Features of the ZyXEL Keenetic router on the second generation NDMS v2.00 firmware
Some time ago, a beta version of the firmware called NDMS 2.0 appeared on the ZyXEL website in the download section for the Keenetic Internet Center . Invited to drive her were also received by registered interested owners of the usual Kinetics. The annotation says that this is not the next update, but the second generation of the software platform, which is radically different from the previous one and addressed to advanced users. The most interesting of the declared (in comparison with the first generation firmware):
So, the new firmware was downloaded from the ZyXEL website and successfully installed on Keenetic (there may be nuances, but they can be solved through the support of the manufacturer in a special topic and in this case are not critical). Let's get to know each other. The web configurator also opens at 192.168.1.1 with the login / password of admin / 1234. We immediately see that the new web interface has practically nothing to do with the previous version:
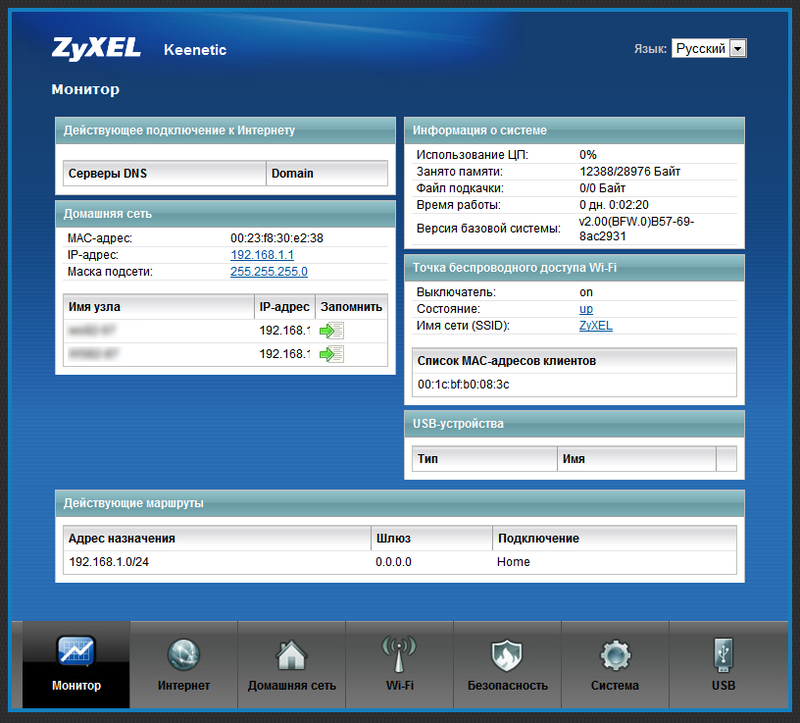
')
He made a double impression on me: on the one hand, he became prettier, but on the other - I had been mastering it much longer. (Looking ahead, you can add that the skin of the web interface then, in the list of components, you can choose from two options to your taste.)
Like the first generation firmware, NDMS 2.0 supports many types of connections, each of which now has a separate tab in the Internet section (IPoE, PPPoE, PPTP, L2TP, 802.1X, 3G, Yota, Wi-Fi client). Unlike V1.00, you can configure several connections at once, and in any combination. Connections are bound either to physical interfaces (Ethernet ports, USB modem, Wi-Fi interface), or to an already created logical interface (for example, you can “nest” one PPTP tunnel into another). Each Internet connection is assigned its own priority, allowing you to determine which of them will be the main and which of them will be basic, secondary or backup depending on your imagination and needs.
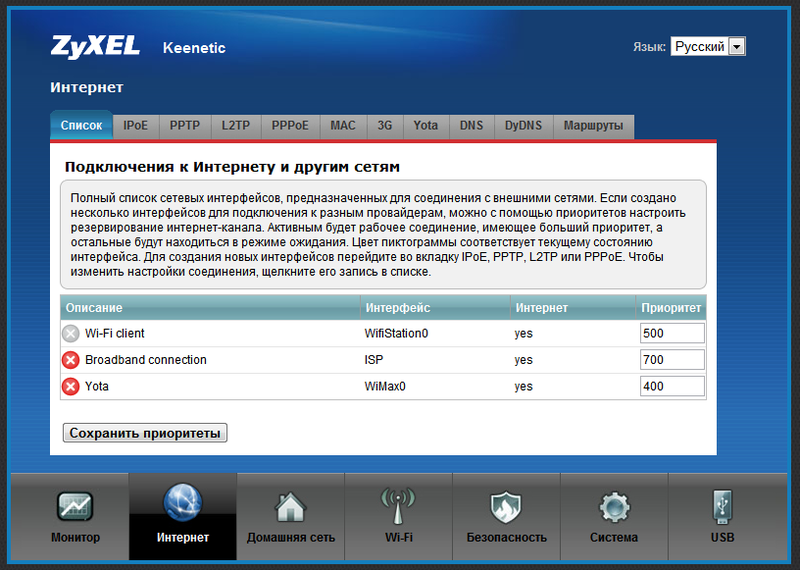
In the default settings, there is only one “Broadband connection (ISP)” Internet connection, which is tied to the WAN port. It brings up a DHCP client that automatically obtains an address from the provider’s network when the cable is connected to the WAN port (of course, provided that the provider issues this address). For the home network, all LAN ports of the router and the Wi-Fi access point are used by default. They are combined into one logical interface (Home VLAN), on which the DHCP server is distributed, which distributes addresses from the 192.168.1.1/24 network.
To connect to the Internet provider via PPTP, as well as via L2TP or PPPoE, you need to configure two (!) Interfaces: one to connect to the provider’s network (IPoE tab), the second is for the Internet itself. If the address in the local network of the provider is issued automatically, then the first interface can be considered already configured - this is the pre-installed Broadband Connection (ISP) interface, which is described above. If the provider has given you a static address, change the settings of the Broadband connection interface (ISP) and do not forget to set the specified DNS servers in the DNS tab. Next, open the PPTP tab (L2TP or PPPoE):

