Government communication based on Asterisk!
Turntables

“Pinwheel” is a closed system of party and government telephone communications in the USSR.
It was originally created on the orders of Vladimir Lenin, as an internal automatic telephone exchange of the Kremlin. Received the name "Pinwheel", because unlike the usual telephone network, where at that time the connection was made through the operator, the subscribers were connected to each other using a PBX and a dial pad ("Pinwheel").
The system was expanding intensively, and was also provided with access to other systems of government and military communications, which are also often called “Pinwheel” among the people, and officially:
')
ATS-1 - the most prestigious communication system for subscribers of the highest category - the first persons of the state, ministers.
PBX-2 is a wider network of city government communications.
"Pinwheel" was an important status symbol of the Soviet era. Regularly upgraded system of government PBX continues to operate today.
“Pinwheel” is not designed for secret negotiations, but it is linked to other government systems for secure communication of long-term cryptographic resistance, including mobile radio telephone (“Caucasus”) and others.
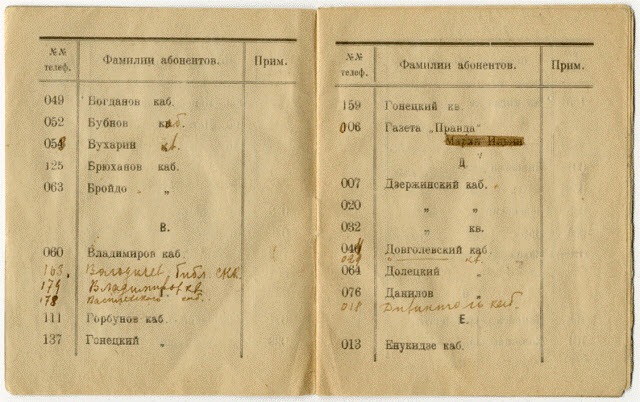
1922 The telephone number of F. Dzerzhinsky's “Turntables” is 007.
Asterisk + OpenVPN "Government Connection" of our time!
Organizing data transfer between offices over a secure communication channel using encryption is possible using OpenVPN.
In addition, when merging branches into a single number space and connecting them to Asterisk, there are often problems with configuring NAT and passing voice traffic without interference.
These problems are eliminated by combining offices using OpenVPN.
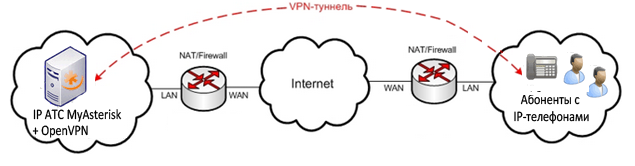
As a subscriber device, it is recommended to use IP phones, for example Yealink, supporting work with OpenVPN. This is an ideal scheme that allows you to configure a VPN tunnel and encryption between offices without using expensive VPN-enabled gateways.
Benefits of using OpenVPN
The convenience of connecting additional offices to Asterisk and no problems with NAT.
Work on secure communication channels. All traffic between offices is under the "seven locks", or rather under the protection of the OpenSSL library. Due to this, the whole set of ciphers available in this library is used. HMAC batch authorization can also be used to provide greater security and hardware acceleration to improve encryption performance.
Install OpenVPN
1. Download the distribution of OpenVPN at the link swupdate.openvpn.net/community/releases/openvpn-2.1.4.tar.gz:
wget swupdate.openvpn.net/community/releases/openvpn-2.1.4.tar.gz
and unpack the archive:
tar -xf openvpn-2.1.4.tar.gz
2. Download the compulsory LZO compression library necessary for compressing the data stream using the link www.oberhumer.com / opensource / lzo / download / lzo-2.04.tar.gz:
wget www.oberhumer.com/opensource/lzo/download/lzo-2.04.tar.gz
and unpack the archive:
