Batniki against exploits
Good day, dear% USERNAME%. My name is Sergey Golovanov, and I still am the leading virus analyst at Kaspersky Lab. I understand that the name of this post in the company's corporate blog can cause laughter, sadness, and some even have an epileptic seizure, but let me explain everything.
I understand that for all batch files look like something very simple and since AUTOEXEC.BAT is almost forgotten, at the same time, exploits, if you are certainly not a professional vulnerability researcher, look very difficult and almost implausible, especially for some developers. But! In this post I will try to turn these ideas around and tell you that everything seems to be the opposite. The batniki are a little lighter and stronger in terms of brainfuck’s functionality, and the exploits are no worse than sorting by the bubble on basic.

(Caution! 3 MB of illustrated stream of consciousness and a bunch of scripts)
')
I came across a box with Windows 7 x64 with minimal system requirements of 2 GB of RAM! And here I thought, really, in all these gigabytes there is no pair of kilobytes of code that could protect users from such misfortunes as exploits and Drive-by ? This scourge of all OS from MS is already five years old! Should there be means for at least some protection? But how to use them, and even standard means? With the help of batch file. But as? To understand this, you need to read this sheet to the end. eight)
In the simplified theory of the exploitation of exploits, everything looks like this: “something looked somewhere, something was sent somewhere, something started somewhere”. In real life, it often looks like this: when a user is browsing the Internet, he ends up on an honestly hacked site, where he is given, along with useful information, either JavaScript or a redirect to JavaScript, which, by analyzing USER-AGENT, information about plugins, etc. gives the user an exploit that will work for the user. After that, the Trojan is downloaded to the user's machine, it starts up, is registered in the system, and starts doing its dirty work.

Google's Anti-Malware Team's Drive-By Picture for Visuals,
reading in the language of the likely opponent
(-SH. Yulia, please correct the following sentence within the meaning of it so that it is understandable and delete this comment. Editor. By the meaning of ??? Yes, I already don’t understand anything after “allocating my memory”. comment.)
If you dig a little deeper, it turns out that in such exploit packs often (almost always) the payload allocates itself memory in the victim process, searches for the necessary system functions, saves the file from the Internet to the locale and does CreateProcess or very rarely - ShellExecute, while privilege elevation problems are shifted to what is downloaded. Everything is in principle simple and clear. And what to do with it? Grabthe fifth point for weak points! There is one weak spot in this whole scheme: it does not matter which application was pierced, the main thing is to launch the file with the Trojan. Thus, it turns out that we simply need to ensure that the extra files on the user's computer do not run, and this must be done by standard means.
In Windows 7, there are several ways to limit or extend the work of programs. Perhaps the most popular means are the ACL and all sorts of politicians.
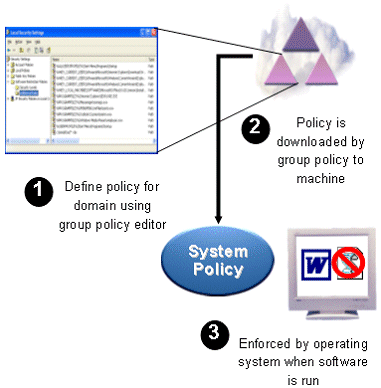
Visual SRP (Software Restriction Policies) from Microsoft
In principle, it is not a secret to anyone that you can create a special user account, assign special rights to it in the system and drive potentially vulnerable applications under it. Five minutes of taxiing with the mouse - and everything is ready. The problem is that a rare user will do this, especially if admins need to do this on all machines on the network. Therefore, let's try to make a batch file, in which we will do approximately the same, only better, and even so that it would be convenient to use.
Total: our batch file must create a user with standard rights, then modify these rights to run only certain software and, finally, make it transparent and convenient for the user. Let's start with ...