Here, in addition to the usual settings typical for mass routers, the items “Connect via” and “Use for Internet access” appeared. The first is needed to indicate to the router through which connection it should establish a PPTP connection (L2TP or PPPoE), in our case it is a Broadband connection (ISP), and the second speaks for itself: if you want to use this PPTP connection (L2TP or PPPoE ) to access the Internet, select the checkbox - then when a connection is made in the router's routing table, the default route will be the gateway of this connection. After applying the settings and connecting to the WAN port of the cable from the provider, the device will connect to the Internet. If you need to use 802.1x (there are also such providers), then it turns on even easier: as a separate connection does not appear, but comes to life on the specified interface.
In principle, we have already received a working router with access to the Internet via PPTP. But, of course, this whole vegetable garden (firmware and article about it) is not for the sake of such a banality. Now we will first look at how to connect to the Internet via USB-modems. Yota modems, as in the first firmware, are automatically recognized when plugged into the USB port, everything that is necessary for their operation is pre-configured. We take the popular Yotovsky Samsung SWC-U200 modem and stick it into the router (money in the account is not important). The connection goes unnoticed quickly, the modem flashes a blue indicator, on the status page the interface Yota merrily turns green, and the connection settings appear on the Yota tab. As we can see, the state of the modem is SLEEP, because its priority is lower by default than that of the PPTP connection that continues to work:
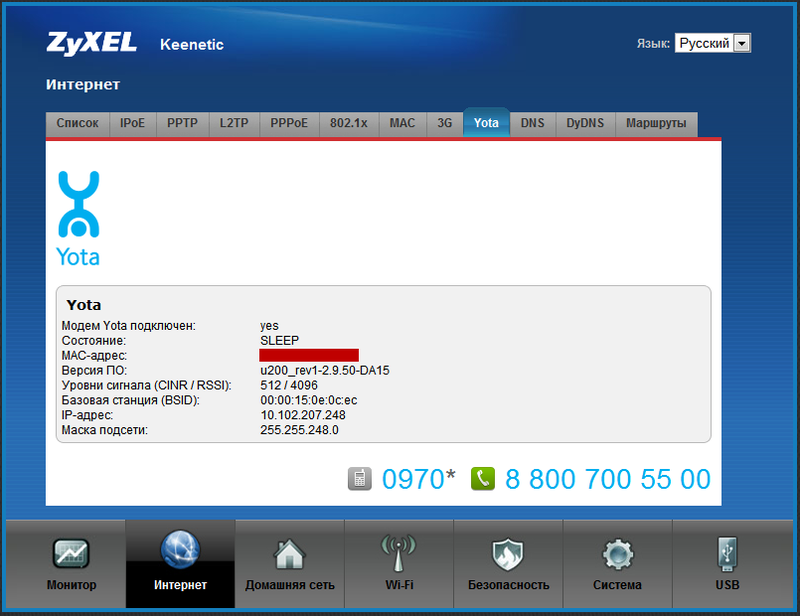
