FreeBSD and D-Link DI-804HV over IPSEC
I want to talk about one of my first experiences with FreeBSD and how to set up IPSEC to communicate with D-Link DI-804HV and the problems that arose. I hope this helps people not to step on my rake.
It so happened that when I came to a new job, the server with FreeBSD, which was the gateway to the Internet, fell into my area of responsibility - a mail server and a firewall were running on it. From previous work there was experience with Linux, but FreeBSD had never seen it before. And one of the first tasks of the new work was to set up a connection to a remote office through the Internet, for this purpose they bought a piece of metal D-Link DI-804HV. It was decided to connect this whole economy through IPSEC.
Some changes have been made to the article, based on comments after the publication
So, what we had in stock (addresses here are given solely for example):
internal enterprise network 192.168.250.0/24 ,
internal office network 192.168.0.0/24 ,
Enterprise Router 192.168.250.1
office router 192.168.0.1
external address on FreeBSD 10.10.10.1 ,
external address on the DI-804HV 10.10.10.2 .
All work carried out first on the test machine to avoid any unpleasant moments.
Well, it all started as usual - from reading the documentation on the D-link site and other network resources. The D-Link website has a description of the FreeBSD 4.8 bundle with this piece of hardware, but some of the information there is already outdated, as it turned out later.
I started my work with rebuilding the kernel, including the necessary options — the kernel configs are in / usr / src / sys / i386 / conf , I copied GENERIC to IPSEC and started making changes.
')
Since I have FreeBSD 9, the changes are as follows:
If the version is less than 7 (as I understood from the discussion in the internet), the following is necessary:
I rebuilt the kernel with the commands:
where IPSEC is my kernel configuration name.
Overloaded the car, checked that it is loaded.
Then proceeded to install the software itself. Before installing, everyone recommends updating ports, in my case it was through the commands:
After that, I started installing the necessary ports. From reading articles in the forum, I realized that I need a racoon, it is located in the ports / usr / ports / security / ipsec-tools . There is also racoon2, but we do not need it, because ikev2 is not supported by DI-804HV.
Install the port through:
After installation, go to the / usr / local / etc / racoon directory - if not, then create - and create the racoon.conf configuration file :
Authentication will occur using a shared key (shared_key), which is located in the /usr/local/etc/racoon/psk.txt file:
I would like to note that this file needs to change the attributes of the form 0600 from the root:
Otherwise, then you can understand for a long time why it does not work.
Then make changes to / etc / rc.conf :
Well, the /etc/ipsec.conf file:
We are overloaded, we see that the new interface has appeared, the service has started, we go to the next stage.
Well, it seems to be done with setting up FreeBSD, it's time to start DI-804HV
Go to the web console, go to the VPN tab, enter the name for our VPN connection and click the More button.

We fall into the following settings and fill in all fields according to our initial conditions:
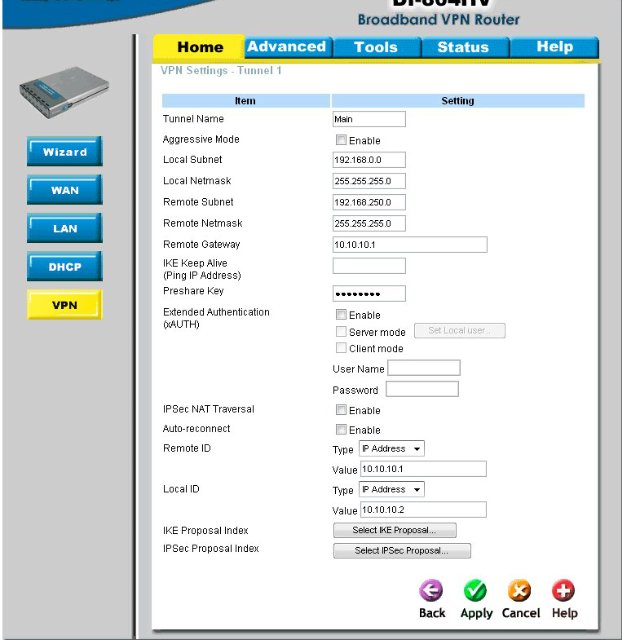
After filling in this data, click Apply and after reloading the page we need to go to the IKE Proposal Index, click on the Select IKE Proposal button and what do we see?

