Symantec experts have discovered 13 popular applications in the Android Market with the Android.Counterclank malware
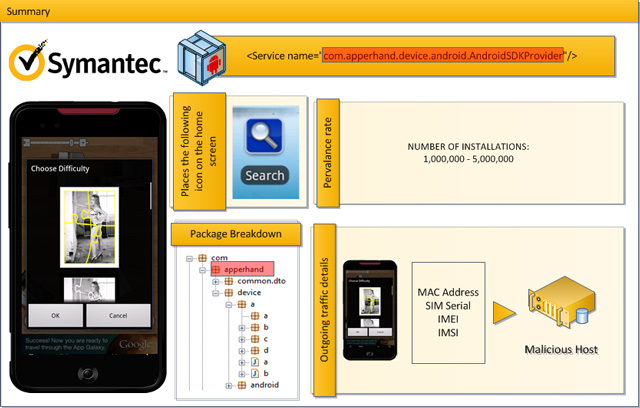
Yesterday, Symantec reported on the discovery by specialists of this company of several popular applications with the Android.Counterclank malware enabled. According to analysts, this could be a targeted campaign by virus writers distributing Android.Counterclank. Applications with malware included in the distribution were downloaded by 5 million people, so this is currently the largest known attempt to spread malware in the Android Market.
As mentioned above, Android.Counterclank was found in 13 different applications from renowned publishers. Applications - from “Sexy Girls Puzzle” to “Counter Strike Ground Force”. These applications were still available at the end of Friday. Kevin Haley, head of the Symantec Security Response Team, said applications are unlikely to be downloaded by real publishers. At the same time, these are not so-called repackaged applications, specialists from Symantec have seen this software before.
')

Earlier, the distributors of malicious software for Android used the tactics of re-selecting applications from well-known publishers, with further download to the Market. Deceived users downloaded applications from developers who seem to be trusted, and received malicious software for their mobile device. Now the tactics are a little different, as we see. According to preliminary calculations, these 13 applications were downloaded from 1 to 5 million times. And this, apparently, is the largest campaign for the distribution of malicious software in the entire history of the Android Market (in any case, according to experts from Symantec). It is clear that any tablets and phones based on Android OS, including the best smartphones in 2012, are subject to this kind of attack.
Android.Counterclank is a trojan that, when installed on a mobile device, collects all sorts of information, including the device manufacturer, user bookmarks, and so on. In addition, this malware modifies the start page of the browser. Malefactors, using this software, insert any advertizing on the compromised devices, and earn money. Despite the fact that this software requires quite a few access levels, few users pay attention to this, because the application, such as from a well-known publisher.
Via computerworld
Source: https://habr.com/ru/post/137187/
All Articles