This, as far as I understood, is a very important feature of NDMS v2.00. Despite a normally working PPTP connection to the Internet, the system will immediately establish a connection with Yota, but will not use it to transfer data. The connection will be in reserve, since the default priority of the Yota interface is lower than that of the ISP and especially PPTP. A typical assignment of priorities is: ISP - 700, PPTP / L2TP / PPPoE - 1000, Yota - 400. What do these priorities mean? And that's what. If the PPTP session drops for some reason and does not recover, nothing special will happen: the system will continuously try to restore it, but it will not switch to Yota, because the priority of the physical connection to the provider's network is higher and it works. But if you pull the cable out of the WAN port, the system immediately switches to the Yotov Internet (I don’t lose any ping when I switch). Since a PPTP session can fall off with a high probability simply because of the planned work in the provider's network, it is reasonable to set a priority through the Yota connection, say, 900. Then, if the PPTP tunnel drops, the system will switch to the mobile Internet, so to speak, without hesitation. As soon as she discovers that the PPTP connection is alive, Yota will be transferred to the reserve. Unfortunately, in the current firmware there is no more accurate check of the Internet connection by periodic pinging, but let's hope that in future versions developers will add this feature. After all, reserving the connection and ensuring uninterrupted access to the Internet, I believe, is the main feature of NDMS v2.00 and this firmware, according to rumors, promises to be extended to the entire line of Keenetic routers.
By the way, to deactivate the interface (that is, so that the system stops working with it and does not react to it at all), it is enough to remove the "Enable interface" checkbox in the interface settings. For inclusion it is necessary to do the same, but in reverse order; Parameters are not erased and remain "ready."
I see no reason why we cannot add another backup connection, for example, ADSL. In the most common version, the provider also provides addresses via DHCP (with static addressing is not more difficult, but describing a little longer). To create a backup ADSL link, we need any ADSL modem with an Ethernet port and preferably