Engineer's Philosophy or Fighting Computer Viruses
The gift of invention affected many people. And the "cocktail" inventiveness + talent + education in the person of one person, in general, can shift human activity to a completely new level. And if this person still has leadership qualities and charisma ... Damn, something was unrealized.
In short, for the engineer-inventor from a philosophical point of view there are only two ways:
Programmers are also inventors, possessing certain knowledge, as well as talent, they can single-handedly move the information sphere of humankind to a qualitatively new level. There is no need to go far for examples. Only one person, the well-known Mark Zuckerberg, changed the way people communicate on computer networks, creating a solution that we know as Facebook . His success spawned many clones, including in the Russian segment of the Internet.
')
For myself, I chose a constructive path of development. My crossroads was, in my opinion, in the second year. Before that, I was engaged in all sorts of hacks, I read Hacker magazine. At the university, in computer labs, I didn’t give rest to the teachers with my antics, and as I was having fun in the SWAMP network [MIET computer hostel network] is a separate song. Once I was even imposed some sanctions on me, so I met common admins.
Now I am only developing and improving software for various purposes, both at work and in the form of a hobby. Recently, I have been helping to "cure" computers from various viruses and give recommendations to ALL my friends about computer security, although I am not an expert in security.
So, virus writers are the same programmers, only the development path they chose was destructive, in my opinion. Although if you look at their activities from a different angle, you can say that they are like software “orderlies”: they find “holes”, “bugs” and use them for their own purposes. It is also worth noting some kind of wrestling between the two "camps". Some people laugh at the fact that the software is "full of holes", others without any problems create patches and continue to improve their creation.
