In the US, a scandal about the illegal use of user data
The beginning of a detective story

What if our smart phones are watching us? It turns out that almost any phone can follow the user's actions. This is not just another plot of the “big brother” movie, it’s our reality.
By chance I came across an interesting topic on the network on xda-developers. Trevor Eckhart (Trevor Eckhart), a developer, delved into the program codes of the Android phone from HTC and found an interesting thing. The phone firmware contained a program that worked in a hidden mode from the user.
It turns out that HTC is building programs into its devices that allow them to collect various statistics. There is such an American company, Carrier IQ (CIQ), which provides operators with tools for collecting and analyzing data from subscribers' cell phones (according to the counter on the site: 141 million devices already have this option). Here is what is written on their website:
Carrier IQ is a market leader in mobile intelligent technology that has created a revolutionary technology that allows mobile operators and manufacturers to collect and process information from end users. The telephone is part of the network and is used as a tool for measuring key parameters of service quality and use. CIQ provides a unique opportunity to analyze usage scenarios and errors by type, location, application and network, at the same time, providing detailed data directly from the device itself, rather than general information about the state of the network.
We understand the question
Sounds good, isn't it? According to Trevor Eckhart, he was able to get a distribution of their program from this company. It resembles something like an interactive user survey:

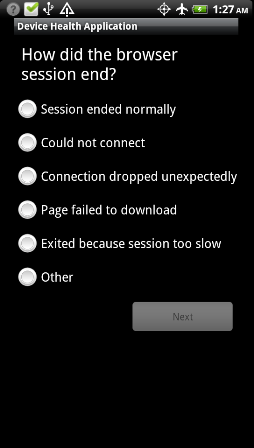
The program can collect data of various nature: signal level, location of the device, keystrokes, device model, in general, everything with which the user interacts. (According to the patent on the collection of data from wireless networks).
')
Information gathering happens like this: there are triggers and there are metrics. The necessary information about the phone is collected and sent when a certain trigger was activated. Judging by the description on the website of Trevor, the number of different metrics and triggers is huge. For example, here’s a list of triggers for HTC phones:
Key pressed on the dialer or keyboard:
Intent - com.htc.android.iqagent.action.ui01
Open advertisement:
Intent - com.htc.android.iqagent.action.ui15
SMS received:
Intent - com.htc.android.iqagent.action.smsnotify
Screen on / off:
Intent - com.htc.android.iqagent.action.ui02
Call received:
Intent - com.htc.android.iqagent.action.ui15
Media statistics:
Intent - com.htc.android.iqagent.action.mp03
Location statistics:
Intent - com.htc.android.iqagent.action.lc30
The program consists of two parts: the first is built into the device, the second is the server collecting and analyzing data (network-related: voice services and non-network data: music player, camera, various downloaded data, etc.). Taken from promotional materials
The operator / operator user gets a convenient interface for working with data (from the CIQ website ):
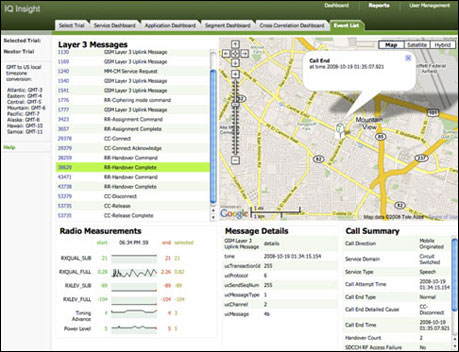
Everything would be fine if the user could voluntarily provide data for analysis, participate in surveys. However, in reality everything happens differently. The equipment manufacturer receives the source code from the CIQ, writes its interface and leaves the required functions, hiding the program from the end user, includes it in the device firmware (with the approval of the operator). Elements of the program code were found in Sense UI, Touch Wiz. Even in my HTC Desire S with the MIUI firmware, I found the remnants of the HTC logger.
Thus, the operator can collect any data about the phone and analyze them, and the user will not even know about it. Trevor classified the program as a rootkit because of its ability to hide itself from the user and at the same time be harmful.
By the way, this is possible not only on smartphones, this code can be embedded in any kind of phones. The blogger claims that this service is used by the American operators Sprint, Verizon, and the rootkit is installed on Android devices, Blakberry, Nokia, tablet computers and others. The phone can be monitored, even if it has never been activated on the operator’s network.
There is also good news: owners of Android phones can download the program from the Xda-developers forum and check their phone for the presence of a rootkit, and if you have root rights, then try to delete it.
The story gets an unexpected continuation.
Trevor received a letter from Carrier IQ with threats to initiate legal proceedings if he did not publicly apologize to the company and did not inform everyone that he had mistaken his conclusions.Additional Information
The original of Trevor Eckhart's article (he has a lot of information on this site, including technical).An article on Xda-developers about threats from CIQ.
CIQ published a press release refuting the words of the developer.
UPD. I add another link to Xda, here is described the squeeze of information from the developer's blog (thanks to ilyuxa ).
UPD2. EFF answer to CIQ claims. EFF - Electronic Frontier Organization, is engaged in consumer protection in the digital sphere, they took upon themselves the protection of Trevor’s rights. Briefly: CIQ claims are groundless. (thanks Joes ).
UPD3. Legal "hitting" is over . News from the fields brought Joes . CIQ has notified of the withdrawal of its claims and respects the EFF for its willingness to protect freedom of speech :)
However, the main issue is still valid.
Source: https://habr.com/ru/post/133505/
All Articles