Banking Trojan Carberp acquires bootkit functionality
Today we are publishing a part of our investigation into the Carberp malware, which is aimed at remote banking services (RB).
This month we managed to collect interesting information about the new modification of the Trojan from the Win32 / TrojanDownloader.Carberp family. This is one of the most common malicious programs in Russia, which is engaged in the theft of funds in remote banking systems and is aimed primarily at the attacks of companies that carry out a large number of cash transactions every day. We already talked about this Trojan in our presentation “Cybercrime in Russia: Trends and issues” . The developers of this malware are one of the most active cybercrime groups in Russia and nearby countries, which is involved in stealing money from RBS. The first incidents with the Carberp Trojan were recorded by us at the beginning of 2010, and the peak of its activity this year falls at the end of spring and summer, and the number of incidents related to this program has increased again since the beginning of autumn.

')
The absolute leader in the number of recorded incidents is Russia, which is confirmed by our statistics by region:

The cash profits of a cybercrime group are estimated at millions of dollars a week, and, as our monitoring shows, attackers do not stint investing money in the development of their malicious technologies. In particular, it shows the evolution of the Hodprot dropper , which was seen in the installations of Carberp, RDPdoor and Sheldor . Moreover, in order to open the backdoor in the system and manually carry out monetary transactions manually, Carberp can also set up RDPdoor. At the moment, we have established that these malicious programs are the result of the activity of one cybercriminal group.
At the beginning of this year, information on the sale of the bootkit builder, not detectable by anti-virus tools, began to appear on various closed cybercriminal forums. The cost of this builder was estimated at several tens of thousands of dollars and seemed fantastic in comparison, for example, with prices for the same SpyEye and Zeus.

How many total cybercriminal groups managed to acquire this toolkit - we do not know. But we had a sample of the installer of the bootkit part compiled, which loaded the driver stub. We were able to detect the identity of this code with some other malware. At the moment, its use is known only in the Rovnix bootkit , which was the first to massively apply this functionality. And from the end of the summer, testing began (distribution in very limited quantities) of the special version of Carberp with bootkit-part. The fact that the bot is working in test mode was indicated by two factors: a large number of debugging messages about the installation process and a very low prevalence. We managed to get access to the logs on the command center of bots with the bootkit-part and confirm the fact of the active testing process:
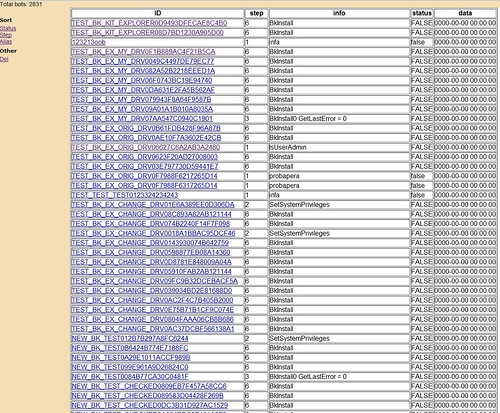
C & C for the test version of the bot
A large number of debug messages were found in the installer of the new version of Carberp:
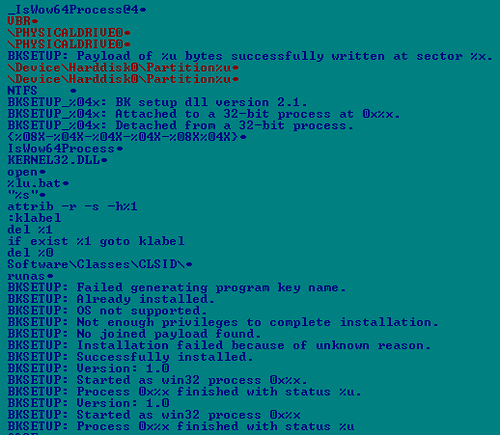
Lines inside unpacked Carberp code
The bootkit part itself was left without significant modifications and is almost completely identical with what we have already seen in Rovnix. Technical details on the work of the bootkit can be seen on the slides of our report “Defeating x64: Modern Trends of Kernel-Mode Rootkits” , which we presented at the Ekoparty conference this fall.
But the installer has undergone significant modifications. In addition to installing Carberp’s bootkit functionality into the system, a number of vulnerabilities are being exploited to enhance privileges. First of all, this is due to the fact that installing a bootkit requires administrator or system privileges. During an attack on corporate users (namely, this is the goal of attackers) who have access to RBS, they may simply not have rights to run the executable file with high privileges, and then an attack using social engineering methods will not help. Therefore, the installer is now operating four different vulnerabilities to increase local privileges in the system:
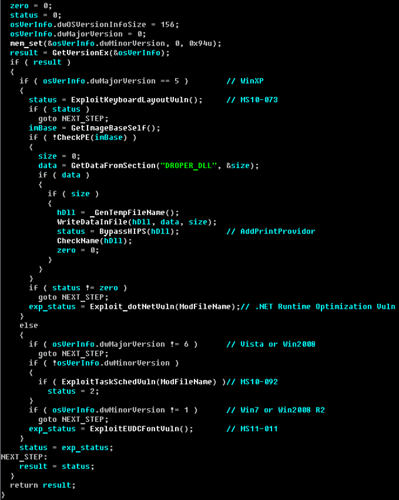
• MS10-073 (win32k.sys KeyboardLayout vuln)
• MS10-092 (Task Scheduler vuln)
• MS11-011 (win32k.sys SystemDefaultEUDCFont vuln)
• .NET Runtime Optimization vuln
Another interesting point of the dropper is the removal of various hooks and splits from the following system functions before directly launching the bootkit installer:

