Create an RDS terminal farm using NLB technology and publish RD Web Access to ISA Server 2006
So, we want to achieve load balancing on our terminal servers, their fault tolerance, or we want to add a second server to the existing terminal server to increase the performance of the service. In my example, I will implement the following scheme:
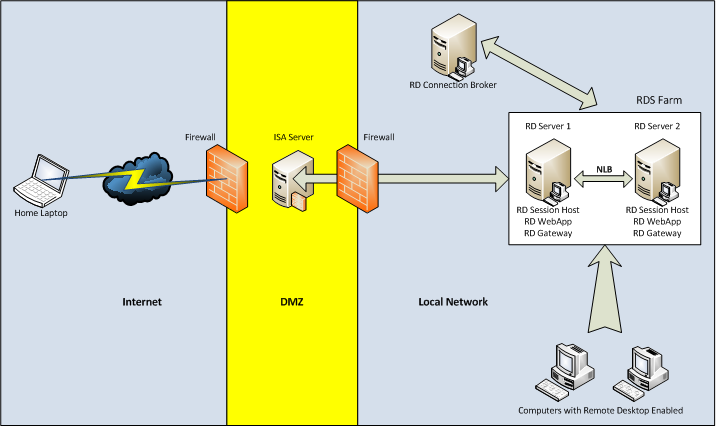
As we see, to implement such a scheme, we need three servers. Moreover, the role of the Broker can be installed on the server we already have, for example, on a file or print server. For clarity, we call our servers as follows:

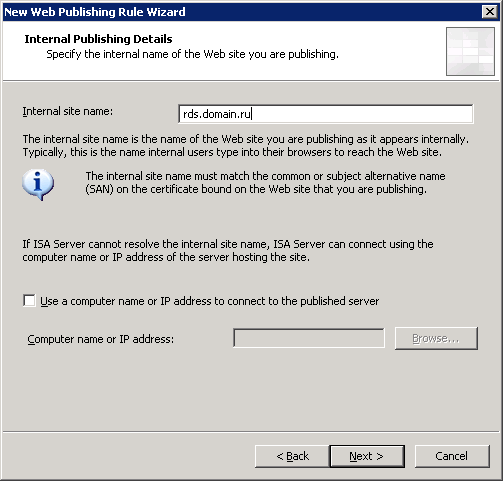
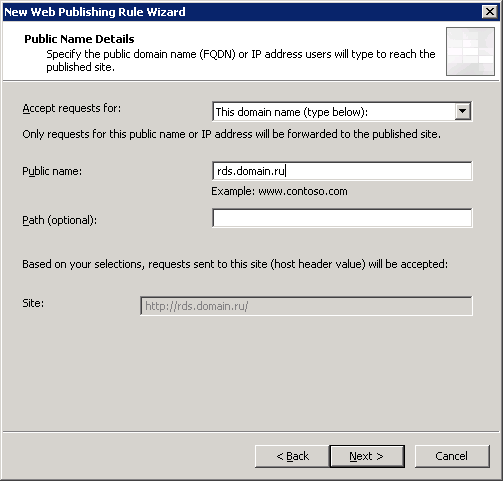
As we see, the name of our domain is domain.local. For access to terminal services outside the domain name domain.ru will be used. Thus, in our DNS domain.local domain, we will need to create an additional zone called domain.ru, where we will then create an RDS.domain.ru record that will refer to the IP address of the terminal farm.
')
- Remote Desktop Session Host (Remote Desktop Session Host)
- Remote Desktop Gateway
- Remote Desktop Web Access
- Network Policy Server (NPS)
When installing services, we tick the “Require NLA” box; the rest of the settings will be configured later. Reboot the server at the first request.
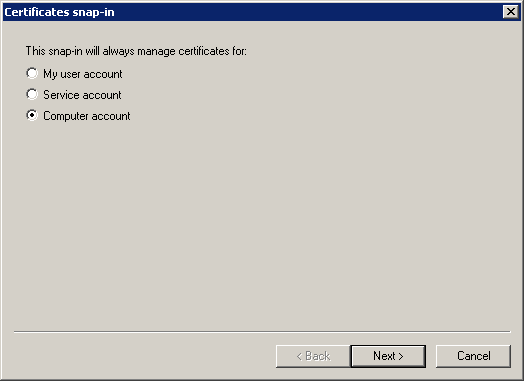
On the Digital Signature tab, we indicate the certificate that must be previously requested. To complete this step, you must have a certificate authority (CA) in your domain. On the RDS1 server, run mmc and add the Certificates (computer account) snap-in:


After receiving the certificate, export it to a pfx file — we will need it to configure the second server.
Now on the Digital Signature tab we can indicate our certificate:


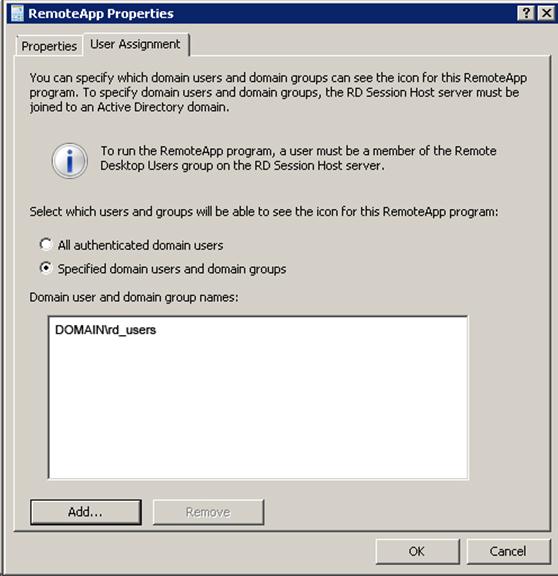
Click the "Properties" button and add to the list of users who can run our Calculator, the rd_users group.
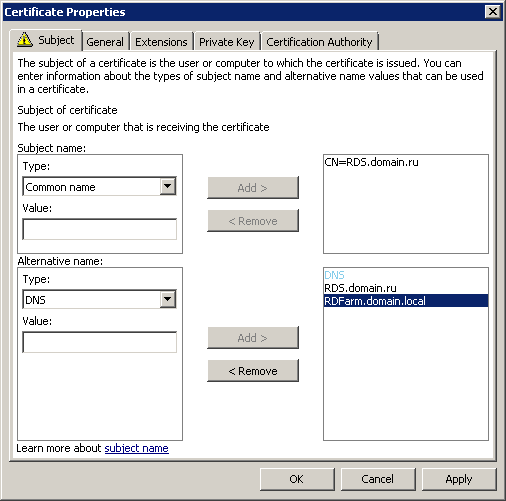

On the Private Key tab, do not forget to specify that the key can be exported.
After receiving the certificate, export it to a pfx file — we will need it to configure the second server.
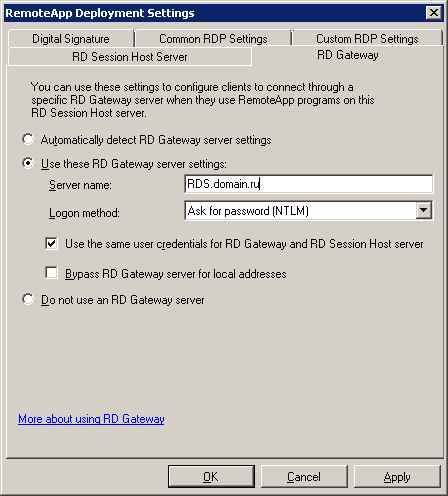
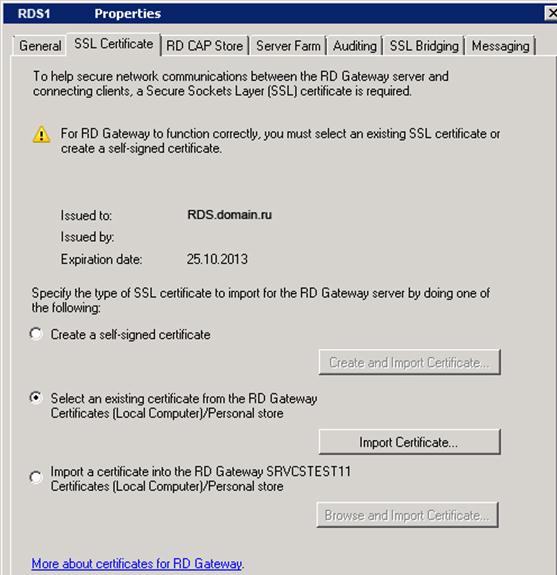
Now we specify this certificate in the properties of our remote desktop gateway:
Go to the Server Farm tab, where we will add our RDS1 server to the gateway farm:
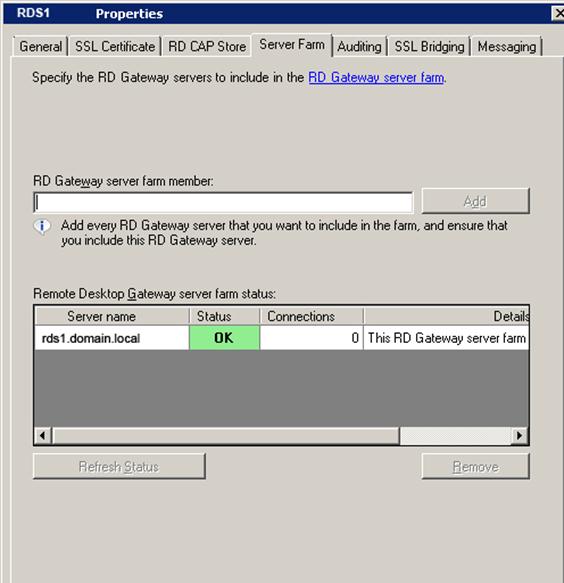
Please note that at this stage the status field does not have to be “OK”.
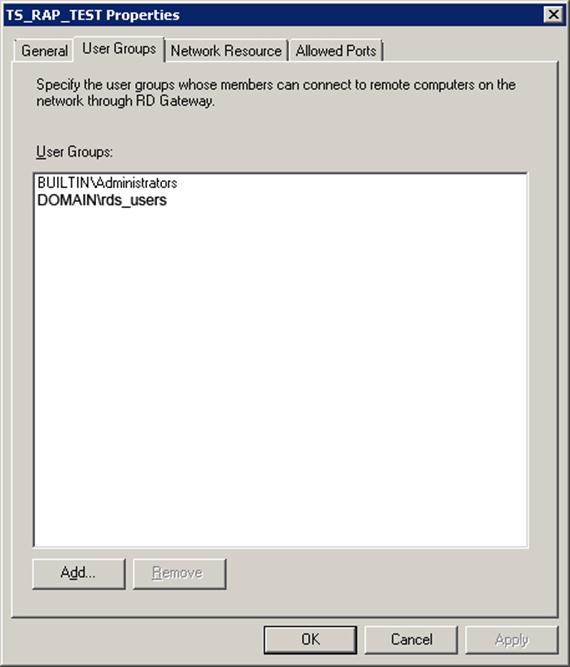
Add to the list of authorized users to connect the group rdg_users, which will include all those who need to get access to terminal services.



