Duqu: Stuxnet's story continues ...
Over the past few days, a lot of attention has been focused on the Win32 / Duqu malware. The fact is that by the characteristics of its implementation Win32 / Duqu is similar to the well-known Win32 / Stuxnet. Last year, we conducted a rather detailed analysis of the Win32 / Stuxnet worm, which resulted in the Stuxnet Under the Microscope research report. And now we are exploring Win32 / Duqu, having studied the modules and mechanisms for their operation, it can be argued that this malware is based on the same source codes or libraries as Win32 / Stuxnet itself. Perhaps this is not even just the source code, but a framework for developing malware or cyber weapons. The recovered Duqu driver code reminded us very much of what we already saw in Stuxnet. These drivers are almost identical to what we saw last fall.
From the moment we began to investigate Win32 / Duqu, we were interested in the question of how to identify the exact date of infection of a computer with this malware. Such information is primarily useful for conducting forensic examination and restoring the picture of what happened. We had an idea that if Duqu stores information about the moment of its self-removal, then there must be information with which this counting begins. We managed to find an interesting thing, at the moment we have several sets of samples from various infected machines. It turned out that during the infection process, the so-called main.dll is formed (the main component in the resources section of which other components are stored), in which the exact date of the infection is stored in UTC-format. Below we provide the decompiled code that performs date verification:
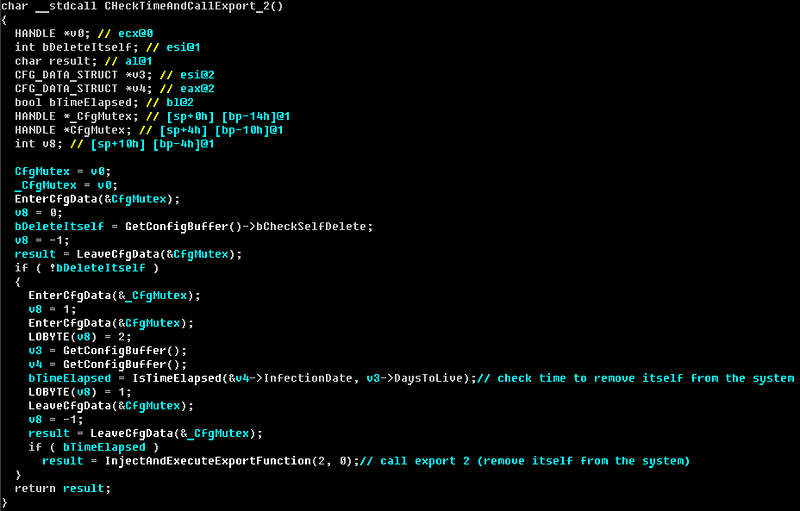
Based on these data in the process of conducting a forensic examination of an infected machine, it is possible to establish the exact date and time of its infection.
')
The Duqu: the precursor to the next Stuxnet report lists Duqu's lifetime on an infected machine for 36 days, after which it is automatically deleted. In order to find out the date of infection, you first need to decrypt the configuration files using a non-clever artisanal cryptoalgorithm:

After examining several sets of samples, we found that this date may change and most likely is set during the infection process based on the dropper configuration data. We have one set of samples should have been removed in the same way after 36 days, but the second only after 30.
The configuration file of infection 11/08/2011 at 7:50:01 and deletion after 36 days:
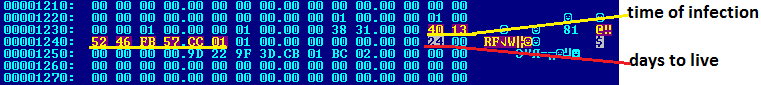
The configuration file of infection on 18/08/2011 at 7:29:07 and deletion after 30 days:

Duqu still contains many interesting technical details, and we continue our research.
From the moment we began to investigate Win32 / Duqu, we were interested in the question of how to identify the exact date of infection of a computer with this malware. Such information is primarily useful for conducting forensic examination and restoring the picture of what happened. We had an idea that if Duqu stores information about the moment of its self-removal, then there must be information with which this counting begins. We managed to find an interesting thing, at the moment we have several sets of samples from various infected machines. It turned out that during the infection process, the so-called main.dll is formed (the main component in the resources section of which other components are stored), in which the exact date of the infection is stored in UTC-format. Below we provide the decompiled code that performs date verification:

Based on these data in the process of conducting a forensic examination of an infected machine, it is possible to establish the exact date and time of its infection.
')
The Duqu: the precursor to the next Stuxnet report lists Duqu's lifetime on an infected machine for 36 days, after which it is automatically deleted. In order to find out the date of infection, you first need to decrypt the configuration files using a non-clever artisanal cryptoalgorithm:

After examining several sets of samples, we found that this date may change and most likely is set during the infection process based on the dropper configuration data. We have one set of samples should have been removed in the same way after 36 days, but the second only after 30.
The configuration file of infection 11/08/2011 at 7:50:01 and deletion after 36 days:

The configuration file of infection on 18/08/2011 at 7:29:07 and deletion after 30 days:

Duqu still contains many interesting technical details, and we continue our research.
Source: https://habr.com/ru/post/131304/
All Articles