Support for user ssh keys in the cloud
News in one line: we implemented the ability to install a cloud server with automatic addition of root to the authorized_keys specified during the installation of the public ssh-key.

The minimum use method is to choose a key during installation / reinstallation:
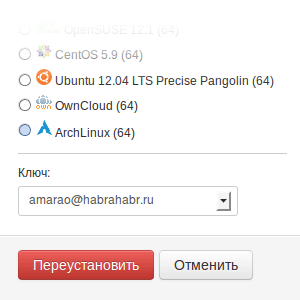
For convenience, we made it so that the key can be specified directly when creating the machine. In this case, we will remember your public key and let you select it in the drop-down list next time.
Note that by default the machine is installed without a key, but it is possible to specify which key to use by default.
')
If you have several keys, you can manage them. Total controls - delete, change the description and mark the key as “preferred”.

Of course, at any time, the “memorized” key can be removed from the list.
The simple part ends here. And then the nuances begin.
Firstly, unlike many services, we fully validate the key. And at the stage of JS, and on the server side. Which, firstly, saves from a common mistake - loading a private key instead of a public key, and secondly, it guarantees that the key is the key.
This is how well prevented disclosure of a private ssh key looks like - we reject it at the JS level, before sending it to the server and thus not compromising it:

Secondly, we write the installation key to the properties of the virtual machine (the “installation key” field, next to the password during installation).
We show its “tail” (description), but if you click on it, we will show the entire key.

And, most importantly: we check that the virtual machine key is known to the user. If the machine is delivered with a key that the user did not add to “his own” (this can be when transferring the server from account to account) or the user has deleted the key, then we show a warning.

Moreover, we will refuse to reinstall the virtual machine with an unknown key. This ensures that the owner of the machineknows exactly what he is doing and trusts the key owner to click “add” on the corresponding page.
Our server API is written in Haskell, the JS web interface (your captain). Neither in Haskell nor in JS, we did not find a ready-made library for validating keys. Our programmers: knsd and rocco66 spent some time and wrote their own .
(section for non-system administrators)

SSH-key allows you to go to the servers without entering a password. The private key is stored on the user’s computer (with or without a password), the public key is uploaded to the server. After that, when connecting to the server, the application (ssh-client) proves to the server that it has a private key (the private key itself is not transmitted) corresponding to the loaded public key. If everything is ok, the user is on the server.
In the everyday sense, it is much more convenient, not to mention the automation of remote command execution.
For Linux / FreeBSD and MacOS X, the key is generated in the console using the ssh-keygen command (the public key can then be copied from ~ / .ssh / id_rsa.pub). For Windows in the PyTTY utility, it can also be generated and used: habrahabr.ru/post/39254 .
Practically, the use of the key is reduced to the presence of the file ~ / .ssh / id_rsa, after that it is enough to dial root@habrahabr.ru and you will find yourself on the habrahabr.ru server with root rights. Assuming your public key is on the server in the /root/.ssh/authorized_keys directory, of course.

The minimum use method is to choose a key during installation / reinstallation:

For convenience, we made it so that the key can be specified directly when creating the machine. In this case, we will remember your public key and let you select it in the drop-down list next time.
Note that by default the machine is installed without a key, but it is possible to specify which key to use by default.
')
If you have several keys, you can manage them. Total controls - delete, change the description and mark the key as “preferred”.

Of course, at any time, the “memorized” key can be removed from the list.
The simple part ends here. And then the nuances begin.
Firstly, unlike many services, we fully validate the key. And at the stage of JS, and on the server side. Which, firstly, saves from a common mistake - loading a private key instead of a public key, and secondly, it guarantees that the key is the key.
This is how well prevented disclosure of a private ssh key looks like - we reject it at the JS level, before sending it to the server and thus not compromising it:

Secondly, we write the installation key to the properties of the virtual machine (the “installation key” field, next to the password during installation).
We show its “tail” (description), but if you click on it, we will show the entire key.

And, most importantly: we check that the virtual machine key is known to the user. If the machine is delivered with a key that the user did not add to “his own” (this can be when transferring the server from account to account) or the user has deleted the key, then we show a warning.

Moreover, we will refuse to reinstall the virtual machine with an unknown key. This ensures that the owner of the machine
SSH Key Libraries
Our server API is written in Haskell, the JS web interface (your captain). Neither in Haskell nor in JS, we did not find a ready-made library for validating keys. Our programmers: knsd and rocco66 spent some time and wrote their own .
- Haskell library: github.com/knsd/crypto-pubkey-openssh .
- Function for coffeescript: github.com/selectel/ssh_pub_key_validation
What are ssh keys for?
(section for non-system administrators)

SSH-key allows you to go to the servers without entering a password. The private key is stored on the user’s computer (with or without a password), the public key is uploaded to the server. After that, when connecting to the server, the application (ssh-client) proves to the server that it has a private key (the private key itself is not transmitted) corresponding to the loaded public key. If everything is ok, the user is on the server.
In the everyday sense, it is much more convenient, not to mention the automation of remote command execution.
For Linux / FreeBSD and MacOS X, the key is generated in the console using the ssh-keygen command (the public key can then be copied from ~ / .ssh / id_rsa.pub). For Windows in the PyTTY utility, it can also be generated and used: habrahabr.ru/post/39254 .
Practically, the use of the key is reduced to the presence of the file ~ / .ssh / id_rsa, after that it is enough to dial root@habrahabr.ru and you will find yourself on the habrahabr.ru server with root rights. Assuming your public key is on the server in the /root/.ssh/authorized_keys directory, of course.
Source: https://habr.com/ru/post/133820/
All Articles