I have a biased attitude towards virus writers, I imagined them as zadro students who accidentally discovered a “hole” and somehow tried to use it. A month ago, I changed my mind about them. Then, late in the evening a good acquaintance called me and just asked for help. Her computer was locked, and a message appeared on the screen about the need to send an SMS to a number. The WinLock virus, the first thing that occurred to me and when I arrived - I was not mistaken. But I confess, I have a good brain sweat to clean the system, because the antivirus did not recognize the infection that my friend picked up on the Internet.
On Sunday, I went again, to another friend, and also cleaned her computer from viruses. Her complaint was that the speed on the Internet has plummeted. She did not have antivirus, but she was always neat on the network. I came, I was amazed at what I found. I have already brought with me a "set" for the extraction of infection. Below is my humble research system and it is clean by hand:
1. It was necessary to find the source of intense network activity. To do this, I put the Firewall and I immediately hung up the system. The standard explorer.exe process was modified, and immediately opened about 5,000 connections to remote computers. Firewall, analyzing the number of connections, just hung up the operating system. To find out with which remote computers the infected had established connections, I had to go another way.
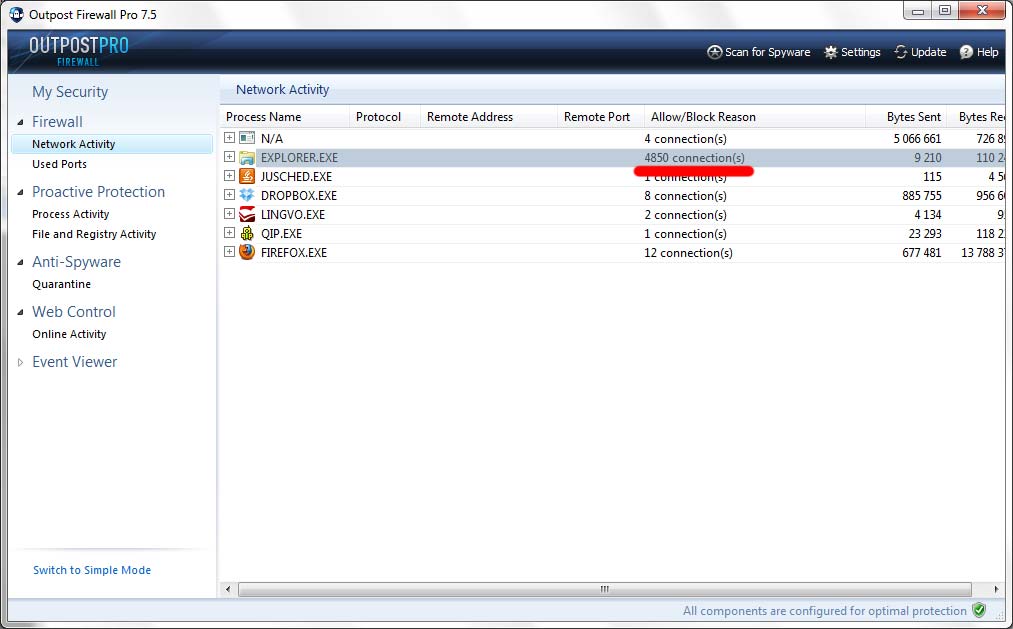
2. Process Explorer is a small utility for programmers, but really helps in the analysis of running processes. On the tab, with the analysis of TCP / IP connections, I found that the process opens UDP port 21810 and waits for a connection from any remote computer that is also infected. That is why our Firewall has detected almost 5,000 connections.