with the condition that it is desirable to remove the IP address from the IP subnets configured on the Kinetics to manage the modem. But this is not fatal, since the modem will work in bridge mode. After pre-setting the ADSL connection on the modem and transferring it to bridge mode (Bridge), we connect it to a free LAN port on the router (in the current example, the LAN4 port). Next, in the settings of the Internet center, create another IPoE interface and bind it to LAN4:
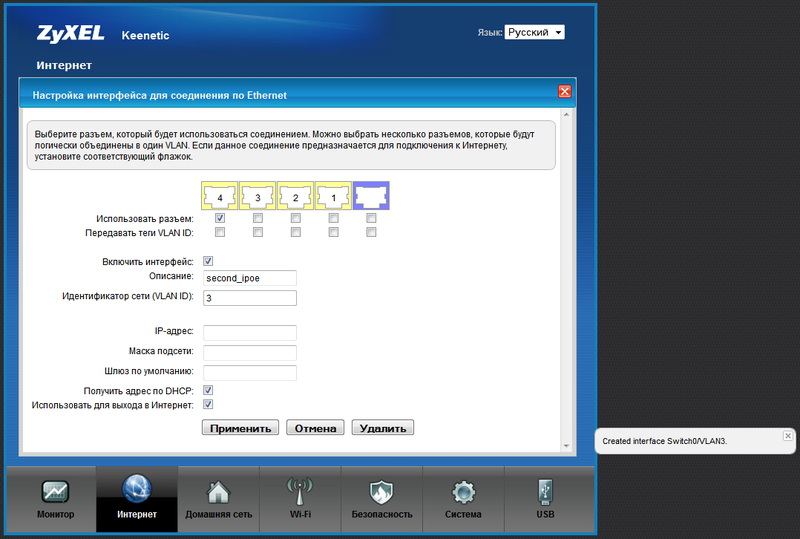
After creating the interface, it will appear in the list:
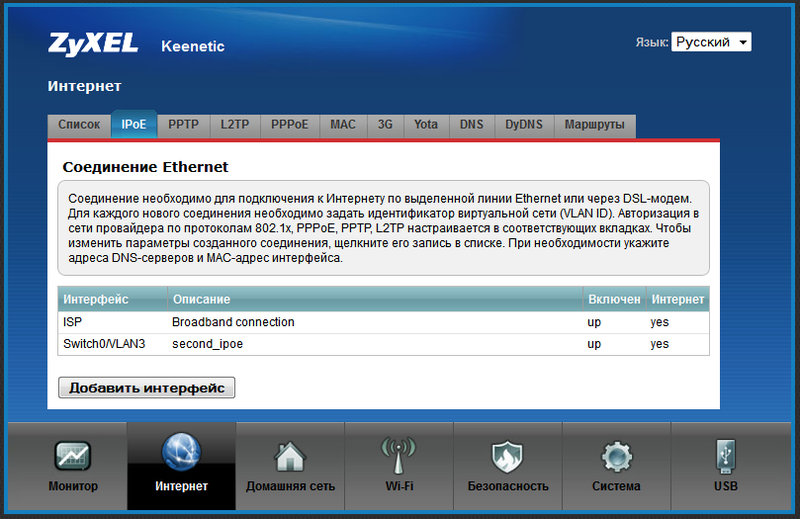
Now we can do anything with this interface (up to delete). Create a PPPoE connection through it. To do this, go to the PPPoE tab and click "Add interface". After that, we enter the data received from the provider, and save the PPPOE interface, not forgetting (!) To specify the IPoE connection created by us as the output, or, so to speak, “carrier” interface.
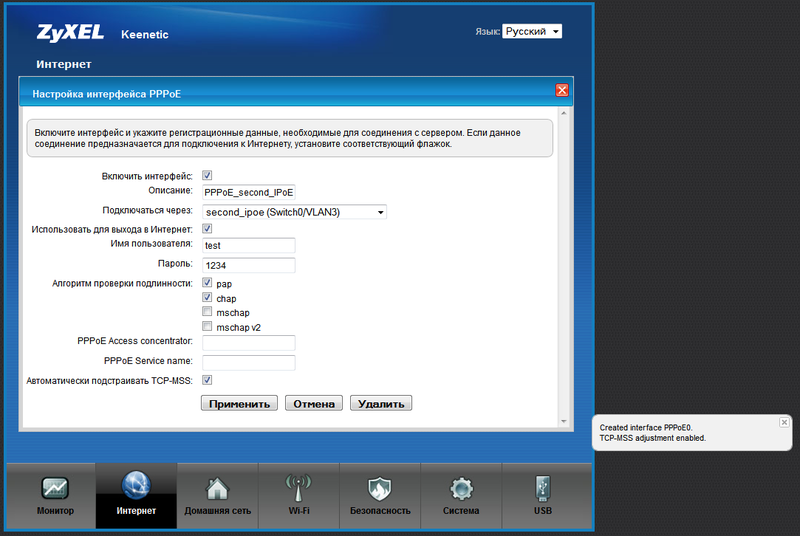
Actually, we managed to get the router authorized at the same time from three providers: via PPTP, PPPoE and Yota, in order to provide uninterrupted access to the Internet. I set up priorities in the following way, as in the screenshot:
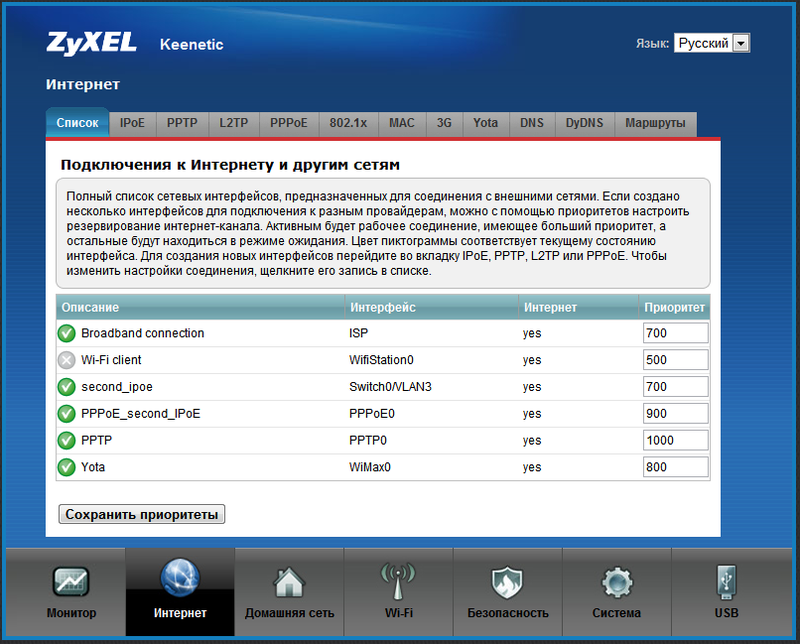
That is, the main compound is PPTP; if suddenly something happens to the connection (in particular, the link falls off), then the router will automatically switch to PPPoE. If there is any trouble, then Yota will take over. At the same time, the router will constantly try to restore PPTPoE and PPPoE connections. The WiFi client is listed by default.
One could stop at this, but I cannot but share the nontrivial knowledge of forwarding in this ports firmware. You can, of course, install the UPnP module, and let everything happen by itself, but, for example, RDP does not want to work on UPnP. In this regard, we will create a rule for port forwarding to the home server. For the scheme we have set up, the process will look like this. First, go to the “Security” tab and immediately get to the NAT tab:

Rules work only between Internet interfaces and local interfaces. We add a rule in which we specify an “Input” interface, that is, an interface to which calls will be received from the Internet (we have PPTP). Next, specify the number of the external destination port and its type (TCP or UDP). After that, we write the IP address of the internal server and, if necessary, indicate which port to transmit the request to. Port forwarding for backup connections is configured in the same way (if necessary, of course). After saving the rules, we need to allow the necessary ports to pass through the firewall of the router to the local network. This is done in the tab "Firewall":
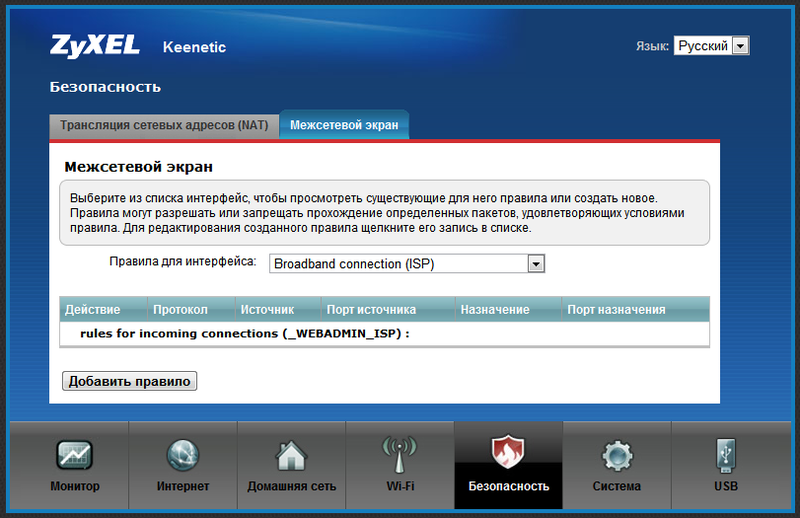
Here we can create rules for the entire device or for each interface separately. If we want to determine the interface on which the rules will spin, we must select it immediately.
In general, as it turned out, there is nothing really complicated in the settings, you just need to understand the logic of the firmware:
1. There are logical interfaces that can be tied to both physical and other logical interfaces.
2. The interface can be “for the Internet” - then the gateway it uses will be the default route for the entire system; and may be “not for the Internet” - such an interface can be used, for example, to connect to a remote network.
3. Each Internet interface has a priority, according to which they will be iterated through the reservation algorithm of the Internet channel.
I will also add that in the NDMS v2.00 firmware, an interesting and, by and large, long-term, feature that I have not previously seen in any other router or network device has appeared. This is declared support for component firmware assembly at the very beginning. That is, with the device or on the ZyXEL website, as envisioned, a basic version of the firmware is supplied, sufficient for initial configuration and access to the Internet. Having connected to the Internet, we go to the component menu and create the firmware for ourselves by installing or removing specific modules. For example, we can remove support for 3G modems, but leave support for Yota, you can remove Transmission and the WiFi client, while adding FTP and CIFS. It would be logical to leave only the type of authorization that is needed to access a particular provider, and remove the rest without regret to free up the device’s memory. I will make a reservation that at the moment you can safely leave all the components in the firmware, there is still enough space, but the developers promise support for "thick" components, such as DLNA, SIP client and other goodies. Then there will be a sense in the fine customization of the firmware.
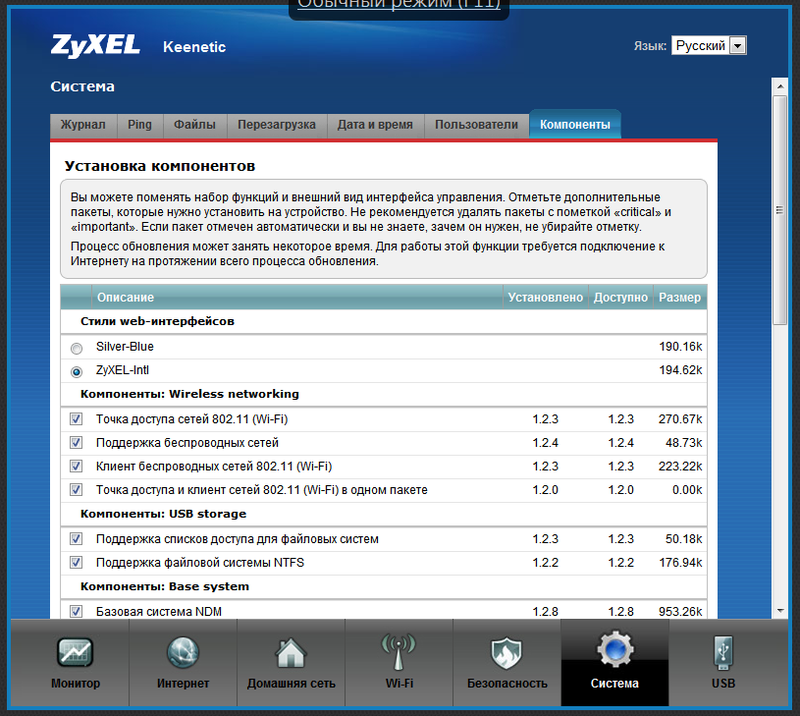