The username and password here are for example only, they will have to be diluted with% random% 's so that it does not turn out that all of the batch file users have the same usernames and passwords on the machines. And then it turns out a sort of Backdoor.Bat.Hren.a, it still has to be detected ...)))
In an amicable way, AppLocker needs to assign permissions to execute using PowerShell, for example:
However, all this cunning crap "is only available in the Ultimate and Enterprise versions of Windows 7." Therefore, as an alternative to the Home version of Windows 7, you can use Parental Control ( link to the forum - I'm not joking), which stores information about which programs you can run in:
This means that politicians are in the firebox, for it is inconvenient, we will use ACLs, especially since, starting with Vista, a wonderful ICACLS team has appeared. In principle, everything that is written further can be projected on XP using XCACLS, but by default there is no such command in XP, and it is included only in the Resource Kit.
In total, in Windows 7, first we will remove the user from the default group in order to limit its ability thanks to group permissions to create files anywhere:
And now let's say that, dear user,you are a loser , you are not allowed to run files from a profile, the only place where you are allowed to create files.
(-Editor. You would still be here to ask me to check something and correct it. Comments, do not forget to kill.)
The parameters “(OI) (IO)” seem to tell us that all the files in the specified folder inherit the rights of the parent, which, in fact, Deny Execute. We check that the rights set out work:
Total: Notepad.exe from the Windows folder works, and if you copy it to the TEMP folder and run it, ACCESS IS DENIED. All OK. Go ahead.
For usability, we need to provide transparent launch support for the maximum number of different browsers under the new user. I propose to do this as follows:
1. Copy the current user's browser profile to the new user. For example, for Firefox like this:
2. Create a file in the folder with the VBS browser in which to register the launch of the Runas browser. You need to do this through VBS to bypass the restriction on receiving a password in STDIN for Runas. Perfect Microsoft did it to increase the security of its OS . As usual, security remained in question, and hemorrhoids increased. The VBS file will look like this, for example:
Little comment. On the Internet, they write that Sendkeys is missing or forbidden in some versions, but on Windows 7 Professional, Ultimate and Home everything works. We continue.
3. Create a shortcut to the newly created VBS file with a browser icon.
4. Replace the new label with all the existing user labels on browsers. Joke. We put the shortcuts in a separate folder on the desktop, and then let the user decide for himself.
Total like everything is OK, it remains all to comb and test.
Well, now let's try how it all works in the wild:
1. Turn off the antivirus and downgrade, for example, JAVA (the couple immediately became uncomfortable for me).
2. Copy-paste batch file from listing.
3. Save it as saferun.bat, take a deep breath and click on it twice.
4. The console blinks and the explorer window opens. We look at the window with labels and think a lot.
5. Choose any browser. We go to Youtube, check that everything works, clicks, etc.
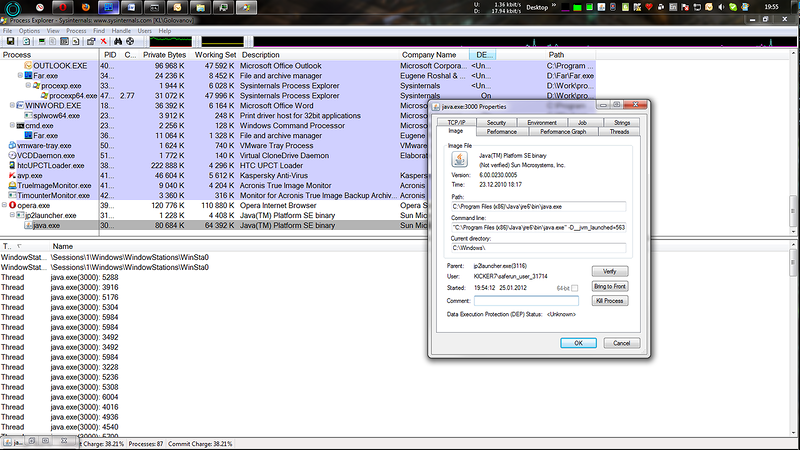
6. Now we go to Google and look for the “Most Popular Runet Browser” (this is what my sister showed me how to download a free porn blocker). We click on several links, and our computer begins to pop suspiciously. We are waiting for a minute. It seems nothing terrible happened. We look in Process Explorer and see that our browser has launched JAVA.exe, which successfully inherited our new user.