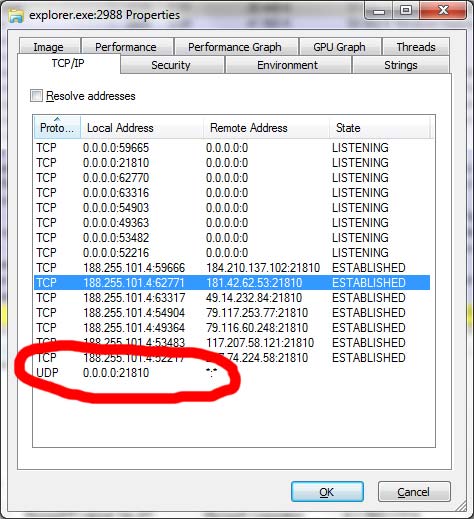
3. Further easier. We ask Google what network activity is. Google knows everything and 4 entries in the search - information from the database Dr. Web about Trojan:
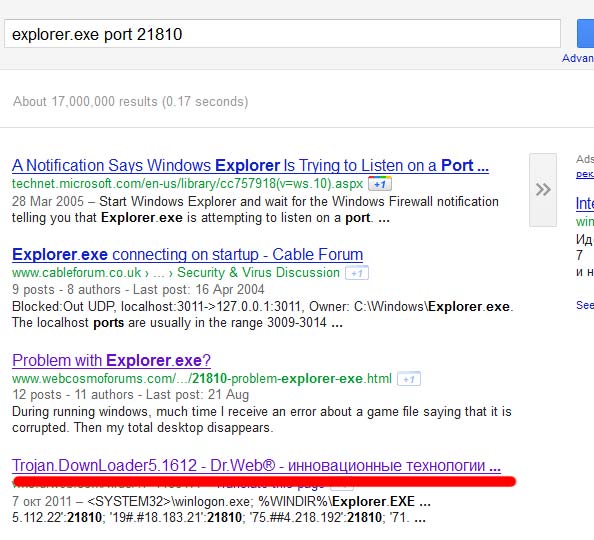
4. Follow the link to the Dr.Web anti-virus library. After seeing the full information about the alleged infection, I can safely say that the guys who write antiviruses do not just eat their bread. From the library we take out the following data:
* A new virus has been added to the antivirus library. 2011-10-07
* All potential virus activity and traces
5. It would be worthwhile to install an antivirus and, perhaps, it would remove the virus, but I noticed, having opened the corresponding key in the registry editor, another arrangement of the traces of the virus program:
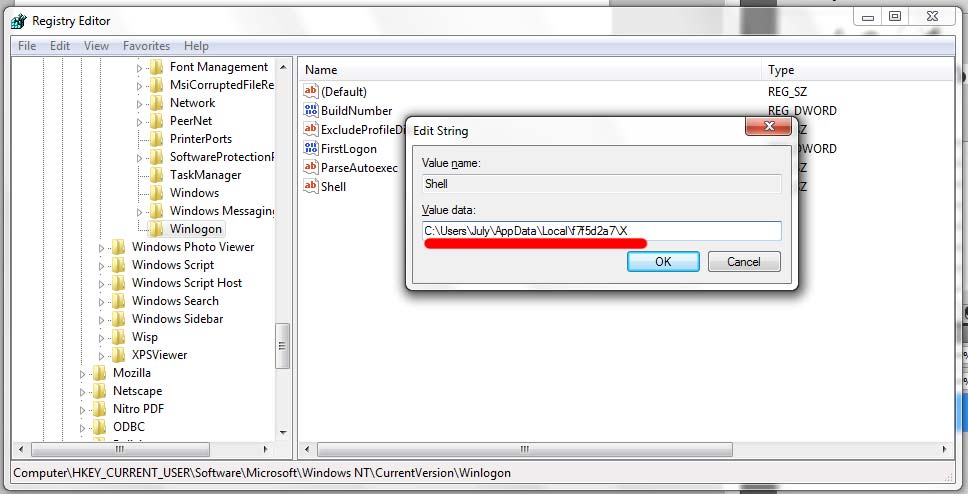
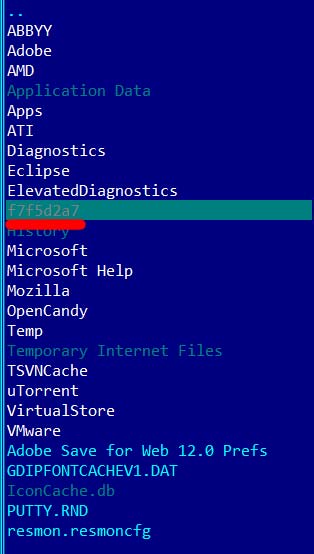
6. To find this place on the hard disk, I decided to use Far, and not the infected application explorer.exe itself (in the Russian version of Explorer). Suspicions were on the topic of self-safety of the virus program. For example, as soon as I would open the directory where the traces of the virus program lie, the virus program would quietly copy to another directory on the hard disk or something like that. Here it is, the directory with the contents:
7. Further analysis showed the absence of entries in the registry of services:
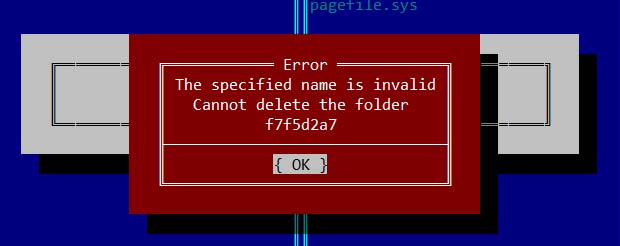
8. Trying to remove Far'om traces of infection. It does not work, some kind of running application blocks access to the directory for us:
9. We begin to study the processes of the Process Monitor utility in order to determine which of them "keeps" access to the directory with the infection. We start our monitor, the activity is very large, so you need to create a filter to display only the activity that blocks access to our directory with infection:

