Everything you wanted to know about operations wizards, but were afraid to ask

Most of the system administrators in their corporate environment use AD DS, which can safely be called the heart of the entire enterprise infrastructure, to provide the system of identification and access of its users to company resources. As many of you know, the structure of domain services in organizations can include one or several forests (a set of domains, including a description of the network configuration and a single copy of the directory), depending on factors such as limiting the area of trust, the complete separation of network data, obtaining administrative isolation. In turn, each large forest should be divided into domains to simplify the administration and replication of data. In each domain, domain controllers are used to manage domain services and perform tasks such as authentication, starting the Kerberos Key Distribution Center service , and access control. And to manage the network traffic between offices developed sites.
All information about forests, domains and sites, of course, must be coordinated when designing Active Directory Domain Services, according to corporate requirements such as: business requirements, functional requirements, legal requirements, security requirements, as well as project documentation restrictions. Often, all these points before the deployment of domain services are carefully planned by the IT department of the company itself or by the project team dealing with the infrastructure of the enterprise and are written into a special service level agreement defining the expected level of performance and the quality of the service provided.
The information obtained after the design or, most often, after the deployment of Active Directory Domain Services has to be carefully documented. Such documentation should include information about the logical and physical structure of domain services, administrative models, name resolution infrastructure, all planned changes in the organization’s environment, as well as such additional infrastructure components as the implementation of Microsoft Exchange mail servers, System Center servers and much more. In most cases, the organization's IT staff ignores the documenting process and, when changing IT staff, new administrators may take some time to fully navigate the organization’s current infrastructure.
You also need to understand that in the directory service almost all domain controllers are equal (in this context we do not take into account read-only domain controllers, RODCs), that is, all domain controllers have the right to write to the database and can replicate this data to other controllers. This topology does an excellent job with most trivial Active Directory operations and is called replication with multiple peers (Multimaster). But, nevertheless, there are some operations that must necessarily be performed on an authorized server allocated for such operations directly. In other words, domain controllers that perform certain operations or roles in their domain are called wizards (or masters) of operations. Know and understand the purpose of all the roles of operations wizards is necessary, since in the event of disaster recovery, updating or migration, domain controllers that perform the roles of operations wizards can play one of the most important roles. Accordingly, it is about the master operations and will be discussed in this article.
From this article you will learn:
- The fact that it would be if there were no masters of operations;
- On the roles of forest-level operations wizards;
- About roles of operations level wizards;
- How you can determine which controller has the role of FSMO;
- About captures and transfer of roles of operations masters;
- On the proper placement of operations wizards on domain controllers.
What will not be considered in the current article:
- Planning and documenting domain controllers with operations master roles . This is a separate topic that includes an understanding of the nuances of planning AD DS and is beyond the scope of this article;
- Global catalog servers . Many system administrators equate global catalog servers with operations wizards. In fact, this is a false proposition. A global catalog is a distributed data repository that stores information about each object, and also allows users and applications to find objects in any domain of the current forest by searching for attributes included in the global catalog that are identified in the schema as a private set of attributes. The global catalog itself is located on domain controllers that are designated as global catalog servers and, in turn, is replicated through Multimaster replication. Although the global catalog contains a complete list of all forest objects, and the global catalog servers can respond to all requests without having to link to other domain controllers, the global catalog is not the role of operations wizards. You can read the following article about global catalog servers: “Global catalog servers” ;
- The interaction of operations wizards with read-only domain controllers . Read-only Domain Controllers (DCs) are a special, relatively new type of domain controllers, which it is advisable to deploy in branch offices that are not provided with an adequate level of security and qualified IT staff. As with the scheduling of operations wizards and global catalog servers, read-only domain controllers are a separate, broad topic that doesn’t make any sense in this article. But you should immediately pay attention to the fact that read-only domain controllers cannot act as a domain controller with the role of operations master;
- Problem solving and errors related to operations wizards . An interesting and rather voluminous topic that will not be considered, in view of the fact that the current article deals with the general concepts of the roles of operations wizards.
What would happen if there were no operations wizards
Before imagining the situation with Active Directory domain controllers, on which there would be no distinction between domain controllers performing specific operations and other domain controllers, consider the advantages of domain controllers equipped with operation master roles.
