Interception PPPoE session
The video shows a practical way to hijack a PPPoE session using a cable tie. In this case, no login or password is intercepted and the type of authorization used (CHAP / PAP) does not matter.
Most ethernet providers, unfortunately, do not use encryption of the entire session, limited only by encryption of the authorization step. This allows you to introduce yourself as a legitimate client, intercepting the details of an existing connection.
')
Theory
PPPoE (Point-to-Point Protocol over Ethernet) is a data link layer protocol, one level below ip, so no IP address is required to establish a connection, addressing occurs over MAC.
Conventionally, the connection process looks like this:
A client searching for a pppoe server sends a broadcast request
The destination MAC address FF: FF: FF: FF: FF: FF.
The server responds to the client and authorizes (for example, CHAP Challenge)
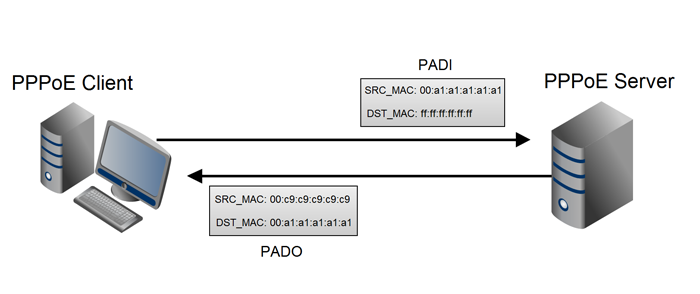
In the established connection, the server identifies the client by its MAC address and Session ID. IP packets are encapsulated inside PPPoE frames. In an unencrypted connection, the entire contents of the packets can be viewed:

Accordingly, having learned the connection details, you can intercept the session:
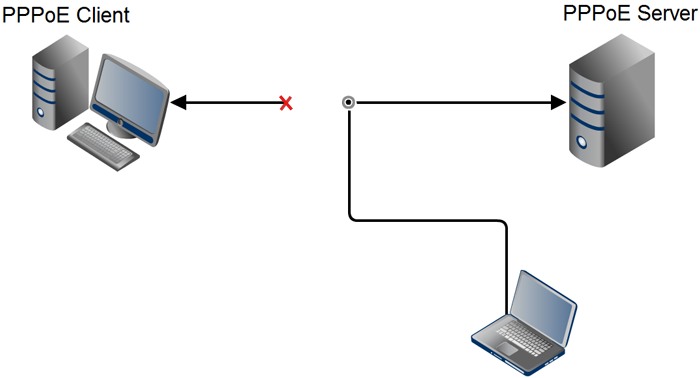
To protect against such attacks, there is the CHAP Rechallenge option when the server re-identifies the client at a given time interval. None of the tested providers used this option.
The video uses a virtual machine running in bridge mode with an ethernet card of the host system.
During cable switching it is important to get between the LCP-echo packages.
PPPoE server www.roaringpenguin.com/products/pppoe recompiled with the option
#define DEFAULT_MAX_SESSIONS 64000Thanks to kekekeks for help in picking the source of the rp-pppoe server.
Source: https://habr.com/ru/post/130710/
All Articles