Whitelisting: about technology, its market prospects and utility for the company
Today we want to tell you about the technology that, in our opinion, can be on par with our best technologies in the field of protection against malicious software and centralized protection management. This is a protection technology based on dynamic lists of trusted software (Dynamic Whitelist, DW). More precisely, not just technology, but the whole concept that we built on its basis. The conversation will lead Nikolai Grebennikov, Director of Research and Development "Kaspersky Lab."
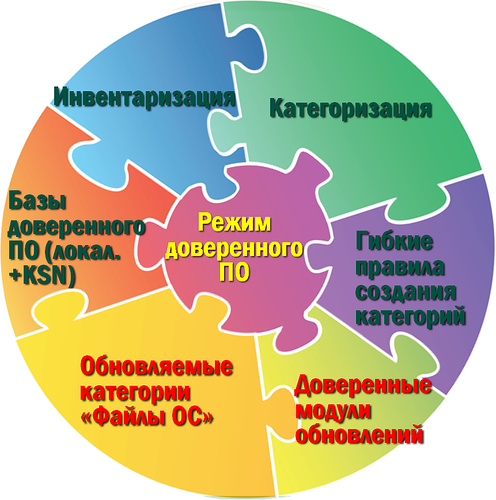
Why do we need a concept? - because it’s not just a new security technology like proactive defense or an emulator. DW can bring enormous benefits, but requires a rethinking of approaches to the protection and adaptation of the process of work of administrators in the organization . However, I am sure that the result is worth it. After all, DW allows not only to protect against malicious programs, but also can allow an administrator to ensure the most efficient use of IT resources in an organization - by limiting the use of non-production software. And this is an excellent base for organizing effective accounting of installed software and licenses for it, which is a serious item of IT expenses of any organization.
But back to the defense. The first ideas of protection based on the lists of trusted (or "white" - hence the English name "whitelisting / whitelist") applications appeared in the early 2000s; we ourselves even had a license agreement with Bit9, one of the players in this market, a few years ago. I remember the articles and panels at the RSA conference, which were called “Antivirus is dead” - where I had to prove that nobody actually died and whitelisting was not a panacea, but just another useful new technology .
But the reality is that there is no serious “separate market” whitelisting , organizations with great reluctance and problems are implementing existing solutions. I think the reason is that the solutions are simply not easy to use ! What is the basic characteristic of any software? - its variability. And the existing solutions are too “hard” to allow their operation without serious constant attention from the administrator. That is why we added technologies that make it easier to work with white lists in dynamics: the word Dynamic in the name DW is not just for beauty.
')
Two technologies add dynamism to our solution: an updated category of OS files (in English beautifully called Golden images) and a procedure for secure updates by trusted update modules (trusted updaters).
The first provides the absence of the administrator’s headache that the inclusion of DW-based protection will make it impossible to start computers due to the blocking of an important application at the start of the operating system. Through our whitelisting analysts, we provide and constantly maintain lists of key files for 18 localizations of all major editions of the Windows operating system .
At the same time, these lists contain not only Microsoft software, but also other important files, such as device driver update modules.
The second technology allows you to update the software already installed on your computer in a safe manner. In this case, the main difficulty lies not in supporting the list of existing update modules of known software, but in the update procedure itself. The office of the architects conducted a study that allowed the implementation of a secure product update procedure that takes into account the complex chains of program calls that are performed. For example, updating the well-known Adobe Reader requires calling five applications in the update chain . It is safe to say that this technology is unique at the current time.
Variability is a common characteristic of trusted and malicious software. The difference is the enormous size of the knowledge base about “the whole variety of existing software”: currently the number of records in our “white database” exceeds 230 million with a replenishment rate of about 1 million objects per day , compared with 40 million and 70 thousand new malicious objects.
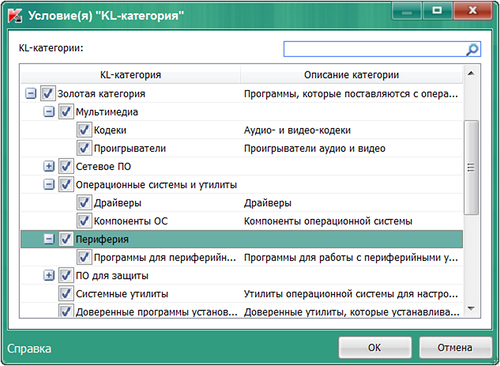
For the convenience of the administrator in Endpoint 8, we divide all software into categories, which allows for flexible management of entire software categories. In addition, support from the LC allows the administrator not to track the appearance of new software versions manually. These categories can be used to create permissive and prohibitive rules for using software in an organization.
