Networks for the smallest. Part One (which is after zero). Connection to the equipment cisco
All issues
8. Networks for the smallest. Part Eight BGP and IP SLA
7. Networks for the smallest. Part Seven. VPN
6. Networks for the smallest. Part six. Dynamic routing
5. Networks for the smallest: Part Five. NAT and ACL
4. Networks for the smallest: Part Four. STP
3. Networks for the smallest: Part Three. Static routing
2. Networks for the smallest. Part two. Switching
1. Networks for the smallest. Part one. Connection to the equipment cisco
0. Networks for the smallest. Part zero. Planning
7. Networks for the smallest. Part Seven. VPN
6. Networks for the smallest. Part six. Dynamic routing
5. Networks for the smallest: Part Five. NAT and ACL
4. Networks for the smallest: Part Four. STP
3. Networks for the smallest: Part Three. Static routing
2. Networks for the smallest. Part two. Switching
1. Networks for the smallest. Part one. Connection to the equipment cisco
0. Networks for the smallest. Part zero. Planning
The topic of cisco on Habré can not be called popular, often interesting articles go almost unnoticed. But we were pleasantly surprised by the excitement around our previous publication . More than a thousand people have added it to their favorites, and this definitely indicates that continuation is necessary.
In addition, many people with real planning and network building experience made very good reservations. The fact is that the network scheme proposed last time is a mock-up, a laboratory for which we will work out and understand technologies, therefore we did not bother with such things. In real life, especially if you are a telecoms provider / provider, you need different backup schemes: VRRP , STP , Link Aggregation , dynamic routing protocols.
We will try to take into account all the comments and, at the end of the cycle, we will probably look at how the network should be built so that six months after launch, the engineer would not be excruciatingly painful.
Today we will turn to the part a bit boring, but important for beginners: how to connect, set or reset a password, log in via telnet. We also consider existing programs - Cisco emulators and hardware interface.
As promised, this time everything is grown-up: from the video.
Under the cut is the same in textual and slightly more detailed form.
So, here they come - the cherished boxes with the words Cisco on board.
Wednesday
Let's start with the environment in which we will work.
')
Currently there are two well-known software packages that allow you to simulate a network built on Cisco equipment:
a) Ziskovsky Packet Tracer product, which in theory is not freely distributed. This is an emulator and has only a few Cisco IOS features. Generally speaking, it is very limited and many things in it are only partially implemented. No tweaks. On the other hand, to date, version 5.3.2 supports the creation of GRE tunnels, dynamic routing protocols (and even BGP among them!). Moreover, it is very easy to learn and has servers (FTP, TFTP, DHCP, DNS, HTTP, NTP, RADIUS, SMTP, POP3), workstations and switches in its arsenal. Now it is already under Linux, although in the old days it was perfectly launched from under Wine.
b) GNS3 simulator distributed under the GNU GPL license. This package requires you to download real Cisco IOS images. On the one hand, this is a plus - you work with a real cisco interface and are limited only by your imagination, existing standards and performance of the workstation, on the other hand, firstly, these IOS still need to be able to get, secondly, it is a more complex product to understand and thirdly, it has only routers and “type” switches.
I think that to get acquainted with the principles, it is better to start with the Packet Tracer, and then switch to heavy artillery as needed. We are not all small children, where we will not take what we need to take.
Connection methods
In Packet Tracer, you can control equipment in the following ways:
The interface of the last three is identical - only the connection method is different. Of course, the GUI is not our method.
In real life, the following are available:
- Telnet / ssh
- Terminal connection from workstation via console cable
- Web interface ( Cisco SDM ).
The last option does not even mention in a decent society. Even if you are an adept mouse and browser, I really do not advise.
In my example, when working with other equipment, I came across the fact that what was configured via the web does not work. Although you burst, but does not work. And the same length in general had a bug in the same firmware version for the switches: if you change the VLAN settings in the web interface from under Linux, the switch becomes inaccessible for management. This is an officially recognized problem. Telnet is a standard, well-known utility, like ssh . To access cisco using these protocols, you need to set up access passwords, more on that later. The ability to use ssh depends on the IOS license.
Console control
Well, you brought a router, printed out, they gave power to it. He languidly rustled with coolers, he winks at you with the LEDs of his ports. And what next to do?