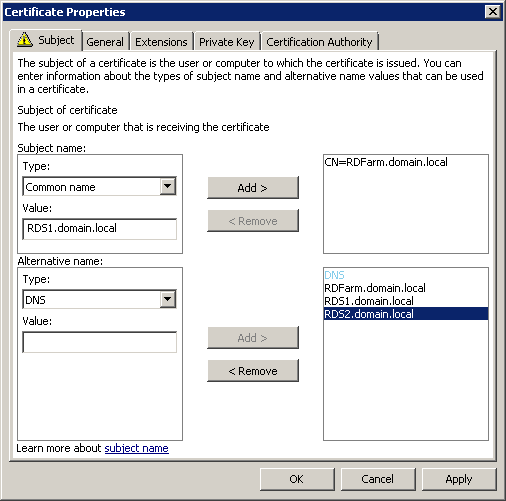
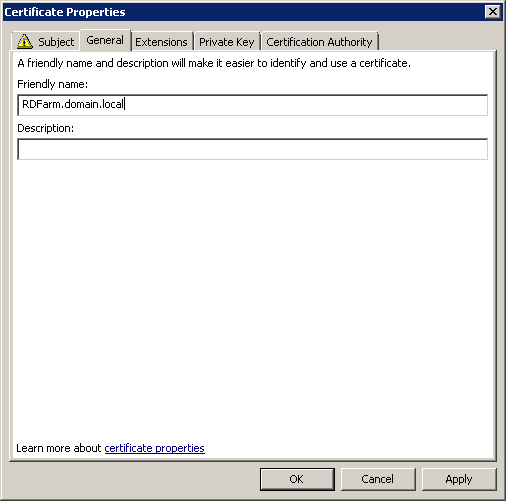
Click on the “Select” button and specify the certificate with the Common Name of our farm - RDFarm.domain.local (it was already installed on the server in paragraph 1.4).
The remaining parameters are not configurable.
Here, in RD Session Host Configuration, we configure licensing parameters.

- Remote Desktop Session Host (Remote Desktop Session Host)
- Remote Desktop Gateway
- Remote Desktop Web Access
- Network Policy Server (NPS)
When installing services, we tick the “Require NLA” box; the rest of the settings will be configured later. Reboot the server at the first request.


Specify the path to the pfx files containing the certificates and import them into the personal certificates of the RDS2 computer.
3.1 Install the RD Connection Broker role on the BROKER server.


Add all our possible RemoteApp resources: RDFarm.domain.local, RDS1.domain.local, RDS2.domain.local and RDS.domain.ru.


