Passive XSS in Yandex.Money
Yandex, Money, two trunks XSS
The story is like that. On one site I saw the news that the site of Mr. Freeman was updated, I decided to check out.
I went to it and saw the Yandex.Money donation field there. According to the old habit of a seasoned Scriptikdie, he inserted the imperishable
[script] alert ("") [/ script] and clicked send:
')

I was transferred to Yandex.Money, and this picture appeared to me:
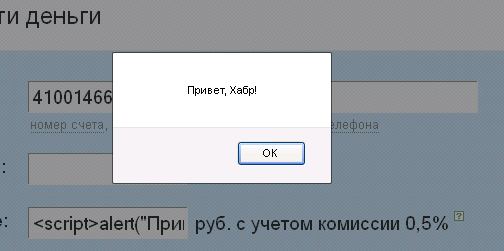
“Cool!” - I thought, and I created this question on Habré. Then he wrote to the Yandex.Money support service and one habraiser related to Yandex.
Well, I decided to continue to continue to deal with this opportunity.
The field where the script was recorded was protected by filtering, so all the scripts except the text alert had to be encoded in the URL code, otherwise they were not executed. What I did on this site.
By the way, at this time I received a response from the support of Yandex, something like this: "Everything is in order, I just checked in Firefox, there are no jambs."
“Cool!” I thought again, and executed the encoded script that issued my cookies:

After that, I sent another letter to the caliper with screenshots of three browsers where the alert is executed.
Then I registered in the sniffer, coded the script, the script was executed - the cookies came.
And after about half an hour, the vulnerability was covered. The caliper has not answered anything yet.
So it goes.
UPD: Received a letter from the caliper confirming the correction of the vulnerability.
Source: https://habr.com/ru/post/136531/
All Articles