We use one of the oldest and ageless ways to control virtually any smart device: the console. To do this, you need a computer, the device itself and a suitable cable.
There is every vendor for that much. What kind of connectors they do not use: RJ-45, DB-9 dad, DB-9 mother, DB-9 with non-standard pinout, DB-25.
The tsiska uses the RJ-45 connector on the device side and the DB-9 mother (for connecting to the COM port) on the PC side.
The console port looks like this:


Always highlighted in blue. Recently, USB control became possible.
This console cable cisco:

Previously, it was shipped in each box, now often worth some money. In principle, a similar cable from HP is suitable.
The problem is that modern PCs often do not have a COM port. Frequently used USB-to-COM converters come to the rescue:


Or RS232-Ethernet converters rarely used for this purpose.

After you plug in the cable, determine the COM port number, you can use Hyperterminal or Putty in Windows and Minicom in Linux to connect.
Management through the console is available immediately, but for telnet you need to set a password. How to do it?
Turn to PT.
Let's start by creating a router: select it on the panel below and transfer it to the workspace. We give some name
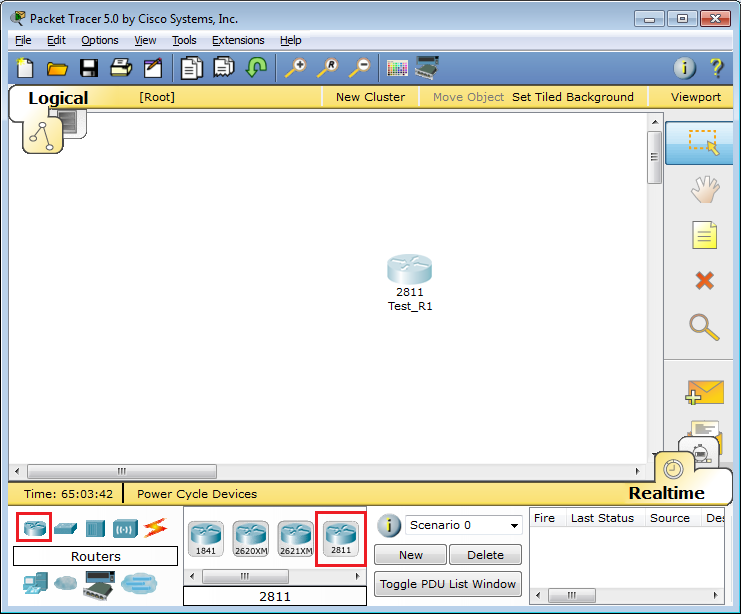
What would you do if it were the most current iron router? They would take a console cable and connect it to it and to the computer. Let's do the same here:

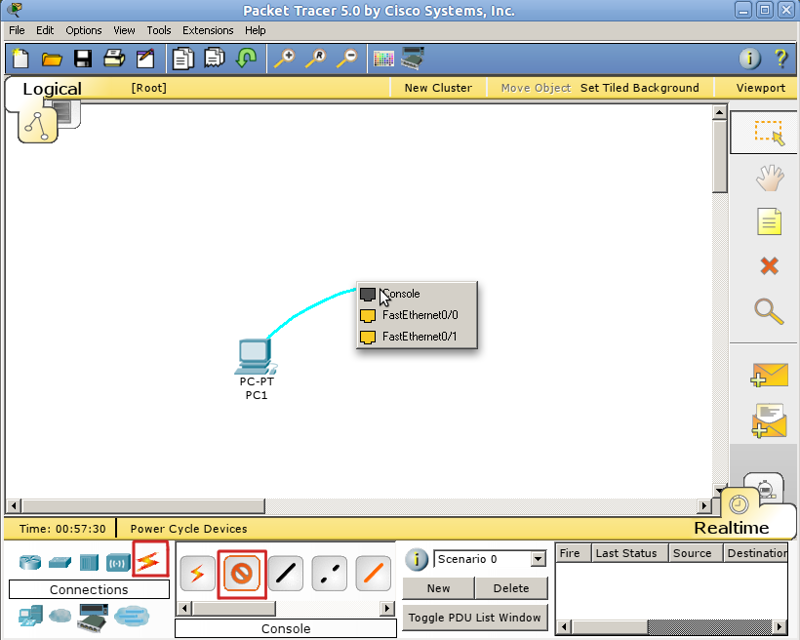
By clicking on the computer, we call up the settings window, in which we are interested in the Desktop tab. Next, select the Terminal, where we are given the choice of parameters

However, all the default parameters suit us, and there is no sense in changing them.
