Yota, Dlink or hidden BotNet?
It all started 1 month ago. Customers of our company began to experience problems with access to the Internet. The problem manifests itself only in customers using routers and STB consoles. During the day, at various times, surges of activity of 5–10 minutes were recorded on the equipment. Bursts could occur at any time of the day in the morning, afternoon and evening. An example of such a surge, I will show.
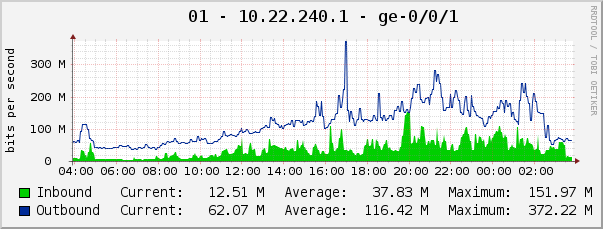
The company's engineers for 2 weeks tried to catch the problem and used all possible means. Elementary trafshow within the framework of multicast on VLAN and on the port did not show any kind of activity. Catching something left on Juniper and Cisco also failed. We observed activity only within TCP sessions on all ports of the head routers. There were no mistakes. Routers on the house (each client has a managed port) were not more than 15% of the CPU load in the normal activity. One of the clients showed a very interesting activity on the port at the time of the peak, his antivirus produced an error, within which we began work.
')
At the very beginning, we sinned on the work of setting up our routing, errors in multicast IPTV, tried to find where we cant, changed the ACL, smoked manuals and tried to solve the problem through Dlink support. Nothing led to the desired result, Dlink responded as always “show the config”. It was decided to create your own stand using the same equipment. We made a bunch of Juniper EX-4200 - DGS-3627 - DES-3200-100 - client port Dlink DIR-300. We set up the computer and within one of the problematic VLANs we began to analyze all incoming and outgoing packets. Because of this, we got a very interesting activity at the time of the burst.
210 192.168.0.108 192.168.0.1 DNS 74 Standard query A rcmlic.roox.ru
211 192.168.0.1 192.168.0.108 DNS 146 Standard query response, No such name
212 192.168.0.108 192.168.0.255 NBNS 92 Name query NB RCMLIC.ROOX.RU <00>
213 192.168.0.108 192.168.0.1 DNS 74 Standard query A rcmlic.roox.ru
214 192.168.0.1 192.168.0.108 DNS 146 Standard query response, No such name
215 192.168.0.108 192.168.0.255 NBNS 92 Name query NB RCMLIC.ROOX.RU <00>
216 192.168.0.108 192.168.0.1 DNS 74 Standard query A rcmlic.roox.ru
217 192.168.0.1 192.168.0.108 DNS 146 Standard query response, No such name
218 192.168.0.108 192.168.0.255 NBNS 92 Name query NB RCMLIC.ROOX.RU <00>
219 192.168.0.108 192.168.0.1 DNS 74 Standard query A rcmlic.roox.ru
220 192.168.0.1 192.168.0.108 DNS 146 Standard query response, No such name
221 192.168.0.108 192.168.0.255 NBNS 92 Name query NB RCMLIC.ROOX.RU <00>
222 192.168.0.108 192.168.0.1 DNS 74 Standard query A rcmlic.roox.ru
223 192.168.0.1 192.168.0.108 DNS 146 Standard query response, No such name
224 192.168.0.108 192.168.0.255 NBNS 92 Name query NB RCMLIC.ROOX.RU <00>
it happened about 10,000 times per second (just not counted)
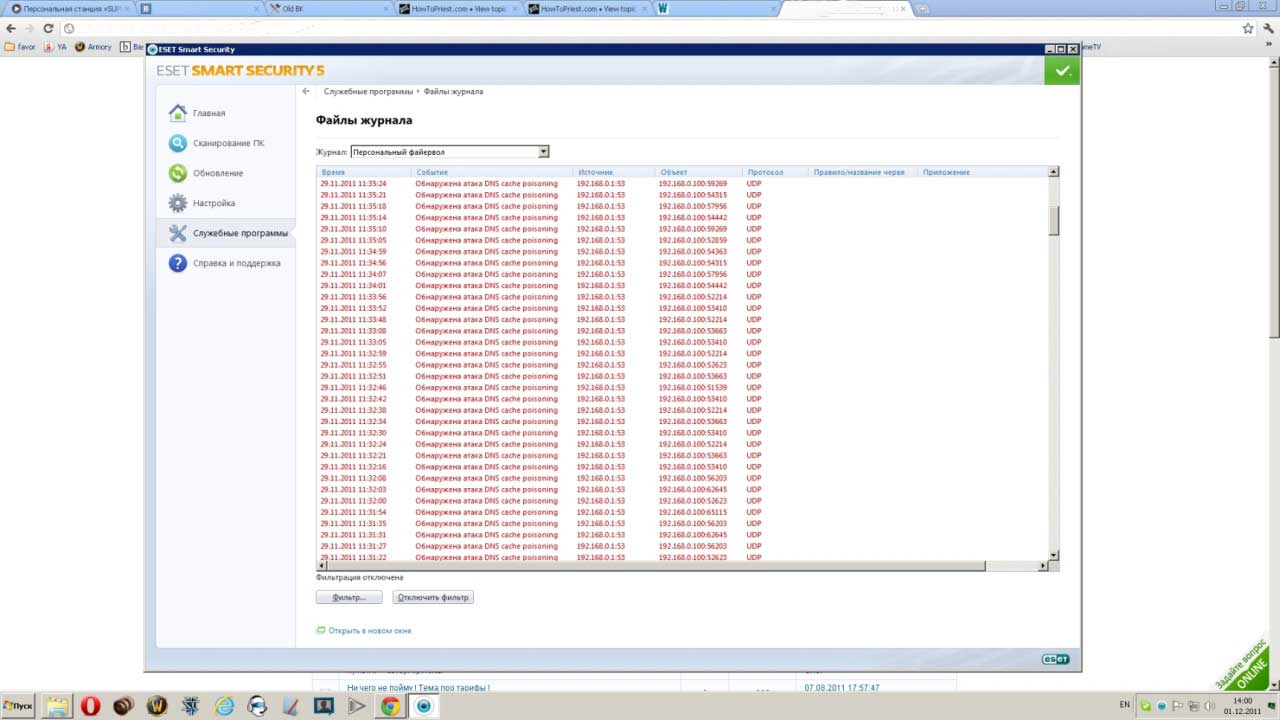
Very interesting DNS agree? We heard about Yota but we never heard about ROOX? We turned the DNS on ourselves. In the server logs, where these computers began to turn, the log was received:
*. *. 238.110 - - [10 / Dec / 2011: 22: 58: 34 +0300] “POST / YA / PushReport / HTTP / 1.1” 404 293 "-" "Yota Access / YD1.14.0.2660 (Windows 6.1 .7601 x64) »
*. *. 238.110 - - [10 / Dec / 2011: 22: 58: 34 +0300] “POST / YA / PushReport / HTTP / 1.1” 404 293 "-" "Yota Access / YD1.14.0.2660 (Windows 6.1 .7601 x64) »
*. *. 238.110 - - [10 / Dec / 2011: 22: 58: 34 +0300] “POST / YA / PushReport / HTTP / 1.1” 404 293 "-" "Yota Access / YD1.14.0.2660 (Windows 6.1 .7601 x64) »
*. *. 238.110 - - [10 / Dec / 2011: 22: 58: 34 +0300] “POST / YA / PushReport / HTTP / 1.1” 404 293 "-" "Yota Access / YD1.14.0.2660 (Windows 6.1 .7601 x64) »
*. *. 238.110 - - [10 / Dec / 2011: 22: 58: 34 +0300] “POST / YA / PushReport / HTTP / 1.1” 404 293 "-" "Yota Access / YD1.14.0.2660 (Windows 6.1 .7601 x64) »
*. *. 238.110 - - [10 / Dec / 2011: 22: 58: 34 +0300] “POST / YA / PushReport / HTTP / 1.1” 404 293 "-" "Yota Access / YD1.14.0.2660 (Windows 6.1 .7601 x64) »
*. *. 238.110 - - [10 / Dec / 2011: 22: 58: 34 +0300] “POST / YA / PushReport / HTTP / 1.1” 404 293 "-" "Yota Access / YD1.14.0.2660 (Windows 6.1 .7601 x64) »
*. *. 238.110 - - [10 / Dec / 2011: 22: 58: 34 +0300] “POST / YA / PushReport / HTTP / 1.1” 404 293 "-" "Yota Access / YD1.14.0.2660 (Windows 6.1 .7601 x64) »
*. *. 238.110 - - [10 / Dec / 2011: 22: 58: 34 +0300] “POST / YA / PushReport / HTTP / 1.1” 404 293 "-" "Yota Access / YD1.14.0.2660 (Windows 6.1 .7601 x64) »
*. *. 238.110 - - [10 / Dec / 2011: 22: 58: 34 +0300] “POST / YA / PushReport / HTTP / 1.1” 404 293 "-" "Yota Access / YD1.14.0.2660 (Windows 6.1 .7601 x64) »
*. *. 238.110 - - [10 / Dec / 2011: 22: 58: 34 +0300] “POST / YA / PushReport / HTTP / 1.1” 404 293 "-" "Yota Access / YD1.14.0.2660 (Windows 6.1 .7601 x64) »
*. *. 238.110 - - [10 / Dec / 2011: 22: 58: 34 +0300] “POST / YA / PushReport / HTTP / 1.1” 404 293 "-" "Yota Access / YD1.14.0.2660 (Windows 6.1 .7601 x64) »
*. *. 238.110 - - [10 / Dec / 2011: 22: 58: 34 +0300] “POST / YA / PushReport / HTTP / 1.1” 404 293 "-" "Yota Access / YD1.14.0.2660 (Windows 6.1 .7601 x64) »
*. *. 238.110 - - [10 / Dec / 2011: 22: 58: 34 +0300] “POST / YA / PushReport / HTTP / 1.1” 404 293 "-" "Yota Access / YD1.14.0.2660 (Windows 6.1 .7601 x64) »
*. *. 238.110 - - [10 / Dec / 2011: 22: 58: 34 +0300] “POST / YA / PushReport / HTTP / 1.1” 404 293 "-" "Yota Access / YD1.14.0.2660 (Windows 6.1 .7601 x64) »
*. *. 238.110 - - [10 / Dec / 2011: 22: 58: 34 +0300] “POST / YA / PushReport / HTTP / 1.1” 404 293 "-" "Yota Access / YD1.14.0.2660 (Windows 6.1 .7601 x64) »
*. *. 238.110 - - [10 / Dec / 2011: 22: 58: 34 +0300] “POST / YA / PushReport / HTTP / 1.1” 404 293 "-" "Yota Access / YD1.14.0.2660 (Windows 6.1 .7601 x64) »
This is only one client within milliseconds. In my opinion, the Yota application behaves in a very interesting way, generating huge activity within one millisecond. Maybe he polls who ddit? And all Yota carriers are potential ddosers? I would like to bring this question to Habr, since here are the most correct users of the network.