After selecting the necessary components, we press the “Apply” button and wait a couple of minutes until Keenetic receives the firmware we ordered from ZyXEL server and automatically installs it. Settings do not need to be reset.
I want to note that the choice of components is “a useful thing, but dangerous as dynamite.” There is no "fool protection" here. You can, for example, delete the component necessary for authorization in the network of your provider (which I, actually, accidentally did) and then not be able to put it back, since you no longer have access to the Internet. In this case, you will have to upload the firmware in the standard way by selecting the firmware file previously downloaded from the manufacturer’s website. Well, according to a beautiful plan - the user should never need the firmware file anymore, because here the components are not only selected again, but updated as already installed if updates are available (what the table says).
In addition to the web configurator, the command line interface (CLI) and the configuration file have been upgraded. Through the CLI, you can configure absolutely any scheme (of course, not beyond the functional limitations of the device), not subject to the web interface. I note that users who are familiar with Cisco routers, hitting the new CLI from ZyXEL, will feel like a fish in water. Here is an example of what the CLI console looks like:
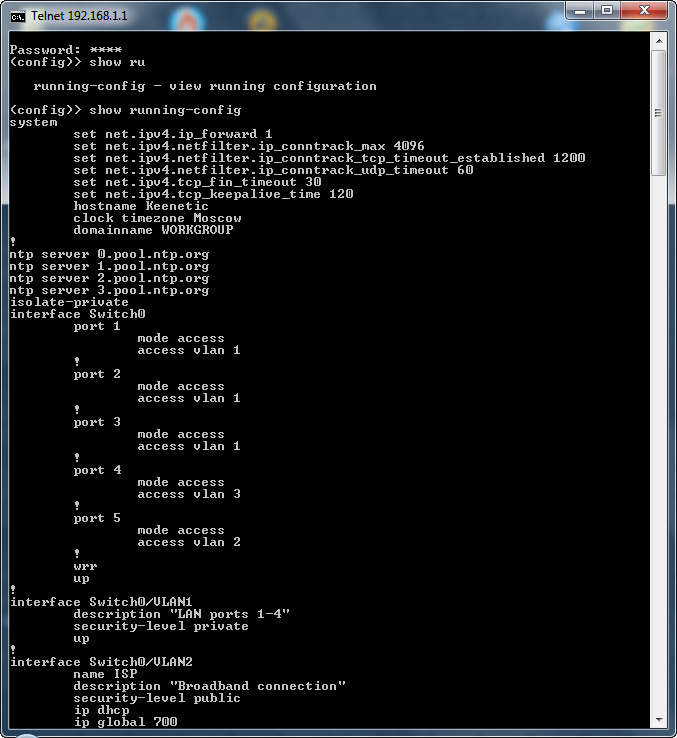
The Keenetic configuration file is now a text file that can be downloaded to your local machine, edited in any text editor and uploaded to the device. After rebooting, the device will start working with new settings.
In general, NDMS firmware v2.00 leaves a good impression and is quite efficient. The advantages include the flexibility and logic of settings that are completely uncommon for home devices, as well as the already well-functioning Internet channel reservation, which allows you to create and simultaneously use several network interfaces. These may include wired interfaces (with or without VLAN), wireless (access point or WiFi network client), connections via USB modems (3G / 4G, CDMA). The firmware supports many authorization methods for Internet access (PPPoE, L2TP, PPTP and 802.1x), as well as the creation of secure VPN tunnels based on common L2TP and PPTP protocols. For people who work remotely, now there is no need to create a secure tunnel to the office on your computer, this can be done by the router itself.
The well-proven functionality of ZyXEL Keenetic Internet Centers also seems to be in place (although so far, in beta status, judging by the forums, v2.00 does not work so smoothly). In particular, it remains possible to use the USB port of the device to connect external USB disks and printers with the ability to work with them simultaneously. There is also a built-in torrent client Transmission, and work with USB-drives via FTP.
The main disadvantage for me was the lack of support for IPTV over Wi-Fi. I will not write about minor issues and flaws here, but they certainly are. Let's wait for the firmware to exit the beta state. So far, I express my wishes and comments directly to the developers in the ICS (my.zyxel.ru) and in the relevant topic on iXBT.
PS Screenshots were taken about a month ago, since then versions of components have changed significantly. IPTV via Wi-Fi has worked, but not perfect yet.
- Full-featured NAT function (full feature NAT) with support for multiple external IP addresses; port forwarding with the ability to select a destination port in the local network; reassignment of network interface roles.
- Support for multiple PPP tunnels to access the Internet and connect to virtual private networks (VPN).
- The ability to assign several additional physical WAN interfaces to the ports of the integrated Ethernet switch.
- Internet connection reservation via 3G / 4G USB modems and additionally assigned WAN interfaces.
- Professional configuration interface via the command line (Cisco like CLI). All functions can be configured from the command line and saved as a text file.
- Batch build firmware "on demand". The functionality of the device is selected by the user in the web interface of the device and is automatically flashed.
So, the new firmware was downloaded from the ZyXEL website and successfully installed on Keenetic (there may be nuances, but they can be solved through the support of the manufacturer in a special topic and in this case are not critical). Let's get to know each other. The web configurator also opens at 192.168.1.1 with the login / password of admin / 1234. We immediately see that the new web interface has practically nothing to do with the previous version:

')
He made a double impression on me: on the one hand, he became prettier, but on the other - I had been mastering it much longer. (Looking ahead, you can add that the skin of the web interface then, in the list of components, you can choose from two options to your taste.)
Like the first generation firmware, NDMS 2.0 supports many types of connections, each of which now has a separate tab in the Internet section (IPoE, PPPoE, PPTP, L2TP, 802.1X, 3G, Yota, Wi-Fi client). Unlike V1.00, you can configure several connections at once, and in any combination. Connections are bound either to physical interfaces (Ethernet ports, USB modem, Wi-Fi interface), or to an already created logical interface (for example, you can “nest” one PPTP tunnel into another). Each Internet connection is assigned its own priority, allowing you to determine which of them will be the main and which of them will be basic, secondary or backup depending on your imagination and needs.

In the default settings, there is only one “Broadband connection (ISP)” Internet connection, which is tied to the WAN port. It brings up a DHCP client that automatically obtains an address from the provider’s network when the cable is connected to the WAN port (of course, provided that the provider issues this address). For the home network, all LAN ports of the router and the Wi-Fi access point are used by default. They are combined into one logical interface (Home VLAN), on which the DHCP server is distributed, which distributes addresses from the 192.168.1.1/24 network.

To connect to the Internet provider via PPTP, as well as via L2TP or PPPoE, you need to configure two (!) Interfaces: one to connect to the provider’s network (IPoE tab), the second is for the Internet itself. If the address in the local network of the provider is issued automatically, then the first interface can be considered already configured - this is the pre-installed Broadband Connection (ISP) interface, which is described above. If the provider has given you a static address, change the settings of the Broadband connection interface (ISP) and do not forget to set the specified DNS servers in the DNS tab. Next, open the PPTP tab (L2TP or PPPoE):

Here, in addition to the usual settings typical for mass routers, the items “Connect via” and “Use for Internet access” appeared. The first is needed to indicate to the router through which connection it should establish a PPTP connection (L2TP or PPPoE), in our case it is a Broadband connection (ISP), and the second speaks for itself: if you want to use this PPTP connection (L2TP or PPPoE ) to access the Internet, select the checkbox - then when a connection is made in the router's routing table, the default route will be the gateway of this connection. After applying the settings and connecting to the WAN port of the cable from the provider, the device will connect to the Internet. If you need to use 802.1x (there are also such providers), then it turns on even easier: as a separate connection does not appear, but comes to life on the specified interface.
In principle, we have already received a working router with access to the Internet via PPTP. But, of course, this whole vegetable garden (firmware and article about it) is not for the sake of such a banality. Now we will first look at how to connect to the Internet via USB-modems. Yota modems, as in the first firmware, are automatically recognized when plugged into the USB port, everything that is necessary for their operation is pre-configured. We take the popular Yotovsky Samsung SWC-U200 modem and stick it into the router (money in the account is not important). The connection goes unnoticed quickly, the modem flashes a blue indicator, on the status page the interface Yota merrily turns green, and the connection settings appear on the Yota tab. As we can see, the state of the modem is SLEEP, because its priority is lower by default than that of the PPTP connection that continues to work:

This, as far as I understood, is a very important feature of NDMS v2.00. Despite a normally working PPTP connection to the Internet, the system will immediately establish a connection with Yota, but will not use it to transfer data. The connection will be in reserve, since the default priority of the Yota interface is lower than that of the ISP and especially PPTP. A typical assignment of priorities is: ISP - 700, PPTP / L2TP / PPPoE - 1000, Yota - 400. What do these priorities mean? And that's what. If the PPTP session drops for some reason and does not recover, nothing special will happen: the system will continuously try to restore it, but it will not switch to Yota, because the priority of the physical connection to the provider's network is higher and it works. But if you pull the cable out of the WAN port, the system immediately switches to the Yotov Internet (I don’t lose any ping when I switch). Since a PPTP session can fall off with a high probability simply because of the planned work in the provider's network, it is reasonable to set a priority through the Yota connection, say, 900. Then, if the PPTP tunnel drops, the system will switch to the mobile Internet, so to speak, without hesitation. As soon as she discovers that the PPTP connection is alive, Yota will be transferred to the reserve. Unfortunately, in the current firmware there is no more accurate check of the Internet connection by periodic pinging, but let's hope that in future versions developers will add this feature. After all, reserving the connection and ensuring uninterrupted access to the Internet, I believe, is the main feature of NDMS v2.00 and this firmware, according to rumors, promises to be extended to the entire line of Keenetic routers.
By the way, to deactivate the interface (that is, so that the system stops working with it and does not react to it at all), it is enough to remove the "Enable interface" checkbox in the interface settings. For inclusion it is necessary to do the same, but in reverse order; Parameters are not erased and remain "ready."
I see no reason why we cannot add another backup connection, for example, ADSL. In the most common version, the provider also provides addresses via DHCP (with static addressing is not more difficult, but describing a little longer). To create a backup ADSL link, we need any ADSL modem with an Ethernet port and preferably with the condition that it is desirable to remove the IP address from the IP subnets configured on the Kinetics to manage the modem. But this is not fatal, since the modem will work in bridge mode. After pre-setting the ADSL connection on the modem and transferring it to bridge mode (Bridge), we connect it to a free LAN port on the router (in the current example, the LAN4 port). Next, in the settings of the Internet center, create another IPoE interface and bind it to LAN4:

After creating the interface, it will appear in the list:

Now we can do anything with this interface (up to delete). Create a PPPoE connection through it. To do this, go to the PPPoE tab and click "Add interface". After that, we enter the data received from the provider, and save the PPPOE interface, not forgetting (!) To specify the IPoE connection created by us as the output, or, so to speak, “carrier” interface.