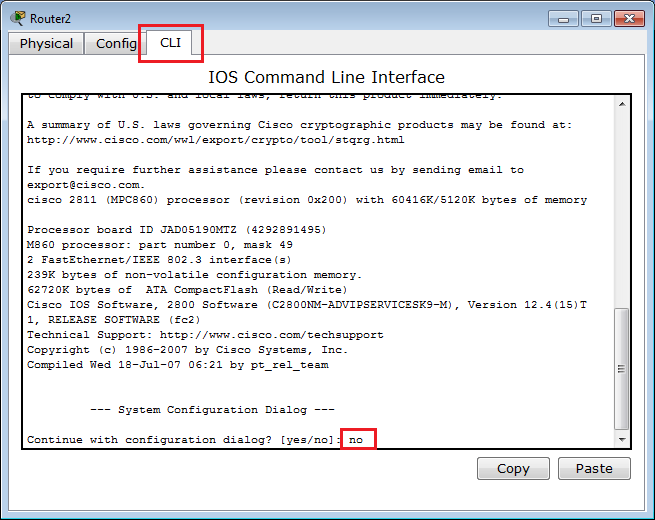
If there is no configuration file (startup-config) in the non-volatile memory of the device, and this will be the case when the new hardware is first turned on, the Initial Configuration Dialog prompt will meet us:
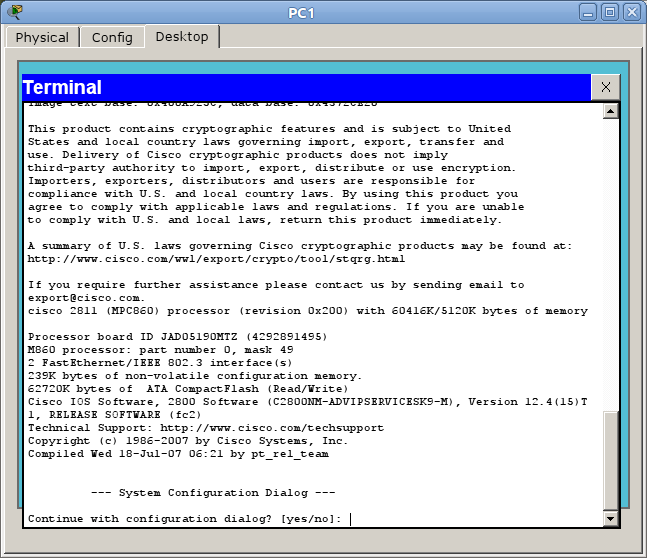
In short, this is such a wizard, which allows you to step by step configure the basic parameters of the device (hostname, passwords, interfaces). But it is not interesting, so we answer no and see the invitation
Router> This is standard, absolutely for any cisco line, an invitation that characterizes a user mode in which you can view some statistics and carry out the simplest operations like ping. Entering the question mark will show a list of available commands:
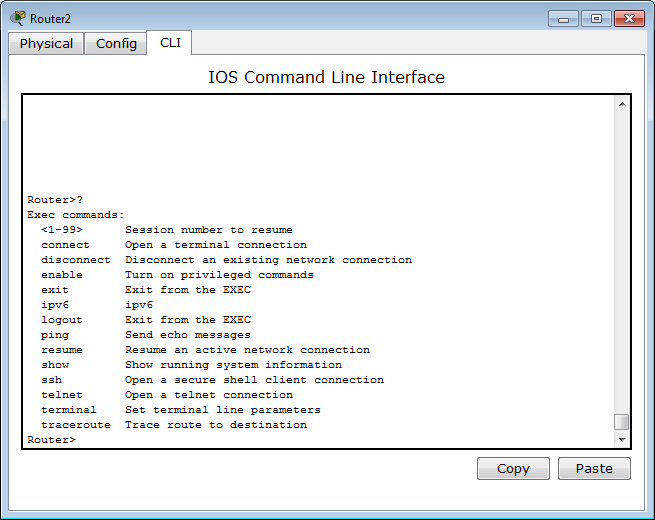
Roughly speaking, this is the mode for the network operator, the engineer of the first line of technical support, so that he doesn’t hurt anything there, doesn’t screw it up and doesn’t know too much.
