Automatic collection and archiving of photo / video surveillance
TASK

Once, the authorities demanded to keep a record around the clock in the offices. And also, during working hours - periodically publish photos from offices on the site.
From my predecessor I got:
- Several offices with smart D-Link camcorders that photograph what is happening
- Server on FreeBSD
- The site of the organization, where the picture from each camera should go
- Network folder on the local network where records archives should be stored
Known:
- FreeBSD server is not accessible from the outside
- The hoster does not like being connected to his FTP more often than once a minute
- Considering the quality and thickness of communication channels, the cameras do not write video, but make periodic photos
At the time of setting the task, the video cameras independently connected to the FTP host and laid out the pictures on a schedule every minute. As a result, the hoster periodically blocked FTP access to the site.
')
DECISION
Solution - Theory
The solution to this problem was one of the lessons on information security, given to me once at SPSU ITMO. The lesson talked about security zones, their levels, and the rules for reading / writing between levels.
In a nutshell: an application with a higher level of security, for example, 1, can read and write to an application of level 2 or 3. But application 2 cannot read or write to application 1, although it can read and write to application 3.
In fact, the rules are somewhat more complicated , but I simplified to facilitate perception.
Who is who
The scheme of interaction of all the above elements is simple:
Cameras add photos to my server via FTP, the server copies them to a network folder, and also publishes them on a hosting.
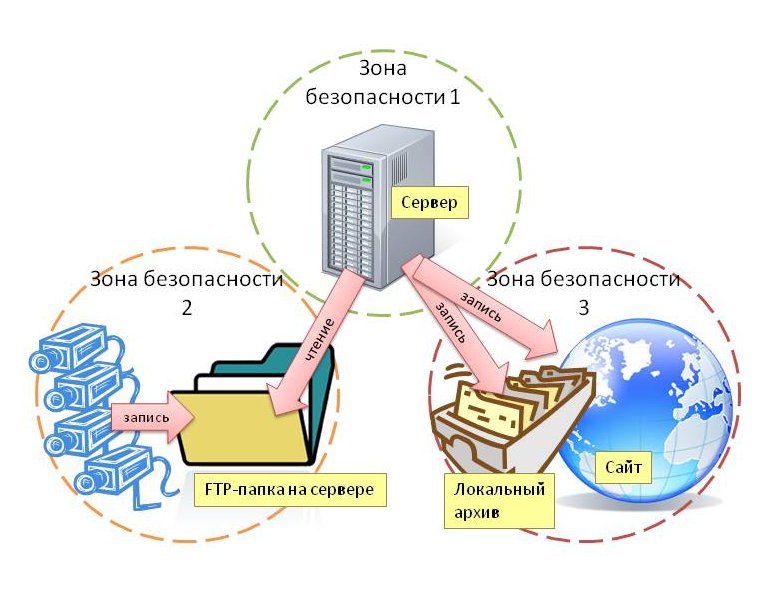
The server here is level 1, with access to all other levels. It is easy to notice that there is a rule violation here: cameras with a lower 2nd level are given the right to write on 1st level. In an amicable way, the server should have been taught to read the picture from the cameras, and not to open access for them, but in this case, the general security of the system was not affected. I explain: the trick is that cameras write to an FTP folder that has the same security level as cameras, i.e. 2nd The folder is separate from all others and contains only the current images from the cameras. Anyone who connects to FTP using the login and password from the camera will receive only a few photos of the offices, but will not be able to see all the archives.
While I painted it all, I thought that an attacker could upload his own photo containing some obscenity in this way, and it would automatically go to the site. We need to think about how to avoid it. You can, for example, restrict access to FTP over the static IP addresses of cameras and complicate passwords for accessing cameras and FTP. But it is better than teaching the server to read the image from the cameras on their own, I'm afraid not to think of anything. What to do - the technical limitations of cameras.
But let's not lose heart. The cameras do not hang in the most convenient place for physical access, but in order to dig into them - you need to know the password ... and you also need to put on a mask or turn off the light before you unscrew the camera, but these actions also spoil the intruder, because who knows what time was where.