In general, we have tried to approach the issue of creating rules as flexibly as possible : in addition to the categories supplied by the LC, the administrator can create rules by manufacturer, name, version, checksum and paths to application files. The latter is especially relevant for organizations that have a centralized distribution of software distributions organized by the administrator (and our Moscow office is no exception :).
We paid special attention to the issue of transition from the state “everything that is not harmful is allowed” to the state “everything is forbidden that is not allowed by the rules” (default deny, DD). One-time transition is fraught with a shaft of requests to the administrator from irritated users, who will stop running their applications.
Therefore, we recommend creating the initial database of software permitted in this organization, including it in the analysis mode (special state “test” of launch rules) for 3-5 days, then analyze the resulting list of potential prohibitions and add rules for the necessary applications / categories. As a result, the subsequent inclusion of the DD mode will not lead to a flurry of requests. At the same time, Endpoint 8 allows the user to quickly send a request for the permission of a blocked application, and the administrator in the Security Center 9 console can quickly process single requests, adding, if necessary , “two-click” rules directly from the list of user complaints .
But the implementation of the concept of DW - this is only half the battle. Despite Gartner’s claim that such an approach can greatly improve user security, this approach has not received serious public acceptance. There is not a single test similar to the av-test, av-comparatives and VB tests in the area of whitelisting. That is why a key success factor for us is also to obtain public recognition of this technology on the market, for which concerted efforts are needed in several areas: convincing key market analysts, obtaining independent public test results, training our sales departments and partners of LC.
In the spring of this year, our company initiated the first public tests of whitelisting solutions . After talking with 10 test organizations, we came to an agreement with westcoast labs to conduct tests of the quality of the base and the quality of the final solution as part of Endpoint 8 and Security Center 9. We actively participated in the discussion of the testing methodology and principles for building an application database for testing. It is important to note that this happened as openly as possible and accessible to all interested vendors. At the moment, testing comes to an end - official results are expected in early November. We believe that our solution will be able to win product tests in comparison with competing products from Symantec, Sophos, McAfee, TrendMicro. In the base quality tests, our solution is a notorious winner, since Bit9, Lumension and SignaCert consistently refused to participate in the tests, obviously, without being confident in their abilities.
Summarizing, I consider the implementation of the concept of dynamic lists of trusted software in the new product line of the company as a landmark moment - the moment of the emergence of a new unique technological advantage of Kaspersky Lab . We will not be the first in virtualization, clouds or mobile technologies. But our whitelisting is the best in the world, while it brings direct benefits to organizations and is the basis for merging security management with IT management in the organization as a whole. This is a unique competitive advantage along with antivirus technology and manageability. Each of them was not so easy to achieve, so I want every R & D employee to understand them, and our marketing and sales departments use it to conquer new users. Thanks to everyone who made this possible - Andrei Efremov, Andrei Guzhov, Andrei Solodovnikov, Kirill Kruglov, Natalia Glavatskaya, Andrei Kulag, Vladimir Zapolyansky and all those who participated in the design, development and testing of the described technologies in the framework of E8 and SC9.

Nikolay Grebennikov,
Director of Research and Development, Kaspersky Lab

Why do we need a concept? - because it’s not just a new security technology like proactive defense or an emulator. DW can bring enormous benefits, but requires a rethinking of approaches to the protection and adaptation of the process of work of administrators in the organization . However, I am sure that the result is worth it. After all, DW allows not only to protect against malicious programs, but also can allow an administrator to ensure the most efficient use of IT resources in an organization - by limiting the use of non-production software. And this is an excellent base for organizing effective accounting of installed software and licenses for it, which is a serious item of IT expenses of any organization.
But back to the defense. The first ideas of protection based on the lists of trusted (or "white" - hence the English name "whitelisting / whitelist") applications appeared in the early 2000s; we ourselves even had a license agreement with Bit9, one of the players in this market, a few years ago. I remember the articles and panels at the RSA conference, which were called “Antivirus is dead” - where I had to prove that nobody actually died and whitelisting was not a panacea, but just another useful new technology .
But the reality is that there is no serious “separate market” whitelisting , organizations with great reluctance and problems are implementing existing solutions. I think the reason is that the solutions are simply not easy to use ! What is the basic characteristic of any software? - its variability. And the existing solutions are too “hard” to allow their operation without serious constant attention from the administrator. That is why we added technologies that make it easier to work with white lists in dynamics: the word Dynamic in the name DW is not just for beauty.