The mode with the talking name privileged provides much greater opportunities. You can get into it by entering the command > enable . Now the invitation looks like this:
Router# Here the list of operations is much more extensive, for example, you can run one of the most frequently used commands, demonstrating the current settings of the device aka “config” #show running-config . In privileged mode, you can view all device information.
Before starting the configuration, we mention several usefulness when working with the cisco CLI, which can greatly simplify life:
- All commands in the console can be abbreviated. The main thing is that the abbreviation clearly indicates the command. For example, show running-config is abbreviated to sh run . Why not before sr ? Because s (in user mode) can mean both the show command and the ssh command, and we get the % Ambiguous command error message : “sr” (ambiguous command).
- Use the Tab key and question mark. By pressing Tab, the abbreviated command is added to the full, and the question mark following the command displays a list of further features and a little help on them (try yourself in PT).
- Use hotkeys in the console:
Ctrl + A - Move the cursor to the beginning of the line
Ctrl + E - Move the cursor to the end of the line
Cursor Up, Down - Navigating the command history
Ctrl + W - Erase the previous word
Ctrl + U - Erase entire line
Ctrl + C - Exit Configuration Mode
Ctrl + Z - Apply current command and exit configuration mode.
Ctrl + Shift + 6 - Stop long processes (the so-called escape sequence)
- Use command output filtering. It happens that a team displays a lot of information in which you need to dig a long time to find a certain word, for example.
We make it easier to work with filtering: after the command we set | , we write the type of filtering and, in fact, the desired word (or part of it). Types of filtering (aka output modifiers):
begin - output all lines, starting with the one where the word was found,
section - output sections of the configuration file in which the word occurs,
include - output lines where the word occurs,
exclude - output lines where the word is NOT found.
But back to the modes. The third major mode, along with user and privileged: global configuration mode . As the name implies, it allows us to make changes to the device settings. It is activated by the command #configure terminal from privileged mode and demonstrates such an invitation:
Router(config)# In the global configuration mode, quite occasionally commands from other modes are not executed (the same show running-config, ping, etc.). But there is such a useful thing as do . Thanks to it, we can, without leaving the configuration mode, execute these very commands, simply by adding before them do. Like that:
Router(config)#do show running-config Configure Telnet Access
From this mode, we will configure the interface for connecting the computer via telnet:
The command to enter the FastEthernet 0/0 interface configuration mode :
# Router(config)# interface fa0/0 By default, all interfaces are disabled (administratively down). Enable the interface:
Router(config-if)#no shutdown Configure the IP address:
Router(config-if)#ip address 192.168.1.1 255.255.255.0 shutdown - means “turn off the interface”. Accordingly, if you want to cancel the action of the command, use the word no in front of it. This is a common CLI rule and applies to most commands.
Connect. For this you need to use a crossover cable . (Although in real life it is often not necessary already - all cards can understand reception / transmission, however, there are still routers whose ports do not rise when using the wrong type of cable - so be careful)
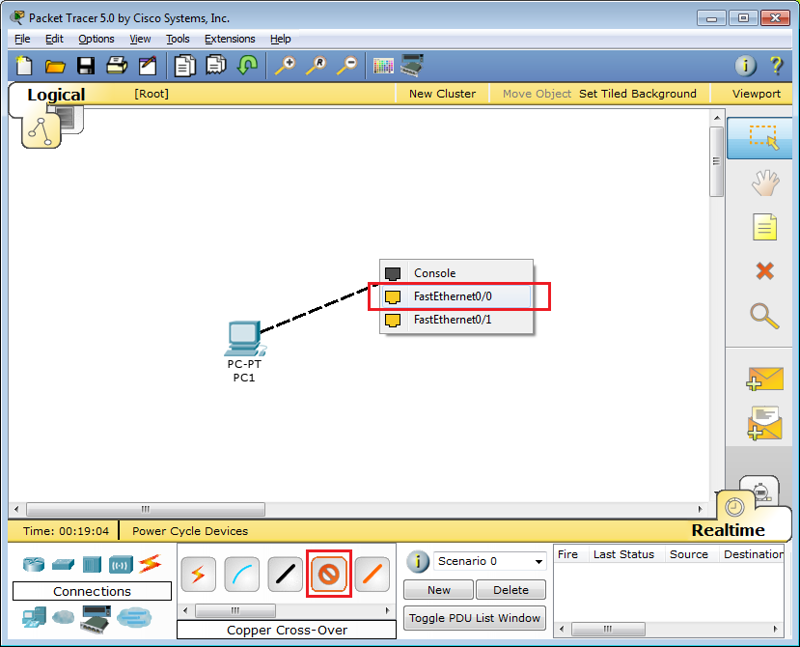
We configure the IP address of the computer through the Desktop.
