How botnets are closed
Recently, much has been said about botnets in runet. This is mainly due to DDoS attacks on known and visited resources. Below we will discuss the experience of large companies in the field of combating this scourge.

A botnet is a collection of systems infected with malicious code and managed centrally. Moreover, it is arranged in such a way that the destruction or shutdown of a sufficiently large number of nodes should not affect its performance in general. Botnets can be used for such purposes as spamming, phishing, DDoS, attacks on other systems, infecting new PCs and turning them into botnet nodes. It is worth noting that at the moment the cybercrime industry is quite segmented by specialization and focus of crimes. That means everyone does their own thing. As a result, the botnet creator sells botnet resources or services to other attackers specializing in various types of crimes (you can look at the illustrations for a typical business structure). It is worth noting that the management interface of the botnet is quite simple. A person with even very low qualifications can cope with it. In accordance with cloud trends, Malware as a Service has recently appeared. If someone cannot create and distribute their malicious code, there will always be a provider who can do it for a certain amount of money. However, to create a botnet today is also not God knows what a difficult task. There are many ready-made botnet kits on the market, such as Zbot (Zeus), Spyeye, Mariposa, Black Energy, ButterFly, Reptile. This means that modern bot owners may not even have any special technological skills. However, if we talk about large botnets, then their creators are, of course, capable, talented people, to fight with which it is quite difficult. As part of this material, I would like to talk about the practices that are used by large companies to combat cybercrime and, in particular, botnets. This, in particular, will focus on the activity of Microsoft, in which I work.