First of all, as already mentioned in the introductory section of this article, operations wizards are domain controllers that perform a special role in Active Directory to ensure integrity and eliminate conflicts. It is for this purpose that a special role is assigned to such domain controllers, and since such roles do not have a strict binding to a single domain controller, such roles are called operation masters (Flexible Single Master Operation, FSMO, which is pronounced fizz-mo). In fact, these roles can be performed by other domain controllers, but each role should be assigned to only one domain controller, and, in the same domain, actions that should be performed on the domain controllers of operations masters cannot be performed at the same time.
I think it would be helpful to know which protocols the operation wizards use. Operation Wizards use three protocols:
- Lightweight Directory Access Protocol (LDAP);
- RPC;
- SMTP.

Now let's imagine for a moment what would happen if there were no operation wizards in Active Directory Domain Services, that is, if all domain controllers could simultaneously perform the same actions.
Suppose there is an organization with one forest and five domains. In each of the domains, the system administrators decided to simultaneously install the Microsoft Exchange mail server, and, in one domain, the administrator installs the 2007 version of this mail server, in the second - 2000, and in the third Microsoft Exchange Server 2010 SP1. All changes to the domain schema and, accordingly, the entire forest are written to the domain controller to which the administrators were connected, and after a while all changes made to the Active Directory scheme are replicated to each domain controller in the organization’s forest.
If someone wants to rename his domain using the system utility Rendom.exe, as another domain has already been named, and the corresponding FSMO role will not be in the enterprise, when accessing which the administrator would see a warning message, saying, “What are you doing- then? You already have such a domain, do you want to break everything? ”And the domain will be renamed, after replication it would be simply impossible to avoid fatal problems.
Take another example ... Again, in nature there are no masters of operations. On client machines, the time can be lost, users can change their time by chance, but all clients in the default domain should synchronize time with the nearest domain controllers. In this case, if there is no specific domain controller, the so-called leading time source, then the time for each user in the entire domain may be different, which may be critical for some business applications.
Actually, examples of corporate apocalypse in connection with the lack of master operations can be given infinitely many. The essence is the same, the wizards of operations simply have to be, should be accessible and should perform only those operations that are intended for them.
In total, Active Directory Domain Services includes five different roles of operations wizards, Namely, two roles are used at the forest level: domain naming master and schema master , and in each forest there can be no more than one domain controller, with assignments of each role. Each domain has only three operations master roles: the relative identifier master RID , the infrastructure master , and the PDC main domain controller emulator . That is, when you install the very first domain controller in the forest, it simultaneously assigns all five roles of operations wizards, and when creating a new Active Directory domain in an existing forest, the new domain controller is assigned three domain level roles. FSMO in the forest and the number of potential owners of these roles can be calculated by the formula "(number of domains * 3) + 2".
For example, if you have an Active Directory forest with four domains, where there is a child and grandchild domain of one of the main domains, then this forest will contain 14 FSMO roles. That is: one scheme master, one domain naming master, four PDC emulators (for two primary, child and grandchild domains with one role), four RID hosts for each domain, and four infrastructure masters for each domain.
At this stage, I think it’s time to consider each role of the forest-level and domain-level operations master.
The roles of forest level wizards
As I wrote above, for the Active Directory forest level, there are two roles of operations wizards, namely:
- Schema master;
- Domain Naming Wizard
The role of the schema master
Before you say a few words about the role of the schema master, I think it makes sense to briefly describe what the “Active Directory Scheme” is .
- See the gopher?
- Not.
- And I do not see. And he is!
K.F. "DMB"

For many novice administrators, the Active Directory scheme can be associated with the expression from the famous movie written above. It seems to be, as there is such a thing as a scheme, but for what it is needed, what it is, and in general what it is, no one knows and does not hurry to find out about it.
According to the terminology, the schema contains the definitions of each attribute and class, which are created and stored in the Active Directory forest. I think it’s unlikely for someone to find the news that AD DS stores and retrieves the necessary information from many corporate applications at the right time. This is done so that, if necessary, the applications do not apply to the various components of the enterprise infrastructure, but to Active Directory Domain Services, information about which will be replicated to all domain controllers. It is worth paying attention to the fact that in each Active Directory forest there is only one scheme that can be replicated to each domain controller in the forest. Therefore, if an organization needs to deploy several applications that may create conflicts in the Active Directory schema, it is advisable to deploy and maintain two separate forests.