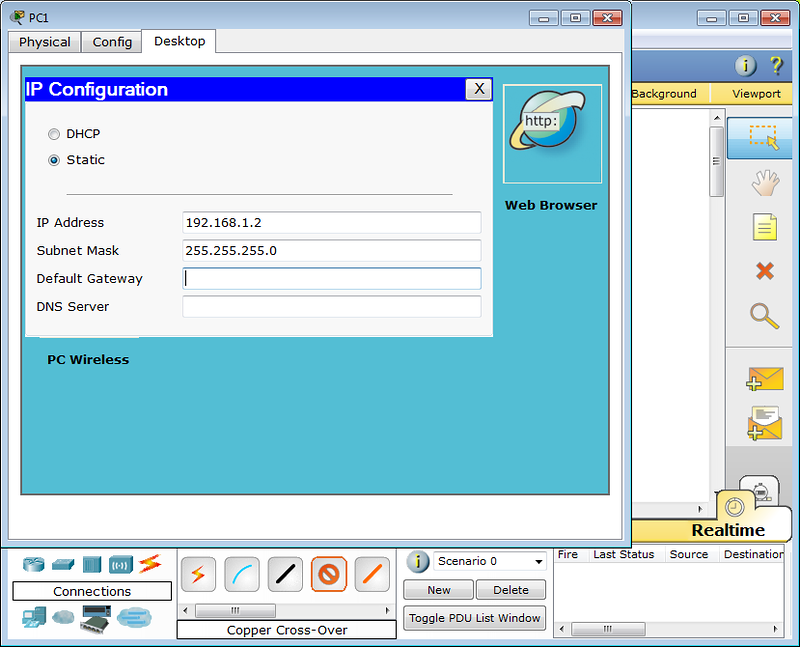
And we try to connect by selecting Command Prompt in the Desktop panel:
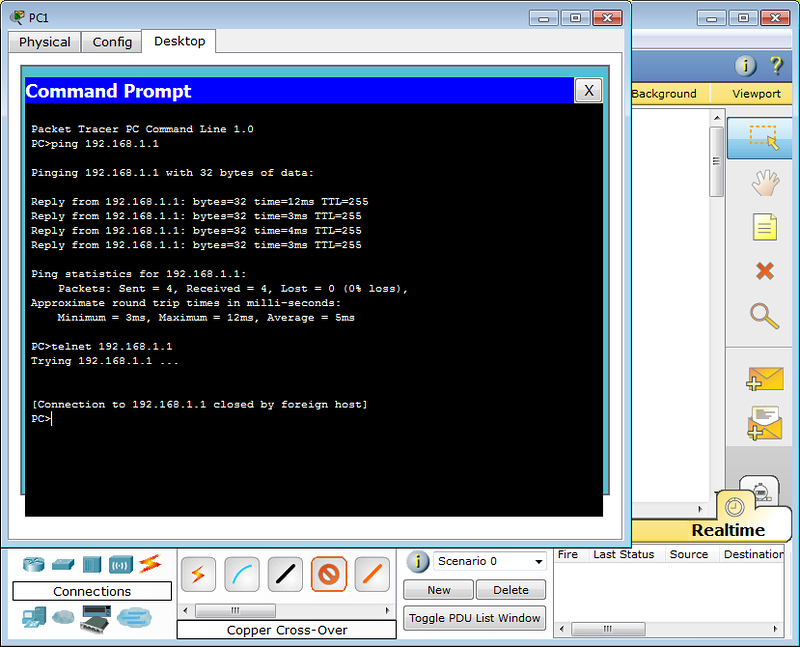
As expected, the tsiska does not allow without a password. In real life, usually gives the phrase “Password required, but none set”
Passwords
A telnet or ssh connection is called a virtual terminal (vt) and is configured as follows:
Router(config)#line vty 0 4 Router(config-line)#password <i>cisco</i> Router(config-line)#login 0 4 is 5 user virtual terminals = telnet sessions.