tar -xf openvpn-2.1.4.tar.gz
3. It is also necessary to install the gcc.i386 library.
Install it from the repository:
yum install gcc.i386
Perhaps this library can already be installed, which can be checked with the command yum list | grep gcc.i386. It must be something like:
gcc.i386 4.1.2-48.el5 installed
libgcc.i386 4.1.2-48.el5 installed
If this library is not installed and you try to install directly with OpenVPN, then an error will be generated during compilation:
configure: error: not acceptable C compiler found in $ PATH
4. Install LZO from the unpacked archive (see p.2):
cd ... / lzo-2.04
./configure
make
make install
5. Install directly OpenVPN itself from the unpacked folder (see item 1):
cd ... / openvpn-2.1.4
./configure
make
make install
6. Create for convenience all the necessary folders for OpenVPN (during installation, these folders are not automatically created) and copy the necessary files there from the unpacked archive (see item 1):
mkdir / etc / openvpn
cp ... / openvpn-2.1.4 / easy-rsa / 2.0 / * / etc / openvpn
mkdir / etc / openvpn / keys - create a folder for certificates and keys
7. Optionally, edit the / etc / openvpn / vars file in accordance with the required parameters so that each time the keys are generated, do not enter the same parameters again.
8. Export the variables from the vars file and delete all possibly existing keys:
cd / etc / openvpn
source ./vars
./clean-all
9. We generate the private key and certificate of the certification server (CA) or call it differently - the Certification Authority, on the basis of which all other keys will be created (key and certificate for the VPN server and keys and certificates for VPN clients) (i.e. the usual PKI mechanism is used (public key infrastructure).
./build-ca
10. We generate the private key and certificate for the server:
./build-key-server name
11. We generate the private key and certificate for the client:
./build-key client1
12. We generate a 1024-bit key using the Diffie-Hellman algorithm, which is used in the key authentication mechanism when establishing a VPN tunnel. This key remains on the server.
Diffie-Hellman (DH) is an algorithm that allows two parties to obtain a shared secret key using a unprotected, but protected from substitution, communication channel.
./build-dh
13. (Optional) Generate a symmetric TLS-key to pre-protect the channel, even before establishing the VPN tunnel. This key is symmetric and must be located both on the server and on the client. We generate in folder / etc / openvpn / keys /
openvpn --genkey --secret ./ta.key
- All created keys, certificates and server-side requests are placed in the / etc / openvpn / keys folder for convenience (in case they were generated elsewhere). Client keys and certificates are transmitted in an appropriately secure way to client machines. In addition, for each certificate there is a private key and a certificate request file:
* .key - private key;
* .csr - certificate request;
* .crt - certificate;
Ideally, client private keys should not be generated on the server and then transferred to the client, but should be generated on the client itself using any established cryptographic provider (for example, the registry, smart card or flash drive is used as the private key storage). Then a certificate request file is created based on the generated private key, which is already sent over the network to the certification server (Certification Authority), where the generated certificate is transmitted over the network. (since the certificate request file and the encryption certificate itself do not constitute a value without a private key, they can be transmitted over unsecured communication channels).
- 14. Copy the sample server.conf VPN configuration file from the unzipped folder (see item 1) to the / etc / openvpn combat folder
cp ..... / openvpn-2.1.4 / sample-config-files / server.conf /etc/openvpn/server.conf
and edit the necessary parameters:
vi /etc/openvpn/server.conf
15. Copy the sample scripts to start and stop OpenVPN from the unzipped folder (see item 1) into the / etc / openvpn combat folder and edit them according to your preferences:
cp ..... / openvpn-2.1.4 / sample-config-files / openvpn-startup.sh / etc / openvpn
16. Start the OpenVPN server:
/etc/openvpn/openvpn-startup.sh
and check if the service started:
netstat -luntp | grep openvp
At this stage the server part is finished.
Setting up an IP phone Yealink consider in the next article.
Source: https://habr.com/ru/post/132710/
All Articles