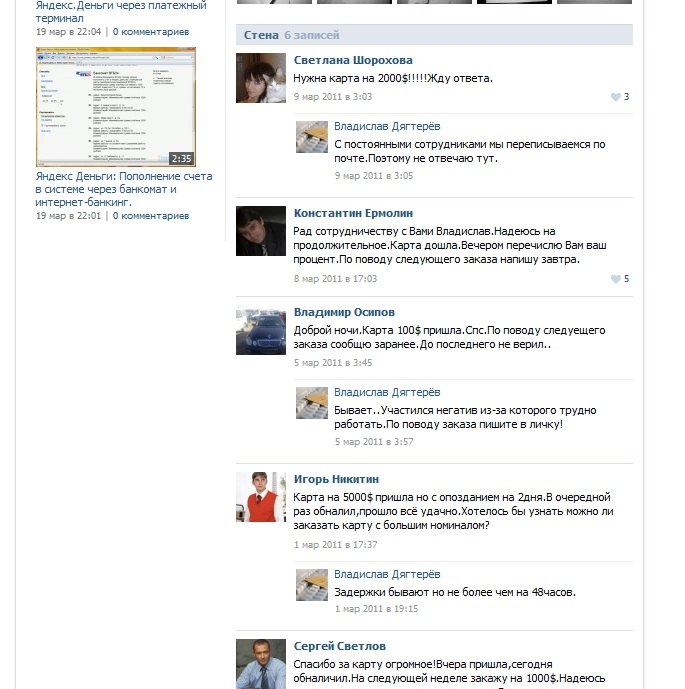
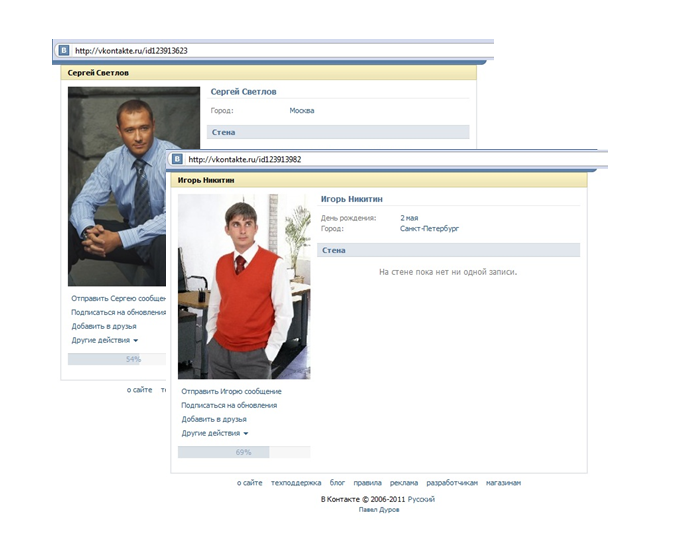
It should be noted here that the methods of social engineering are used in this case to the full extent. So, people who unsubscribed on the above wall are very likely to be bots. This is indicated not only by actually empty pages with no signs of activity, but also by approximately the same creation time, judging by the id numbers:
And what about other social networks? Consider the situation in the largest international social network - facebook.
The first thing that paid attention in September after using vkontakte is how much the situation is different for the better. Obviously, facebook was moderated relatively successfully since it was not so easy to find similar proposals in such an open form.
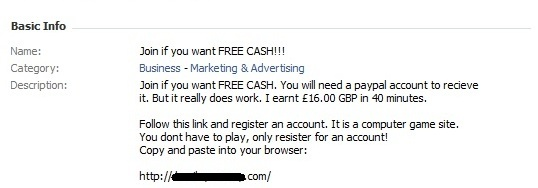
The typical schemes for hiring mules through facebook were described in some detail by my colleague Roel and added Dmitry Bestuzhev in his blog . As a rule, such proposals are hidden behind "work at home", "easy money on the Internet", etc. A significant part of the advertisements in fact is the use of other people's accounts in one or another payment system in exchange for a reward.
If we compare vkontakte and facebook, on the side of the latter one can observe quite clearly pronounced differences:
1) The attackers often more carefully select the target audience, which, presumably, is due to more stringent moderation. Thus, two tasks are being addressed simultaneously - to reach a significant number of potential “partners” and not to catch the eye of people who are more likely to immediately send a complaint to the network administration.

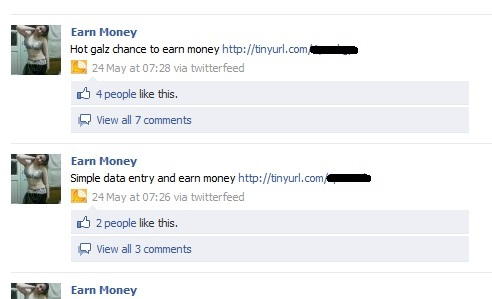
2) the social network is often used not for directly creating ads, but for posting links to other resources. In principle, this can also provide some advantages in terms of social engineering. As the simplest example, use of the GeoIP service to determine the location of a potential “partner” in the criminal business can be cited. In addition, the increasing popularity of the attackers are gaining services to reduce links, not allowing a descent on its appearance to find out where the transition will take place.
3) announcements with offers of illegal equipment for carrying out fraudulent activities of this kind, such as selling skimmers for ATM, are more common.

However, the administration of facebook is also not idle, and currently the author of the article was able to find only one offer to sell the corresponding equipment.