This is enough to get into user mode, but not enough for the privileged one:
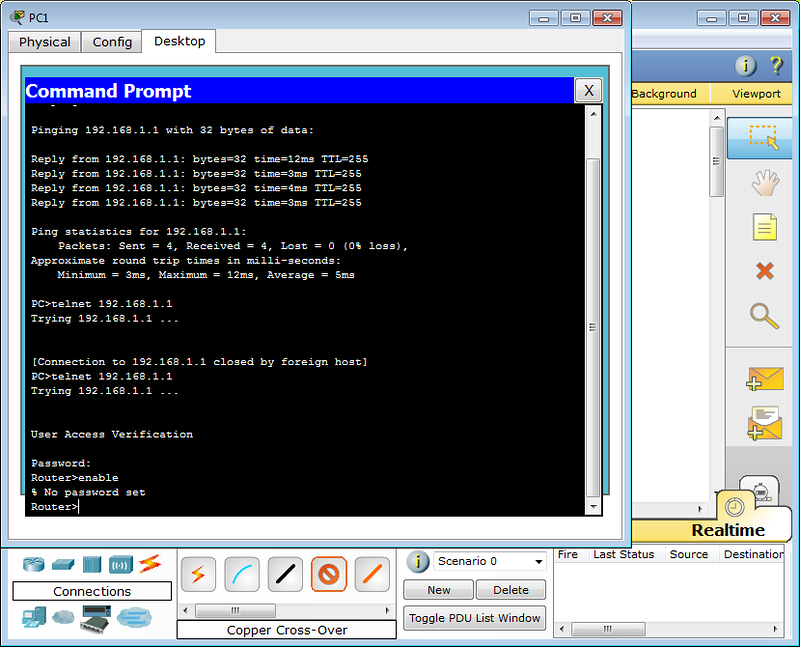
Set the password for enable mode:
Router(config)#enable secret <i>test</i> 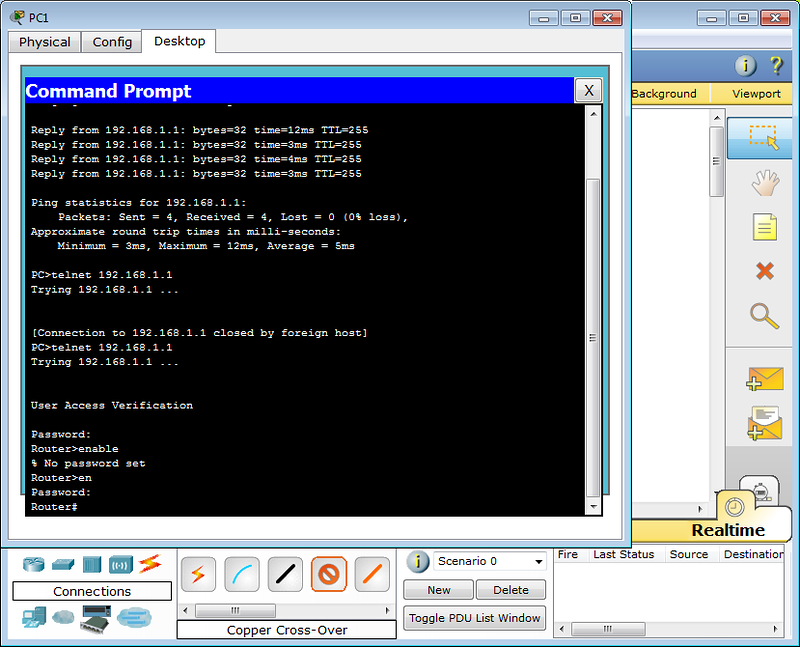
What is the difference between secret and password ? Approximately the same as ssh from telnet. When you configure secret, the password is stored in an encrypted form in the configuration file, and password - in the open. Therefore it is recommended to use secret .
