We investigate protection on the basis of certificates (utm5)
This article does not tell about how to make a crack or keygen. There will be a simple study of the protection of a fairly expensive software product.
It so happened that the choice fell on utm5.
The goal was to understand what protection method this software uses, especially since this complex of programs is available both under windows and under linux / freebsd.
I took the unix version, since it was the first experience of researching programs not under windows.
And we will use all the same IDA launched from under wine.
Assume that utm5 is loaded, there is a demo key, everything is set up and working. Well, let's get started:
')
We take the core of the system (utm5_core) and feed it with IDA. Let's drink some tea and go back to the computer where IDA will happily report that it has fully analyzed the file.
We look at the reg.sql file, and we come to the conclusion that the kernel of the system reads the license from mysql.
Carefully looking at the data, we decide that we are interested in the "hash1, hash2, data" fields.
Do a search for the string hash1 in strings, we find:
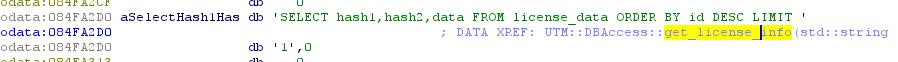
Great, this is a query in the database, so we go to where this string is used, that is, in UTM :: DBAccess :: get_license_info (there are such names only in the unix version, in the windows version there are no such amenities, only abstract names functions )
Having rotated back and forth in UTM :: DBAccess :: get_license_info, we see that data from the table is read here, and at the end either all is good or all is bad:
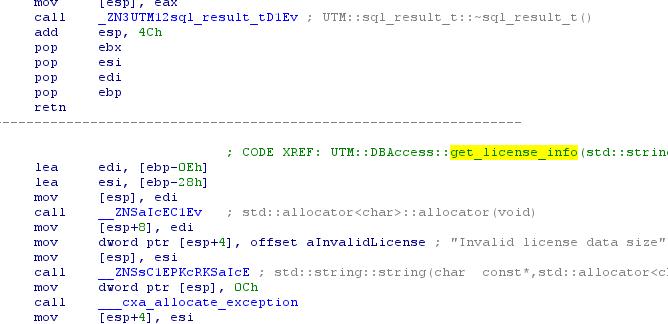
Therefore, we go to a higher level in main + ABC:

