Authentication on CISCO network devices by means of Active Directory
Integration of CISCO AAA and Microsoft Active Directory
Surely, many system administrators sooner or later face the problem of authentication on network devices. If you are guided by best-practices, then the accounts must be personalized, the passwords must meet the criteria of stability, the lifetime of passwords should be limited. Also, let's not forget about the delimitation of access levels in accordance with the tasks performed and supporting the relevance of the user base associated with changes in staff. If these requirements are met, maintaining the user base on each device becomes a laborious and nontrivial task, but in practice it is often simply ignored, administrators are limited to setting passwords for the physical and virtual console and setting the superuser password (enable). The logical solution to this problem is to maintain a single user base with control of the requirements put forward to the accounts. If we have an Active Directory , why not use it?
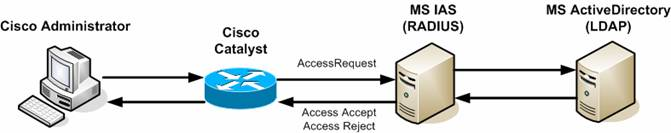
Fig.1 System Topology
Everything is not so simple - Cisco devices do not provide a mechanism for authentication by means of LDAP, which is MS ActiveDirectory, directly. To solve this problem, CISCO provides the AAA (Authentication Authorization Accounting) mechanism in its solutions. In order not to stretch the article, refer to the original source [1] for details, also a good article describes the main features [2]. In short, the AAA client sends the learned data to the authentication server, and based on its response (or no response) makes a decision to deny or provide the requested access.
As an authentication server, AAA allows you to use a RADIUS or TACAS + server. At first glance, TACAS + is preferable to the description of capabilities, but its main drawback is that it is a closed solution from CISCO and its implementation exists only for * nix systems [3]. The RADIUS protocol is an open industry standard for which there are many implementations, including the Internet Authentication Service (IAS) built into Windows Server 2000/2003. In Windows Server 2008, instead of the IAS service, the Network Policy Server service is supplied [4].
')
Topology
The system for authentication of Cisco network devices using LDAP domain Active Directory in the simplest case has the topology shown in Figure 1. The administrator connects from his workplace to the virtual terminal of the network device. According to the configured AAA policies, the device requests a login and password, and then sends the login and password hash to the RADIUS server. The RADIUS server uses Active Directory to authenticate the user and check if he is a member of the administrative group. If the user is successfully authenticated, the Cisco network device receives confirmation from the RADIUS server that authentication and authorization are successful, and allows the user to connect, otherwise reports unsuccessful authentication and closes the connection.
Authentication of users on network equipment will be done using ActiveDirectory via RADIUS, access authorization will be based on belonging to one of two groups that allow non-privileged (User exec mode) and privileged (Privilege exec mode) access to the device, respectively. In the future, you can divide access by roles by configuring profiles on devices with permission to run the necessary commands and associating each profile with the appropriate AD group.
Setup MS ActiveDirectory
We assume that security policies for the length, complexity of passwords, their lifetime, etc. have already been implemented. And so, for starters, let's create two security groups ( gsgrCiscoUserEXEC and gsgrCiscoPrivEXEC) :
Now let's create PetrovI and IvanovP administrator accounts , making them members of the gsgrCiscoUserEXEC and gsgrCiscoPrivEXEC groups, respectively. Thus, we see that PetrovI will be a non-privileged user, and IvanovP will be privileged.
On this with AD everything.
Configuring MS Internet Authentication Service
If IAS is not already installed on the server, then it must be installed. To do this, in the control panel, select “Add / remove programs” -> “Add / remove Windows components”, select the item “Network Services”, click the Details button, select the item “Internet Information Service (IIS)” and once again Click Details (Optional), select Internet Authentication Service.
Open the Internet Authentication Service snap-in and create a new Remote Access Policies -> RClick -> New Remote Access Policy) with the name CiscoAAA_AD. In the Select Attribute window that opens, select the Authentication Type and add CHAP,
The criterion is that users belong to the previously created gsgrCiscoUserEXEC group. Select the item Windows-Groups, add gsgrCiscoUserEXEC .