We include in the balancing only 443 and 3389 TCP ports.
3.8.2 Add a second computer (RDS2) to the NLB cluster
First you need to install our certificate with the Common Name "RDS.domain.ru" on the ISA server (you can do it the same way as in the case of the RDS2 server, when we transferred the certificate to it from RDS1).
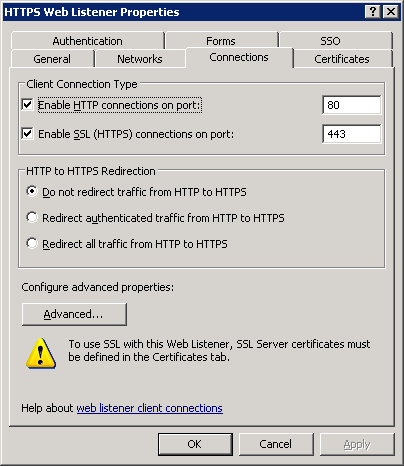
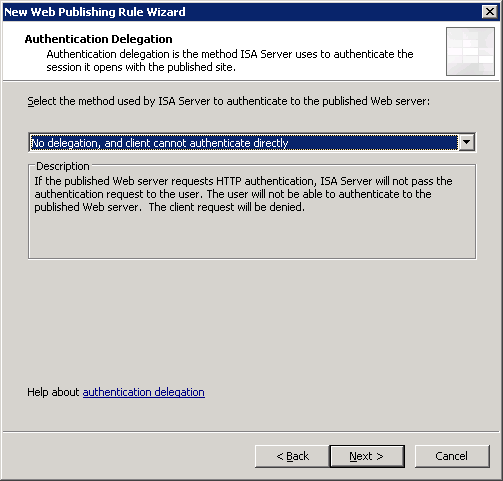
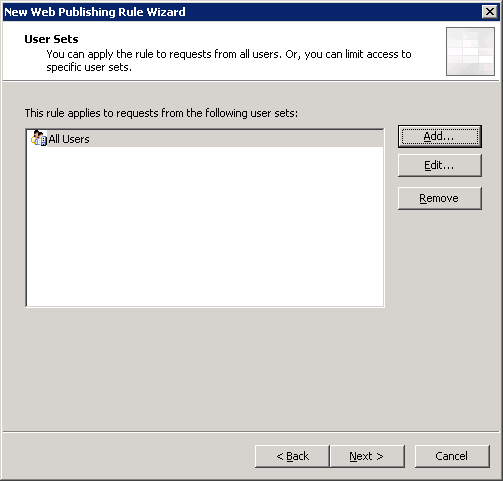
I will not discuss this section in too much detail, but I will manage only the most important screenshots with the settings of the publishing rule and the creation of a WEB listener:
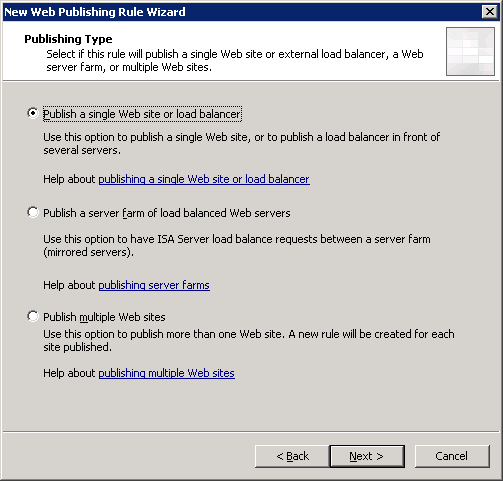
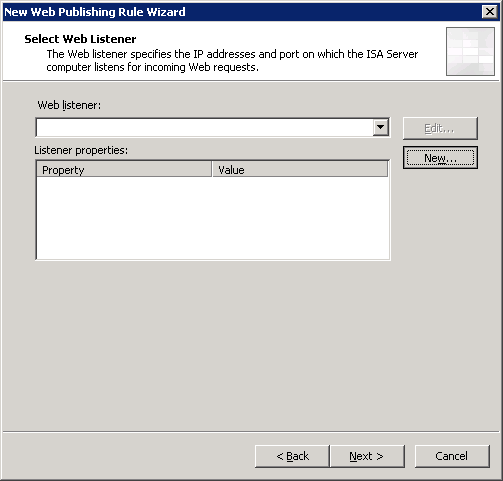
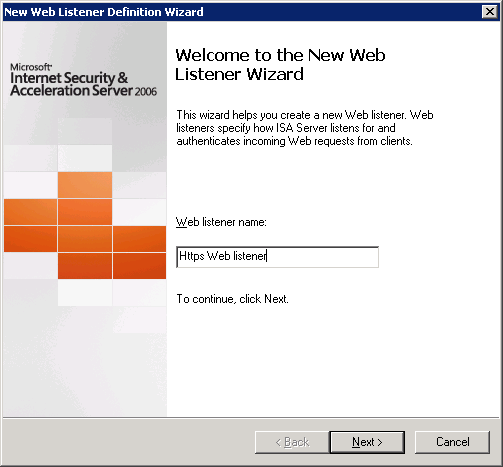