Perhaps this will make someone smile, but Microsoft has been working hard over the past few years to improve the security of products and services. Methodologies for developing a secure SDL code have emerged and began to be applied, which has a key impact on the number of recent vulnerabilities (especially those that can be exploited). But today it’s not about preventive measures that can prevent future threats, but about dealing with problems that are relevant today. A large number of infected machines running under the Windows operating system - just such a problem.
Inside the company was created a number of divisions to combat cybercrime. The latter have different names - Digital Crime Unit, Microsoft Security Response Center, Trust worth Computing, - but each one’s tasks somehow overlap with the problem of cybercrime. Together with law enforcement agencies and research organizations, Microsoft began operations to destroy the largest botnets. Sounds loud? Perhaps, but during the year botnets were destroyed such as:
In order to understand the typical methods of destroying a botnet, it is necessary to understand its architecture and weak points. Most often, one or several command (often central) servers, called Command & Control, or C & C, are used to control the botnet. They interact with the botnet end nodes using different protocols. Most often IRC is used as a control protocol. However, the use of P2P protocols as a more sustainable, albeit technologically complex alternative has recently increased dramatically. Recently, the use of file-sharing networks for managing a botnet and the transfer of control commands in the body of photos published on Facebook has become an interesting exotic. Anyway, several specific actions can be taken to combat a botnet:
')
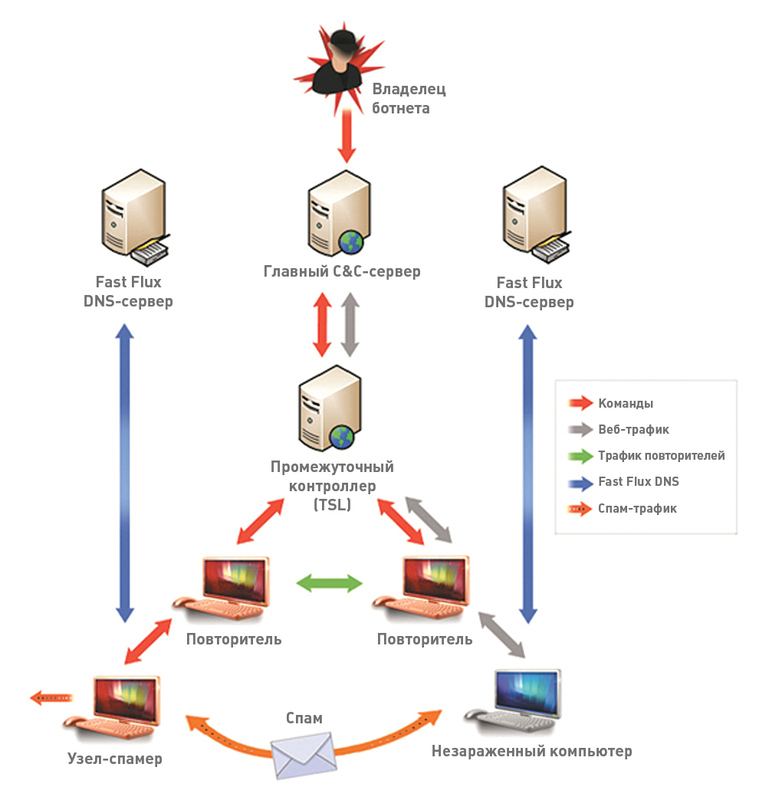
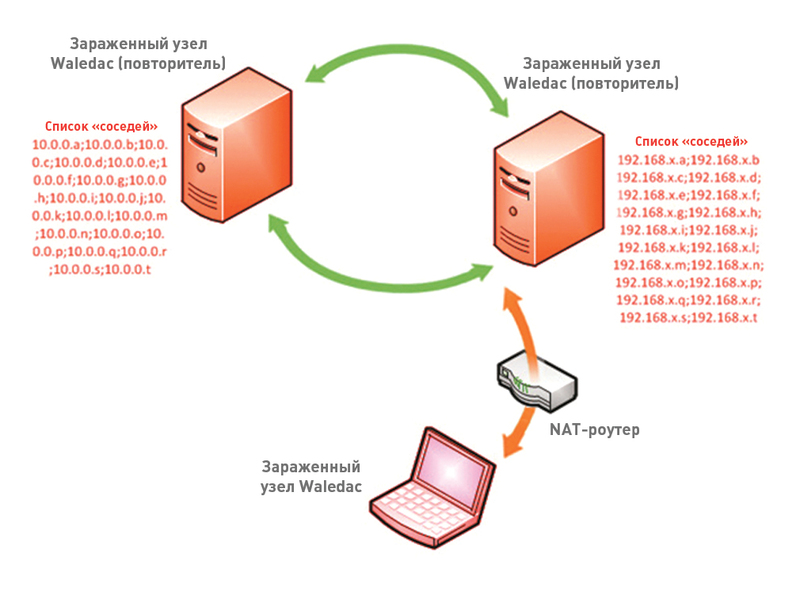
The challenge of dealing with Waledac was the botnet’s decentralized pattern of operation. For his work, as many as 277 domain names have been reserved. This means that it was necessary to capture servers at the same time in several data centers, from different hosting providers. In addition, the P2P mechanism was successfully used to control the botnet. If you look at the botnet scheme, the layering of the control servers immediately catches the eye. In the process of infecting the system with Waledac, the malicious code determines what role the new node will play. It becomes either a simple spamming node, if it is behind NAT and does not accept incoming connections on port 80, or a node that repeats (retransmits) commands from the center, that is, a kind of repeater. Repeaters are used to manage the botnet. In addition to sending control commands to spammers, each repeater also supports a list of “neighbors” consisting of 100 nodes that also act as a repeater, to which it can connect using the P2P protocol. Over time, any repeater will register its domain name with fast flux DNS. This is done in order to allow spammers nodes to contact themselves if the closest to them repeater suddenly fails and becomes unavailable. Thus, botnet nodes can always find the nearest relay node and receive