NAT is not a firewall, we repeat once more
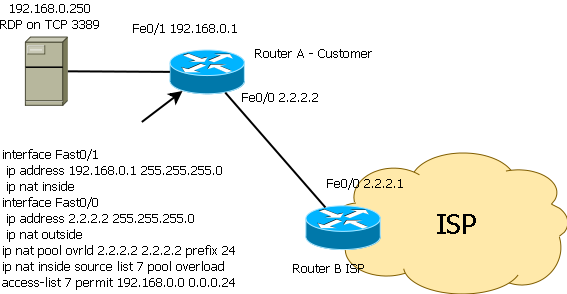
Look at the drawing. This is how classic NAT is configured on a Cisco router; let's say nothing is configured there anymore. Now answer your own question. Can anyone, under certain conditions, call from outside the RDP port (TCP 3389) of the super-secret server 192.168.0.250 and try to match the password to it. Let's clarify that the server is lonely on the network and does not turn itself anywhere (meaning that it does not have any Trojans, automatic updates and other delights).
Do you think - no? Recall a joke.
')
Lecture on philology. An old professor tells:
- In some languages of the world, double denial means agreement. In others, double negation remains negative. But, there is not a single language in the world in which double agreement means denial. Voice from the back of the desk:
- Well, yes, of course, professor.
Why not
An intelligent network engineer with a CCNP level will immediately respond — no, and justify it as follows. In order to exchange data with the host for NAT, it is necessary for NAT to create a translation. Creating a broadcast is initiated by hosts from the internal, in terms of NAT, network. The server application on TCP port 3389 itself will not go anywhere, for that it is a server one, so the broadcast will never be created, and no one will get inside. The engineer will be right. However, it does not take into account the fact that it is possible to access the host for NAT from outside with such a configuration, and after that a translation will be created through which the server will transmit data.
Why yes
Theoretically, everything is simple. Think about what will happen if the provider on your router B prescribes this route:
ip route 192.168.0.0 255.255.255.0 2.2.2.2
And there will be the following. Any provider client can send a TCP packet to IP 192.168.0.250 port 3389. This packet, according to the provider’s routing tables, will be delivered to interface FE0 / 0 of router A. What will router A do with it? What all routers are intended for is smarshrutiziruet to the host 192.168.0.250. Server 192.168.0.250 in response will send a packet to the IP address of the source that came in the original packet. Router A will create a broadcast through which data will be transmitted to the host by the source of the original packet.
And here there are difficulties. They are related to the fact that the packet goes to the IP address 192.168.0.250 port 3389, and returning from the address 2.2.2.2 and the port is not necessarily 3389. You may not believe me, but if the attacker has FreeBSD with its divert sockets, perl -a, imagination and understanding of how TCP / IP protocols work, there is nothing impossible and you can get access to the terminal of the attacked server in one day.
Talk a little more about it
When I talked about such an attack to a friend working for an ISP, he asked me a reasonable question - but would you name me at least one provider who would do this kind of thing? I used to work at the provider myself and I know that it’s nothing, but I answered with a question - do you know what source routing is, and that by default it is not disabled on Cisco routers? Do you turn it off?
When using source routing, the attack is not too complicated; it’s enough to add, as far as I remember, 5 bytes in the IP packet options.
Conclusion
Maybe the post is provocative, but I know that most networkers are not aware of such an attack and never configure a firewall when using NAT. Perhaps, after reading this post, someone will begin to follow all the recommendations for protecting the network, believe me, they are not just written like that ...
Source: https://habr.com/ru/post/134638/
All Articles