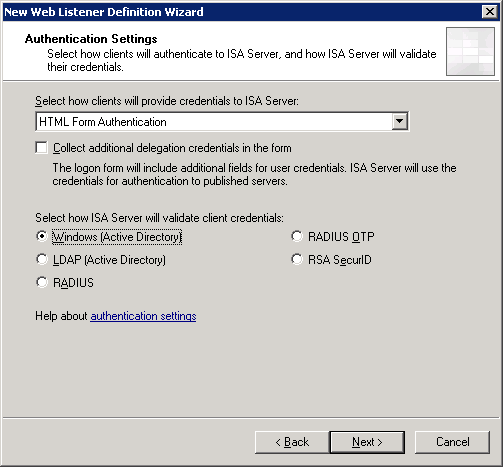
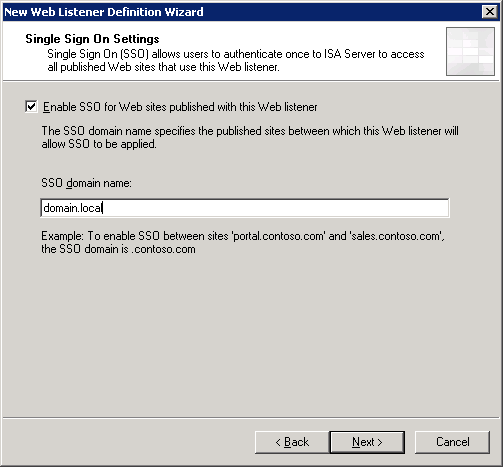

Thanks for attention.

As we see, to implement such a scheme, we need three servers. Moreover, the role of the Broker can be installed on the server we already have, for example, on a file or print server. For clarity, we call our servers as follows:

As we see, the name of our domain is domain.local. For access to terminal services outside the domain name domain.ru will be used. Thus, in our DNS domain.local domain, we will need to create an additional zone called domain.ru, where we will then create an RDS.domain.ru record that will refer to the IP address of the terminal farm.
')
1. Install terminal services on an RDS1 server.
1.1 Add the roles “Remote Desktop Services” (Remote Desktop Services) and “Network Policy and Access Services” (Network Policy and Access Services). Select the following role services for installation:
- Remote Desktop Session Host (Remote Desktop Session Host)
- Remote Desktop Gateway
- Remote Desktop Web Access
- Network Policy Server (NPS)
When installing services, we tick the “Require NLA” box; the rest of the settings will be configured later. Reboot the server at the first request.
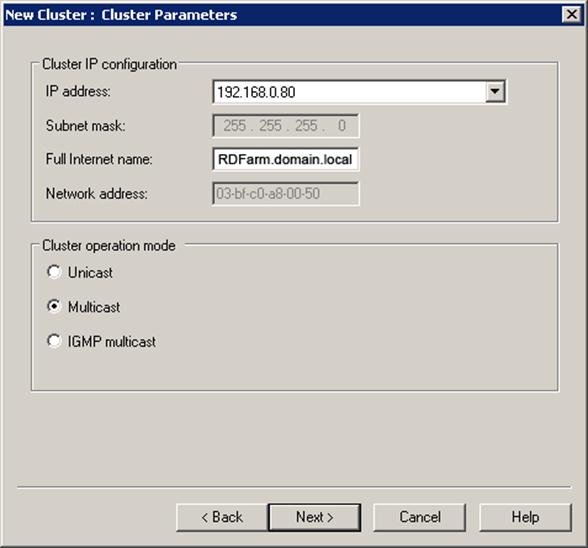
1.2 Let's create an RDFarm.domain.local record in the DNS of our domain, which will be assigned the IP address 192.168.0.80. This will be the internal address of our farm, as well as the address of the NLB cluster.
1.3 Let's create in the DNS zone domain.ru of our domain an RDS.domain.ru record, to which we will assign the same IP address as the cluster address - 192.168.0.80. This will be the external address of our farm through which remote users will log in.
1.4 Go to the Remote Desktop Services - RemoteApp Manager - RD Gateway snap-in and configure the settings as follows:

On the Digital Signature tab, we indicate the certificate that must be previously requested. To complete this step, you must have a certificate authority (CA) in your domain. On the RDS1 server, run mmc and add the Certificates (computer account) snap-in:





After receiving the certificate, export it to a pfx file — we will need it to configure the second server.
Now on the Digital Signature tab we can indicate our certificate:

1.5 Go to the Remote Desktop Services snap-in - RemoteApp Manager and in the RemoteApp Programs section and add one remote application. Let it be a calculator.