PS After the turn of the DNS, the burst activity ceased. Remained and growing only a huge log on the server. We have solved the problem of a larger botnet on the network or what is it?

Job went
The company's engineers for 2 weeks tried to catch the problem and used all possible means. Elementary trafshow within the framework of multicast on VLAN and on the port did not show any kind of activity. Catching something left on Juniper and Cisco also failed. We observed activity only within TCP sessions on all ports of the head routers. There were no mistakes. Routers on the house (each client has a managed port) were not more than 15% of the CPU load in the normal activity. One of the clients showed a very interesting activity on the port at the time of the peak, his antivirus produced an error, within which we began work.

')
Little fun
At the very beginning, we sinned on the work of setting up our routing, errors in multicast IPTV, tried to find where we cant, changed the ACL, smoked manuals and tried to solve the problem through Dlink support. Nothing led to the desired result, Dlink responded as always “show the config”. It was decided to create your own stand using the same equipment. We made a bunch of Juniper EX-4200 - DGS-3627 - DES-3200-100 - client port Dlink DIR-300. We set up the computer and within one of the problematic VLANs we began to analyze all incoming and outgoing packets. Because of this, we got a very interesting activity at the time of the burst.
210 192.168.0.108 192.168.0.1 DNS 74 Standard query A rcmlic.roox.ru
211 192.168.0.1 192.168.0.108 DNS 146 Standard query response, No such name
212 192.168.0.108 192.168.0.255 NBNS 92 Name query NB RCMLIC.ROOX.RU <00>
213 192.168.0.108 192.168.0.1 DNS 74 Standard query A rcmlic.roox.ru
214 192.168.0.1 192.168.0.108 DNS 146 Standard query response, No such name
215 192.168.0.108 192.168.0.255 NBNS 92 Name query NB RCMLIC.ROOX.RU <00>
216 192.168.0.108 192.168.0.1 DNS 74 Standard query A rcmlic.roox.ru
217 192.168.0.1 192.168.0.108 DNS 146 Standard query response, No such name
218 192.168.0.108 192.168.0.255 NBNS 92 Name query NB RCMLIC.ROOX.RU <00>
219 192.168.0.108 192.168.0.1 DNS 74 Standard query A rcmlic.roox.ru
220 192.168.0.1 192.168.0.108 DNS 146 Standard query response, No such name
221 192.168.0.108 192.168.0.255 NBNS 92 Name query NB RCMLIC.ROOX.RU <00>
222 192.168.0.108 192.168.0.1 DNS 74 Standard query A rcmlic.roox.ru
223 192.168.0.1 192.168.0.108 DNS 146 Standard query response, No such name
224 192.168.0.108 192.168.0.255 NBNS 92 Name query NB RCMLIC.ROOX.RU <00>
it happened about 10,000 times per second (just not counted)
Very interesting DNS agree? We heard about Yota but we never heard about ROOX? We turned the DNS on ourselves. In the server logs, where these computers began to turn, the log was received:
*. *. 238.110 - - [10 / Dec / 2011: 22: 58: 34 +0300] “POST / YA / PushReport / HTTP / 1.1” 404 293 "-" "Yota Access / YD1.14.0.2660 (Windows 6.1 .7601 x64) »