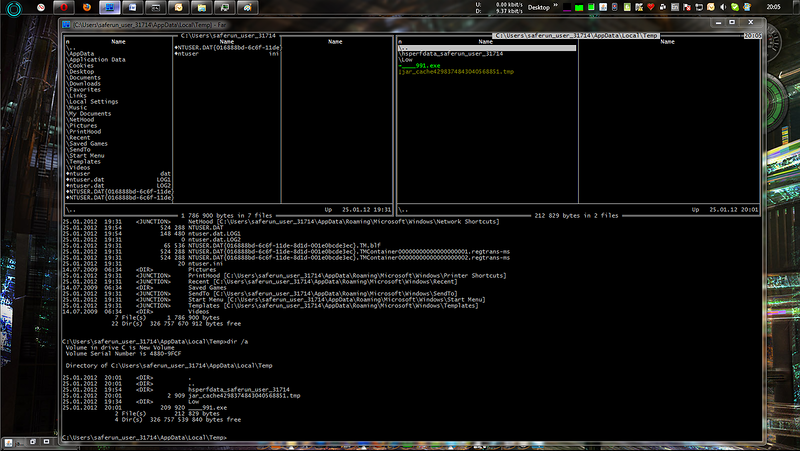
7. Now go to the temporary directory of the new user and see the following there ...
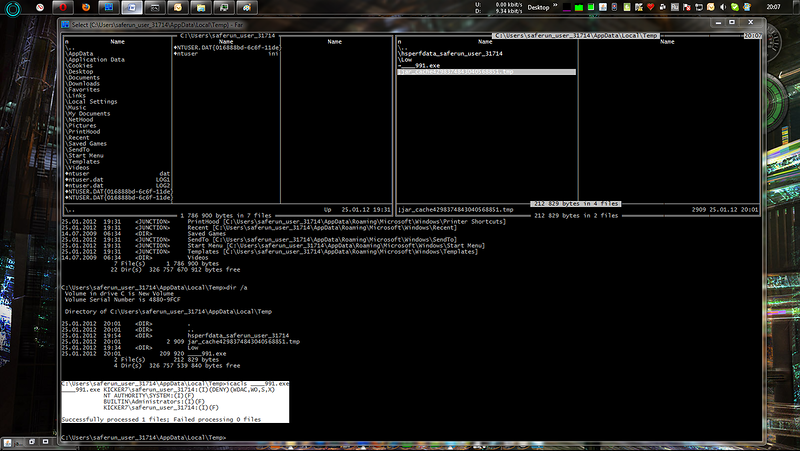
8. Check the rights to the file "____ 991.exe"
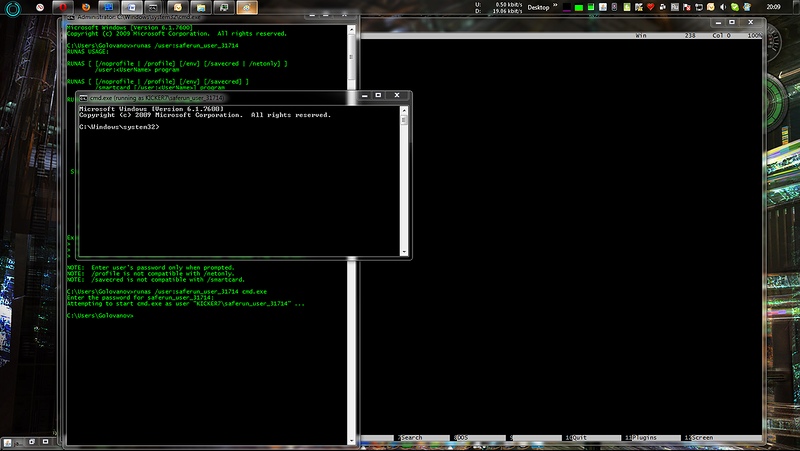
9. Disable cmd.exe under the created user. The password for it can be viewed, for example, in the VBS script next to the browser's EXE