')
Two technologies add dynamism to our solution: an updated category of OS files (in English beautifully called Golden images) and a procedure for secure updates by trusted update modules (trusted updaters).
The first provides the absence of the administrator’s headache that the inclusion of DW-based protection will make it impossible to start computers due to the blocking of an important application at the start of the operating system. Through our whitelisting analysts, we provide and constantly maintain lists of key files for 18 localizations of all major editions of the Windows operating system .

At the same time, these lists contain not only Microsoft software, but also other important files, such as device driver update modules.
The second technology allows you to update the software already installed on your computer in a safe manner. In this case, the main difficulty lies not in supporting the list of existing update modules of known software, but in the update procedure itself. The office of the architects conducted a study that allowed the implementation of a secure product update procedure that takes into account the complex chains of program calls that are performed. For example, updating the well-known Adobe Reader requires calling five applications in the update chain . It is safe to say that this technology is unique at the current time.
Variability is a common characteristic of trusted and malicious software. The difference is the enormous size of the knowledge base about “the whole variety of existing software”: currently the number of records in our “white database” exceeds 230 million with a replenishment rate of about 1 million objects per day , compared with 40 million and 70 thousand new malicious objects.
For the convenience of the administrator in Endpoint 8, we divide all software into categories, which allows for flexible management of entire software categories. In addition, support from the LC allows the administrator not to track the appearance of new software versions manually. These categories can be used to create permissive and prohibitive rules for using software in an organization.
In general, we have tried to approach the issue of creating rules as flexibly as possible : in addition to the categories supplied by the LC, the administrator can create rules by manufacturer, name, version, checksum and paths to application files. The latter is especially relevant for organizations that have a centralized distribution of software distributions organized by the administrator (and our Moscow office is no exception :).
We paid special attention to the issue of transition from the state “everything that is not harmful is allowed” to the state “everything is forbidden that is not allowed by the rules” (default deny, DD). One-time transition is fraught with a shaft of requests to the administrator from irritated users, who will stop running their applications.
Therefore, we recommend creating the initial database of software permitted in this organization, including it in the analysis mode (special state “test” of launch rules) for 3-5 days, then analyze the resulting list of potential prohibitions and add rules for the necessary applications / categories. As a result, the subsequent inclusion of the DD mode will not lead to a flurry of requests. At the same time, Endpoint 8 allows the user to quickly send a request for the permission of a blocked application, and the administrator in the Security Center 9 console can quickly process single requests, adding, if necessary , “two-click” rules directly from the list of user complaints .
But the implementation of the concept of DW - this is only half the battle. Despite Gartner’s claim that such an approach can greatly improve user security, this approach has not received serious public acceptance. There is not a single test similar to the av-test, av-comparatives and VB tests in the area of whitelisting. That is why a key success factor for us is also to obtain public recognition of this technology on the market, for which concerted efforts are needed in several areas: convincing key market analysts, obtaining independent public test results, training our sales departments and partners of LC.
In the spring of this year, our company initiated the first public tests of whitelisting solutions . After talking with 10 test organizations, we came to an agreement with westcoast labs to conduct tests of the quality of the base and the quality of the final solution as part of Endpoint 8 and Security Center 9. We actively participated in the discussion of the testing methodology and principles for building an application database for testing. It is important to note that this happened as openly as possible and accessible to all interested vendors. At the moment, testing comes to an end - official results are expected in early November. We believe that our solution will be able to win product tests in comparison with competing products from Symantec, Sophos, McAfee, TrendMicro. In the base quality tests, our solution is a notorious winner, since Bit9, Lumension and SignaCert consistently refused to participate in the tests, obviously, without being confident in their abilities.
Summarizing, I consider the implementation of the concept of dynamic lists of trusted software in the new product line of the company as a landmark moment - the moment of the emergence of a new unique technological advantage of Kaspersky Lab . We will not be the first in virtualization, clouds or mobile technologies. But our whitelisting is the best in the world, while it brings direct benefits to organizations and is the basis for merging security management with IT management in the organization as a whole. This is a unique competitive advantage along with antivirus technology and manageability. Each of them was not so easy to achieve, so I want every R & D employee to understand them, and our marketing and sales departments use it to conquer new users. Thanks to everyone who made this possible - Andrei Efremov, Andrei Guzhov, Andrei Solodovnikov, Kirill Kruglov, Natalia Glavatskaya, Andrei Kulag, Vladimir Zapolyansky and all those who participated in the design, development and testing of the described technologies in the framework of E8 and SC9.

Nikolay Grebennikov,
Director of Research and Development, Kaspersky Lab
Source: https://habr.com/ru/post/130827/
All Articles