10. It can be seen that all activity comes from the "infected" process explorer.exe with PID 29.2, and pay attention to the lines from the Dr.Web library:
Malicious functions: Implements code in the following system processes:
11. We kill the explorer.exe process and delete the infected files, replacing them from the distribution with the original ones. Then we delete our catalog with traces of infection.
12. As a final touch, we restore the registry entry, which is responsible for loading the explorer into Winlogon
Modify the following registry key:
13. Everything! Reboot and check network activity with Firewall and make sure everything is calm.
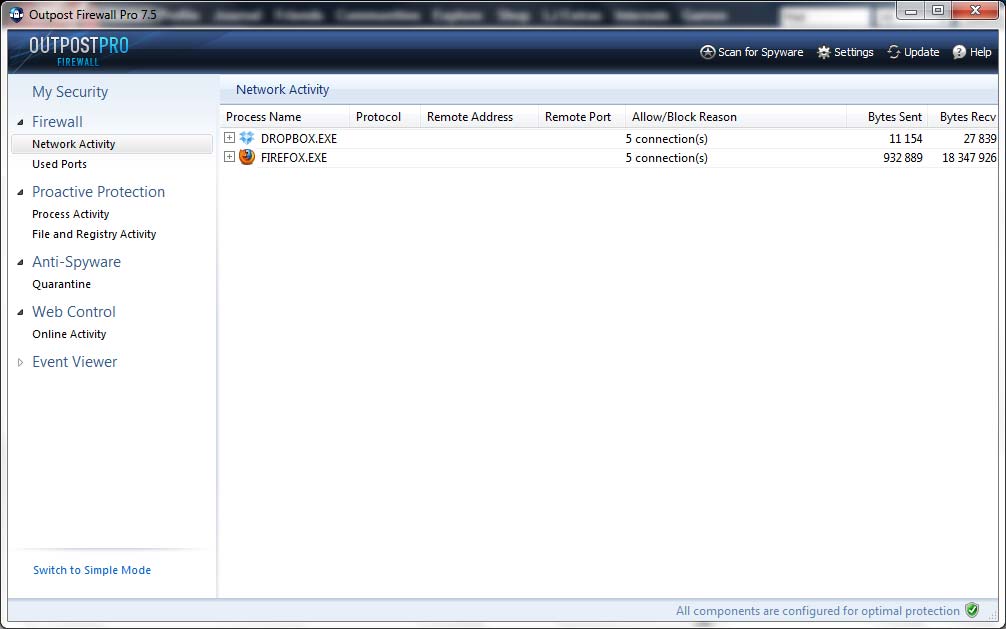
And there are no open connections from our explorer.exe
14. System cleared
For those who are particularly inquisitive, it would be possible to analyze the traffic exchanged between the virus explorer.exe and remote computers using tcpdump and the wireshar application.
So, back to the header. Philosophical ways: creation is a constructive way, and destruction - destructive ways - these are at the heart of even radically different ways of development of engineers. How to choose - everyone's business!
In short, for the engineer-inventor from a philosophical point of view there are only two ways:
- Constructive;
- Destructive.
Programmers are also inventors, possessing certain knowledge, as well as talent, they can single-handedly move the information sphere of humankind to a qualitatively new level. There is no need to go far for examples. Only one person, the well-known Mark Zuckerberg, changed the way people communicate on computer networks, creating a solution that we know as Facebook . His success spawned many clones, including in the Russian segment of the Internet.
')
For myself, I chose a constructive path of development. My crossroads was, in my opinion, in the second year. Before that, I was engaged in all sorts of hacks, I read Hacker magazine. At the university, in computer labs, I didn’t give rest to the teachers with my antics, and as I was having fun in the SWAMP network [MIET computer hostel network] is a separate song. Once I was even imposed some sanctions on me, so I met common admins.
Now I am only developing and improving software for various purposes, both at work and in the form of a hobby. Recently, I have been helping to "cure" computers from various viruses and give recommendations to ALL my friends about computer security, although I am not an expert in security.
So, virus writers are the same programmers, only the development path they chose was destructive, in my opinion. Although if you look at their activities from a different angle, you can say that they are like software “orderlies”: they find “holes”, “bugs” and use them for their own purposes. It is also worth noting some kind of wrestling between the two "camps". Some people laugh at the fact that the software is "full of holes", others without any problems create patches and continue to improve their creation.
I have a biased attitude towards virus writers, I imagined them as zadro students who accidentally discovered a “hole” and somehow tried to use it. A month ago, I changed my mind about them. Then, late in the evening a good acquaintance called me and just asked for help. Her computer was locked, and a message appeared on the screen about the need to send an SMS to a number. The WinLock virus, the first thing that occurred to me and when I arrived - I was not mistaken. But I confess, I have a good brain sweat to clean the system, because the antivirus did not recognize the infection that my friend picked up on the Internet.
On Sunday, I went again, to another friend, and also cleaned her computer from viruses. Her complaint was that the speed on the Internet has plummeted. She did not have antivirus, but she was always neat on the network. I came, I was amazed at what I found. I have already brought with me a "set" for the extraction of infection. Below is my humble research system and it is clean by hand:
1. It was necessary to find the source of intense network activity. To do this, I put the Firewall and I immediately hung up the system. The standard explorer.exe process was modified, and immediately opened about 5,000 connections to remote computers. Firewall, analyzing the number of connections, just hung up the operating system. To find out with which remote computers the infected had established connections, I had to go another way.

