Poking around in the SIM-card: processor, memory, file system + I / O
It is difficult to find a person who does not know what a SIM card or Subscriber Identity Module is - a subscriber identification module. This piece of plastic with gold contacts on one of the surfaces is the key to the services provided by the mobile operator. And also inside the SIM card there is a specialized computer with a rather complex functionality.
The SIM card is actually one of the varieties of a more general entity - the processor "smart card" (Smart Card).

The processor in the body of the SIM card
')
Such smart cards can be used for various purposes:
CDMA networks use the R-UIM - Removable User Identity Module to identify subscribers. The word Removable (replaceable) underlines its new status, because earlier, in IS-95 networks (communication standard, on the basis of which CDMA networks worked in the USA, Russia and other countries, for example, SONET in Moscow), the subscriber identification elements were placed among electronic phone components. It is obvious that the use of R-UIM greatly simplifies the replacement of the phone in case of its malfunction or the purchase of a new one, and allows you to use a phone of another standard in roaming.
But then we will talk about the identification modules of subscribers used in GSM-UMTS networks, which by tradition we will call SIM or cards.
Currently, three formats of GSM-UMTS subscriber identification modules have been standardized.

Three formats of subscriber identification modules GSM-UMTS
ID-1 UICC - the very first option - has the size of a regular bank card. Many people remember him in the models of the 90s - Motorola 8900, StarTAC and others. Currently, the new models of mobile terminals are practically not used due to the large size.
UICC plug-in is the most common format now. Typically, such modules are broken out of ID-1 size cards by cuts made during manufacture.
Mini-UICC is the format of cards that Apple began to use in iPhone 4, iPad, iPad 2. Now other mobile phone manufacturers and other device manufacturers intend to release models into which it will be necessary to insert modules of exactly this format. Sometimes this format is called 3FF, or popularly "micro-SIM". And these cards are usually broken out of an ID-1 card. The reasons for the appearance of such a diversity are obvious - saving space inside the phone.
A universal hole, which allows a user to break a module of both Plug-in and Mini-UICC from an ID-1 plastic card, for reliability reasons - when trying to break a Plug-in card, it is very easy to damage the remaining thin jumpers, after which the Plug-in card will not be held securely in the phone.

ID-1 card with “universal” slot for Plug-in and Mini-UICC
And the shift of the SIM-card in the holder faces problems with the operation of the phone. The minimum trouble - the phone simply does not feel the presence of the SIM and does not register on the network. In the worst case, it can turn out as if the wires are entangled - voltage is not at the address and a short circuit with unpredictable consequences.
Manufacturers of mobile terminals who are active, who are less determined, usually object to the use of adapters that are advertised for using Mini-UICC cards in phones designed for Plug-in cards. The adapter is slightly thicker than the Plug-in module, and in addition, the slots at the junction of the card and the adapter can break contacts in the phone when installing the SIM, depriving the user of the chances of warranty repair.
Some devices operating in the mobile network (navigators, devices for monitoring the location of vehicles, etc.) can identify subscribers' subscriber units simply in the form of microchips, but ordinary subscribers do not usually encounter such modules.
In everyday life there are modules with a different pattern of the contact pad and a different number of contacts. Some manufacturers use the "corporate" drawing of the contact pad as their business card.
The standards provided for 8 positions for sites through which modules are connected to mobile terminals, but not all of them are used. Often there are cards with 6 contacts, and the rest of the metallized part is usually connected to the “ground”.