If you still set the password with the password command, you should also apply service password-encryption , then your password will be encrypted in the configuration file:
line vty 0 4 password 7 08255F4A0F0A0111 A friend of mine told me a story:
He once stood smoking near one of his knots, located in a residential building. With tool bag, laptop in hand. Suddenly two drunks come up with a package and offer to buy, opening the package and showing some kind of switch. They ask for 500 rubles. Well, he bought. According to the tags and the switch model, the guy concluded which provider he belongs to. I came home, started picking - the telnet is closed, the console is password-protected. Merged config on snmp. Passwords are stored in clear text, the name with the head gives the provider. With their admin, he personally knows, called him instead of “Hello” issued a username and password in the handset. It was heard how the brain creaked in the first 20 seconds: everywhere access lists, authorization, binding to the MAC address. How?! In general, all is well that ends well.
You can read a little about it here . Well, or a little more in Russian, here .
We want to draw your attention:
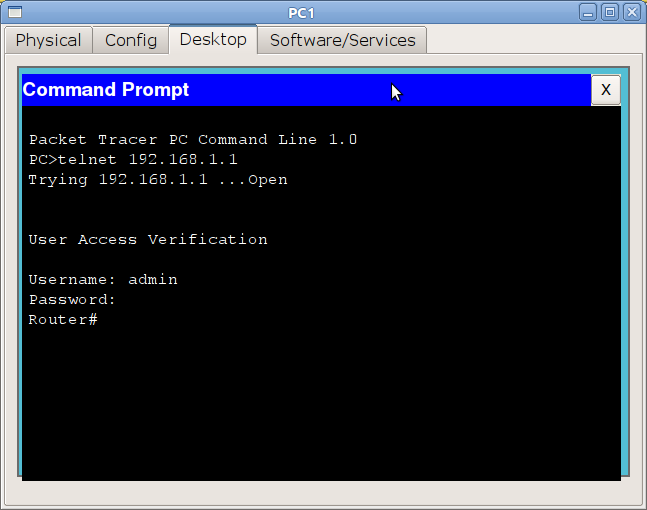
It is now accepted to configure accesses not through virtual terminals, but with #username and #aaa new-model commands. In PT 5.3.2, they already exist and work fine.
To do this, perform:
Router(config)#aaa new-model Router(config)#username admin password 1234 The first command is to activate a new model.
Be careful : the priority of the aaa new-model command is higher than the commands of the virtual terminals and therefore even despite the fact that you have configured the password in the line vty mode, if you do not have users in the local database, you will not be able to access the device remotely.
Now when connecting, the router will request the user name and the corresponding password.
With a deeper setting of line vty there is one danger.
There is such a parameter: access-class . Its configuration allows you to limit the IP-addresses from which you can connect. Then one day I, like a smart Masha, decided to take up security in the network and almost all the equipment put these access lists on it so that the mosquito does not fly. At one point, I had to go to the field and that day I cursed my accuracy — I could not reach anywhere — I didn't leave the slightest loophole. In general, be careful with this team or leave loopholes for yourself.
When working with access-lists and other dangerous things, the incorrect configuration of which can deprive you of access to the device, you can use the remarkable command reload in min , where the min time is in minutes. This command will reboot the device after the specified time, unless it is interrupted by the reload cancel command. Those. The scheme of work is this: you are remotely digging something that can in theory (do not forget Murphy's law) interrupt your communication session with the device. We save the current (working) config in the startup-config (it is used when loading), set reload in 15, enter the key command about which we have doubts ;-), and we get a break of communication, the worst fears were justified. We are waiting for 15 minutes, the device is overloaded with a working config, a connection is voila, there is a connection. Or (if the connection was not interrupted), we check that everything works, and do a reload cancel .
If you want to restrict access via the console port to a password, you will need commands
Router(config)#line console 0 Router(config-line)#login Router(config-line)#password <i>cisco</i> Privilege Level
Another important point that the articles pay little attention to: privelege level.
As is clear from the Latin sound - this is the level of user rights. In total there are 16 levels: 0-15.
privilege level 0 - these are the disable, enable, exit, help, and logout commands that work in all modes
privilege level 1 - These are user-mode commands, that is, as soon as you get on the tsiska and you see the prompt Router> you have level 1.
privilege level 15 - These are privileged mode commands, sort of like root in Unixes
Example1
Router(config)#line vty 0 4 Router(config-line)privilege level 15 After logging in to the router with this setting, you will immediately see the Router # with all the rights therein.
All levels 2 through 14 are manually configured. That is, for example, you can give a go-ahead to the user with privelege level 2 to execute the show running-config command
Example2
The username command already mentioned will help to configure permissions for a specific user.