The schema itself consists of the classSchema and attributeSchema objects, which are requested when defining the required object in the domain services. Classes themselves are certain definitions located in the schema, which, in turn, define attribute groups. It must be remembered that each class can use many attributes. And, finally, for each attribute located in Active Directory Domain Services, the data type is specified in the schema as the syntax of the attribute itself. And, of course, the value of each attribute included in a class instance must comply with the syntax requirements of the current attribute.
Since a detailed review of the Active Directory schema is beyond the scope of this article, I think the definition described above is more than enough. More information about the Active Directory schema will be discussed in one of the following articles. Now consider what is the role of the master circuit.
The domain controller, which is the schema master, is responsible for all changes that are made to the schema of the Active Directory forest. It must be remembered that the domain controller responsible for this role should be the only one in the whole forest, and all other domain controllers will contain only replicas of the forest-only scheme for reading. That is, if you make any changes to the Active Directory schema manually or when installing applications that modify the schema, the administrator needs to make changes on the domain controller that manages this role. To make changes, the administrator must connect to the schema wizard and must be a member of the Schema Administrators security group. After updating the schema, it is replicated from the schema wizard to all other domain controllers. When attempting to modify a schema not on a domain controller that performs the role of a schema master, the action usually fails and you need to send them to the domain controller with the schema master role after making changes to the schema. Accordingly, this role is critical, since when you try to modify the Active Directory schema with the disabled schema master, you will run into errors all the time. In turn, the master schema role can be located on any domain controller in the forest designated for this purpose.
By default, the schema master role is assigned to the first domain controller, which is installed in the forest, and this role is recommended to be placed along with the domain naming master role, which will be described below, on one domain controller. Despite the recommendations, you can at any time move this role to any domain controller using the Active Directory Schema snap- in or through the Ntdsutil command-line tool . You will also learn about the transfer of roles to other domain controllers in this article. The schema master is identified by the fSMORoleOwner attribute value of the root object of the schema section.
The role of the Domain Naming Wizard

The next role that will be considered is called the domain naming master. This role of the operations wizard and, accordingly, the only domain controller in the forest that can contain this role, is mainly used to add and delete domains and all directory partitions in the forest hierarchy. The domain controller with the role of the domain naming master is designed to perform the following four operations:
- Add and remove domains . When performing such an operation as adding or deleting a child domain by using the Active Directory installation wizard or the command line utility, the installation wizard refers specifically to the domain naming wizard and asks for the right to add or, respectively, delete the latter. Also, the domain naming master is responsible for ensuring that domains in the forest own unique NETBIOS names throughout the forest. Naturally, for obvious reasons, if the domain naming master is not available, you will not be able to add or delete domains in the forest;
- Add and remove cross-references . As you already know, during the creation of the first domain controller in the forest, it creates sections of the schema, configuration and domain directories. At this time, for each directory partition in the Partitions container of the configuration section (CN = partitions, CN = configuration, DC = forestRootDomain), a cross-reference object is created (class crossRef). The cross-reference object defines the name and location of the servers that store each directory partition in the forest. When each subsequent domain or application directory section is created, the creation of a cross-reference object in the Partitions container is initiated.
- Add and remove application directory partitions . Application directory partitions are special sections that you can create on Windows Server 2003, Windows Server 2008 or Windows Server 2008 R2 domain controllers to provide dynamic data storage for LDAP applications. If your forest is running at the Windows Server 2000 level, then in such a forest all non-domain data is limited to configuration and schema data that is replicated to all domain controllers in the forest. In a Windows Server 2003/2008 and 2008R2 forest, application directory sections provide storage of application specific data on a domain controller, which can be played on any domain controller in the forest.
