Storing passwords in Chrome

Hello!
Not so long ago, I had the idea of creating my own personalized program for backing up Google Chrome passwords. Yes, there are a lot of similar programs on the Internet, but the result of paranoia (that the passwords are merged onto someone's server "in reserve"), and the desire to find out what your favorite browser breathes - outweighed the balance.
')
I will tell on the basis of Windows 7.
I'll start with where the password file is stored. This file is " Login Data " in the folder " C: \ Users \ SomeUser \ AppData \ Local \ Google \ Chrome \ User Data \ Default \ ".
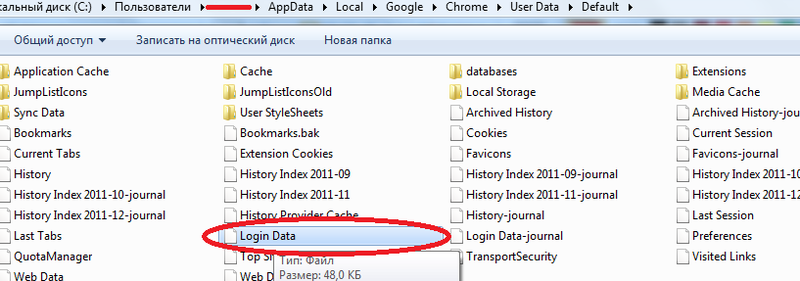
This is a SQLite database.
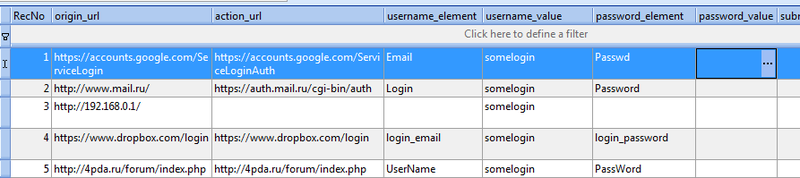
It has 14 columns. We are only interested in 3: origin_url (link to the site itself), username_value (login), password_value (password). Among other columns there is the same: authorization page, input element name for login and password, and others. All data is unencrypted (seen on the screenshot), except for the password_value field.
In the field with the password is a byte array. It looks like this.
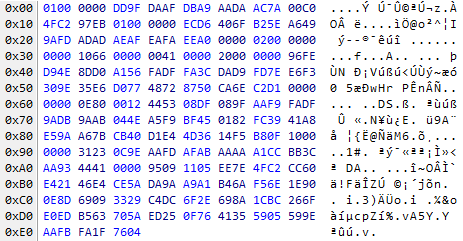
The encryption method chosen is very convenient for developers. They used the Data Protection Application Programming Interface ( an excellent article (as it turned out later, the only one) that describes how this system works ) that Windows uses.
More information in the link, especially since this encryption system deserves a separate topic. In short, I will say that this system works in one of 2 modes.
- Using a machine key.
The key is unique for the current system. But it allows different programs to work with encrypted data without transferring the key to each other, but excluding data leakage outside the machine, or rather the user. - Using a user key.
No comments.
It is also worth noting that this security system uses the well-known IE version 7 and higher. Protection in it is arranged even higher than Google Chrome. It also uses entropy, and the registry is used as a repository. Microsoft developers were pleasantly surprised.
At the end of the article is the source code of the program. Its main points, we now analyze.
So, let's begin!
We will need to read the bytes of the password field, since the password is stored in the byte array. For this, I used System.Data.SQLite Interop Library version 1.0.65.0 (available in the archive).
The project used the DPAPI class, which was found on the Internet. At the time of the creation of the project, there was no goal of writing the article, so the author of the class was lost, but I take off my hat to him - the work has been done seriously.
Let's declare the objects and variables we need:

Next we fill the DataTable DB with a database from our file:
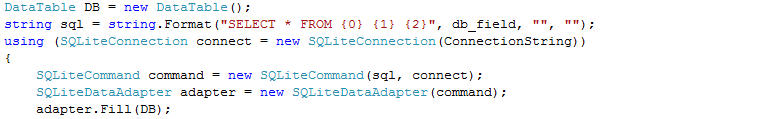
Now it remains only to pull out the necessary information from it and write to the file. At this stage, the file is no longer used - work is carried out only with the DataTable object:
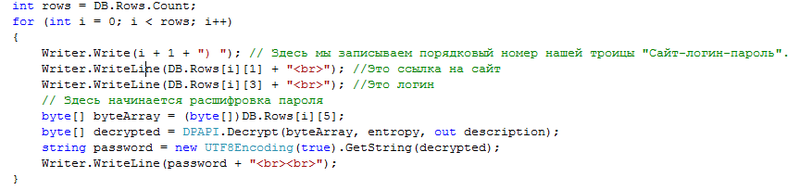
As a result, we have an HTML document with our login passwords that can be stored on your mobile phone, or printed and put into an envelope ... If you wish, you can write more fields, but I personally have enough of the above three.
If you have questions - I will answer with pleasure. Thank you very much for your attention!
Sources of the program
PS If you have a 64-bit operating system, then you should replace the library file with the one located in the root folder of the archive. I do not guarantee that this program will work on Windows XP, or other operating systems. Since it was tested only on Windows 7.
Source: https://habr.com/ru/post/134982/
All Articles