The Duqu worm, a relative of Stuxnet, appeared on the Web.

I remember that some time ago news resources were full of headlines about the most dangerous Stuxnet worm, which hit specialized software of specific NPP equipment (remember, controllers from Siemens fell under the distribution). So, now experts from Symantec have discovered malware related to Stuxnet, already known as Duqu. According to experts, this worm will not use Stuxnet tactics, choosing several other objects for destruction. Duqu is designed to steal all sorts of information from industrial facilities. A new worm was discovered only this week, and experts have just started working with this software.
The worm received such a strange name, Duqu, thanks to the extension of the files it creates, ~ DQ. Here you can find a more or less complete analysis (first stages) of the worm, conducted by Symantec experts. For the first time this software was discovered in computer systems of European enterprises. The worm was detected on October 14, so the experts do not yet have much data to work with.
')
The information that the worm is looking for is primarily concerned with documents describing the company's IT infrastructure. Probably, these data are needed by attackers to carry out subsequent attacks in order to establish control over various types of industrial systems. As mentioned above, Duqu is related to the Stuxnet worm, and contains parts of the code that are identical to the “atomic” relative. Experts make the assumption that the same team worked out with Duqu, whose representatives developed Stuxnet.
Additional analysis of the worm was conducted by representatives of McAfee, who reported that Duqu also “works” in Africa and in the Middle East, and not only in Europe. As soon as the worm enters the system, a keylogger is installed immediately, recording all user actions, and additional system information is also searched. The worm can copy the list of processes running in the system, information about the user's account, as well as information about the domain. It also makes screenshots, records network information, and also “examines” files on all available drives, including removable and networked ones.
According to Symantec, the worm works on the system for 36 days from the launch, and then self-destructs.
Here is a comparison of Stuxnet and the new worm conducted by Symantec.
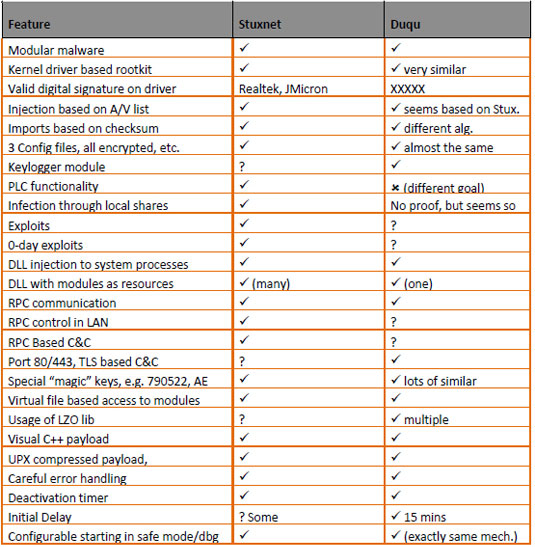
Via techtarget
Source: https://habr.com/ru/post/130728/
All Articles