Pictographic password. Experiment
Text passwords have long been common, and their problems are not new . With the growth of computing abilities of computers, the requirements for the length and frequency of changing passwords only increase, and the human ability to memorize nonsense character sets is growing at a not so impressive pace. Biometric methods do not cause confidence yet, and how is biofeedback better than text passwords, except that they cannot be changed and that they do not allow anonymity? But it is not about text passwords that will be discussed and not about the flaws in biometrics, consider one of the alternative ways of setting and entering a password that has become especially interesting with the proliferation of touch devices. The basis of the method is that a person easily recognizes visual images, while for a machine it is painful. This image of the password can be stored and transferred between people, but between computers in any way or too expensive.
Many such systems must have been buried by history, I know only a few.
Background Draw a Secret requires the user to draw a picture, then its similarity with the standard is evaluated. One of the implementations of the idea of an autograph, which in ancient times people put on paper. The recently introduced Picture Password by Microsoft in Windows 8 requires the user to draw dots, vectors and circles on the background of the photo, and the system will compare them with the standard. Two methods were proposed by the Graphical Password project in 2006. — In PassPoints, you need to mark points in the photo, and the server will compare them with those marked during registration. But in ConvexHull, the user gets a picture with a set of icons arranged in a random order and points to a point on it. The server, remembering where the icons are, calculates whether the entered point is between the three icons specified during registration. The procedure is repeated several times, which increases safety and trains patience. There is also Winfrasoft Pin + , where you need to mark the pattern selected during authorization in the matrix of numbers. I admit, I still do not understand how to use it.
')
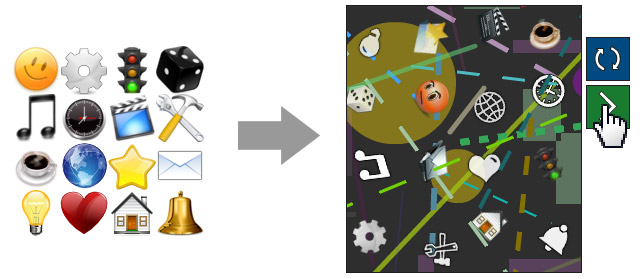
The pictographic password, and simpler — the picto password that I suggest, works without any special knowledge.
- Upon receiving a request, the server generates an image, placing on it icons from a set in a random order. Set, for example, may consist of 16 icons of common objects. The image is distorted, the pictograms change, like letters in a regular captcha, in every way opposing machine recognition.
- The server remembers the coordinates of the icon centers and sends the picture to the user.
- The user sequentially clicks the icons by entering the sequence selected during registration.
- From the coordinates of the clicks formed an array of points that is sent to the server.
- The server, estimating the distance of the sent points to the saved ones, determines the entered sequence of pictograms.
- After receiving the sequence, the system with the picto-password works the same as with a regular password — calculates the hash and compares it with the content in the database.
Looking at the script, it is clear that the password can be stored only in one place — in the head of a person and can be transmitted only from person to person. Such a password for hacking will require a significant improvement in the technology of classification of images, because the pictograms according to the style are much more complicated than letters and numbers. Then, if there is no algorithm capable of recognizing icons on the image with acceptable speed, quality and cost, the following is true.
- The only way to choose a password is manual search, and the time required for such a search is measured in man-hours. For example, it will take 90 hours to try a four-digit password with a 5 second attempt time, and although a cluster of 10,000 Indians can solve this problem in half an hour (in the worst case) it will cost about $ 50 ($ 1 for 1000 attempts), but for a five-digit one already $ 800. The target attack will not survive, but will make a massive one too expensive.
- An attacker cannot log in automatically, even if he has a password, which seriously complicates the massive use of fake or captured system accounts;
- If the password cannot be communicated quickly and cannot be transferred to the machine, the reliability of short passwords increases. To send or save a password you need to draw it or somehow describe it in words, which reduces the effectiveness of phishing attacks aimed at luring a password.
- To intercept a password with a sniffer, trojan, or spying, but at least scanning the cerebral cortex, again, it will take a person to recognize the intercepted password.
- According to the complexity of implementation, the server load and the impenetrability of the picto-password, it is comparable to a system where a text password is used and a captcha is required at the same time, but safer, more convenient to enter and easier to remember.
I suggest you to take part in the experiment. Challenge yourself to a demo flash app. The program collects statistics: the number of attempts, the ratio of the number of incorrect password entries to the number of attempts, the average speed of the test. It would be nice if not only Habr's visitors will test the system — more interesting is how much it seems convenient and understandable to ordinary users. How to get decent statistics will definitely write. Maybe the picto-password is not at all what is needed, but some kind of human, non-digitized, way of manipulating objects is used to access systems, it seems to me necessary.
Ps Also, the method is suitable for protection against bots instead of alphanumeric captcha. It may look like this: you should click on the bottom image those icons that are on the top.

upd: The experiment is completed, read the results here.
Source: https://habr.com/ru/post/136918/
All Articles