Click the "Properties" button and add to the list of users who can run our Calculator, the rd_users group.

1.6 Go to the snap-in Remote Desktop Services - RD Gateway Manager and configure the properties of RDS1 (Local). But before that, you need to request another certificate (see clause 1.4), but this time with the Common Name of the external address - RDS.domain.ru.


On the Private Key tab, do not forget to specify that the key can be exported.
After receiving the certificate, export it to a pfx file — we will need it to configure the second server.
Now we specify this certificate in the properties of our remote desktop gateway:

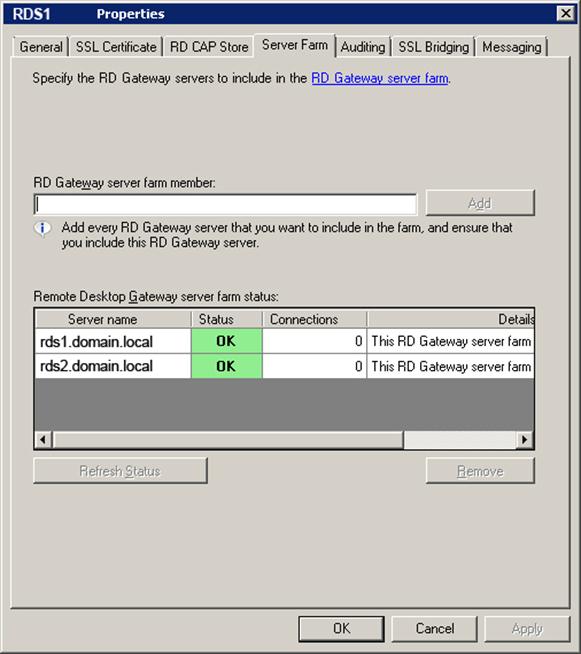
Go to the Server Farm tab, where we will add our RDS1 server to the gateway farm:

Please note that at this stage the status field does not have to be “OK”.
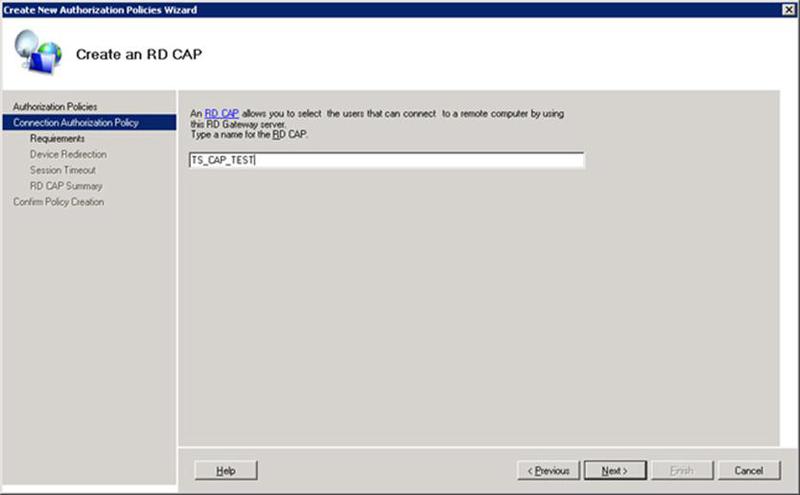
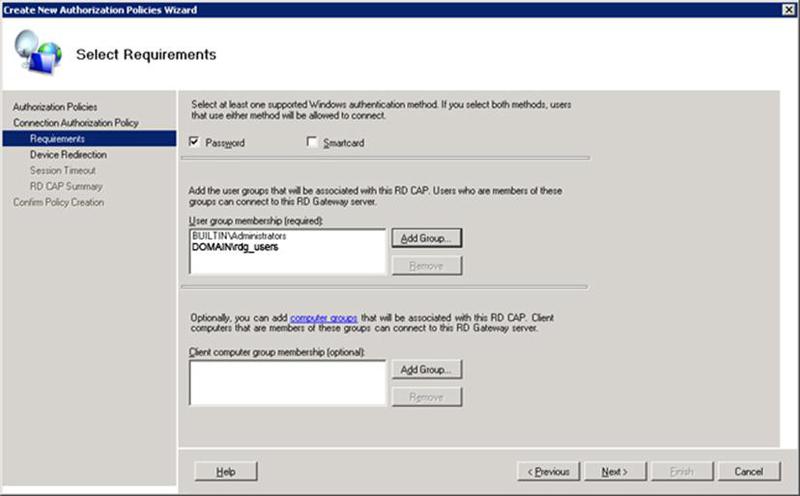
1.7 Go to the Remote Desktop Services - RD Gateway Manager - RDS1 (Local) - Policies - Connection Authorization Policies snap-in and create a connection authorization policy using the wizard:

Add to the list of authorized users to connect the group rdg_users, which will include all those who need to get access to terminal services.

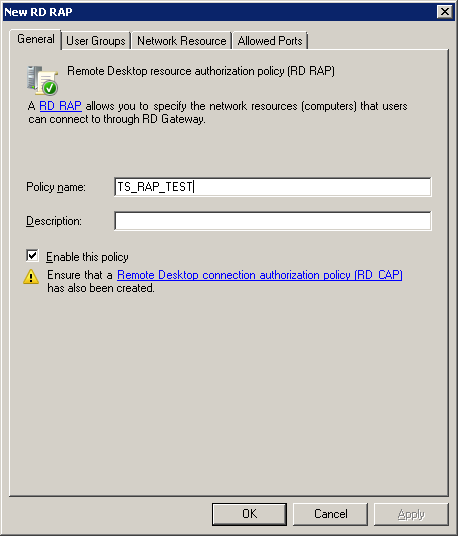
1.8 Go to the snap-in Remote Desktop Services - RD Gateway Manager - RDS1 (Local) - Policies - Resource Authorization Policies and create an application authorization policy bypassing the wizard (Create New Policy - Custom):




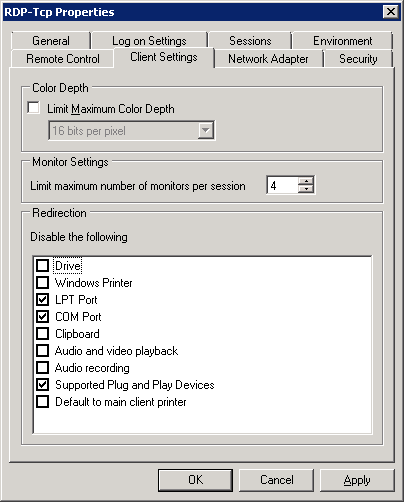
1.9 Go to the Remote Desktop Services - RD Session Host Configuration snap-in and configure the RDP-Tcp connection properties as follows:

Click on the “Select” button and specify the certificate with the Common Name of our farm - RDFarm.domain.local (it was already installed on the server in paragraph 1.4).

The remaining parameters are not configurable.
Here, in RD Session Host Configuration, we configure licensing parameters.

1.10 To check the settings of the RemoteApp application, go to localhost / RDWeb
2. Install terminal services on an RDS2 server.
2.1 Add the roles “Remote Desktop Services” (Remote Desktop Services) and “Network Policy and Access Services” (Network Policy and Access Services). Select the following role services for installation:
- Remote Desktop Session Host (Remote Desktop Session Host)
- Remote Desktop Gateway
- Remote Desktop Web Access
- Network Policy Server (NPS)
When installing services, we tick the “Require NLA” box; the rest of the settings will be configured later. Reboot the server at the first request.
2.2 Configure the second RDS2 server in the same way as our first server is configured, except that you do not need to request certificates - they must be imported from the RDS1 server. To import certificates, run mmc and add the Certificates (computer account) snap-in:


Specify the path to the pfx files containing the certificates and import them into the personal certificates of the RDS2 computer.
3. Creating and configuring a terminal farm.
3.1 Install the RD Connection Broker role on the BROKER server.
3.2 Add the RDS1 and RDS2 servers to the Session Broker Computers local group on the BROKER server.
3.3 We add all our three servers to the TS Web Access Computers local group on the RDS1 and RDS2 servers
3.4 On the BROKER server, we add our RDS1 and RDS2 servers to the RD Web Access group (Admin Tools> Remote Desktop Services> Remote Desktop Connection Manager> Add RD Web Access Server).
3.5 First on the RDS1 server and then on the RDS2, go to Remote Desktop Services> Remote Desktop Session Host Configuration and change the settings of the RD Connection Broker:

3.6 Configuring RemoteApp applications to work with our farm. To do this, on the RDS1 and RDS2 servers, go to Remote Desktop Services> RemoteApp Manager and change the Server Name parameter:

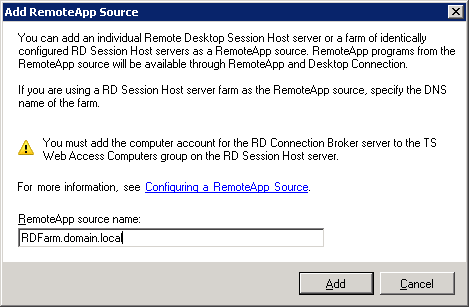
3.7 On the BROKER server, go to Remote Desktop Services> Remote Desktop Connection Manager> RemoteApp Sources and click the button "Add RemoteApp Source ...":

Add all our possible RemoteApp resources: RDFarm.domain.local, RDS1.domain.local, RDS2.domain.local and RDS.domain.ru.
3.8 Create an NLB cluster.
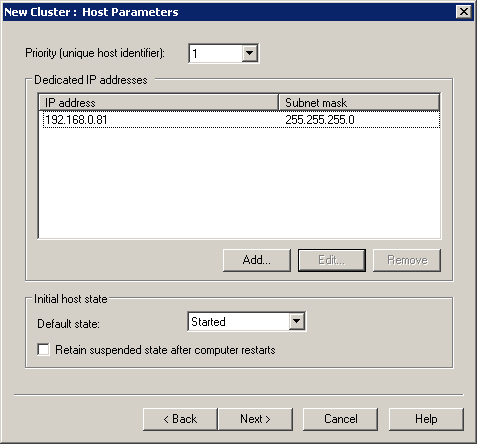
3.8.1 Install the Network Load Balancing component on RDS1 and RDS2 servers. Next, open the Network Load Balancing Manager snap-in on the RDS1 server and create a cluster:




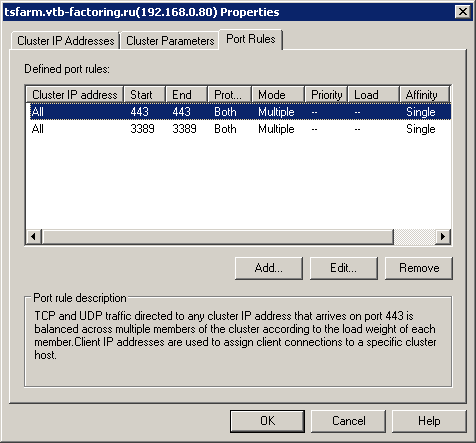
We include in the balancing only 443 and 3389 TCP ports.

3.8.2 Add a second computer (RDS2) to the NLB cluster
3.9 Make sure that on the RDS1 and RDS2 servers, in the properties of the RD Gateway Manager server, both our servers are listed on the Server Farm tab:

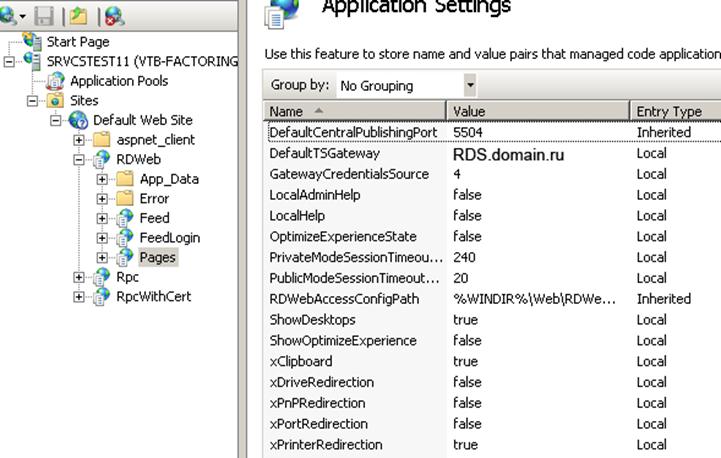
3.10 On the RDS1 and RDS2 servers, go to the IIS Manager snap-in, then Sites - Default Web Site - RDWeb - Pages and on the right click Application Settings, where we set the DefaultTSGateway parameter to RDS.domain.ru:

4. Publish the RemoteApp application farm on ISA Server.
First you need to install our certificate with the Common Name "RDS.domain.ru" on the ISA server (you can do it the same way as in the case of the RDS2 server, when we transferred the certificate to it from RDS1).
I will not discuss this section in too much detail, but I will manage only the most important screenshots with the settings of the publishing rule and the creation of a WEB listener:















Thanks for attention.
Source: https://habr.com/ru/post/134456/
All Articles