- Confirmation of domain renaming instructions . The last action performed by the domain naming master is confirmation of the domain renaming instructions. Usually, domains are renamed with the help of a special command line utility. So, when using the Rendom.exe utility, which is designed to rename domains, in order to rename a domain, the utility should have access to the domain naming master. In addition to the above features, the domain naming master is also responsible for confirming domain renaming instructions. When you run the specified tool, the domain script's msDS-UpdateScript attribute of the Partitions container object (CN = partitions, CN = configuration, DC = forestRootDomain) of the Configuration directory section is written to the XML directory with domain renaming instructions on the domain controller with the role of the wizard. It is worth remembering that the Partitions container can only be updated on a domain controller that contains the role of the domain naming wizard. In addition to the value of the msDS-UpdateScript attribute, the Rendom.exe utility writes the new DNS name of each renamed domain to the msDS-DnsRootAlias attribute of the cross-reference object (the crossRef class) corresponding to that domain. Again, since the cross-reference object is stored in the Partitrions container, this object can only be updated on a domain controller with the role of the domain naming wizard. The changed attribute data msDS-UpdateScript and msDS-DnsRootAlias are replicated to all domain controllers in the forest.
By default, the domain naming master role gets the first domain controller in a new forest, but you can move this role at any time using the Active Directory - Domains and Trust snap-in or the Ntdsutil.exe command-line tool . Do not forget that it is recommended to have the roles of the schema master and the domain naming master on one domain controller. A domain controller that has been assigned the role of a domain naming master must also be a global catalog server. Otherwise, some operations may fail. The schema master is identified by the value of the fSMORoleOwner attribute in the Partitions container.
Just as in the case of the previous operations wizard, if you try to perform any of the above operations when the operation wizard is not available, your actions will fail. But since all these actions are performed for a long period of time almost once, that you can recognize a domain naming master in an unsuitable state, you can find out at a critical moment, therefore, periodically check the availability of forest operation wizards.
')
Roles of domain level operation wizards
Unlike the forest level, each Active Directory domain has the following three roles of operations wizards:
- Relative RID ID Wizard
- PDC Primary Domain Controller Emulator
- Infrastructure master
Let us consider in detail each of these wizards of operations.
RID Master

The first master of operations for the domain level described in this article will be the relative identifier master (RID). The RID wizard is used to manage a pool of RIDs in order to generate security identifiers (SIDs) for such security principals as users, groups, and computers, as well as for moving objects from one domain to another. The SID of the security principal must be unique for the entire domain, so each security principal is assigned a unique security identifier SID, which contains the domain identifier and a relative RID that is unique to each security principal. All SIDs have four different elements. For example, according to Microsoft documentation, the elements of identifier S1-5-Y1-Y2-Y3-Y4 are provided in the following table:
Table 1. The structure of the element identifier
| SID element | Description |
| S1 | Indicates the SID revision. Currently only one revision is used for SID |
| five | Indicates the issuing center of a security principal. The value 5 is always specified for the Windows NT, Windows 2000, Windows 2003, Windows 2008 and Windows 2008 R2 domains. |
| Y1-Y2-Y3 | Part of the domain SID. For security principals created in the domain, this identifier element is identical |
| Y4 | Relative identifier (RID) for a domain that represents a user or group name. This item is generated from the RID pool on the domain controller during object creation |
Since security principals can create any domain controller, a mechanism is needed to ensure the uniqueness of the SID identifiers generated by the domain controller and therefore the RID master ensures that two domain controllers do not assign the same RID. The RID master assigns a block of relative RIDs, called a RID pool, to each controller in the domain. In other words, the RID Operations Wizard is responsible for maintaining a pool of relative identifiers for using domain controllers in a domain and providing groups of relative identifiers for each domain controller. When a new domain controller is added to a domain, the RID master assigns a pool of 500 relative RID requests to that domain controller. Every time a new security principal is created on a domain controller, a domain controller assigns a relative identifier from its pool to assign an identifier to a new object. When the number of relative RIDs in this RID pool on any domain controller drops below 100, in other words, approaches zero, the RID master requests another RID block. After completing the request, the RID master assigns another domain pool of 500 relative RIDs to the domain controller.