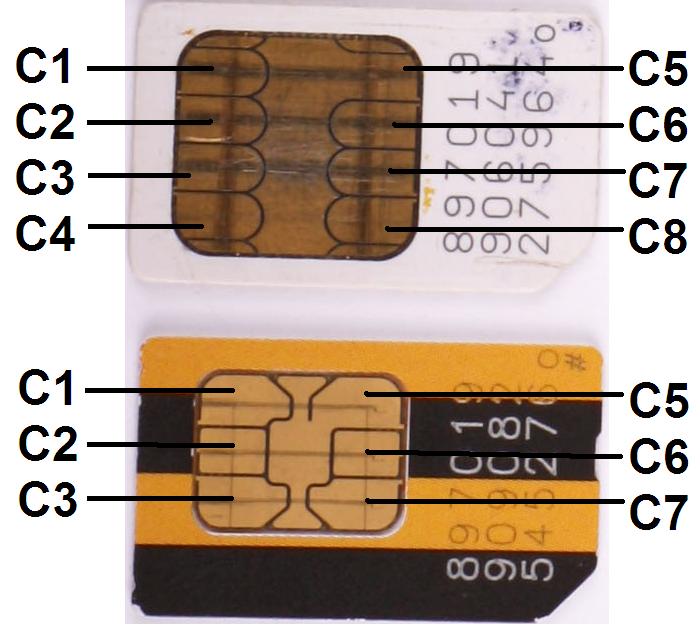
Cards with 6th and 8th contacts
Used contacts:
C1 - Vcc - power;
C2 - Reset - contact control card;
C3 - CLK - Clock - clock frequency;
C5 - common ("land");
C6 - Vpp - programming voltage that is used when recording service information
C7 - I / O - serial I / O line.
The standards provide for the use of C4 and C8 contacts in the mode of information exchange with a mobile terminal in USB mode, which provides a higher speed of information transfer than through the usual I / O SIM interface.
In practice, now the USB-interface mode is not actually used, since the equipment with this interface is practically not produced and is not ordered by consumers, so these contacts, even if they are on the card, are connected to ground. Further work will be discussed through the line I / O interface.
By comparing the electronic contents of a SIM with a computer (especially with a pocket one), one can find many elements of the same function:
There are differences - something that is not in the module:
Additional information about the architecture and production of SIM can be found here in this topic .
The amount of memory that can be used to store information in a SIM is different and gradually grows as technology develops. A few years ago there was a flash of euphoria from the advent of technology that allows you to place gigabytes of information in a SIM. It was then, after a heated discussion in the industry and two rounds of voting in the GSM Association, the USB standard was chosen for working with large amounts of information. But then the euphoria subsided, and now there are not so many mobile terminals on the market that can work with such SIMs, and the SIMs themselves with a gigabyte memory do not enjoy much demand from operators.
Why do we need large amounts of memory SIM-cards and how much memory is really needed?
SIM memory is used for several purposes:
It is also obvious that the increase in the amount of memory increases the cost of the SIM, and therefore now the operators, most often, try to limit themselves to the volumes minimally necessary to accommodate the necessary information.
Besides the fact that the phone or another mobile terminal provides the SIM card with power and a clock signal, it is fully responsible for the exchange of information between devices - the phone always acts as the master, and the card is always the slave.
The phone sends commands / requests to the SIM, and the SIM only responds to them, accompanying the answers with information on the status of the answer.
In the status information, the card can confirm that the command was completed successfully, ask for additional time to prepare an answer, report errors of various types, or report that it has special information for the phone that it can receive by sending a special request to the following command to select .
This mechanism for transferring information from a card to a telephone is usually called a SIM (or Card) Application Toolkit, STK. It is used to implement various services, which are based on application programs (usually written in JavaCE - Java Card Edition), executed within the SIM. In the menu of phones, with installed SIM-cards of the main operators, you can find items and whole menu trees, formed on the basis of information provided by applications working in SIM-cards.
Real-time services are based on the same technology, for example, constantly providing information about the current balance.
It is possible to organize roaming for small companies using the switching of two IMSIs in one map - one that corresponds to its network, and the other - provided by “borrowing” by another operator - the “big brother”. For example, Beeline networks operating in the CIS countries use the Dual IMSI mechanism to provide roaming services to their subscribers. One IMSI of its network and another IMSI corresponding to the Russian Beeline network are registered in their SIM-cards. In the Russian Beeline network, these IMSIs are reserved in the HLR to provide roaming services to subsidiaries and channels of communication with them are organized. A Beeline subscriber from a “subsidiary” company, being, for example, in a European country, with the help of the STK menu switches the SIM operation mode to roaming. As a result, a phone with such a SIM card is presented to the roaming network as belonging to a subscriber of the Russian Beeline network. Then everything happens, as usual, only the Russian Beeline network organizes the transfer of information on behalf of the "affiliated" network.
