Mandate OS OS MSVS 3.0
Mandatory access control system delivers many problems to novice developers under MAWS. A typical problem is the impossibility of working with files, access to which is restricted by mandatory labels. Usually this problem is explained by the glitchiness of the MSWS. Although this is not at all in the MSWS. It's all about the misapplication of mandated labels. A misuse of tags is associated with a lack of understanding of the basic principles of mandatory access control. In this article, I will outline the basic principles of the mandatory model — the basis for secure access to files in this operating system. I did not specifically describe the practical side of the question in order to focus attention on the fundamentals of the model.
It is no secret to anyone that the WSWS is in fact the good old RedHat (more old than good). These two operating systems do not differ much. In addition to the modified desktop images, and the RF flag on the user login dialog, there are several differences associated with restrictions imposed by admissions to sensitive information. One of these differences is the presence in the MAWS, in addition to discretionary, and also mandatory access control. In addition to an increased level of security, this also causes problems when developing programs.
In addition to the problems described above, there are more interesting cases. There is a database stored on the server. It is impossible to work with this base from a computer on which a non-zero access level is set. And the fact is that the MSVS to all sent packages adds information about the current level of secrecy, which makes these packages unsuitable for reading.
When mindlessly assigning mandatory labels common to all users of files, they become inaccessible for some users. As a result, login is not possible.
')
There are many more problems. All these problems are not so difficult if you know what they are caused by and how to solve them. But in practice, it is not always clear what caused the failure. And how to solve the problem is all the more unclear. In addition, in the Qt 4.2 library (as far as I know, 4.2 is the current version of the library certified for MSWS), for obvious reasons, there are no classes for working with mandatory labels. All this together makes life difficult for the developer.
Mandatory access control in OS MSVS is based on the Bell-LaPadula’s mandatory security model. This model is based on the rules of secret workflow applied in many countries.
In contrast to discretionary control, in which the rights to read, write and execute are directly assigned to users, access control in the mandatory model occurs implicitly. All users (subjects) and files (objects) are assigned access levels. For example, “secret”, “top secret”.
Example of access level hierarchy:
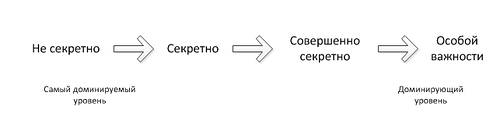
Access levels are ordered by the dominance of one level over another. Then access to protected files is carried out according to two simple rules:
1. The user has the right to read only those documents whose security level does not exceed his own security level.
This rule protects information processed by higher-level users from access by low-level users.
2. The user has the right to enter information only in those documents whose security level is not lower than his own security level.
This rule prevents violation of the access mode by high-level participants in the processing of information to low-level users.
We illustrate both rules with a picture:
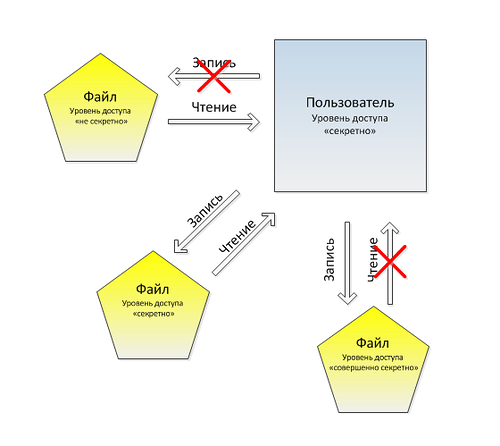
The figure shows the user's relationship with the level of "secret" with the subjects in the three-level credentials model.
Moreover, "top secret"> "secret"> "not secret"
Thus, by assigning access levels to all objects and subjects, we will determine all permissible interactions within the system. It can be seen from the above described rules that mandatory access control does not limit the interaction of objects and subjects that are at the same access level. Therefore, for effective access control, the mandate model is used in conjunction with the discretionary one, which describes the interaction of objects and subjects at the same level.
In the Bella LaPadula model there are only two types of access: read and write. If other types of access are needed: for example, execution, they will still be reduced to reading and writing. This is due to the fact that the model does not register user actions on files, but information flows. Which can be of two kinds: from user to file (write), and from file to user (read).
Further development of the Bella LaPadula model has led to the emergence of a variety of mandate models. However, the Bella LaPadula model is the classic model of mandatory access control.
Understanding these basic principles of the model will allow you to avoid many of the problems associated with mandatory access to files, and perhaps even help you correctly configure access in the system.
It is no secret to anyone that the WSWS is in fact the good old RedHat (more old than good). These two operating systems do not differ much. In addition to the modified desktop images, and the RF flag on the user login dialog, there are several differences associated with restrictions imposed by admissions to sensitive information. One of these differences is the presence in the MAWS, in addition to discretionary, and also mandatory access control. In addition to an increased level of security, this also causes problems when developing programs.
In addition to the problems described above, there are more interesting cases. There is a database stored on the server. It is impossible to work with this base from a computer on which a non-zero access level is set. And the fact is that the MSVS to all sent packages adds information about the current level of secrecy, which makes these packages unsuitable for reading.
When mindlessly assigning mandatory labels common to all users of files, they become inaccessible for some users. As a result, login is not possible.
')
There are many more problems. All these problems are not so difficult if you know what they are caused by and how to solve them. But in practice, it is not always clear what caused the failure. And how to solve the problem is all the more unclear. In addition, in the Qt 4.2 library (as far as I know, 4.2 is the current version of the library certified for MSWS), for obvious reasons, there are no classes for working with mandatory labels. All this together makes life difficult for the developer.
Mandatory access control in OS MSVS is based on the Bell-LaPadula’s mandatory security model. This model is based on the rules of secret workflow applied in many countries.
In contrast to discretionary control, in which the rights to read, write and execute are directly assigned to users, access control in the mandatory model occurs implicitly. All users (subjects) and files (objects) are assigned access levels. For example, “secret”, “top secret”.
Example of access level hierarchy:

Access levels are ordered by the dominance of one level over another. Then access to protected files is carried out according to two simple rules:
1. The user has the right to read only those documents whose security level does not exceed his own security level.
This rule protects information processed by higher-level users from access by low-level users.
2. The user has the right to enter information only in those documents whose security level is not lower than his own security level.
This rule prevents violation of the access mode by high-level participants in the processing of information to low-level users.
We illustrate both rules with a picture:

The figure shows the user's relationship with the level of "secret" with the subjects in the three-level credentials model.
Moreover, "top secret"> "secret"> "not secret"
Thus, by assigning access levels to all objects and subjects, we will determine all permissible interactions within the system. It can be seen from the above described rules that mandatory access control does not limit the interaction of objects and subjects that are at the same access level. Therefore, for effective access control, the mandate model is used in conjunction with the discretionary one, which describes the interaction of objects and subjects at the same level.
In the Bella LaPadula model there are only two types of access: read and write. If other types of access are needed: for example, execution, they will still be reduced to reading and writing. This is due to the fact that the model does not register user actions on files, but information flows. Which can be of two kinds: from user to file (write), and from file to user (read).
Further development of the Bella LaPadula model has led to the emergence of a variety of mandate models. However, the Bella LaPadula model is the classic model of mandatory access control.
Understanding these basic principles of the model will allow you to avoid many of the problems associated with mandatory access to files, and perhaps even help you correctly configure access in the system.
Source: https://habr.com/ru/post/133247/
All Articles