More to the point, the RID master does not count pool numbers, but serves the higher value of the last selected range. When a new request is received, the value of the new pool increases by one and 499 new values. After that, the two values are sent to the requested domain controller to use the new relative RIDs. If the local RID pool of the domain controller is empty or the RID master is unavailable for some time, the process of creating accounts on some domain controllers may be interrupted and an event 16645 will be recorded in the event log of this domain controller. This error code indicates that the maximum account identifier from those allocated to the domain controller and the domain controller could not get a new pool of identifiers from the RID master. In the same wayadding a new object to the domain will create an event with the code 16650, indicating that the object could not be created because the directory service could not allocate a relative identifier. The mechanism for requesting a new block of RID identifiers is designed to prevent such interruptions, since the query is executed before exhausting all the available RID identifiers in the pool. To enable the account creation process again, you need to either connect a domain controller that manages the RID master role to the network, or move this role to another domain controller.The mechanism for requesting a new block of RID identifiers is designed to prevent such interruptions, since the query is executed before exhausting all the available RID identifiers in the pool. To enable the account creation process again, you need to either connect a domain controller that manages the RID master role to the network, or move this role to another domain controller.The mechanism for requesting a new block of RID identifiers is designed to prevent such interruptions, since the query is executed before exhausting all the available RID identifiers in the pool. To enable the account creation process again, you need to either connect a domain controller that manages the RID master role to the network, or move this role to another domain controller.
Also during the migration of Active Directory objects between domains, the RID master is required, that is, the object can migrate only if the RID master is available in the domain. The presence of an active current operations wizard prevents the creation of two objects with identical identifiers in different Active Directory domains. When migrating objects from one domain to another, Microsoft recommends using the Acrive Directory Migration Tool. By default, the RID master role is assigned to the first domain controller installed in the forest. You can move this role at any time using the Active Directory Users and Computers snap -in or using the tools Ntdsutil.exe . RID master is identified by attribute valuefSMORoleOwner in the rIDManager class object in the Domain section.
PDC emulator

Domain controller with designated PDC emulator operation wizard(The main domain controller is the Primary Domain Controller) serves as the main domain controller for backward compatibility with operating systems below Windows 2000. At the time of the member servers and Windows NT 4.0 client computers, only the main PDCs could make changes to the directory. Older tools, clients, and utilities that support Windows NT 4.0 are not designed so that all Active Directory domain controllers can write to the directory, and therefore these applications need to be connected to the PDC. A domain controller with the role of a PDC emulator registers itself as the main PDC domain controller, specifically so that various low-level applications can localize the writing domain controller. Despite,that in our time servers and client computers with operating systems below Windows 2000 are almost impossible to meet, the PDC emulator still remains the most important role of operations wizards. In addition to backward compatibility with applications running on Windows NT 4.0, the PDC emulator performs the following important functions:
- . , , , PDC- . , . , , , , . , PDC-, . , PDC- ;
- . , . , , , , . , PDC- : , , PDC GPO PDC-;
- . Active Directory. «» . . , , . , . , PDC , , , ;
- . Active Directory, Kerberos, DFS-R FRS , . PDC- . PDC-, – . , Win32Time.
By default, the PDC emulator master role is assigned to the first domain controller installed in the forest. You can move this role at any time using the Active Directory Users and Computers snap -in or using the tools Ntdsutil.exe . The PDC emulator wizard is identified by the value of the fSMORoleOwner attribute in an object of the rIDManager class in the root object of the Domain section.
Infrastructure master

In organizations based on multiple domains, objects in some domains often refer to objects in others. Infrastructure mastersimilar to a device that tracks members of a group of domains. The infrastructure master is responsible for updating the group-user links between domains, thereby ensuring that the name changes of objects are reflected in information about group memberships localized in the domain. The Infrastructure Wizard maintains an updated list of such links, and then replicates this information to all controllers in the domain. You should know that when a member of another domain is added to the group of the target domain, the distinguished name of the new member is added to the member attribute and if the domain controller of the member of such a group is not available, then a phantom object is created in the domain services, representing the member of such a group. Such an object can contain only the member SID, the distinguished name (DN), and the object GUID. In the event that the infrastructure master is unavailable,“group - user” links between domains will not be updated. Periodically, the infrastructure master scans domain accounts and checks group memberships. If a user account moves to a new domain, the infrastructure master identifies the new domain of the user account and updates the groups accordingly.