commands and executable code updates from it. The botnet is designed so that over time the role of the nodes may change. If a system used as a repeater, for example, enters the corporate network and loses the ability to accept connections to port 80, it automatically receives the role of spammer. At the same time, it is not so easy to analyze the topology of a botnet, because another task of the repeater is to counteract the research of the botnet topology. It serves as a kind of proxy and does not allow spammer nodes to know anything about C & C control nodes.
After analyzing the botnet architecture, we worked out a plan for attacking a botnet with the following specific steps:
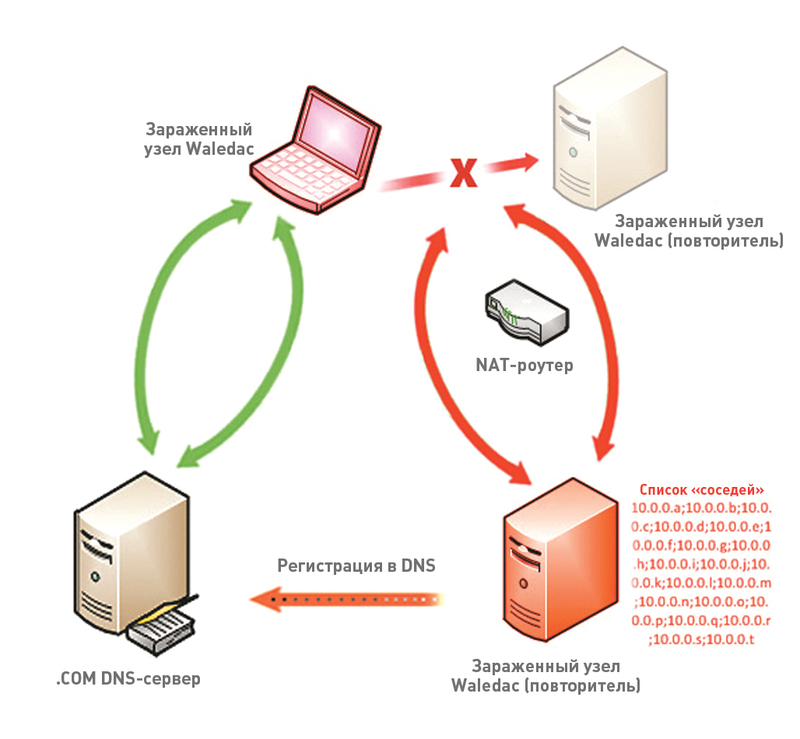
If the P2P mechanism fails, the botnet nodes start searching for each other using the fast flux DNS mechanism. Therefore, it was necessary to destroy this method of control so that the attacker could not regain control of the botnet. This is an interesting point, because here we used a legal mechanism. A typical procedure for revoking a DNS name through ICANN using a procedure with the scary name “Uniform Domain-Name Dispute-Resolution Policy” can take quite a long time. This would allow attackers to have time to realize that they are attacking and take steps to register new DNS names, to which control of the botnet will later be transferred. Therefore, instead of the standard ICANN procedure, we used the “TRO (temporary restraining order)” procedure - the ability to temporarily suspend domains for 28 days by decision of the US federal court. At this stage, another complication was that part of the DNS names were registered in China.
In order for attackers to compete with Microsoft in court, if they have a desire to declare their rights to the botnet, a statement of claim was published on the site. Also in national newspapers on the territory of the countries from which the suspects controlled the botnet, notices of summons were published. As expected, no one dared to appear in court and declare their rights to the botnet. Thus, Microsoft won the trial in the United States and China. More information about the legal intricacies and peripetia of the struggle for a botnet can be found in a special section of the Microsoft site .
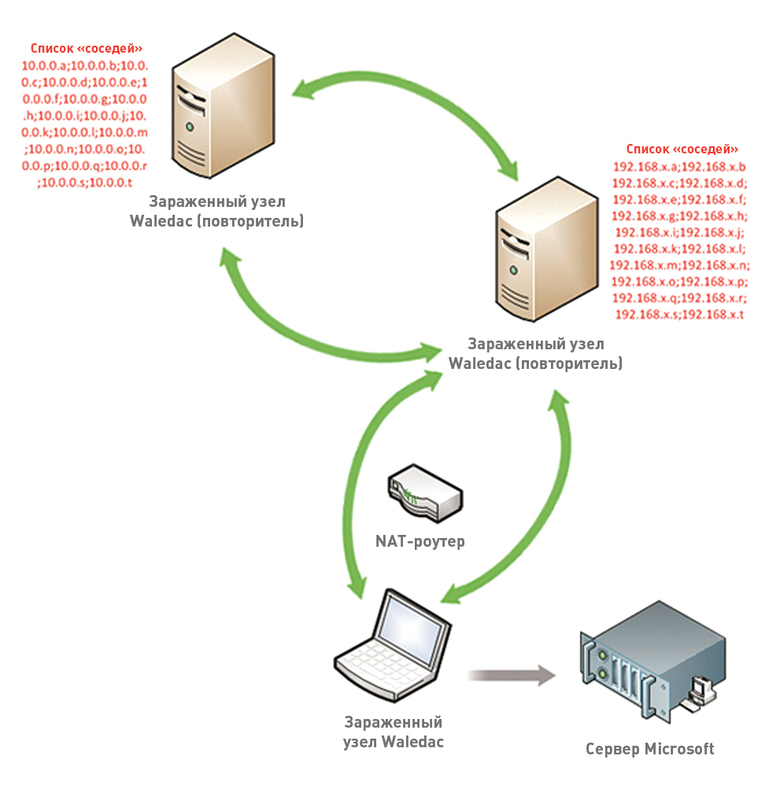
As a result of these legal actions, DNS rights were transferred to Microsoft. Currently, DNS names are connected to Microsoft servers. If an infected node is connected to these servers from a botnet, a command is issued to it, ordering the removal of the malicious code of the Waledac bot.
In this way, we hope to gradually clean the Internet from the last remnants of the Waldac botnet. To prevent intruders from creating botnets in the future, Microsoft continues to investigate and collect evidence. To this end, we offered a reward of $ 250,000 to those who would provide information that would contribute to the arrest of the criminal group behind Rustock . In our experience, such an approach might work. In conclusion, I would like to say that Microsoft intends to actively fight cybercrime in the future, pursuing the intruders with all means available to it.

