About blocking resources in Kazakhstan
In the morning a friend turned to me in the hope of getting information about blocking the Internet, arguing that I was involved in the transfer of data, and a number of resources were not available to him.
The blocking was apparently caused by unrest in a city in western Kazakhstan, I don’t want and will not discuss the legitimacy of this blockage or the events themselves, but resources are not available to subscribers of the overwhelming number of providers in the country.
I could not help, because we are not a backbone provider, but I became interested. People claim in the network that twitter does not work, check - it does not work, it works through a proxy. Okay, let's see what happens.
Traceroute in our hands.
Wonderful. We take not blocked resource. Suppose ieee.org.
Fine! The route passed through the mysterious akto-gate-1.online.kz and went to the network of Russian Golden Telecom.
Another pair of experiments indicates problems at the junction points, and only for a number of resources. Nothing new, so LJ has been blocked in Kazakhstan for several years.
Further.
People complain that youtube.com is not working.
I open it - it works, but the link to a certain video does not work.
This tells us that the system that can filter by DPI is working!
For clarity, turn on wireshark.
Does not work. Proxy no.
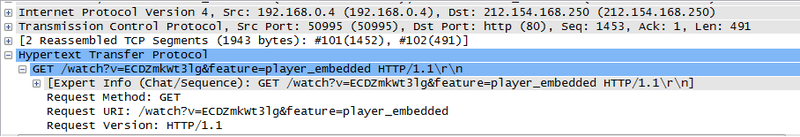
I turn on the proxy, the link works.

How the rule on the DPI can be described. Based on the experience with this functionality, I think something like this:
L3: List of IP Addresses
L7: Request URI: / watch? V = ECDZmkWt3lg & feature = player_embedded
This is done in order to reduce the load on the piece of iron, since filtering by IP first is easier than looking for a specific HTTP request in all packets.
What have my colleagues achieved?
1) I didn’t know whom to follow, and cut off the target group from the information, usually those who did not even hear the words of the proxy participate in the riots. In general, completed their work.
2) screwed up. Closed resources in such a way that it is immediately visible where and how the filter is set. In fact, they confirmed the installation of special equipment. And, after that, they officially declare that they did not close anything.
Further conclusions will not do.
UPDATE !!! Please refrain from discussing the non-technical part.
The blocking was apparently caused by unrest in a city in western Kazakhstan, I don’t want and will not discuss the legitimacy of this blockage or the events themselves, but resources are not available to subscribers of the overwhelming number of providers in the country.
I could not help, because we are not a backbone provider, but I became interested. People claim in the network that twitter does not work, check - it does not work, it works through a proxy. Okay, let's see what happens.
Traceroute in our hands.
C: \> tracert twitter.com
')
Tracing route to twitter.com [199.59.148.10]
with a maximum number of hops 30:
...
9 56 ms 58 ms 55 ms akto-gate-1.online.kz [92.47.151.170]
10 * * * timed out for the request.
Wonderful. We take not blocked resource. Suppose ieee.org.
C: \> tracert ieee.org
Tracing the route to ieee.org [140.98.193.141]
with a maximum number of hops 30:
...
10 58 ms 55 ms 58 ms akto-gate-1.online.kz [92.47.151.174]
11,140 ms 137 ms 129 ms 195.239.3.37
12,129 ms 131 ms 130 ms 195.126.105.213
13 132 ms 131 ms 131 ms xe-4-0-2.XT1.FFT1.ALTER.NET [149.227.16.73]
...
Fine! The route passed through the mysterious akto-gate-1.online.kz and went to the network of Russian Golden Telecom.
Another pair of experiments indicates problems at the junction points, and only for a number of resources. Nothing new, so LJ has been blocked in Kazakhstan for several years.
Further.
People complain that youtube.com is not working.
I open it - it works, but the link to a certain video does not work.
This tells us that the system that can filter by DPI is working!
For clarity, turn on wireshark.
Does not work. Proxy no.

I turn on the proxy, the link works.

How the rule on the DPI can be described. Based on the experience with this functionality, I think something like this:
L3: List of IP Addresses
L7: Request URI: / watch? V = ECDZmkWt3lg & feature = player_embedded
This is done in order to reduce the load on the piece of iron, since filtering by IP first is easier than looking for a specific HTTP request in all packets.
What have my colleagues achieved?
1) I didn’t know whom to follow, and cut off the target group from the information, usually those who did not even hear the words of the proxy participate in the riots. In general, completed their work.
2) screwed up. Closed resources in such a way that it is immediately visible where and how the filter is set. In fact, they confirmed the installation of special equipment. And, after that, they officially declare that they did not close anything.
Further conclusions will not do.
UPDATE !!! Please refrain from discussing the non-technical part.
Source: https://habr.com/ru/post/134767/
All Articles