HiJacking DLL in Qt Applications
In March 2011, I wrote about the HiJacking DLL in VirtualBox . Then the developers reported that the problem is not in their product, but in Qt , on which their products are based.
Finally, having found the time, I decided to check whether this was so. It turned out that way.
I have been checked:
And they were vulnerable.
')
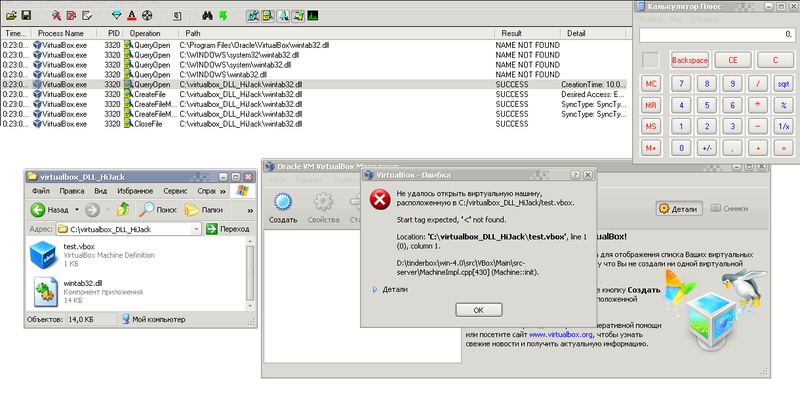
Video demonstration of vulnerability (video without sound):
However, Oracle VirtualBox version 4.1.2 was no longer vulnerable. Trying to find out from which Qt version the problem was solved, I began to study the Qt changelog , where I found the following entry for version 4.7.1 :
For those who use applications written in Qt, I recommend checking versions of libraries (Qt * .dll) that are in the same directory as the executable file of the application. If their version is <4.7.1, update them manually by downloading Qt Libraries .
The list of potentially vulnerable applications (some of them are already using the updated Qt).
UPD: Translation of the post into English
Related Links:
Finally, having found the time, I decided to check whether this was so. It turned out that way.
I have been checked:
And they were vulnerable.
')

Video demonstration of vulnerability (video without sound):
However, Oracle VirtualBox version 4.1.2 was no longer vulnerable. Trying to find out from which Qt version the problem was solved, I began to study the Qt changelog , where I found the following entry for version 4.7.1 :
QLibrary
* [QT-3825] System libraries are only loaded from the system directories.For those who use applications written in Qt, I recommend checking versions of libraries (Qt * .dll) that are in the same directory as the executable file of the application. If their version is <4.7.1, update them manually by downloading Qt Libraries .
The list of potentially vulnerable applications (some of them are already using the updated Qt).
UPD: Translation of the post into English
Related Links:
- Hijacking dll (search toolkit, operation via Metasploit)
- Profitable DLL Hijacking (thanks to elgrand )
- Microsoft Security Advisory (2269637)
Insecure Library Loading Could Allow Remote Code Execution (thanks ComodoHacker ) - Qt: Security announcement - Windows DLL preloading
- Published new registry key CWDIllegalInDllSearch, allowing you to manage the DLL search path algorithm
Source: https://habr.com/ru/post/131505/
All Articles