10. Make cd% temp% in the new console and write ". \ ____ 991.exe". Hit Enter!
11. URA-URA !!! This is victory.

12. Who are interested in the details, then
If this file were launched, we would see funny pictures and a request to work with the payment terminal.

In total, our batch file will be very useful for protecting against Drive-by attacks and exploits when working with Windows 7 both from under the admin and as a simple user. Yes, he has a theoretical limit on payloads with elevated privileges, but such a benefit in the wild is rare. Pros when working with a batch file - you can quickly edit it and add support for new programs, such as email clients, office programs, etc. Adjustment, flexibility, coolness and coolness are very important, and we in LK understand this very well.
Thank you very much for reading this stream of consciousness of the author to the end and have never pressed a minus. 8) Good luck!
PS This batch file has nothing to do with SafeBrowser, which is a part of LC products.
PPP. The batch file creates a very convenient Uninstall - just in case something suddenly went wrong.
Ppps As usual in comments a friendly user k1k hangs out, who pretends to be the author of the article. The way it is. Thank!
I understand that for all batch files look like something very simple and since AUTOEXEC.BAT is almost forgotten, at the same time, exploits, if you are certainly not a professional vulnerability researcher, look very difficult and almost implausible, especially for some developers. But! In this post I will try to turn these ideas around and tell you that everything seems to be the opposite. The batniki are a little lighter and stronger in terms of brainfuck’s functionality, and the exploits are no worse than sorting by the bubble on basic.

(Caution! 3 MB of illustrated stream of consciousness and a bunch of scripts)
')
How did I get to this?
I came across a box with Windows 7 x64 with minimal system requirements of 2 GB of RAM! And here I thought, really, in all these gigabytes there is no pair of kilobytes of code that could protect users from such misfortunes as exploits and Drive-by ? This scourge of all OS from MS is already five years old! Should there be means for at least some protection? But how to use them, and even standard means? With the help of batch file. But as? To understand this, you need to read this sheet to the end. eight)
Theory
In the simplified theory of the exploitation of exploits, everything looks like this: “something looked somewhere, something was sent somewhere, something started somewhere”. In real life, it often looks like this: when a user is browsing the Internet, he ends up on an honestly hacked site, where he is given, along with useful information, either JavaScript or a redirect to JavaScript, which, by analyzing USER-AGENT, information about plugins, etc. gives the user an exploit that will work for the user. After that, the Trojan is downloaded to the user's machine, it starts up, is registered in the system, and starts doing its dirty work.

Google's Anti-Malware Team's Drive-By Picture for Visuals,
reading in the language of the likely opponent
(-SH. Yulia, please correct the following sentence within the meaning of it so that it is understandable and delete this comment. Editor. By the meaning of ??? Yes, I already don’t understand anything after “allocating my memory”. comment.)
If you dig a little deeper, it turns out that in such exploit packs often (almost always) the payload allocates itself memory in the victim process, searches for the necessary system functions, saves the file from the Internet to the locale and does CreateProcess or very rarely - ShellExecute, while privilege elevation problems are shifted to what is downloaded. Everything is in principle simple and clear. And what to do with it? Grab
Standard tools
In Windows 7, there are several ways to limit or extend the work of programs. Perhaps the most popular means are the ACL and all sorts of politicians.