It is worth paying attention to the fact that the role of the infrastructure master should not be performed by a domain controller that is a global catalog server. Otherwise, the infrastructure master will not update information about objects, since it does not contain references to objects that it does not store. This is because the global catalog server stores partial replicas of all objects in the forest. As a result, the cross-domain object links in this domain will not be updated, and the corresponding warning will appear in the event log of this domain controller. By default, the infrastructure master role gets the first domain controller installed in the forest. You can relocate this role at any time using the Active Directory Users and Computers snap -in or using the toolsNtdsutil.exe . The infrastructure master is identified by the value of the fSMORoleOwner attribute in the Infrastructure container in the Domain section.
How can I determine which domain controller has the role of FSMO
In principle, they have already figured out the theoretical part, but now it would be nice to practice. Despite the fact that in your organization there can be only one domain, a large number of domain controllers can be installed and administrators may not always know exactly which domain controllers are assigned the roles of operations masters. For example, if you are restructuring your domain, you will need to know which domain controller is assigned to one or another role. Each role can be defined using the GUI or command line tools. Consider both methods.
Identifying Operation Masters Ownerships with GUI Tools
First of all, you need to remember that to identify the operations wizards in Active Directory Domain Services, various administrative toolings are used. Most difficult to identify the wizard schema. From him and begin. To find out which domain controller has the schema master role, follow these steps:
- Log on to a domain controller with an account that has administrator rights;
- Open the Run dialog box and register the Active Directory Schema snap-in dynamic library using the regsvr32.exe command schmmgmt ;
- Then open the MMC Management Console window and call the Add New Snap-In dialog. In the list of snap-ins, select Active Directory Schema , as shown in the following illustration:
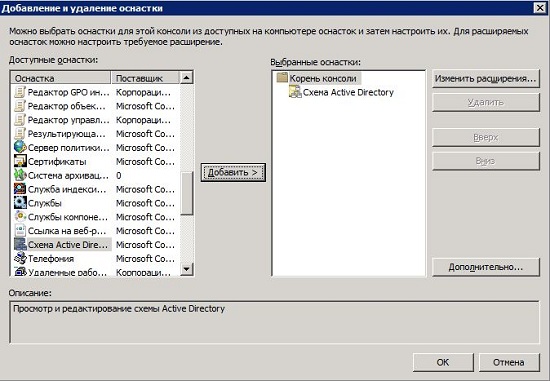
Fig. 1. Add the Active Directory Schema snap-in - In the open Active Directory Schema snap -in, right-click on the root node of the snap-in and select the Operations Master command from the context menu , as shown below:

Fig. 2. Master Operations Scheme
To identify the remaining operations wizards, you need to perform significantly fewer actions. To find which domain controller has the rights of the domain naming operation wizard, you need to:
- Open the window of the Active Directory - domains and trust snap-in ;
- « » , :
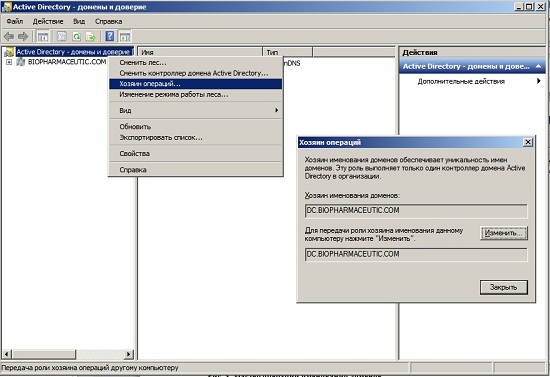
Fig. 3.