This is a kind of bypass of various sandboxes and monitoring tools that use hooks in user mode.
In the process of working, the bootkit code bypasses the digital signature checks and other defense mechanisms by loading a malicious driver. The task of this driver is to inject the payload into the address space of user-mode processes.
After unpacking the original driver file, you can find the build date and version of the compiler:
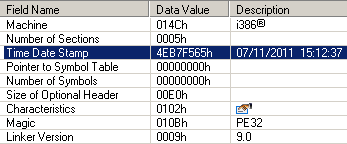
From these data, it is clear that the file was compiled at the beginning of this month, and now, apparently, it is running in for stability. After the compilation, an interesting line remained in the driver, pointing to the source directory on the developers computer:
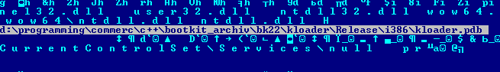
Apparently, this is not the first and not the latest version for tests, which has appeared recently. We also do not exclude the possibility that the author, who previously offered it for sale, is further supporting this code. Since, besides Rovnix and this version of Carberp, malware based on this code is unknown to us, and there has never been a low-level part in any version of Carberp, this suggests that they did not have developers of this qualification.
The main task of this driver is to introduce a dynamic library with a payload into the address space of user processes.

After unpacking a dynamic library with a payload, you can also see the compilation date, from which it becomes clear that it was compiled at different times when compared with the driver.
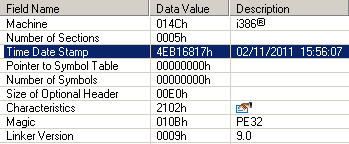
Inside there was an interesting string constant pointing to a completely different directory with the project and interesting root directory called “GSVSoft”.
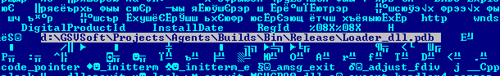
Interestingly, compilation dates and paths to project directories are different, which indirectly indicates that two different development teams were working. In addition, with the name "GSVSoft" there is a very real domain (gsvsoft.ru), but it is impossible to draw any conclusions based only on this.
The main functionality of the dynamic library is in many respects similar to the previous version of Carberp. The main objective of this module is the introduction of JS scripts to pages with Internet banking, the loading of additional plug-ins and interaction with the command center.
All of the above suggests that the current methods of concealment in the Carberp Trojan system do not suit its developers, and they are ready to invest in the development of their own technologies to bypass the security software. So the evolution of this malicious program over the past two years has made it number one in terms of the number of incidents with clients of Russian banks, and not only commercial organizations suffer from it - there are incidents in state institutions. With the new bootkit, Carberp comes one step further in analysis complexity and detection, with threats like TDL4 and Rovnix.
Despite the fact that now the main purpose of Carberp are the clients of Russian banks, this situation can quickly change, as there are no technological obstacles for attacks on banks in other countries in this cybercriminal group. And access to other regions does not occur, most likely due to the fact that they are satisfied with everything so far and in this form. But in the near future they may find partners in attacks in other regions. Last year, Carberp was already active in European countries, but then it began to decline.
This month we managed to collect interesting information about the new modification of the Trojan from the Win32 / TrojanDownloader.Carberp family. This is one of the most common malicious programs in Russia, which is engaged in the theft of funds in remote banking systems and is aimed primarily at the attacks of companies that carry out a large number of cash transactions every day. We already talked about this Trojan in our presentation “Cybercrime in Russia: Trends and issues” . The developers of this malware are one of the most active cybercrime groups in Russia and nearby countries, which is involved in stealing money from RBS. The first incidents with the Carberp Trojan were recorded by us at the beginning of 2010, and the peak of its activity this year falls at the end of spring and summer, and the number of incidents related to this program has increased again since the beginning of autumn.