And we see there only 56-bit DES, which corresponds to 1DES, and not 3DES at all, as we need.
At first I did not pay attention to this, because of what I lost half an hour figuring out why the connection was not established. I decided that there might be a problem in the firmware, went to ftp.dlink.ru and found out that I have the latest firmware 1.53RU. By further googling, Google’s cache pulled information that I don’t have 3DES in my firmware, which means I need to roll back to the old one. Found version 1.51 for 2008 ftp.dlink.com/Gateway/di804HV/Firmware/di804HV_firmware_151.BIN , upgraded , or rather, asked for voila and voila - the 3DES we needed appeared on the right page.

Well, then everything is simple - choose DH Group - Group 2 (this is the same as modp1024, if for racoon2), encrypt algorithm - 3DES , Auth algorithm - SHA1 , Life Time = 28800 (it is necessary to ensure that all these parameters coincide with those that we have in /usr/local/etc/racoon/racoon.conf.In the end, do not forget to select the desired Proposal ID in the combo box, click Add to Proposal Index and after that - Apply.
Go back and go to IPSeS Proposal and fill in all the necessary fields there:

We also add this all by analogy, save and go to the Status-> VPN Status tab:
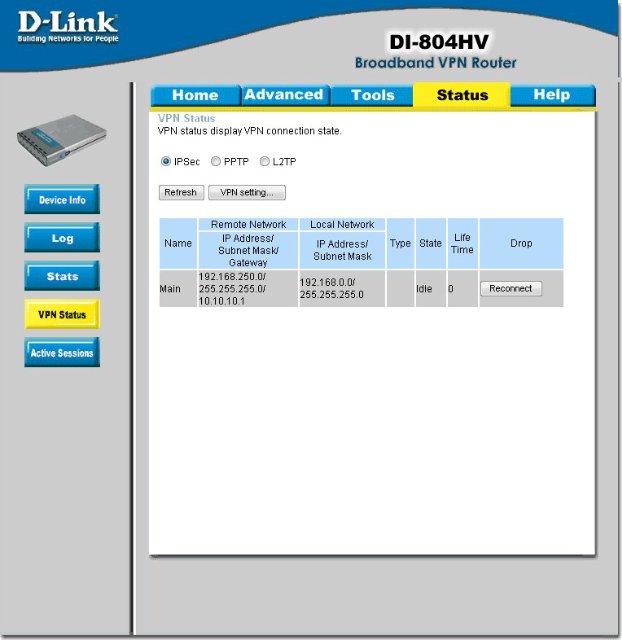
Click Reconnect - and that's it, you can check the operation of the channel:
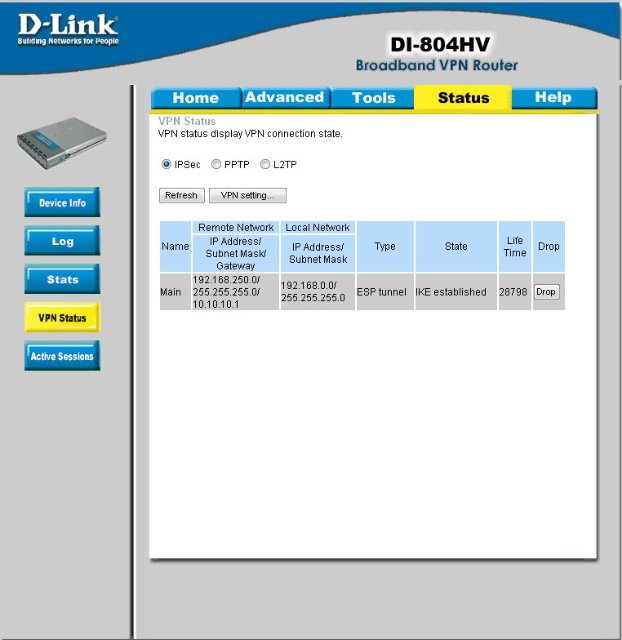
References:
www.opennet.ru
forum.lissyara.su
www.google.ru
PS This article was written only to facilitate the installation of this FreeBSD <-> D-Link DI-804HV bundle, because during the setup process I regularly ran into various problems in the bundle on the forums. Any constructive comments are welcome.
It so happened that when I came to a new job, the server with FreeBSD, which was the gateway to the Internet, fell into my area of responsibility - a mail server and a firewall were running on it. From previous work there was experience with Linux, but FreeBSD had never seen it before. And one of the first tasks of the new work was to set up a connection to a remote office through the Internet, for this purpose they bought a piece of metal D-Link DI-804HV. It was decided to connect this whole economy through IPSEC.
Some changes have been made to the article, based on comments after the publication
So, what we had in stock (addresses here are given solely for example):
internal enterprise network 192.168.250.0/24 ,
internal office network 192.168.0.0/24 ,
Enterprise Router 192.168.250.1
office router 192.168.0.1
external address on FreeBSD 10.10.10.1 ,
external address on the DI-804HV 10.10.10.2 .
All work carried out first on the test machine to avoid any unpleasant moments.
Well, it all started as usual - from reading the documentation on the D-link site and other network resources. The D-Link website has a description of the FreeBSD 4.8 bundle with this piece of hardware, but some of the information there is already outdated, as it turned out later.
I started my work with rebuilding the kernel, including the necessary options — the kernel configs are in / usr / src / sys / i386 / conf , I copied GENERIC to IPSEC and started making changes.
')
Since I have FreeBSD 9, the changes are as follows:
options IPSEC
device crypto
If the version is less than 7 (as I understood from the discussion in the internet), the following is necessary:
options IPSEC
options IPSEC_ESP
options IPSEC_DEBUG # ,
I rebuilt the kernel with the commands:
make buildkernel KERNCONF=IPSEC
make installkernel KERNCONF=IPSEC
where IPSEC is my kernel configuration name.
Overloaded the car, checked that it is loaded.
Then proceeded to install the software itself. Before installing, everyone recommends updating ports, in my case it was through the commands:
portsnap fetch
portsnap extract
portsnap update
After that, I started installing the necessary ports. From reading articles in the forum, I realized that I need a racoon, it is located in the ports / usr / ports / security / ipsec-tools . There is also racoon2, but we do not need it, because ikev2 is not supported by DI-804HV.
Install the port through:
make install clean
After installation, go to the / usr / local / etc / racoon directory - if not, then create - and create the racoon.conf configuration file :
freebsd# cat /usr/local/etc/racoon/racoon.conf
path include "/usr/local/etc/racoon";
path pre_shared_key "/usr/local/etc/racoon/psk.txt";
padding
{
maximum_length 20; # maximum padding length.
randomize off; # enable randomize length.
strict_check off; # enable strict check.
exclusive_tail off; # extract last one octet.
}
listen
{
#isakmp ::1 [7000];
isakmp 10.10.10.1 [500];
#admin [7002]; # administrative port for racoonctl.
#strict_address; # requires that all addresses must be bound.
}
# Specify various default timers.
timer
{
# These value can be changed per remote node.
counter 5; # maximum trying count to send.
interval 20 sec; # maximum interval to resend.
persend 1; # the number of packets per send.
# maximum time to wait for completing each phase.
phase1 30 sec;
phase2 15 sec;
}
remote anonymous
{
exchange_mode main,base;
# doi ipsec_doi;
# situation identity_only;
lifetime time 28800 sec;
#my_identifier asn1dn;
#certificate_type x509 "my.cert.pem" "my.key.pem";
#nonce_size 16;
# initial_contact on;
generate_policy on;
proposal {
encryption_algorithm 3des;
hash_algorithm sha1;
authentication_method pre_shared_key;
dh_group 2;
}
proposal_check strict;
}
sainfo anonymous
{
#pfs_group 2;
lifetime time 28800 sec;
encryption_algorithm 3des, cast128, blowfish 448, des, rijndael;
authentication_algorithm hmac_sha1, hmac_md5;
compression_algorithm deflate;
}
Authentication will occur using a shared key (shared_key), which is located in the /usr/local/etc/racoon/psk.txt file:
freebsd# cat /usr/local/etc/racoon/psk.txt
10.10.10.2 123456789q
I would like to note that this file needs to change the attributes of the form 0600 from the root:
freebsd# ls -l /usr/local/etc/racoon/psk.txt
-rw------- 1 root wheel 21 Jan 31 13:55 /usr/local/etc/racoon/psk.txt
Otherwise, then you can understand for a long time why it does not work.
Then make changes to / etc / rc.conf :
racoon_enable="YES"
# , gif0
cloned_interfaces="gif0"
gif_interfaces="gif0"
gifconfig_gif0="10.10.10.1 10.10.10.2"
ifconfig_gif0="inet 192.168.250.1 192.168.0.1 netmask 0xffffffff"
ipsec_enable="YES"
ipsec_file="/etc/ipsec.conf"
Well, the /etc/ipsec.conf file:
flush;
spdflush;
spdadd 192.168.250.0/24 192.168.0.0/24 any -P out ipsec esp/tunnel/10.10.10.1.-10.10.10.2/require;
spdadd 192.168.0.0/24 192.168.250.0/24 any -P in ipsec esp/tunnel/10.10.10.2-10.10.10.1/require;
We are overloaded, we see that the new interface has appeared, the service has started, we go to the next stage.
Well, it seems to be done with setting up FreeBSD, it's time to start DI-804HV
Go to the web console, go to the VPN tab, enter the name for our VPN connection and click the More button.