Router(config)#username pooruser privilege 2 secret poorpass Router(config)#privilege exec level 2 show running-config Router(config)#enable secret level 2 l2poorpass In the first line we assign the level of rights to the user, in the second command allowed for this level, in the third we set the password to enter the privileged mode with this level.
After that, from the user mode, you can execute the enable 2 command and enter the l2poorpass password to get into the privileged mode, in which all commands of level 1 + commands of level 2 will be available.
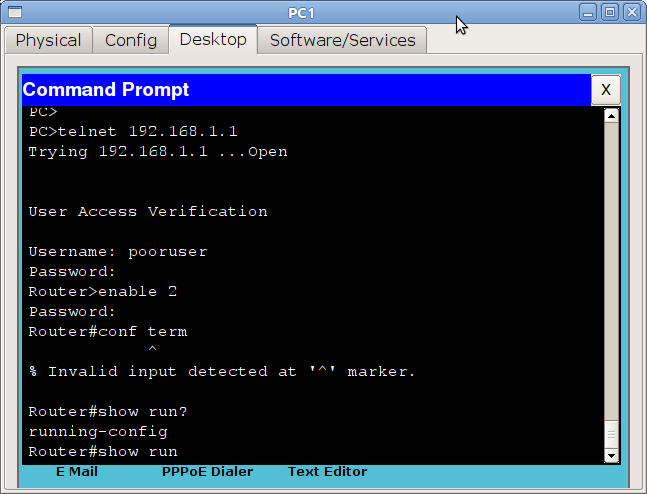
What can it be for? In the Russian realities, there is practically nothing, because usually engineers need to go to the device with full rights at once. Well, except that the 15th level is set so that double authentication does not pass. And all the other levels, again, so that the staff of younger staff (technical support, for example) could enter and monitor some parameters or configure a non-critical function.
Ssh
It is necessary to mention that telnet is an unprotected protocol and transmits the password and data in open form. Using any packet analyzer, you can calculate the password.
Therefore, it is highly recommended to use ssh - any cisco devices with not the shortened firmware can act as an ssh server.
The following set of commands will allow you to enable ssh and disable telnet access:
Router(config)#hostname R0 Router(config)#ip domain-name cisco-dmn Router(config)#crypto key generate rsa Router(config)#line vty 0 4 Router(config-line)#transport input ssh The host name must be different from the Router, the domain name must be specified. The third line generates the key and then only ssh is allowed. The key length must be more than 768 bits if you want to use ssh version 2, and you want it. Everything.
Another final note for newbies: do not forget about the write memory command - this is saving the current configuration. However, it is enough to get burned twice, forgetting to save, to permanently earn immunity to this - whoever wrote at night or wrote a term paper, he would understand.
Using PT, we will configure the equipment not through the terminal or telnet, but directly through the device CLI, which is called by clicking on the icon of the router - it is more convenient:
Well, for sweets: password reset
So, what to do if a Bush tsiska with an unknown password fell on the table or did you forget it at the wrong time? In fact, it is repeatedly described and easily googled, but it is necessary to repeat it.
Virtually any network device has the ability to reset the password, having physical access. If this is not possible or it is a separate paid service, then most likely you have some kind of Russian hand-made article (no offense, of course, to our manufacturers, but twice I read these lines in the documentation :))
So, cisco:
1) Connect to the device with a console cable,
2) Send it to reboot (at least for food, even though the command #reload )
3) When such a line of ######## ... ###, meaning image loading (40-60 seconds after switching on) runs on the screen, you need to send a Break signal. How to do it in different programs read here . You are in ROMMON mode.
4) In this mode, enter the command: confreg 0x2142 , it will cause the device to ignore startup-config on boot.
5) Enter reset to reboot.
6) After booting, the running-config will be pristine clean, and the startup-config will still contain the last saved configuration. Now is the time to change the password or merge the config.
7) The most important thing: return back registers :
Router(config)#config-register 0x2102 If you do not do this, then all of your configuration will be relevant until the first reboot.) And it’s good if this device is standing next to you, and you’ll remember what you have done. I was not lucky)
In the next article we turn to the vlans and the local network. Be sure to read:
OSI .
VLAN
Unregistered readers of Habrahabr can ask their questions in LiveJournal .
I want to thank thegluck user for helping to write this article.
Source: https://habr.com/ru/post/136056/
All Articles