Even a web server can be organized inside the SIM! So, if someone is confused by the “slave position” of the SIM, he may well consider it as a server.
After switching on and starting the operating system, the phone powers on the Vcc power supply to the SIM. The standards provide for three SIM supply voltage ratings - 5V, 3V and 1.8V.
Previously issued cards that can work only at a voltage of 5V. After the appearance of phones that applied no more than 3V to the card, these old SIMs were gradually replaced by new ones capable of operating from 3V, which also withstand work in phones providing 5V.
Since the phones that provide SIM cards with a voltage of only 1.8V have not yet been encountered, modern SIM cards do not create compatibility problems due to supply voltages.
After the power supply is applied to the phone, a clock signal is given, and after establishing a stable mode, the voltage on the Reset pin is raised. This serves as a signal for the SIM card to start working with it, to which it responds with a sequence of bytes called ATR (Answer To Reset).
The ATR bytes contain basic information about the card’s capabilities and supported communication protocols. In particular, he can tell the phone possible options for accelerating the exchange of information through the interface by increasing the clock frequency and speed of information transfer.
After reading the information from the ATR, the phone can run the PPS (Protocol and Parameter Selection) procedure to negotiate the mode of exchanging phone information with the card. If the phone is not able to find an option that is acceptable both for it and for SIM, then communication with the card will continue in the default mode (at a speed of 9600 bps).
In such cases, subscribers often complain that the phonebook is read from the SIM card to the phone for too long, for some reason, reproaching the operator who issued the SIM card.
In the process of turning on the SIM card and the mobile terminal (telephone) exchange “business cards”. The phone reads from the SIM file containing the SST - SIM Service Table - in a certain way encoded information about the STK functions that the SIM is able to perform. In turn, the phone sends to the SIM-card TERMINAL PROFILE - in a certain way coded information about what functions of communication with the SIM it can support. As a result, both parties receive information about the capabilities of the partner and can interact correctly when implementing services based on STK.
SIM has a multi-level hierarchical file structure with access control.
Access to files is governed by the need for the user to first present access codes of various types.
Some of these access codes are well known - this is Personal Identification Numbers - PIN (aka PIN1) and PIN2. Other codes are used for administrative access to service files.
What makes such a distinction? Activated PIN request allows you to protect money on the personal account associated with the SIM card from unauthorized use by unauthorized persons.
Another important security technique is, for example, the inability to read information from some files, for example, reading the key Ki, which is used in various cryptographic algorithms for authenticating the subscriber and generating traffic encryption keys.
Several years ago, at a round table on the prospects of smartphones, organized by one of the manufacturers, one of the participants complained to me that Beeline lacks a service that is very useful for parents. He wanted parents to limit the possibility for their children to call only on a specific set of phone numbers - home, parents, grandparents, and the child should not call the other numbers.
What was his surprise when I showed him the work of the FDN function - Fixed Dialing Numbers, which is implemented by the joint actions of the phone and the SIM card. Allowed numbers using the phone are simply recorded in a specific SIM card file, and access to change this list is blocked using PIN2. After that, a phone with such a SIM will refuse to call numbers that are not listed in the FDN list.
However, it should be noted that not all phones support the operation of this service.
The skin of the fingers is coated with organic fatty acids, which on contact cause corrosion of metal parts. Small details - this is exactly about the contacts of the SIM-card.
The photo shows a laser pointer, the surface of which, after a rather rare use, has lost several layers of metallic coating - chrome plating and copper plating just because of these fatty acids! As you know, “radio engineering is the science of contacts,” and SIM has a lot of them!