Journal Hacker, October (10) 153
Andrey Beshkov .
Subscribe to "Hacker"

What is a botnet?
A botnet is a collection of systems infected with malicious code and managed centrally. Moreover, it is arranged in such a way that the destruction or shutdown of a sufficiently large number of nodes should not affect its performance in general. Botnets can be used for such purposes as spamming, phishing, DDoS, attacks on other systems, infecting new PCs and turning them into botnet nodes. It is worth noting that at the moment the cybercrime industry is quite segmented by specialization and focus of crimes. That means everyone does their own thing. As a result, the botnet creator sells botnet resources or services to other attackers specializing in various types of crimes (you can look at the illustrations for a typical business structure). It is worth noting that the management interface of the botnet is quite simple. A person with even very low qualifications can cope with it. In accordance with cloud trends, Malware as a Service has recently appeared. If someone cannot create and distribute their malicious code, there will always be a provider who can do it for a certain amount of money. However, to create a botnet today is also not God knows what a difficult task. There are many ready-made botnet kits on the market, such as Zbot (Zeus), Spyeye, Mariposa, Black Energy, ButterFly, Reptile. This means that modern bot owners may not even have any special technological skills. However, if we talk about large botnets, then their creators are, of course, capable, talented people, to fight with which it is quite difficult. As part of this material, I would like to talk about the practices that are used by large companies to combat cybercrime and, in particular, botnets. This, in particular, will focus on the activity of Microsoft, in which I work.

Standard botnet management approach
Microsoft vs. Botnet
Perhaps this will make someone smile, but Microsoft has been working hard over the past few years to improve the security of products and services. Methodologies for developing a secure SDL code have emerged and began to be applied, which has a key impact on the number of recent vulnerabilities (especially those that can be exploited). But today it’s not about preventive measures that can prevent future threats, but about dealing with problems that are relevant today. A large number of infected machines running under the Windows operating system - just such a problem.
Inside the company was created a number of divisions to combat cybercrime. The latter have different names - Digital Crime Unit, Microsoft Security Response Center, Trust worth Computing, - but each one’s tasks somehow overlap with the problem of cybercrime. Together with law enforcement agencies and research organizations, Microsoft began operations to destroy the largest botnets. Sounds loud? Perhaps, but during the year botnets were destroyed such as:
- Rustock, which sent 80% of world spam.
- Coreflood, which served as a tool for crimes that brought more than $ 100 million in damages.
- Waledac, whose bots sent 1.5 billion spam messages daily.
Fighting botnets: common practices
In order to understand the typical methods of destroying a botnet, it is necessary to understand its architecture and weak points. Most often, one or several command (often central) servers, called Command & Control, or C & C, are used to control the botnet. They interact with the botnet end nodes using different protocols. Most often IRC is used as a control protocol. However, the use of P2P protocols as a more sustainable, albeit technologically complex alternative has recently increased dramatically. Recently, the use of file-sharing networks for managing a botnet and the transfer of control commands in the body of photos published on Facebook has become an interesting exotic. Anyway, several specific actions can be taken to combat a botnet:
- Capture or disable C & C nodes.
- DDoS on C & C nodes.
- Complaints to a provider where C & C nodes are hosted.
- Capture DNS names used by C & C.
- Block IP addresses.
- Arrest botnet owner.
- Legal action