And to identify the remaining three roles at the domain level, you need to perform the least of all actions. In other words, all remaining roles of operations wizards can be found in a single dialog box. To do this, open the Active Directory Users and Computers snap -in , right-click on your domain and select the Operations Hosts command from the context menu . In the dialog box that appears on the appropriate tabs, you can view the names of domain controllers that are assigned current roles. The “Operations Hosts” dialog box can be viewed in the following illustration:
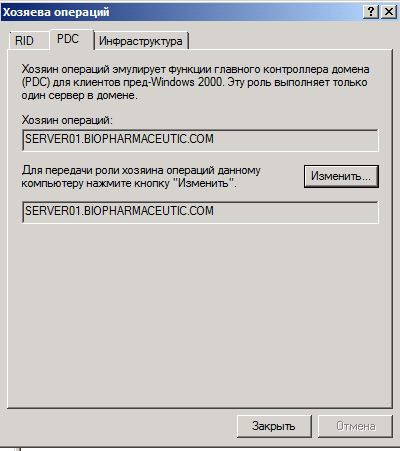
Fig. 4. Operations masters for domain level
Identifying owners of operations wizards using command line tools
As with most features provided by Windows operating systems, you can identify all owners of operations wizards with the help of a special command line utility. In Active Directory Domain Services, the Ntdsutil command-line utility is used to monitor certain changes . To view all domain controllers equipped with operations master roles using this utility, perform the following steps:
- Open a command prompt;
- Run the Ntdsutil command ;
- Navigate to the owner tokens of the NTDS role management by entering the roles command ;
- Active Dirctory. connections ;
- «server connections» connect to server , «Enter» ;
- fsmo management , quit ;
- «Select operation target» , , , , ;
- , List roles for connected server , :
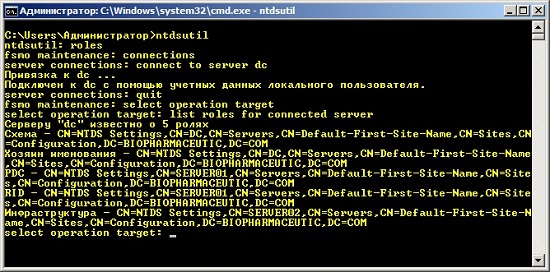
Fig. 5. Defining operation wizards using command line tools.
You can also use the Dcdiag utility with the command / test: Knowsofroleholders / v to view the FSMO roles . Part of the output of this command can be seen below:
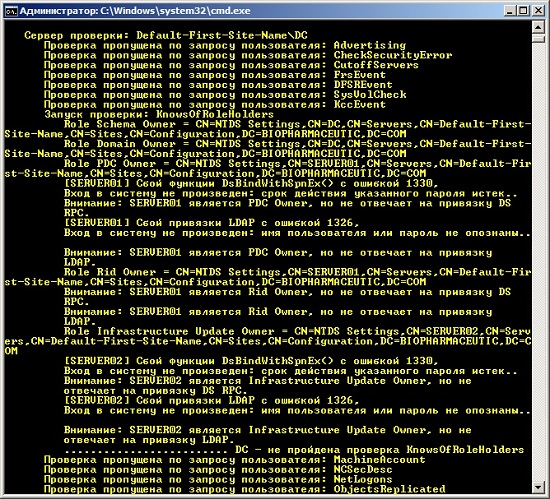
Fig. 6. Defining FSMO Roles with the Dcdiag Utility
Capturing and transferring operations master roles
In Active Directory, there are such concepts as transferring and capturing (also known as recall) roles of operations wizards. First of all, you should find out what it is and what is the difference between these concepts.
As mentioned above, initially all five roles of operations wizards are installed on the first domain controller in the forest. It is usually accepted to improve performance and fault tolerance in an organization, within one domain, several additional domain controllers. And, accordingly, in order to avoid conflicts in the future, it is recommended to immediately distribute the roles of operations wizards to different domain controllers. Also, if you need to disable a domain controller that performs the role of an operations master or decommission it, you should transfer all FSMO roles from it to other domain controllers.
In turn, the capture of the role is necessary if the domain controller with specific roles of the operations wizards has failed and you did not have time to transfer the roles from this DC. The risks that you may incur in the event of a failure of domain controllers with operations master roles were described a little earlier in this article. In this case, you have no way to transfer the FSMO role to your preferred role transfer method. Therefore, you only have to capture the operation marker by revoking the role. But it is worth remembering that the capture of the role is the most radical method and it is necessary to perform it only in the case when the owner of the roles of the masters of operations has failed. When the process of capturing the role of the operations wizard is performed, the attribute of the fsmoRoleOwner object changes on an existing computer,representing the root data directory, without performing any data synchronization. Other domain controllers, of course, learn about the new owner of the role of FSMO as the changes are replicated.
