Carberp, Facebook and ddos.plug
We have already written about Carberp more than once, but here again, citizens are notable for their interesting activity. First, last week an interesting thing was noticed by analysts from Trusteer that, with a certain configuration, Carberp began to extort money from infected users for logging into Facebook.

And moreover, he very persistently demanded payment in the amount of 20 Euro through Ukash:
')
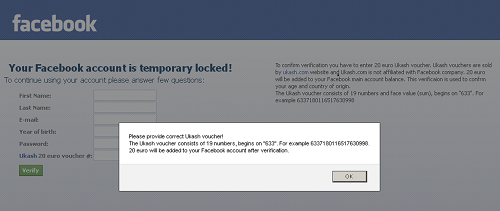
There were thoughts that maybe some new modification, but no, only a special configuration file containing injects for Facebook. This configuration file looks like this:
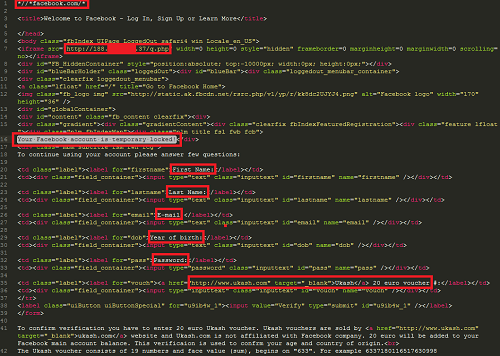
Moreover, this modification did not use the bootkit functionality, but could install it upon request. When analyzing the module being introduced into system processes, it became clear that the code of this library was almost identical to the one that was supplied immediately with the bootkit. This Facebook activity a little embarrassed us, because before that, Carberp didn’t have much love for foreign services and banks. Nevertheless, earlier attacks on the following foreign banks were observed: Bank of America, CityBank, HSBC, CHASE, Nordea. Perhaps this is not all, but at least what was personally seen in the configs was remembered. After continuing the analysis of the situation, an idea emerged about whether Carberp has recently changed its distribution vector. Here are statistics on detections in our region:

As can be seen from the above data, December was the peak month last year, but January is not losing ground (given that the data are from the beginning of this week). Apparently, the Carberp + Blackhole bundle is still very effective. From the point of view of regionalization, our region only strengthened its share in the number of incidents:

And if you look at the directory with fresh web injections, they are still aimed at Russian payment systems and banks:

Well, for dessert, we discovered an interesting plugin (Win32 / Mishigy.AB), which is aimed at implementing DDoS attacks. Can actually not so much: HTTP / HTTPS, GET / POST and download flood. This plugin is written in Delphi and is based mainly on the functionality of the Synapse TCP / IP library component. In some places it is very reminiscent of the Dirt Jumper bot (Win32 / Delf.PYI), which was sensational last year, but its structure is much simpler. For a primitive method of counteraction, the DDoS prevention system uses numerous lines with user agents:

With so many millions of infected users, even such a simple implementation of a DDoS bot can be a very serious weapon.

And moreover, he very persistently demanded payment in the amount of 20 Euro through Ukash:
')

There were thoughts that maybe some new modification, but no, only a special configuration file containing injects for Facebook. This configuration file looks like this:

Moreover, this modification did not use the bootkit functionality, but could install it upon request. When analyzing the module being introduced into system processes, it became clear that the code of this library was almost identical to the one that was supplied immediately with the bootkit. This Facebook activity a little embarrassed us, because before that, Carberp didn’t have much love for foreign services and banks. Nevertheless, earlier attacks on the following foreign banks were observed: Bank of America, CityBank, HSBC, CHASE, Nordea. Perhaps this is not all, but at least what was personally seen in the configs was remembered. After continuing the analysis of the situation, an idea emerged about whether Carberp has recently changed its distribution vector. Here are statistics on detections in our region:

As can be seen from the above data, December was the peak month last year, but January is not losing ground (given that the data are from the beginning of this week). Apparently, the Carberp + Blackhole bundle is still very effective. From the point of view of regionalization, our region only strengthened its share in the number of incidents:

And if you look at the directory with fresh web injections, they are still aimed at Russian payment systems and banks:

Well, for dessert, we discovered an interesting plugin (Win32 / Mishigy.AB), which is aimed at implementing DDoS attacks. Can actually not so much: HTTP / HTTPS, GET / POST and download flood. This plugin is written in Delphi and is based mainly on the functionality of the Synapse TCP / IP library component. In some places it is very reminiscent of the Dirt Jumper bot (Win32 / Delf.PYI), which was sensational last year, but its structure is much simpler. For a primitive method of counteraction, the DDoS prevention system uses numerous lines with user agents:

With so many millions of infected users, even such a simple implementation of a DDoS bot can be a very serious weapon.
Source: https://habr.com/ru/post/137309/
All Articles