')
The absolute leader in the number of recorded incidents is Russia, which is confirmed by our statistics by region:

The cash profits of a cybercrime group are estimated at millions of dollars a week, and, as our monitoring shows, attackers do not stint investing money in the development of their malicious technologies. In particular, it shows the evolution of the Hodprot dropper , which was seen in the installations of Carberp, RDPdoor and Sheldor . Moreover, in order to open the backdoor in the system and manually carry out monetary transactions manually, Carberp can also set up RDPdoor. At the moment, we have established that these malicious programs are the result of the activity of one cybercriminal group.
At the beginning of this year, information on the sale of the bootkit builder, not detectable by anti-virus tools, began to appear on various closed cybercriminal forums. The cost of this builder was estimated at several tens of thousands of dollars and seemed fantastic in comparison, for example, with prices for the same SpyEye and Zeus.

How many total cybercriminal groups managed to acquire this toolkit - we do not know. But we had a sample of the installer of the bootkit part compiled, which loaded the driver stub. We were able to detect the identity of this code with some other malware. At the moment, its use is known only in the Rovnix bootkit , which was the first to massively apply this functionality. And from the end of the summer, testing began (distribution in very limited quantities) of the special version of Carberp with bootkit-part. The fact that the bot is working in test mode was indicated by two factors: a large number of debugging messages about the installation process and a very low prevalence. We managed to get access to the logs on the command center of bots with the bootkit-part and confirm the fact of the active testing process:

C & C for the test version of the bot
A large number of debug messages were found in the installer of the new version of Carberp:

Lines inside unpacked Carberp code
The bootkit part itself was left without significant modifications and is almost completely identical with what we have already seen in Rovnix. Technical details on the work of the bootkit can be seen on the slides of our report “Defeating x64: Modern Trends of Kernel-Mode Rootkits” , which we presented at the Ekoparty conference this fall.
But the installer has undergone significant modifications. In addition to installing Carberp’s bootkit functionality into the system, a number of vulnerabilities are being exploited to enhance privileges. First of all, this is due to the fact that installing a bootkit requires administrator or system privileges. During an attack on corporate users (namely, this is the goal of attackers) who have access to RBS, they may simply not have rights to run the executable file with high privileges, and then an attack using social engineering methods will not help. Therefore, the installer is now operating four different vulnerabilities to increase local privileges in the system:

• MS10-073 (win32k.sys KeyboardLayout vuln)
• MS10-092 (Task Scheduler vuln)
• MS11-011 (win32k.sys SystemDefaultEUDCFont vuln)
• .NET Runtime Optimization vuln
Another interesting point of the dropper is the removal of various hooks and splits from the following system functions before directly launching the bootkit installer:

This is a kind of bypass of various sandboxes and monitoring tools that use hooks in user mode.
In the process of working, the bootkit code bypasses the digital signature checks and other defense mechanisms by loading a malicious driver. The task of this driver is to inject the payload into the address space of user-mode processes.
After unpacking the original driver file, you can find the build date and version of the compiler:

From these data, it is clear that the file was compiled at the beginning of this month, and now, apparently, it is running in for stability. After the compilation, an interesting line remained in the driver, pointing to the source directory on the developers computer:

Apparently, this is not the first and not the latest version for tests, which has appeared recently. We also do not exclude the possibility that the author, who previously offered it for sale, is further supporting this code. Since, besides Rovnix and this version of Carberp, malware based on this code is unknown to us, and there has never been a low-level part in any version of Carberp, this suggests that they did not have developers of this qualification.
The main task of this driver is to introduce a dynamic library with a payload into the address space of user processes.

After unpacking a dynamic library with a payload, you can also see the compilation date, from which it becomes clear that it was compiled at different times when compared with the driver.

Inside there was an interesting string constant pointing to a completely different directory with the project and interesting root directory called “GSVSoft”.

Interestingly, compilation dates and paths to project directories are different, which indirectly indicates that two different development teams were working. In addition, with the name "GSVSoft" there is a very real domain (gsvsoft.ru), but it is impossible to draw any conclusions based only on this.
The main functionality of the dynamic library is in many respects similar to the previous version of Carberp. The main objective of this module is the introduction of JS scripts to pages with Internet banking, the loading of additional plug-ins and interaction with the command center.
All of the above suggests that the current methods of concealment in the Carberp Trojan system do not suit its developers, and they are ready to invest in the development of their own technologies to bypass the security software. So the evolution of this malicious program over the past two years has made it number one in terms of the number of incidents with clients of Russian banks, and not only commercial organizations suffer from it - there are incidents in state institutions. With the new bootkit, Carberp comes one step further in analysis complexity and detection, with threats like TDL4 and Rovnix.
Despite the fact that now the main purpose of Carberp are the clients of Russian banks, this situation can quickly change, as there are no technological obstacles for attacks on banks in other countries in this cybercriminal group. And access to other regions does not occur, most likely due to the fact that they are satisfied with everything so far and in this form. But in the near future they may find partners in attacks in other regions. Last year, Carberp was already active in European countries, but then it began to decline.
Source: https://habr.com/ru/post/133173/
All Articles