Laser pointer affected by fatty acids on fingers
Such a fate should not grasp the contacts of the SIM-card, and for this you need to protect the contacts of the SIM from contamination by all means, and try not to touch them with your fingers!
If a problem with contacts between the phone and the SIM has arisen, then a neat cleaning of the contacts with a soft eraser can help. Just do not need after the cleaning operation to remove the crumbs from the contacts with your fingers, otherwise all the problems will begin again! It is better to simply blow them away or gently rinse with alcohol.
Once a subscriber came to the Beeline office, who was sent to change the SIM card from the phone repair service, because his completely new phone spontaneously turned off during a call, checking the balance, sending an SMS.
I had to explain to him that turning off the phone has no connection with the health of the SIM. Using an eraser, I carefully cleaned the contacts on the battery and in the phone, after which the phone began to work normally. Along the way, I gave the subscriber a small lecture on hygiene.
Of course, the situation is not so obvious in all cases, and it is not easy to determine who is to blame - the phone or the SIM that the services do not work, because their communication is almost intimate. It is especially important to understand the causes of conflicts when developing new services using STK or when detecting problems of incompatibility of SIM with some models of phones or other mobile terminals.
In such cases, the analyzer of information exchange protocols on the interface of the SIM terminal provides an invaluable service:

Analyzer of communication protocols between the SIM and the mobile terminal.
Instead of a SIM card, a special probe is inserted into the terminal, and the SIM is connected via a flexible loop. During operation, all information about events occurring on the interface is recorded in the memory of the computer connected to the analyzer.
Comparison of the collected information with the requirements of the standards allows unambiguously and convincingly to establish the side guilty of the conflict.
Of course, the material touched upon only some of the features of SIM-cards and their work in phones, but if there is an interest in this topic, just ask questions, I will answer in detail.
PS Today, Boomboorum wrote another review of our office .
SIM-card is the same processor card, but in profile
The SIM card is actually one of the varieties of a more general entity - the processor "smart card" (Smart Card).

The processor in the body of the SIM card
')
Such smart cards can be used for various purposes:
- Identification of mobile subscribers.
- Providing access to the encrypted content of various paid systems, such as television.
- Like bank cards
- For identification of the user who is granted access to corporate networks, etc.
CDMA networks use the R-UIM - Removable User Identity Module to identify subscribers. The word Removable (replaceable) underlines its new status, because earlier, in IS-95 networks (communication standard, on the basis of which CDMA networks worked in the USA, Russia and other countries, for example, SONET in Moscow), the subscriber identification elements were placed among electronic phone components. It is obvious that the use of R-UIM greatly simplifies the replacement of the phone in case of its malfunction or the purchase of a new one, and allows you to use a phone of another standard in roaming.
But then we will talk about the identification modules of subscribers used in GSM-UMTS networks, which by tradition we will call SIM or cards.
Pick your cards?
Currently, three formats of GSM-UMTS subscriber identification modules have been standardized.

Three formats of subscriber identification modules GSM-UMTS
ID-1 UICC - the very first option - has the size of a regular bank card. Many people remember him in the models of the 90s - Motorola 8900, StarTAC and others. Currently, the new models of mobile terminals are practically not used due to the large size.
UICC plug-in is the most common format now. Typically, such modules are broken out of ID-1 size cards by cuts made during manufacture.
Mini-UICC is the format of cards that Apple began to use in iPhone 4, iPad, iPad 2. Now other mobile phone manufacturers and other device manufacturers intend to release models into which it will be necessary to insert modules of exactly this format. Sometimes this format is called 3FF, or popularly "micro-SIM". And these cards are usually broken out of an ID-1 card. The reasons for the appearance of such a diversity are obvious - saving space inside the phone.
A universal hole, which allows a user to break a module of both Plug-in and Mini-UICC from an ID-1 plastic card, for reliability reasons - when trying to break a Plug-in card, it is very easy to damage the remaining thin jumpers, after which the Plug-in card will not be held securely in the phone.

