Duqu: 0day + installer
In the previous post, we briefly told about a very sophisticated Trojan Dujan, stealing company confidential information and self-destructing after completion of work. For which we received 2 applications
1. find installation file
2. find zero day vulnerability
So, the concert on the requests:
')
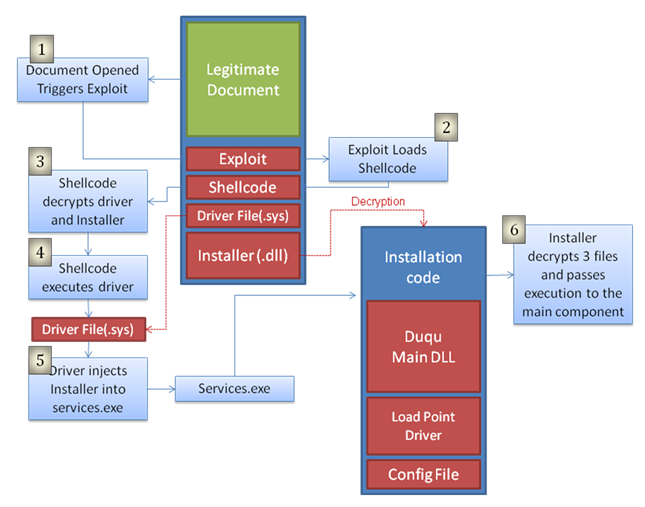
Together with CrySyS, we were able to detect and analyze the installation file of the Trojan, which has not yet been identified by anyone.
As it turned out, this file is a Microsoft Word document (.doc)! The infection of the system occurs through the exploitation of a previously unknown, and, accordingly, an open vulnerability in the Windows kernel, which allows the execution of malicious code. In the case of a file being launched, Duqu files are installed on the target computer. According to our data, Microsoft is already working to eliminate the detected vulnerability.
The document was configured so that the infection was possible only at a certain time, and was intended only for designated enterprises. The malicious program was set aside for the infection process for eight days in August of the current year. Note that this sample installation file at the time of publication was one of a kind, and it is possible that there are several more of its varieties.
As a result of infecting the target system, attackers are able to control the actions of their creation. An investigation conducted in one of the affected organizations showed that the trojan was controlled through an application layer network protocol (SMB), used to provide remote access to a computer. It is important to note that some of the infected machines did not have an Internet connection. However, the malware configuration files found on them were formed in such a way that communication with the remote control and command server (C & C) was carried out through some common C & C protocol, through which all infected computers “communicated”. Thus, with the help of other computers, which in this case were used as proxy servers, attackers could gain access to a secure zone.
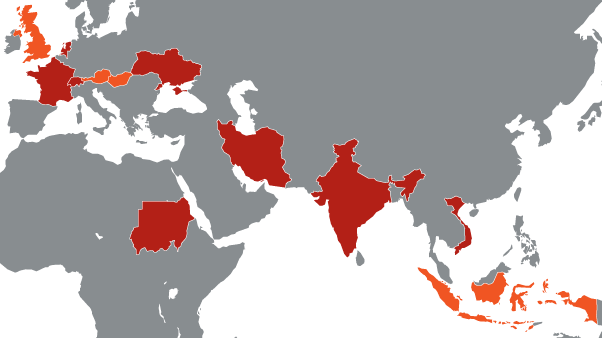
The threat managed to spread in several countries, despite the fact that the total number of companies that confirmed the existence of a threat is relatively small. However, the threat was seen in six organizations located in eight countries, such as France, the Netherlands, Switzerland, Ukraine, India, Iran, Sudan and Vietnam. It is important to note that this information was obtained through an Internet provider, and, therefore, their number may be different. Moreover, it is impossible to accurately identify the company by IP address.
Finally, in the course of this work, it became known that there was a different Duqu sample, different from the previously known ones, the control server of which was located in India. This instance of the C & C server is located in Belgium with the IP address '77 .241.93.160 '. It is currently disabled.
1. find installation file
2. find zero day vulnerability
So, the concert on the requests:

Duqu Infection Scheme
')
Together with CrySyS, we were able to detect and analyze the installation file of the Trojan, which has not yet been identified by anyone.
As it turned out, this file is a Microsoft Word document (.doc)! The infection of the system occurs through the exploitation of a previously unknown, and, accordingly, an open vulnerability in the Windows kernel, which allows the execution of malicious code. In the case of a file being launched, Duqu files are installed on the target computer. According to our data, Microsoft is already working to eliminate the detected vulnerability.
The document was configured so that the infection was possible only at a certain time, and was intended only for designated enterprises. The malicious program was set aside for the infection process for eight days in August of the current year. Note that this sample installation file at the time of publication was one of a kind, and it is possible that there are several more of its varieties.
As a result of infecting the target system, attackers are able to control the actions of their creation. An investigation conducted in one of the affected organizations showed that the trojan was controlled through an application layer network protocol (SMB), used to provide remote access to a computer. It is important to note that some of the infected machines did not have an Internet connection. However, the malware configuration files found on them were formed in such a way that communication with the remote control and command server (C & C) was carried out through some common C & C protocol, through which all infected computers “communicated”. Thus, with the help of other computers, which in this case were used as proxy servers, attackers could gain access to a secure zone.
The threat managed to spread in several countries, despite the fact that the total number of companies that confirmed the existence of a threat is relatively small. However, the threat was seen in six organizations located in eight countries, such as France, the Netherlands, Switzerland, Ukraine, India, Iran, Sudan and Vietnam. It is important to note that this information was obtained through an Internet provider, and, therefore, their number may be different. Moreover, it is impossible to accurately identify the company by IP address.

Red indicates countries where the infection is confirmed, orange indicates that the infection is likely but not confirmed
Finally, in the course of this work, it became known that there was a different Duqu sample, different from the previously known ones, the control server of which was located in India. This instance of the C & C server is located in Belgium with the IP address '77 .241.93.160 '. It is currently disabled.
Source: https://habr.com/ru/post/131813/
All Articles