And we come across a very interesting thing - “CirtificationCenterImpl”:
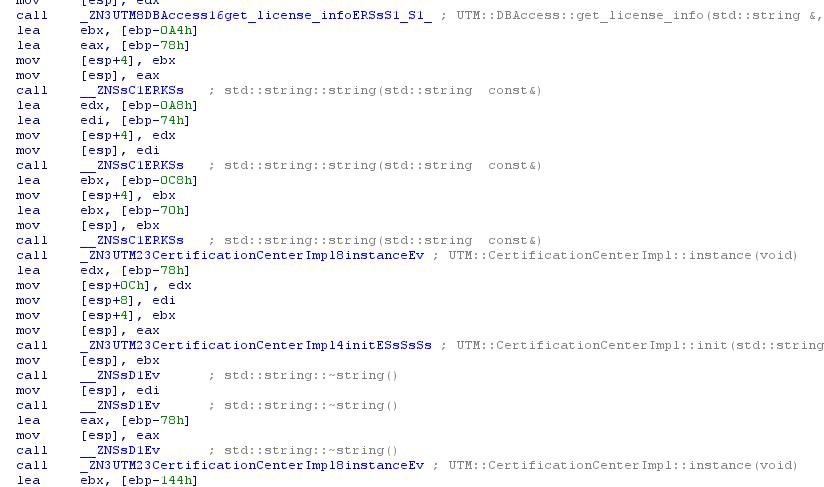
There is nothing interesting in UTM :: CertificationCenterImpl :: instance (void), so let's enter UTM :: CertificationCenterImpl :: init and see what might be interesting inside:
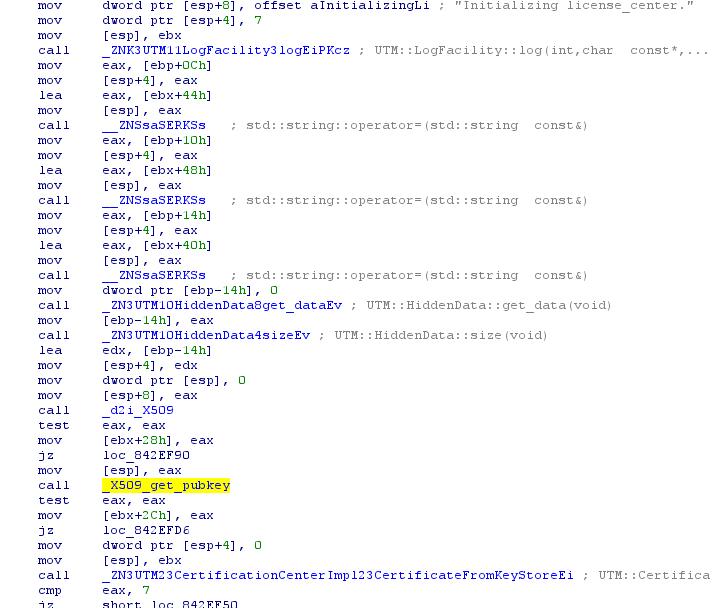
We see "_d2i_X509" and "_X509_get_pubkey". A quick search leads us to the fact that these functions are needed to work with X.509 .
And now we will pay attention, what data get in _d2i_X509.
Just above, we see two functions - “UTM :: HiddenData :: get_data (void)” and “UTM :: HiddenData :: size (void)”
Open UTM :: HiddenData :: get_data (void):
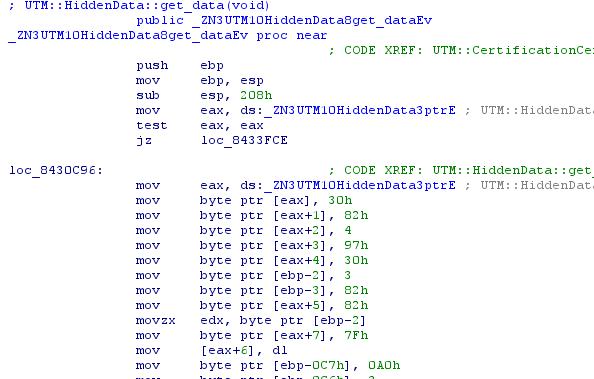
It is clearly seen that the developers did not want to just "put" the data into the executable file, but did it with the help of a number of mov'ov.
The second function simply returns the size of this data:
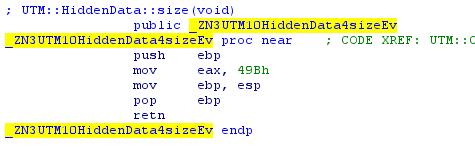
Put a breakpoint in GDB in this place:

After stopping at this place, you can dump 0x49B characters from memory to an address that is located in eax.
We look through either through gcr-viewer, or through console openssl x509 and we see:
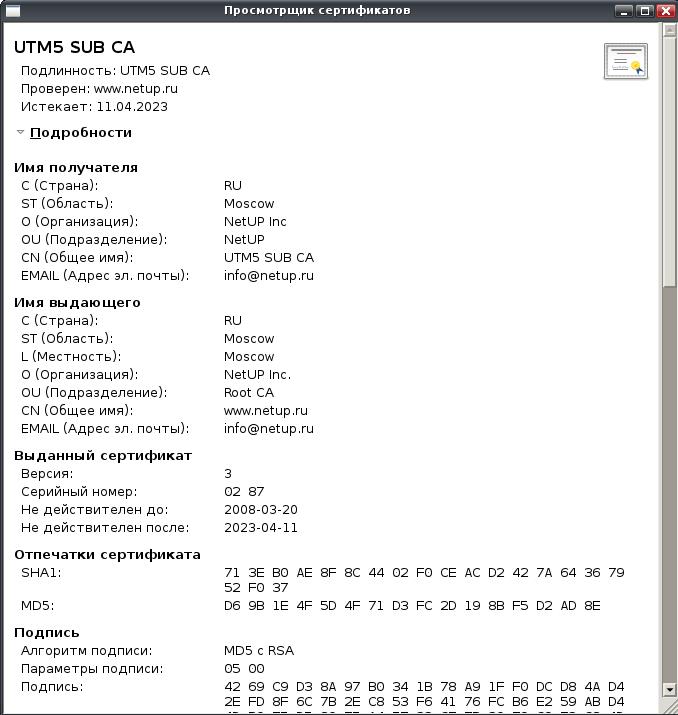
Well, we have some kind of certificate, now let's go ahead and examine what happens next:
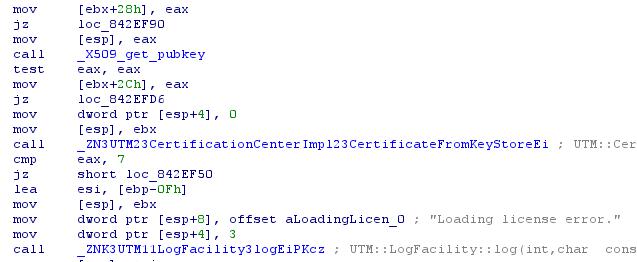
Next, the program receives the public key from this certificate, and sends it all to "_ZN3UTM23CertificationCenterImpl23CertificateFromKeyStoreEi", and below you can see that the error message is already coming, then the check is here, go to this function and scroll through, stumble on:
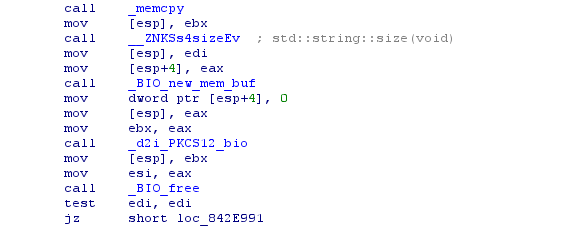
Now we can come to the idea that in mysql, in the data field there is another certificate in the pkcs12 format.
We extract this data from the reg.sql file, translate into a binary format, since This is an ascii-hex entry.
After saving the data, let's say in the “key” file, use the command to extract a lot of certificates:
Openssl will ask us for a password. Give her the password, which came with the key in reg.sql, because we did not see anything like this in the asm listing.
Having entered passwords several times, we get key.pem.
We take all the same gcr-viewer, review this key.pem and see:
utm5_core
Authenticity: utm5_core
Checked: UTM5 SUB CA
Expires on 03/01/2012
utm5_dealer
Authenticity: utm5_dealer
Checked: UTM5 SUB CA
Expires on 03/01/2012
utm5_dynashape
Authenticity: utm5_dynashape
Checked: UTM5 SUB CA
Expires on 03/01/2012
utm5_hotspot
Authenticity: utm5_hotspot
Checked: UTM5 SUB CA
Expires on 03/01/2012
utm5_radius
Authenticity: utm5_radius
Checked: UTM5 SUB CA
Expires on 03/01/2012
utm5_tel
Authenticity: utm5_tel
Checked: UTM5 SUB CA
Expires on 03/01/2012
Key
RSA secret key
Reliability: 1024 bits
After reading the "Practical Guide to Creating a Certification Authority " , it becomes clear that the license for utm5 is made using certificates, and we have certificates of licenses + pulled out of the program a certificate to verify the authenticity of license certificates.
If you select each certificate from the key.pem file into a separate file, then you can view additional fields in the same console utility “openssl x509”, which contain the limitations of various modules.
At this step, the study can be completed, since it is quite clear that it is impossible to generate the necessary license certificate without having a private key, which only NetUP has.
Although, in fact, protection has a very large vulnerability further, when those very restrictions are read out - they are transmitted to the program in the form of regular strings, which can be easily changed, either for very large values, or even for “-1”.
The license validity period is also limited by the certificate validity period, so this place can also be patched, and the program will work even after the certificate expires.
But a more elegant method would be to create your own certificates, with the values we need. The program will be able to accept them, since we simply take and insert our verification certificate into the program, replacing the code of the functions “UTM :: HiddenData :: get_data (void)” and “UTM :: HiddenData :: size (void)” with your own, and utm5 will work even until 2050, but is it necessary?
It so happened that the choice fell on utm5.
The goal was to understand what protection method this software uses, especially since this complex of programs is available both under windows and under linux / freebsd.
I took the unix version, since it was the first experience of researching programs not under windows.
And we will use all the same IDA launched from under wine.
Assume that utm5 is loaded, there is a demo key, everything is set up and working. Well, let's get started:
')
We take the core of the system (utm5_core) and feed it with IDA. Let's drink some tea and go back to the computer where IDA will happily report that it has fully analyzed the file.
We look at the reg.sql file, and we come to the conclusion that the kernel of the system reads the license from mysql.
Carefully looking at the data, we decide that we are interested in the "hash1, hash2, data" fields.
Do a search for the string hash1 in strings, we find:

Great, this is a query in the database, so we go to where this string is used, that is, in UTM :: DBAccess :: get_license_info (there are such names only in the unix version, in the windows version there are no such amenities, only abstract names functions )
Having rotated back and forth in UTM :: DBAccess :: get_license_info, we see that data from the table is read here, and at the end either all is good or all is bad:

Therefore, we go to a higher level in main + ABC:

And we come across a very interesting thing - “CirtificationCenterImpl”:

There is nothing interesting in UTM :: CertificationCenterImpl :: instance (void), so let's enter UTM :: CertificationCenterImpl :: init and see what might be interesting inside:

We see "_d2i_X509" and "_X509_get_pubkey". A quick search leads us to the fact that these functions are needed to work with X.509 .
And now we will pay attention, what data get in _d2i_X509.
Just above, we see two functions - “UTM :: HiddenData :: get_data (void)” and “UTM :: HiddenData :: size (void)”
Open UTM :: HiddenData :: get_data (void):

It is clearly seen that the developers did not want to just "put" the data into the executable file, but did it with the help of a number of mov'ov.
The second function simply returns the size of this data:

Put a breakpoint in GDB in this place:

After stopping at this place, you can dump 0x49B characters from memory to an address that is located in eax.
We look through either through gcr-viewer, or through console openssl x509 and we see:

Well, we have some kind of certificate, now let's go ahead and examine what happens next:

Next, the program receives the public key from this certificate, and sends it all to "_ZN3UTM23CertificationCenterImpl23CertificateFromKeyStoreEi", and below you can see that the error message is already coming, then the check is here, go to this function and scroll through, stumble on:

Now we can come to the idea that in mysql, in the data field there is another certificate in the pkcs12 format.
We extract this data from the reg.sql file, translate into a binary format, since This is an ascii-hex entry.
After saving the data, let's say in the “key” file, use the command to extract a lot of certificates:
openssl pkcs12 -in key -out key.pemOpenssl will ask us for a password. Give her the password, which came with the key in reg.sql, because we did not see anything like this in the asm listing.
Having entered passwords several times, we get key.pem.
We take all the same gcr-viewer, review this key.pem and see:
utm5_core
Authenticity: utm5_core
Checked: UTM5 SUB CA
Expires on 03/01/2012
utm5_dealer
Authenticity: utm5_dealer
Checked: UTM5 SUB CA
Expires on 03/01/2012
utm5_dynashape
Authenticity: utm5_dynashape
Checked: UTM5 SUB CA
Expires on 03/01/2012
utm5_hotspot
Authenticity: utm5_hotspot
Checked: UTM5 SUB CA
Expires on 03/01/2012
utm5_radius
Authenticity: utm5_radius
Checked: UTM5 SUB CA
Expires on 03/01/2012
utm5_tel
Authenticity: utm5_tel
Checked: UTM5 SUB CA
Expires on 03/01/2012
Key
RSA secret key
Reliability: 1024 bits
After reading the "Practical Guide to Creating a Certification Authority " , it becomes clear that the license for utm5 is made using certificates, and we have certificates of licenses + pulled out of the program a certificate to verify the authenticity of license certificates.
If you select each certificate from the key.pem file into a separate file, then you can view additional fields in the same console utility “openssl x509”, which contain the limitations of various modules.
At this step, the study can be completed, since it is quite clear that it is impossible to generate the necessary license certificate without having a private key, which only NetUP has.
Although, in fact, protection has a very large vulnerability further, when those very restrictions are read out - they are transmitted to the program in the form of regular strings, which can be easily changed, either for very large values, or even for “-1”.
The license validity period is also limited by the certificate validity period, so this place can also be patched, and the program will work even after the certificate expires.
But a more elegant method would be to create your own certificates, with the values we need. The program will be able to accept them, since we simply take and insert our verification certificate into the program, replacing the code of the functions “UTM :: HiddenData :: get_data (void)” and “UTM :: HiddenData :: size (void)” with your own, and utm5 will work even until 2050, but is it necessary?
Source: https://habr.com/ru/post/136500/
All Articles