ID-1 card with “universal” slot for Plug-in and Mini-UICC
And the shift of the SIM-card in the holder faces problems with the operation of the phone. The minimum trouble - the phone simply does not feel the presence of the SIM and does not register on the network. In the worst case, it can turn out as if the wires are entangled - voltage is not at the address and a short circuit with unpredictable consequences.
Manufacturers of mobile terminals who are active, who are less determined, usually object to the use of adapters that are advertised for using Mini-UICC cards in phones designed for Plug-in cards. The adapter is slightly thicker than the Plug-in module, and in addition, the slots at the junction of the card and the adapter can break contacts in the phone when installing the SIM, depriving the user of the chances of warranty repair.
Some devices operating in the mobile network (navigators, devices for monitoring the location of vehicles, etc.) can identify subscribers' subscriber units simply in the form of microchips, but ordinary subscribers do not usually encounter such modules.
How many contacts should there be?
In everyday life there are modules with a different pattern of the contact pad and a different number of contacts. Some manufacturers use the "corporate" drawing of the contact pad as their business card.
The standards provided for 8 positions for sites through which modules are connected to mobile terminals, but not all of them are used. Often there are cards with 6 contacts, and the rest of the metallized part is usually connected to the “ground”.

Cards with 6th and 8th contacts
Used contacts:
C1 - Vcc - power;
C2 - Reset - contact control card;
C3 - CLK - Clock - clock frequency;
C5 - common ("land");
C6 - Vpp - programming voltage that is used when recording service information
C7 - I / O - serial I / O line.
The standards provide for the use of C4 and C8 contacts in the mode of information exchange with a mobile terminal in USB mode, which provides a higher speed of information transfer than through the usual I / O SIM interface.
In practice, now the USB-interface mode is not actually used, since the equipment with this interface is practically not produced and is not ordered by consumers, so these contacts, even if they are on the card, are connected to ground. Further work will be discussed through the line I / O interface.
Where did they put the computer?
By comparing the electronic contents of a SIM with a computer (especially with a pocket one), one can find many elements of the same function:
- Processor (CPU);
- RAM (RAM, RAM);
- Permanent memory for storing the operating system ROM (ROM);
- Memory for storing user information;
- File system;
- I / O controller (I / O controller).
There are differences - something that is not in the module:
- Interface elements with a person who are simply not needed by the module.
- Power supply (terminal power is used)
- Clock Generator (Likewise, terminal supply).
Additional information about the architecture and production of SIM can be found here in this topic .
The amount of memory that can be used to store information in a SIM is different and gradually grows as technology develops. A few years ago there was a flash of euphoria from the advent of technology that allows you to place gigabytes of information in a SIM. It was then, after a heated discussion in the industry and two rounds of voting in the GSM Association, the USB standard was chosen for working with large amounts of information. But then the euphoria subsided, and now there are not so many mobile terminals on the market that can work with such SIMs, and the SIMs themselves with a gigabyte memory do not enjoy much demand from operators.
Can I store HD movies on SIM cards?
Why do we need large amounts of memory SIM-cards and how much memory is really needed?
SIM memory is used for several purposes:
- Storing information that is vital for the phone to work with this SIM in a mobile network. For example, this is IMSI - International Mobile Subscriber Identity - a sequence of numbers that not only identifies a particular SIM and its owner, but also indicates which operator from which country it was released. This information helps in roaming to quickly figure out where to find out what services you can provide with the phone with this card, because the first three digits of the IMSI are the country code, and the next two digits are the network code (in the Americas, the network code consists of three numbers). This Ki is the secret key that makes it possible for the network to make sure that it really is its own SIM card, and not some fraudster uses someone else's IMSI to gain access to services. Plus files to store other service information.
- Storage of user information . Typically, the cards are located phone book received SMS-ki. In maps for the UMTS network, the phone book may have substantially more functionality than just a list of names and their corresponding phone numbers. You can attach several numbers to a name, add an email address and other information. However, due to the development of the same functions in the phones themselves, these SIM capabilities are practically not used.