2. Process Explorer is a small utility for programmers, but really helps in the analysis of running processes. On the tab, with the analysis of TCP / IP connections, I found that the process opens UDP port 21810 and waits for a connection from any remote computer that is also infected. That is why our Firewall has detected almost 5,000 connections.

3. Further easier. We ask Google what network activity is. Google knows everything and 4 entries in the search - information from the database Dr. Web about Trojan:

4. Follow the link to the Dr.Web anti-virus library. After seeing the full information about the alleged infection, I can safely say that the guys who write antiviruses do not just eat their bread. From the library we take out the following data:
* A new virus has been added to the antivirus library. 2011-10-07
* All potential virus activity and traces
5. It would be worthwhile to install an antivirus and, perhaps, it would remove the virus, but I noticed, having opened the corresponding key in the registry editor, another arrangement of the traces of the virus program:

6. To find this place on the hard disk, I decided to use Far, and not the infected application explorer.exe itself (in the Russian version of Explorer). Suspicions were on the topic of self-safety of the virus program. For example, as soon as I would open the directory where the traces of the virus program lie, the virus program would quietly copy to another directory on the hard disk or something like that. Here it is, the directory with the contents:

7. Further analysis showed the absence of entries in the registry of services:
- [<HKLM> \ SYSTEM \ ControlSet001 \ Services \ a72a1ac3] 'ImagePath' = '% WINDIR% \ 3273271975: 1490412860.exe'
- [<HKLM> \ SYSTEM \ ControlSet001 \ Services \ .i8042prt] 'ImagePath' = '\?'
- % WINDIR% \ $ NtUninstallKB16918 $ \ 2804554435 \ L \ acbrwqkz
- % WINDIR% \ $ NtUninstallKB16918 $ \ 2804554435 \ @
- % WINDIR% \ 3273271975: 1490412860.exe
8. Trying to remove Far'om traces of infection. It does not work, some kind of running application blocks access to the directory for us:

9. We begin to study the processes of the Process Monitor utility in order to determine which of them "keeps" access to the directory with the infection. We start our monitor, the activity is very large, so you need to create a filter to display only the activity that blocks access to our directory with infection:

10. It can be seen that all activity comes from the "infected" process explorer.exe with PID 29.2, and pay attention to the lines from the Dr.Web library:
Malicious functions: Implements code in the following system processes:
- <SYSTEM32> \ winlogon.exe
- % WINDIR% \ Explorer.EXE
11. We kill the explorer.exe process and delete the infected files, replacing them from the distribution with the original ones. Then we delete our catalog with traces of infection.
12. As a final touch, we restore the registry entry, which is responsible for loading the explorer into Winlogon
Modify the following registry key:
- [<HKCU> \ Software \ Microsoft \ Windows NT \ CurrentVersion \ Winlogon] 'Shell' = '<LS_APPDATA> \ f7f5d2a7 \ X'
- [< HKLM > \ Software \ Microsoft \ Windows NT \ CurrentVersion \ Winlogon] 'Shell' key values
- [< HKLM > \ Software \ Microsoft \ Windows NT \ CurrentVersion \ Winlogon] key values 'Shell' = "explorer.exe"
13. Everything! Reboot and check network activity with Firewall and make sure everything is calm.

And there are no open connections from our explorer.exe

14. System cleared
For those who are particularly inquisitive, it would be possible to analyze the traffic exchanged between the virus explorer.exe and remote computers using tcpdump and the wireshar application.
So, back to the header. Philosophical ways: creation is a constructive way, and destruction - destructive ways - these are at the heart of even radically different ways of development of engineers. How to choose - everyone's business!
Source: https://habr.com/ru/post/130628/
All Articles