We fall into the following settings and fill in all fields according to our initial conditions:

After filling in this data, click Apply and after reloading the page we need to go to the IKE Proposal Index, click on the Select IKE Proposal button and what do we see?

And we see there only 56-bit DES, which corresponds to 1DES, and not 3DES at all, as we need.
At first I did not pay attention to this, because of what I lost half an hour figuring out why the connection was not established. I decided that there might be a problem in the firmware, went to ftp.dlink.ru and found out that I have the latest firmware 1.53RU. By further googling, Google’s cache pulled information that I don’t have 3DES in my firmware, which means I need to roll back to the old one. Found version 1.51 for 2008 ftp.dlink.com/Gateway/di804HV/Firmware/di804HV_firmware_151.BIN , upgraded , or rather, asked for voila and voila - the 3DES we needed appeared on the right page.

Well, then everything is simple - choose DH Group - Group 2 (this is the same as modp1024, if for racoon2), encrypt algorithm - 3DES , Auth algorithm - SHA1 , Life Time = 28800 (it is necessary to ensure that all these parameters coincide with those that we have in /usr/local/etc/racoon/racoon.conf.In the end, do not forget to select the desired Proposal ID in the combo box, click Add to Proposal Index and after that - Apply.
Go back and go to IPSeS Proposal and fill in all the necessary fields there:

We also add this all by analogy, save and go to the Status-> VPN Status tab:

Click Reconnect - and that's it, you can check the operation of the channel:

References:
www.opennet.ru
forum.lissyara.su
www.google.ru
PS This article was written only to facilitate the installation of this FreeBSD <-> D-Link DI-804HV bundle, because during the setup process I regularly ran into various problems in the bundle on the forums. Any constructive comments are welcome.
Source: https://habr.com/ru/post/137456/
All Articles