And most importantly, we select the attribute “Service-Type” = Login for user and Administrative for privileged access:

Fig.2. Select the attribute Service Type
At the end of the wizard, select the item “Grant remote access permission”
Now you need to create accounts for devices that will be granted access. To do this, in the IAS snap-in, select the item RADIUS Clients -> RClick -> New RADIUS Client ,
Fig.3. Create a device account
in the window that appears, enter a friendly name, for example, Switch1 and device IP address, click Next, select “Client-Vendor” = “Cisco” , enter the key for authentication of the RADIUS server and client (Fig. 4).

Fig. 4. Authentication data for RADUIS session
Setup from the IAS is completed, proceed to the configuration of network devices.
Configuring a Cisco Network Device Using the Catalyst 2960 Switch Example
!
service password-encryption
!
enable secret *******
!!! !!!
! AAA , ,
!
!
! RADIUS - ,
! , .
username recover password *********
!
aaa new-model
!. ,
aaa authentication banner ^ Access only for persons explicitly authorized. All rights reserved.
^
! .
aaa authentication fail-message ^ Authentication failed
^
!
!
aaa authentication login login-RADIUS group radius local
! .
aaa authorization exec auth-RADIUS-exec group radius local
! RADIUS.
! AD, 1
radius-server retransmit 1
! RADUIS
radius-server host 10.0.0.2
!
radius-server key SupErkEy
!
!
line vty 0 15
exec-timeout 15 0
login authentication login-RADIUS
authorization exec auth-RADIUS-exec
timeout login response 180
no password
Setup is complete, overrun testing.
We check the work
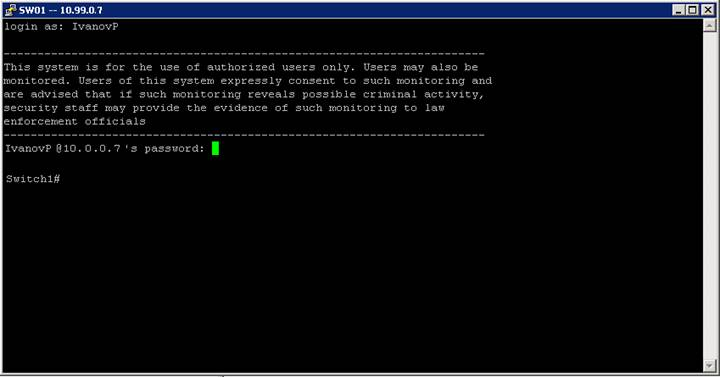
Fig. 5. Verification of work
Debugging
Not everything is always going well. In this case, you should use the Cisco IOS debug commands:
# debug radius events
# debug aaa authentication
# debug aaa authorization
# debug aaa protocols
# debug radius [authentication | elog | verbose]
And just do not forget to look at the Event log AD and IAS.
Conclusion
Thus, spending some time on centralizing accounts, we will save a lot of time in the future and reduce the risk of account compromise. In the event of an administrator’s error, it will be easy to identify the culprit for his credentials, as well as to delimit the rights of access to devices, restricting administrators to rights according to their duties
Sources
1) Authentication, Authorization, and Accounting Overview [http://www.cisco.com/en/US/products/ps6638/products_data_sheet09186a00804fe332.html]
2) Setting up AAA on CISCO - a brief overview [http://faq-cisco.ru/index.php?option=com_content&task=view&id=26&Itemid=30]
3) Remote Authentication Dial In User Service (RADIUS) [http://en.wikipedia.org/wiki/RADIUS]
4) Understanding the Windows Server 2008 Network Policy Server http://www.windowsnetworking.com/articles_tutorials/Understanding-new-Windows-Server-2008-Network-Policy-Server.html]
Source: https://habr.com/ru/post/135419/
All Articles