Visual SRP (Software Restriction Policies) from Microsoft
In principle, it is not a secret to anyone that you can create a special user account, assign special rights to it in the system and drive potentially vulnerable applications under it. Five minutes of taxiing with the mouse - and everything is ready. The problem is that a rare user will do this, especially if admins need to do this on all machines on the network. Therefore, let's try to make a batch file, in which we will do approximately the same, only better, and even so that it would be convenient to use.
Batnik
Total: our batch file must create a user with standard rights, then modify these rights to run only certain software and, finally, make it transparent and convenient for the user. Let's start with ...
1. Create a user. Freebie.
net user saferun_user Passw0rd /addThe username and password here are for example only, they will have to be diluted with% random% 's so that it does not turn out that all of the batch file users have the same usernames and passwords on the machines. And then it turns out a sort of Backdoor.Bat.Hren.a, it still has to be detected ...)))
2. Modify rights. Uh ... and here there are already problems
In an amicable way, AppLocker needs to assign permissions to execute using PowerShell, for example:
PS C:\> Get-ApplockerFileInformation -Directory 'C:\Program Files (x86)\Adobe\' -Recurse -FileType Exe | New-ApplockerPolicy -RuleType Publisher -User SafeRun_user -RuleNamePrefix Adobe -Optimize -Xml > Adoby.xml
PS C:\> Set-AppLockerPolicy –XmlPolicy Adoby.xmlHowever, all this cunning crap "is only available in the Ultimate and Enterprise versions of Windows 7." Therefore, as an alternative to the Home version of Windows 7, you can use Parental Control ( link to the forum - I'm not joking), which stores information about which programs you can run in:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Parental Controls\Users\UID\App RestrictionsThis means that politicians are in the firebox, for it is inconvenient, we will use ACLs, especially since, starting with Vista, a wonderful ICACLS team has appeared. In principle, everything that is written further can be projected on XP using XCACLS, but by default there is no such command in XP, and it is included only in the Resource Kit.
In total, in Windows 7, first we will remove the user from the default group in order to limit its ability thanks to group permissions to create files anywhere:
net localgroup users saferun_user /deleteAnd now let's say that, dear user,
icacls %USERPROFILE% /deny saferun_user:(OI)(IO)(WDAC,WO,X)(-Editor. You would still be here to ask me to check something and correct it. Comments, do not forget to kill.)
The parameters “(OI) (IO)” seem to tell us that all the files in the specified folder inherit the rights of the parent, which, in fact, Deny Execute. We check that the rights set out work:
C:\Users\Golovanov>runas /user: saferun_user cmd.exe
Enter the password for saferun_user:
Attempting to start cmd.exe as user “saferun_user" ...
C:\Windows\system32> cd %temp%
C:\Users\saferun_user\AppData\Local\Temp>%windir%notepad.exe
C:\Users\saferun_user\AppData\Local\Temp>copy c:\windows\notepad.exe .
1 file(s) copied.
C:\Users\saferun_user\AppData\Local\Temp>.\notepad.exe
Access is denied.Total: Notepad.exe from the Windows folder works, and if you copy it to the TEMP folder and run it, ACCESS IS DENIED. All OK. Go ahead.
3. Usability
For usability, we need to provide transparent launch support for the maximum number of different browsers under the new user. I propose to do this as follows:
1. Copy the current user's browser profile to the new user. For example, for Firefox like this:
xcopy /E /I /C /Y /Q /H /R %APPDATA%\Mozilla\* C:\Users\saferun_user\AppData\Roaming\Mozilla\2. Create a file in the folder with the VBS browser in which to register the launch of the Runas browser. You need to do this through VBS to bypass the restriction on receiving a password in STDIN for Runas. Perfect Microsoft did it to increase the security of its OS . As usual, security remained in question, and hemorrhoids increased. The VBS file will look like this, for example:
Option explicit
Dim oShell
set oShell= Wscript.CreateObject("WScript.Shell")
oShell.Run "RunAs /noprofile /user:saferun_user Firefox.exe"
WScript.Sleep 1000
oShell.Sendkeys "Passw0rd"
oShell.Sendkeys "{ENTER}"
Wscript.QuitLittle comment. On the Internet, they write that Sendkeys is missing or forbidden in some versions, but on Windows 7 Professional, Ultimate and Home everything works. We continue.