- Placement of application files that can be executed in a Java virtual machine embedded in a SIM and provide certain services. If the operator actively uses services based on applications running in the SIM card, then this part may occupy the most significant part of the card's memory.
It is also obvious that the increase in the amount of memory increases the cost of the SIM, and therefore now the operators, most often, try to limit themselves to the volumes minimally necessary to accommodate the necessary information.
Who drives who?
Besides the fact that the phone or another mobile terminal provides the SIM card with power and a clock signal, it is fully responsible for the exchange of information between devices - the phone always acts as the master, and the card is always the slave.
The phone sends commands / requests to the SIM, and the SIM only responds to them, accompanying the answers with information on the status of the answer.
In the status information, the card can confirm that the command was completed successfully, ask for additional time to prepare an answer, report errors of various types, or report that it has special information for the phone that it can receive by sending a special request to the following command to select .
This mechanism for transferring information from a card to a telephone is usually called a SIM (or Card) Application Toolkit, STK. It is used to implement various services, which are based on application programs (usually written in JavaCE - Java Card Edition), executed within the SIM. In the menu of phones, with installed SIM-cards of the main operators, you can find items and whole menu trees, formed on the basis of information provided by applications working in SIM-cards.
Real-time services are based on the same technology, for example, constantly providing information about the current balance.
It is possible to organize roaming for small companies using the switching of two IMSIs in one map - one that corresponds to its network, and the other - provided by “borrowing” by another operator - the “big brother”. For example, Beeline networks operating in the CIS countries use the Dual IMSI mechanism to provide roaming services to their subscribers. One IMSI of its network and another IMSI corresponding to the Russian Beeline network are registered in their SIM-cards. In the Russian Beeline network, these IMSIs are reserved in the HLR to provide roaming services to subsidiaries and channels of communication with them are organized. A Beeline subscriber from a “subsidiary” company, being, for example, in a European country, with the help of the STK menu switches the SIM operation mode to roaming. As a result, a phone with such a SIM card is presented to the roaming network as belonging to a subscriber of the Russian Beeline network. Then everything happens, as usual, only the Russian Beeline network organizes the transfer of information on behalf of the "affiliated" network.
Even a web server can be organized inside the SIM! So, if someone is confused by the “slave position” of the SIM, he may well consider it as a server.
How does it turn on and why does the book load slowly?
After switching on and starting the operating system, the phone powers on the Vcc power supply to the SIM. The standards provide for three SIM supply voltage ratings - 5V, 3V and 1.8V.
Previously issued cards that can work only at a voltage of 5V. After the appearance of phones that applied no more than 3V to the card, these old SIMs were gradually replaced by new ones capable of operating from 3V, which also withstand work in phones providing 5V.
Since the phones that provide SIM cards with a voltage of only 1.8V have not yet been encountered, modern SIM cards do not create compatibility problems due to supply voltages.
After the power supply is applied to the phone, a clock signal is given, and after establishing a stable mode, the voltage on the Reset pin is raised. This serves as a signal for the SIM card to start working with it, to which it responds with a sequence of bytes called ATR (Answer To Reset).
The ATR bytes contain basic information about the card’s capabilities and supported communication protocols. In particular, he can tell the phone possible options for accelerating the exchange of information through the interface by increasing the clock frequency and speed of information transfer.
After reading the information from the ATR, the phone can run the PPS (Protocol and Parameter Selection) procedure to negotiate the mode of exchanging phone information with the card. If the phone is not able to find an option that is acceptable both for it and for SIM, then communication with the card will continue in the default mode (at a speed of 9600 bps).
In such cases, subscribers often complain that the phonebook is read from the SIM card to the phone for too long, for some reason, reproaching the operator who issued the SIM card.
"Hello, who are you?"