Moreover, the number of search results for contacts from the ad clearly hints that the group is not doing very well:

A good example is the fate of the group members who robbed users with the help of the ZeuS Trojan family. As a result of the special operation, several dozen people were tracked down, and they were charged with complicity in the theft and money laundering. As a result of the trial, they face imprisonment and fines on large sums. As we can see, the bulk of the “drops” were young people who bought the proposal to quickly earn extra money.
Alas, the thirst for free money is ineradicable in people, especially inexperienced and not sufficiently secure financially. Warn your friends that free cheese is only in a mousetrap, and for similar offenses, according to the laws of different countries, it is punishable, even criminal.
Also I would like to separately thank the administrations of social networks for their contribution to the fight against cybercrime.
Virus analyst of Kaspersky Lab Alexey Kleymenov aka Kleymenov raised the level of citizens' consciousness

As you can see, this way of earning does not require any outstanding abilities from a person and can be performed even by a child. That is why such a simple criminal scheme attracts lovers of "freebies" around the world. Far from everyone is thinking about the illegality of the actions being carried out, and meanwhile they are the ones who fall into the hands of the police in order to subsequently bear the responsibility established by the legislation.
Announcements about such a side job can be found everywhere without any problems: on ad sites, in spam , social networks. Social networks are of particular interest, because they are a priori more personalized and cause people more confidence. In addition, the applied methods of social engineering in this case are limited only by the fantasy of intruders. The study will conduct a comparative analysis of the state of networks for September 2011 and now.
')
To begin, consider the most popular social network in the CIS - vkontakte. Variants of such proposals in it are quite diverse:
ads
Until recently, the existing service enjoyed increased attention from intruders. Searching for keywords like “ATMs”, “withdrawals”, “cashing out” gave out a lot of offers for every taste about “freebies”, “earning up to 90 thousand rubles at a time”, “working for disciplined responsible guys”:

And search for contacts from these ads:

pointed out that the attackers are trying not to be limited to one source of recruiting:

Since the specificity of “work” is such that not only does it not require people from a specific geographic location, but, on the contrary, welcomes their distance from each other, the same ads are often duplicated for various cities:

However, since October 2011, the administration of vkontakte has closed the ad service, forcing the attackers to look for other sites to earn money. Some of them, however, chose not to part with the lived-in social network and gradually moved into groups.
Groups
In September, searching for similar keywords easily gave out dozens of relevant groups to users:

The number of participants in such groups may initially be puzzling, but, as a rule, a significant part of them are bots, consisting of several similar groups each. Often, many people simply automatically add to all the groups they offer, without ever visiting them. In addition, it is worth considering the probability of hacking and unauthorized use of pages of respectable users.

However, if we look at the current state of the problem, then we can observe dramatic changes for the better. So, the search for the end of January 2012 yields significantly less similar offers:

In addition, the administration of such groups in most cases banned:

People who place ads in similar groups are not deprived of attention:

Personal offers
Here, much attention is paid to the design of a personal page in order to produce the maximum good impression for potential “partners”. Attention to detail in such a case - the key to success.

Often, on the walls of such accounts, you can see open discussions of people already involved in this business:

It should be noted here that the methods of social engineering are used in this case to the full extent. So, people who unsubscribed on the above wall are very likely to be bots. This is indicated not only by actually empty pages with no signs of activity, but also by approximately the same creation time, judging by the id numbers:

international arena
And what about other social networks? Consider the situation in the largest international social network - facebook.
The first thing that paid attention in September after using vkontakte is how much the situation is different for the better. Obviously, facebook was moderated relatively successfully since it was not so easy to find similar proposals in such an open form.
The typical schemes for hiring mules through facebook were described in some detail by my colleague Roel and added Dmitry Bestuzhev in his blog . As a rule, such proposals are hidden behind "work at home", "easy money on the Internet", etc. A significant part of the advertisements in fact is the use of other people's accounts in one or another payment system in exchange for a reward.

If we compare vkontakte and facebook, on the side of the latter one can observe quite clearly pronounced differences:
1) The attackers often more carefully select the target audience, which, presumably, is due to more stringent moderation. Thus, two tasks are being addressed simultaneously - to reach a significant number of potential “partners” and not to catch the eye of people who are more likely to immediately send a complaint to the network administration.

2) the social network is often used not for directly creating ads, but for posting links to other resources. In principle, this can also provide some advantages in terms of social engineering. As the simplest example, use of the GeoIP service to determine the location of a potential “partner” in the criminal business can be cited. In addition, the increasing popularity of the attackers are gaining services to reduce links, not allowing a descent on its appearance to find out where the transition will take place.

3) announcements with offers of illegal equipment for carrying out fraudulent activities of this kind, such as selling skimmers for ATM, are more common.

However, the administration of facebook is also not idle, and currently the author of the article was able to find only one offer to sell the corresponding equipment.

Moreover, the number of search results for contacts from the ad clearly hints that the group is not doing very well:

What about responsibility?
A good example is the fate of the group members who robbed users with the help of the ZeuS Trojan family. As a result of the special operation, several dozen people were tracked down, and they were charged with complicity in the theft and money laundering. As a result of the trial, they face imprisonment and fines on large sums. As we can see, the bulk of the “drops” were young people who bought the proposal to quickly earn extra money.
Conclusion
Alas, the thirst for free money is ineradicable in people, especially inexperienced and not sufficiently secure financially. Warn your friends that free cheese is only in a mousetrap, and for similar offenses, according to the laws of different countries, it is punishable, even criminal.
Also I would like to separately thank the administrations of social networks for their contribution to the fight against cybercrime.
Virus analyst of Kaspersky Lab Alexey Kleymenov aka Kleymenov raised the level of citizens' consciousness
Source: https://habr.com/ru/post/137460/
All Articles