3. Create a shortcut to the newly created VBS file with a browser icon.
Set oWS = WScript.CreateObject("WScript.Shell")
sLinkFile = "C:\firefox_saferun.LNK"
Set oLink = oWS.CreateShortcut(sLinkFile)
oLink.TargetPath = "C:\Program Files (x86)\Mozilla Firefox\firefox.vbs"
oLink.IconLocation = "C:\Program Files (x86)\Mozilla Firefox\firefox.exe,0"
oLink.WorkingDirectory = "C:\Program Files (x86)\Mozilla Firefox\"
oLink.Save4. Replace the new label with all the existing user labels on browsers. Joke. We put the shortcuts in a separate folder on the desktop, and then let the user decide for himself.
Batch file listing
Total like everything is OK, it remains all to comb and test.
::Writed by: Sergey.Golovanov at kaspersky.com for habrahabr.ru @echo on @Echo This batch file will create a new user for browsers with no rights to run downloaded from Internet files. Pause ::Setup new user:: set safeusername=saferun_user_%random% set safepassword=%random%Ai%random% echo Login: %safeusername% echo Password: %safepassword% net user %safeusername% /delete del Browserlist4saferun.txt net user %safeusername% %safepassword% /add ::init new user profile:: echo Option explicit > init_new_user_profile.vbs echo Dim oShell >> init_new_user_profile.vbs echo set oShell= Wscript.CreateObject("WScript.Shell") >> init_new_user_profile.vbs echo oShell.Run "RunAs /profile /user:%safeusername% ping" >> init_new_user_profile.vbs echo WScript.Sleep 1000 >> init_new_user_profile.vbs echo oShell.Sendkeys "%safepassword%" >> init_new_user_profile.vbs echo oShell.Sendkeys "{ENTER}" >> init_new_user_profile.vbs echo Wscript.Quit >> init_new_user_profile.vbs call cscript init_new_user_profile.vbs ping -n 10 localhost >> nul del init_new_user_profile.vbs ::Setup privileges for new user:: net localgroup users %safeusername% /delete icacls c:\users\%safeusername%\ /deny %safeusername%:(OI)(IO)(WDAC,WO,X) ::Setup browsers:: :FindOpera if exist %APPDATA%\Opera\ xcopy /E /I /C /Y /Q /H /R %APPDATA%\Opera\* C:\Users\%safeusername%\AppData\Roaming\Opera\ if exist "%Programfiles%\Opera\Opera.exe" goto run4opera if exist "%Programfiles(x86)%\Opera\Opera.exe" goto run4operax86 Goto FindFireFox :run4opera echo Opera^|%Programfiles%\Opera>> Browserlist4saferun.txt Goto FindFireFox :run4operax86 Set Browsername=Opera echo Opera^|%Programfiles(x86)%\Opera>> Browserlist4saferun.txt Goto FindFireFox :FindFireFox if exist %APPDATA%\Mozilla\ xcopy /E /I /C /Y /Q /H /R %APPDATA%\Mozilla\* C:\Users\%safeusername%\AppData\Roaming\Mozilla\ if exist "%Programfiles%\Mozilla Firefox\Firefox.exe" goto run4Firefox if exist "%Programfiles(x86)%\Mozilla Firefox\Firefox.exe" goto run4Firefoxx86 Goto FindChrome :run4Firefox echo Firefox^|%Programfiles%\Mozilla Firefox>> Browserlist4saferun.txt Goto FindChrome :run4Firefoxx86 echo Firefox^|%Programfiles(x86)%\Mozilla Firefox>> Browserlist4saferun.txt Goto FindChrome :FindChrome If exist %LOCALAPPDATA%\Google\Chrome\Application\chrome.exe goto run4chrome Goto FindIE :run4chrome ::// Can work for some versions