In the process of turning on the SIM card and the mobile terminal (telephone) exchange “business cards”. The phone reads from the SIM file containing the SST - SIM Service Table - in a certain way encoded information about the STK functions that the SIM is able to perform. In turn, the phone sends to the SIM-card TERMINAL PROFILE - in a certain way coded information about what functions of communication with the SIM it can support. As a result, both parties receive information about the capabilities of the partner and can interact correctly when implementing services based on STK.
File system and security
SIM has a multi-level hierarchical file structure with access control.
Access to files is governed by the need for the user to first present access codes of various types.
Some of these access codes are well known - this is Personal Identification Numbers - PIN (aka PIN1) and PIN2. Other codes are used for administrative access to service files.
What makes such a distinction? Activated PIN request allows you to protect money on the personal account associated with the SIM card from unauthorized use by unauthorized persons.
Another important security technique is, for example, the inability to read information from some files, for example, reading the key Ki, which is used in various cryptographic algorithms for authenticating the subscriber and generating traffic encryption keys.
Why is it helpful to read the instructions?
Several years ago, at a round table on the prospects of smartphones, organized by one of the manufacturers, one of the participants complained to me that Beeline lacks a service that is very useful for parents. He wanted parents to limit the possibility for their children to call only on a specific set of phone numbers - home, parents, grandparents, and the child should not call the other numbers.
What was his surprise when I showed him the work of the FDN function - Fixed Dialing Numbers, which is implemented by the joint actions of the phone and the SIM card. Allowed numbers using the phone are simply recorded in a specific SIM card file, and access to change this list is blocked using PIN2. After that, a phone with such a SIM will refuse to call numbers that are not listed in the FDN list.
However, it should be noted that not all phones support the operation of this service.
Wash your hands before eating
The skin of the fingers is coated with organic fatty acids, which on contact cause corrosion of metal parts. Small details - this is exactly about the contacts of the SIM-card.
The photo shows a laser pointer, the surface of which, after a rather rare use, has lost several layers of metallic coating - chrome plating and copper plating just because of these fatty acids! As you know, “radio engineering is the science of contacts,” and SIM has a lot of them!

Laser pointer affected by fatty acids on fingers
Such a fate should not grasp the contacts of the SIM-card, and for this you need to protect the contacts of the SIM from contamination by all means, and try not to touch them with your fingers!
If a problem with contacts between the phone and the SIM has arisen, then a neat cleaning of the contacts with a soft eraser can help. Just do not need after the cleaning operation to remove the crumbs from the contacts with your fingers, otherwise all the problems will begin again! It is better to simply blow them away or gently rinse with alcohol.
To change or not to change?
Once a subscriber came to the Beeline office, who was sent to change the SIM card from the phone repair service, because his completely new phone spontaneously turned off during a call, checking the balance, sending an SMS.
I had to explain to him that turning off the phone has no connection with the health of the SIM. Using an eraser, I carefully cleaned the contacts on the battery and in the phone, after which the phone began to work normally. Along the way, I gave the subscriber a small lecture on hygiene.
Of course, the situation is not so obvious in all cases, and it is not easy to determine who is to blame - the phone or the SIM that the services do not work, because their communication is almost intimate. It is especially important to understand the causes of conflicts when developing new services using STK or when detecting problems of incompatibility of SIM with some models of phones or other mobile terminals.
In such cases, the analyzer of information exchange protocols on the interface of the SIM terminal provides an invaluable service:

Analyzer of communication protocols between the SIM and the mobile terminal.
Instead of a SIM card, a special probe is inserted into the terminal, and the SIM is connected via a flexible loop. During operation, all information about events occurring on the interface is recorded in the memory of the computer connected to the analyzer.
Comparison of the collected information with the requirements of the standards allows unambiguously and convincingly to establish the side guilty of the conflict.
Of course, the material touched upon only some of the features of SIM-cards and their work in phones, but if there is an interest in this topic, just ask questions, I will answer in detail.
PS Today, Boomboorum wrote another review of our office .
Source: https://habr.com/ru/post/133388/
All Articles