Waledac multi-layer management architecture
')
Waledac: device
The challenge of dealing with Waledac was the botnet’s decentralized pattern of operation. For his work, as many as 277 domain names have been reserved. This means that it was necessary to capture servers at the same time in several data centers, from different hosting providers. In addition, the P2P mechanism was successfully used to control the botnet. If you look at the botnet scheme, the layering of the control servers immediately catches the eye. In the process of infecting the system with Waledac, the malicious code determines what role the new node will play. It becomes either a simple spamming node, if it is behind NAT and does not accept incoming connections on port 80, or a node that repeats (retransmits) commands from the center, that is, a kind of repeater. Repeaters are used to manage the botnet. In addition to sending control commands to spammers, each repeater also supports a list of “neighbors” consisting of 100 nodes that also act as a repeater, to which it can connect using the P2P protocol. Over time, any repeater will register its domain name with fast flux DNS. This is done in order to allow spammers nodes to contact themselves if the closest to them repeater suddenly fails and becomes unavailable. Thus, botnet nodes can always find the nearest relay node and receive commands and executable code updates from it. The botnet is designed so that over time the role of the nodes may change. If a system used as a repeater, for example, enters the corporate network and loses the ability to accept connections to port 80, it automatically receives the role of spammer. At the same time, it is not so easy to analyze the topology of a botnet, because another task of the repeater is to counteract the research of the botnet topology. It serves as a kind of proxy and does not allow spammer nodes to know anything about C & C control nodes.

Each repeater maintains a neighbor list.
Waledac: destruction
After analyzing the botnet architecture, we worked out a plan for attacking a botnet with the following specific steps:
- Violation of peer-to-peer control exchange mechanisms.
- Violation of the exchange of DNS / HTTP-commands.
- Violation of the two upper layers of C & C-servers.
If the P2P mechanism fails, the botnet nodes start searching for each other using the fast flux DNS mechanism. Therefore, it was necessary to destroy this method of control so that the attacker could not regain control of the botnet. This is an interesting point, because here we used a legal mechanism. A typical procedure for revoking a DNS name through ICANN using a procedure with the scary name “Uniform Domain-Name Dispute-Resolution Policy” can take quite a long time. This would allow attackers to have time to realize that they are attacking and take steps to register new DNS names, to which control of the botnet will later be transferred. Therefore, instead of the standard ICANN procedure, we used the “TRO (temporary restraining order)” procedure - the ability to temporarily suspend domains for 28 days by decision of the US federal court. At this stage, another complication was that part of the DNS names were registered in China.
In order for attackers to compete with Microsoft in court, if they have a desire to declare their rights to the botnet, a statement of claim was published on the site. Also in national newspapers on the territory of the countries from which the suspects controlled the botnet, notices of summons were published. As expected, no one dared to appear in court and declare their rights to the botnet. Thus, Microsoft won the trial in the United States and China. More information about the legal intricacies and peripetia of the struggle for a botnet can be found in a special section of the Microsoft site .
As a result of these legal actions, DNS rights were transferred to Microsoft. Currently, DNS names are connected to Microsoft servers. If an infected node is connected to these servers from a botnet, a command is issued to it, ordering the removal of the malicious code of the Waledac bot.

Domain Name Registration

Connecting Microsoft servers to Waledac
Conclusion
In this way, we hope to gradually clean the Internet from the last remnants of the Waldac botnet. To prevent intruders from creating botnets in the future, Microsoft continues to investigate and collect evidence. To this end, we offered a reward of $ 250,000 to those who would provide information that would contribute to the arrest of the criminal group behind Rustock . In our experience, such an approach might work. In conclusion, I would like to say that Microsoft intends to actively fight cybercrime in the future, pursuing the intruders with all means available to it.
Not like everyone else
It is rash to assume that botnets consist only of Windows machines. There are botnets on Linux / Unix - Psyb0t, Chuck Norris, with hundreds of thousands of devices. Basically, these botnets are created from home routers, switches and low-end NAS. Destroying such a botnet is extremely difficult, as the home user in most cases does not have Linux knowledge and skills to update the device firmware. The device manufacturer is interested in the rapid obsolescence of the device and often not only does not intend to eliminate the shortcomings, but also has no mechanisms for centralized updating of its products. According to a study from 2009, on the Internet at any time you can find several million home devices with outdated firmware and default passwords.
Journal Hacker, October (10) 153
Andrey Beshkov .
Subscribe to "Hacker"
Source: https://habr.com/ru/post/130680/
All Articles