of Chrome by not stable. Dissabled for performance. ::xcopy /E /I /C /Y /Q /H /R %LOCALAPPDATA%\Google\Chrome\* C:\Users\%safeusername%\AppData\Local\Google\Chrome\ ::for /r C:\Users\%safeusername%\AppData\Local\Google\Chrome\ %%C in (*.exe) do icacls %%C /grant %safeusername%:(X) ::for /r C:\Users\%safeusername%\AppData\Local\Google\Chrome\ %%C in (*.dll) do icacls %%C /grant %safeusername%:(X) ::echo Chrome^|C:\Users\%safeusername%\AppData\Local\Google\Chrome\Application\>> Browserlist4saferun.txt Goto FindIE :FindIE ::// TODO A lot of XCOPYs if exist "%LOCALAPPDATA%\Microsoft\Internet Explorer" ( xcopy /E /I /C /Y /Q /H /R "%USERPROFILE%\Favorites\*" "C:\Users\%safeusername%\Favorites\" xcopy /E /I /C /Y /Q /H /R "%LOCALAPPDATA%\Microsoft\Internet Explorer\*" "C:\Users\%safeusername%\AppData\Local\Microsoft\Internet Explorer\" xcopy /E /I /C /Y /Q /H /R "%LOCALAPPDATA%\Microsoft\Windows\History\*" "C:\Users\%safeusername%\AppData\Local\Windows\History\" xcopy /E /I /C /Y /Q /H /R "%APPDATA%\Roaming\Microsoft\Windows\Cookies\*" "C:\Users\%safeusername%\AppData\Roaming\Microsoft\Windows\Cookies\" ) if exist "%Programfiles(x86)%\Internet Explorer\iexplore.exe" goto run4iex86 if exist "%Programfiles%\Internet Explorer\iexplore.exe" goto run4ie :run4iex86 echo IExplore^|%Programfiles(x86)%\Internet Explorer>> Browserlist4saferun.txt goto MakeLinks :run4ie echo IExplore^|%Programfiles%\Internet Explorer>> Browserlist4saferun.txt ::Make links:: :MakeLinks rd /s /q %USERPROFILE%\Downloads\Browser rd /s /q %USERPROFILE%\Desktop\SafeLinks mklink /d %USERPROFILE%\Downloads\Browser C:\Users\%safeusername%\Downloads mkdir %USERPROFILE%\Desktop\SafeLinks echo on For /f "tokens=1,2 delims=|" %%A in (Browserlist4saferun.txt) do ( echo Option explicit > "%%B\%%A.vbs" echo Dim oShell >> "%%B\%%A.vbs" echo set oShell= Wscript.CreateObject^("WScript.Shell"^) >> "%%B\%%A.vbs" echo oShell.Run "RunAs /user:%safeusername% %%A.exe" >> "%%B\%%A.vbs" echo WScript.Sleep 1000 >> "%%B\%%A.vbs" echo oShell.Sendkeys "%safepassword%" >> "%%B\%%A.vbs" echo oShell.Sendkeys "{ENTER}" >> "%%B\%%A.vbs" echo Wscript.Quit >> "%%B\%%A.vbs" echo Set oWS = WScript.CreateObject^("WScript.Shell"^) > "%USERPROFILE%\Desktop\SafeLinks\%%A.lnk.vbs" echo sLinkFile = "%USERPROFILE%\Desktop\SafeLinks\%%A_saferun.LNK" >> "%USERPROFILE%\Desktop\SafeLinks\%%A.lnk.vbs" echo Set oLink = oWS.CreateShortcut^(sLinkFile^) >> "%USERPROFILE%\Desktop\SafeLinks\%%A.lnk.vbs" echo oLink.TargetPath = "%%B\%%A.vbs" >> "%USERPROFILE%\Desktop\SafeLinks\%%A.lnk.vbs" echo oLink.IconLocation = "%%B\%%A.exe,0" >> "%USERPROFILE%\Desktop\SafeLinks\%%A.lnk.vbs" echo oLink.WorkingDirectory = "%%B\" >> "%USERPROFILE%\Desktop\SafeLinks\%%A.lnk.vbs" echo oLink.Save >> "%USERPROFILE%\Desktop\SafeLinks\%%A.lnk.vbs" ) for /r %USERPROFILE%\Desktop\SafeLinks\ %%p in (*.vbs) do cscript %%p for /r %USERPROFILE%\Desktop\SafeLinks\ %%v in (*.vbs) do del %%v :: Open Explorer with links:: explorer %USERPROFILE%\Desktop\SafeLinks\ :: Create Uninstall:: echo @echo off > uninstall_%~n0.bat echo net user %safeusername% /del >> uninstall_%~n0.bat echo rd /s /q %USERPROFILE%\Downloads\Browser >> uninstall_%~n0.bat echo rd /s /q %USERPROFILE%\Desktop\SafeLinks >> uninstall_%~n0.bat echo rd /s /q C:\Users\%safeusername%\ >> uninstall_%~n0.bat echo For /f "tokens=1,2 delims=|" %%%%A in (Browserlist4saferun.txt) do del "%%%%B\%%%%A.vbs" >> uninstall_%~n0.bat echo del Browserlist4saferun.txt >> uninstall_%~n0.bat echo del %%0 >> uninstall_%~n0.bat :Exit Testing
Well, now let's try how it all works in the wild:
1. Turn off the antivirus and downgrade, for example, JAVA (the couple immediately became uncomfortable for me).
2. Copy-paste batch file from listing.
3. Save it as saferun.bat, take a deep breath and click on it twice.
4. The console blinks and the explorer window opens. We look at the window with labels and think a lot.
5. Choose any browser. We go to Youtube, check that everything works, clicks, etc.
6. Now we go to Google and look for the “Most Popular Runet Browser” (this is what my sister showed me how to download a free porn blocker). We click on several links, and our computer begins to pop suspiciously. We are waiting for a minute. It seems nothing terrible happened. We look in Process Explorer and see that our browser has launched JAVA.exe, which successfully inherited our new user.
7. Now go to the temporary directory of the new user and see the following there ...
8. Check the rights to the file "____ 991.exe"
9. Disable cmd.exe under the created user. The password for it can be viewed, for example, in the VBS script next to the browser's EXE
10. Make cd% temp% in the new console and write ". \ ____ 991.exe". Hit Enter!
11. URA-URA !!! This is victory.

12. Who are interested in the details, then
C:\Users\saferun_user_31714\AppData\Local\Temp>d:\md5.exe ____991.ex ____991.ex : 04DA16B5447D8F2B4BD23AFD469FB153 If this file were launched, we would see funny pictures and a request to work with the payment terminal.
Instead of conclusion

In total, our batch file will be very useful for protecting against Drive-by attacks and exploits when working with Windows 7 both from under the admin and as a simple user. Yes, he has a theoretical limit on payloads with elevated privileges, but such a benefit in the wild is rare. Pros when working with a batch file - you can quickly edit it and add support for new programs, such as email clients, office programs, etc. Adjustment, flexibility, coolness and coolness are very important, and we in LK understand this very well.
Thank you very much for reading this stream of consciousness of the author to the end and have never pressed a minus. 8) Good luck!
PS This batch file has nothing to do with SafeBrowser, which is a part of LC products.
PPP. The batch file creates a very convenient Uninstall - just in case something suddenly went wrong.
Ppps As usual in comments a friendly user k1k hangs out, who pretends to be the author of the article. The way it is. Thank!
Source: https://habr.com/ru/post/137304/
All Articles