*. *. 238.110 - - [10 / Dec / 2011: 22: 58: 34 +0300] “POST / YA / PushReport / HTTP / 1.1” 404 293 "-" "Yota Access / YD1.14.0.2660 (Windows 6.1 .7601 x64) »
*. *. 238.110 - - [10 / Dec / 2011: 22: 58: 34 +0300] “POST / YA / PushReport / HTTP / 1.1” 404 293 "-" "Yota Access / YD1.14.0.2660 (Windows 6.1 .7601 x64) »
*. *. 238.110 - - [10 / Dec / 2011: 22: 58: 34 +0300] “POST / YA / PushReport / HTTP / 1.1” 404 293 "-" "Yota Access / YD1.14.0.2660 (Windows 6.1 .7601 x64) »
*. *. 238.110 - - [10 / Dec / 2011: 22: 58: 34 +0300] “POST / YA / PushReport / HTTP / 1.1” 404 293 "-" "Yota Access / YD1.14.0.2660 (Windows 6.1 .7601 x64) »
*. *. 238.110 - - [10 / Dec / 2011: 22: 58: 34 +0300] “POST / YA / PushReport / HTTP / 1.1” 404 293 "-" "Yota Access / YD1.14.0.2660 (Windows 6.1 .7601 x64) »
*. *. 238.110 - - [10 / Dec / 2011: 22: 58: 34 +0300] “POST / YA / PushReport / HTTP / 1.1” 404 293 "-" "Yota Access / YD1.14.0.2660 (Windows 6.1 .7601 x64) »
*. *. 238.110 - - [10 / Dec / 2011: 22: 58: 34 +0300] “POST / YA / PushReport / HTTP / 1.1” 404 293 "-" "Yota Access / YD1.14.0.2660 (Windows 6.1 .7601 x64) »
*. *. 238.110 - - [10 / Dec / 2011: 22: 58: 34 +0300] “POST / YA / PushReport / HTTP / 1.1” 404 293 "-" "Yota Access / YD1.14.0.2660 (Windows 6.1 .7601 x64) »
*. *. 238.110 - - [10 / Dec / 2011: 22: 58: 34 +0300] “POST / YA / PushReport / HTTP / 1.1” 404 293 "-" "Yota Access / YD1.14.0.2660 (Windows 6.1 .7601 x64) »
*. *. 238.110 - - [10 / Dec / 2011: 22: 58: 34 +0300] “POST / YA / PushReport / HTTP / 1.1” 404 293 "-" "Yota Access / YD1.14.0.2660 (Windows 6.1 .7601 x64) »
*. *. 238.110 - - [10 / Dec / 2011: 22: 58: 34 +0300] “POST / YA / PushReport / HTTP / 1.1” 404 293 "-" "Yota Access / YD1.14.0.2660 (Windows 6.1 .7601 x64) »
*. *. 238.110 - - [10 / Dec / 2011: 22: 58: 34 +0300] “POST / YA / PushReport / HTTP / 1.1” 404 293 "-" "Yota Access / YD1.14.0.2660 (Windows 6.1 .7601 x64) »
*. *. 238.110 - - [10 / Dec / 2011: 22: 58: 34 +0300] “POST / YA / PushReport / HTTP / 1.1” 404 293 "-" "Yota Access / YD1.14.0.2660 (Windows 6.1 .7601 x64) »
*. *. 238.110 - - [10 / Dec / 2011: 22: 58: 34 +0300] “POST / YA / PushReport / HTTP / 1.1” 404 293 "-" "Yota Access / YD1.14.0.2660 (Windows 6.1 .7601 x64) »
*. *. 238.110 - - [10 / Dec / 2011: 22: 58: 34 +0300] “POST / YA / PushReport / HTTP / 1.1” 404 293 "-" "Yota Access / YD1.14.0.2660 (Windows 6.1 .7601 x64) »
*. *. 238.110 - - [10 / Dec / 2011: 22: 58: 34 +0300] “POST / YA / PushReport / HTTP / 1.1” 404 293 "-" "Yota Access / YD1.14.0.2660 (Windows 6.1 .7601 x64) »
This is only one client within milliseconds. In my opinion, the Yota application behaves in a very interesting way, generating huge activity within one millisecond. Maybe he polls who ddit? And all Yota carriers are potential ddosers? I would like to bring this question to Habr, since here are the most correct users of the network.
PS After the turn of the DNS, the burst activity ceased. Remained and growing only a huge log on the server. We have solved the problem of a larger botnet on the network or what is it?
Source: https://habr.com/ru/post/134427/
All Articles