Back to our sheep
So, the cameras will take pictures together on the server, and he, in turn, using the ingenious script on SH, will copy them to the archive folder with the current date and upload copies on the site if the current time matches the institution's mode of operation. And the next day, the server will clean up the archive folder that has already become yesterday from files with 0 size, collect all the photos into a video using the ffmpeg utility, and delete them.
Solution - Practice
- We install and configure on the FreeBSD ProFTP server (there is no argument about tastes, I just offer a clear option) and ffmpeg.
- Create a folder for video cameras and a folder for the archive (for example, somewhere in the folder / usr /)
- Create an account for video cameras in ProFTP and give it the created folder
- We set up cameras using their web interface, so that they are around the clock and, for example, every minute (to whom what period is right), connect to our server via FTP and save a photo.
- It is also very important to set the cameras with the correct date, time and automatic synchronization with the local NTP time server.
- We remember the FTP connection parameters of our hosting.
- We write an ingenious SH-script and put it in cron with a frequency of execution similar to the frequency of uploading photos with cameras, i.e. once a minute.
- Enjoy and go to report to the authorities.
Finally, the heart of the solution is a script of its own work
#!/bin/sh ## . , ## , day="`date +%Y-%m-%d`" archive="/store/STORE/cam_archive" ## FTP ## FTPUSER='*********' ## IP- FTPHOST='***.***.***.***' ## FTP FTPPASS='************' ## , REMOTEDIR="/www/img" ## LOCALDIR="/store/STORE/cam" ## , cd $LOCALDIR # echo . echo -================================================- date ## , mkdir $archive/$day >/dev/null 2>&1 ## . time1=`date +%H_%M_%S` ## , . # ( , ) echo . for file in $(ls -1 *.jpg) do camfolder=`echo ${file} | sed 's/\.jpg//'` mkdir $archive/$day/$camfolder >/dev/null 2>&1 cp $file $archive/$day/$camfolder/$time1\_$file done # , # grep , minutes1 minutes2 minutes1='01 03 05 07 09 11 13 15 17 19 21 23 25 27 29 31 33 35 37 39 41 43 45 47 49 51 53 55 57 59' minutes2=`date +%M` result=`echo ${minutes1} | grep ${minutes2}` # , (>=10 and <=18 and !result) if [ `date +%H` -ge 10 ] && [ `date +%H` -le 18 ] && [ -n "$result" ] then { echo FTP. ## FTP- ftp -n $FTPHOST <<EOF quote USER $FTPUSER quote PASS $FTPPASS binary cd $REMOTEDIR dir mput * a EOF } fi # (=00 and =00), . if [ `date +%H` -eq '00' ] && [ `date +%M` -eq '00' ] then { # LASTDAY=`date -v-1d +"%Y-%m-%d"` ## cd $archive/$LASTDAY/ ## ## 10k, - find $archive/$LASTDAY/ -size -10k -print | { while read files do rm "${files}" done } ## , for camfolders in $(ls -1 -U) do ## 1. y=0 ls -1 $archive/$LASTDAY/$camfolders/*.jpg | { while read files2 do y=`expr ${y} + 1` mv ${files2} $archive/$LASTDAY/$camfolders/img`printf %04d ${y}`.jpg done } ## 2. ## TODO: ffmpeg -f image2 -i $archive/$LASTDAY/$camfolders/img%04d.jpg -r 6 -s 720x576 $archive/$LASTDAY/$camfolders\_$LASTDAY.avi ## 3. rm -rf $camfolders done } fi exit 0 File work:
- The quality of video compression, to put it mildly, suffers terribly. I can not figure out the smart options ffmpeg. And perhaps that is not enough codecs. I ask those who came across - to prompt the appropriate list of keys.
An insider intruder, pretending to be a camera, can arrange a non-sour defeat to a respected site, if of course he finds out the password from FTP.It is necessary either to close somehow, or to teach the server to enter the web interface of the cameras and download the current image from them (the camera has a static address cam1 / snapshot.php for this, and authentication is based on .htaccess).Please advise, with the help of which commands and utilities, this can be solved.
UPD: the decision of this moment was suggested by Akint . A little later, add to the code.
Source: https://habr.com/ru/post/132315/
All Articles