Consider the processes of transferring and capturing the roles of operations wizards.
To transfer the FSMO role, follow these steps:
- Open a snap-in that can be used to identify the roles of the operations wizard, which were discussed in the previous section of this article. For example, to transfer the role of the PDC emulator, open the Active Directory Users and Computers snap -in ;
- Using the current snap-in, connect to the domain controller to which the operations master role will be transferred. This can be done using the dialog box "Domain controller change" , which is called from the context menu of the root node of the snap-in. The dialog box for changing the domain controller can be seen below:
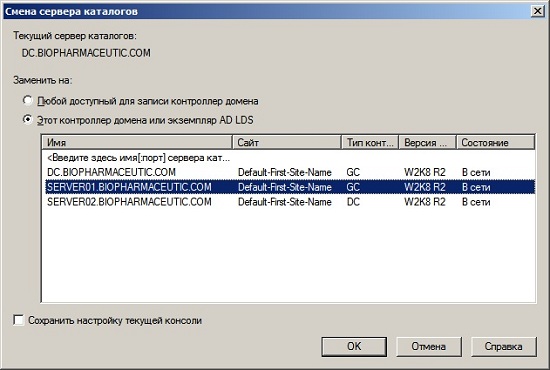
Fig. 7. Changing the domain controller for transferring the operations master role - Open the "Operations Hosts" dialog box , go to the required tab and click on the "Change" button . The role of the operations wizard will be transferred to another domain controller.
The process of capturing the roles of operations wizards is a bit more complicated than the transfer, since for this it is necessary to use the Ntdsutil utility , which was discussed in the previous section. In order to seize the role of a failed domain controller, follow these steps:
- Open a command prompt and go to the ntdsutil utility ;
- Switch to NTDS role management using the roles command ;
- , . connections ;
- «server connections» connect to server ;
- fsmo management , quit ;
- fsmo management seize Enter ;
- , , FSMO-, .
The attentive reader may ask the following question: what can I do if the dead domain controller was able to be reanimated and how do I return ownership of the captured role to this domain controller? It's all relatively simple.First of all, you need to know that if the role of a PDC emulator or infrastructure has been revoked, then you will be able to transfer back the role of the operations wizard to the restored domain controller without any special problems.
But in the event that the role of the scheme master, domain naming or relative RID identifiers was captured, you will need to perform the following actions:
- Physically disable such a domain controller from the network;
- Reduce the role of a domain controller to a member server using the Dcpromo / forceremoval command ;
- . Ntdsutil Metadata Cleanup ;
- , , ;
- .

In this section, I will talk a little about the recommendations for locating all the roles of operations wizards on domain controllers. As such, there are not many such recommendations, so I will try to simplify this section as soon as possible.
First of all, if you have one forest, one domain and one domain controller, then all five roles of the operation wizards will be placed on this particular domain controller, but in order to balance the load, it is recommended to transfer the roles to other domain controllers.
The main recommendations for placing FSMO roles are as follows:
- RID PDC- . . , , Active Directory . , , , ;
- . , , . , , , , , . , . , , , , , ;
- The infrastructure master role must be located on a domain controller that does not serve as a global catalog server . Typically, the infrastructure master should be deployed on a domain controller that does not serve as a global catalog server, but has a direct connection object to one of the global directories in the forest. Since the global catalog server stores partial replicas of all objects in the forest, the infrastructure wizard hosted on the global catalog server will not perform updates because it does not contain references to objects that it does not store.
Guided by these three rules, you can place the master of operations in your forest in the best way possible.
Instead of conclusion
So, this article comes to an end. In this article, you learned about the role of operations masters and why they are needed. Several examples were considered that described what would happen if there were no operations wizards in Active Directory Domain Services and all domain controllers were equal. All five FSMO roles were examined in detail, methods for identifying roles on domain controllers were described. You also learned about the transfer and capture of operations master roles and how you can perform these actions. In addition, you got acquainted with three rules that should guide you when choosing options for hosting operations wizards on domain controllers in your organization.
Source: https://habr.com/ru/post/133370/
All Articles