Actually, we managed to get the router authorized at the same time from three providers: via PPTP, PPPoE and Yota, in order to provide uninterrupted access to the Internet. I set up priorities in the following way, as in the screenshot:

That is, the main compound is PPTP; if suddenly something happens to the connection (in particular, the link falls off), then the router will automatically switch to PPPoE. If there is any trouble, then Yota will take over. At the same time, the router will constantly try to restore PPTPoE and PPPoE connections. The WiFi client is listed by default.
One could stop at this, but I cannot but share the nontrivial knowledge of forwarding in this ports firmware. You can, of course, install the UPnP module, and let everything happen by itself, but, for example, RDP does not want to work on UPnP. In this regard, we will create a rule for port forwarding to the home server. For the scheme we have set up, the process will look like this. First, go to the “Security” tab and immediately get to the NAT tab:

Rules work only between Internet interfaces and local interfaces. We add a rule in which we specify an “Input” interface, that is, an interface to which calls will be received from the Internet (we have PPTP). Next, specify the number of the external destination port and its type (TCP or UDP). After that, we write the IP address of the internal server and, if necessary, indicate which port to transmit the request to. Port forwarding for backup connections is configured in the same way (if necessary, of course). After saving the rules, we need to allow the necessary ports to pass through the firewall of the router to the local network. This is done in the tab "Firewall":

Here we can create rules for the entire device or for each interface separately. If we want to determine the interface on which the rules will spin, we must select it immediately.
In general, as it turned out, there is nothing really complicated in the settings, you just need to understand the logic of the firmware:
1. There are logical interfaces that can be tied to both physical and other logical interfaces.
2. The interface can be “for the Internet” - then the gateway it uses will be the default route for the entire system; and may be “not for the Internet” - such an interface can be used, for example, to connect to a remote network.
3. Each Internet interface has a priority, according to which they will be iterated through the reservation algorithm of the Internet channel.
I will also add that in the NDMS v2.00 firmware, an interesting and, by and large, long-term, feature that I have not previously seen in any other router or network device has appeared. This is declared support for component firmware assembly at the very beginning. That is, with the device or on the ZyXEL website, as envisioned, a basic version of the firmware is supplied, sufficient for initial configuration and access to the Internet. Having connected to the Internet, we go to the component menu and create the firmware for ourselves by installing or removing specific modules. For example, we can remove support for 3G modems, but leave support for Yota, you can remove Transmission and the WiFi client, while adding FTP and CIFS. It would be logical to leave only the type of authorization that is needed to access a particular provider, and remove the rest without regret to free up the device’s memory. I will make a reservation that at the moment you can safely leave all the components in the firmware, there is still enough space, but the developers promise support for "thick" components, such as DLNA, SIP client and other goodies. Then there will be a sense in the fine customization of the firmware.


After selecting the necessary components, we press the “Apply” button and wait a couple of minutes until Keenetic receives the firmware we ordered from ZyXEL server and automatically installs it. Settings do not need to be reset.
I want to note that the choice of components is “a useful thing, but dangerous as dynamite.” There is no "fool protection" here. You can, for example, delete the component necessary for authorization in the network of your provider (which I, actually, accidentally did) and then not be able to put it back, since you no longer have access to the Internet. In this case, you will have to upload the firmware in the standard way by selecting the firmware file previously downloaded from the manufacturer’s website. Well, according to a beautiful plan - the user should never need the firmware file anymore, because here the components are not only selected again, but updated as already installed if updates are available (what the table says).
In addition to the web configurator, the command line interface (CLI) and the configuration file have been upgraded. Through the CLI, you can configure absolutely any scheme (of course, not beyond the functional limitations of the device), not subject to the web interface. I note that users who are familiar with Cisco routers, hitting the new CLI from ZyXEL, will feel like a fish in water. Here is an example of what the CLI console looks like:

The Keenetic configuration file is now a text file that can be downloaded to your local machine, edited in any text editor and uploaded to the device. After rebooting, the device will start working with new settings.
In general, NDMS firmware v2.00 leaves a good impression and is quite efficient. The advantages include the flexibility and logic of settings that are completely uncommon for home devices, as well as the already well-functioning Internet channel reservation, which allows you to create and simultaneously use several network interfaces. These may include wired interfaces (with or without VLAN), wireless (access point or WiFi network client), connections via USB modems (3G / 4G, CDMA). The firmware supports many authorization methods for Internet access (PPPoE, L2TP, PPTP and 802.1x), as well as the creation of secure VPN tunnels based on common L2TP and PPTP protocols. For people who work remotely, now there is no need to create a secure tunnel to the office on your computer, this can be done by the router itself.
The well-proven functionality of ZyXEL Keenetic Internet Centers also seems to be in place (although so far, in beta status, judging by the forums, v2.00 does not work so smoothly). In particular, it remains possible to use the USB port of the device to connect external USB disks and printers with the ability to work with them simultaneously. There is also a built-in torrent client Transmission, and work with USB-drives via FTP.
The main disadvantage for me was the lack of support for IPTV over Wi-Fi. I will not write about minor issues and flaws here, but they certainly are. Let's wait for the firmware to exit the beta state. So far, I express my wishes and comments directly to the developers in the ICS (my.zyxel.ru) and in the relevant topic on iXBT.
PS Screenshots were taken about a month ago, since then versions of components have changed significantly. IPTV via Wi-Fi has worked, but not perfect yet.
Source: https://habr.com/ru/post/135557/
All Articles