Countering mobile fraud: what happens after phishing emails
 - Hello! Hello, I accidentally put money on your phone instead of mine. Could you return them to me?
- Hello! Hello, I accidentally put money on your phone instead of mine. Could you return them to me? - Hello, you are talking to an employee of the information security department of the company whose subscribers you are trying to deceive.
- And what, it somehow prevents you from transferring money to my account?
Under the cut - the history of the investigation, conducted on the fact of receiving information about the next fraudulent mailing. Investigation is similar to those that are conducted by us every time it becomes aware of the activity of fraudsters in the mobile network.
Several divisions of our company are involved in countering mobile fraud, and the information security department where I work is just one of these divisions. Strictly speaking, mobile fraud is not in itself an IT threat, but can speak about the possible realization of such threats by fraudsters against both the company's subscribers and its infrastructure. Simply put, it is classified, most often, as soci-engineering, as a result of which the IT threat is realized.
')
Accordingly, when receiving information about the next activity of fraudsters, it is very important to quickly understand the scheme by which they act. This is necessary in order to collect all the information required for the adoption of operational measures to curb fraudulent activities and timely inform subscribers and law enforcement agencies.
Here is what we do:
- We reconstruct the scenarios of attacks carried out with the use of various information systems and technologies;
- Perform malware analysis, if one was used to implement them;
- We investigate the reasons for which the attack was possible (in the area of responsibility of the department);
- We develop technical measures for their elimination and feasible prevention of such attacks in the future.
On that July day, it all started with contacting the company of one of the LJ authors (his post ) with a complaint of fraudulent actions. A subscriber was sent an SMS: “Received photos in MMS format: http: // mms-beeline.ru/ms256918” from an unknown person. When you follow the link, the subscriber’s mobile phone browser offered to download and install the j2me application. The subscriber did not risk downloading it, but simply informed us about a possible attack, suggesting that he was far from the only one who became the addressee of this mailing.
Preliminary Information Collection
The mass nature of the newsletter was confirmed by the receipt of several more similar complaints, immediately after the very first appeal. Only the mobile numbers of the SMS sender and the download links for the same java application differed. The numbers were not “ours”, so a request was sent to the security service of another operator. Immediately, a response was received about the absence of these numbers in commercial operation: this indicated that the fraudster used the services of one of the numerous third-party SMS messaging services that provide the service for specifying arbitrary content in the sender's number field.
Application analysis
In search of information that could help in this, we began to analyze the contents of the sent link. It provided a jar-archive of 5941 bytes, MD5 hash B6CE4C19E18E757D8FD4FF4E4571A942, and content more or less typical for j2me applications:
¦ icon.png
¦ percent.txt
¦ screen1.txt
¦ screen2.txt
¦ screen3.txt
¦ sms.txt
¦ url.txt
¦
+---Beeline
¦ a.class
¦
L---META-INF
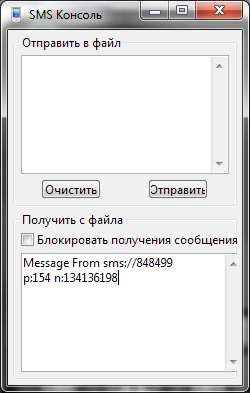
MANIFEST.MFThe most interesting of these files was sms.txt, which contains a single line:
[49:848499:p:154 n:134136198]Many of the users of the Vkontakte social network will probably find the fragments of this line familiar: before the payment system closed on this network, 848499 was a short number for replenishing the e-wallet with subscribers of our company by sending SMS with the text “p: 154 n: 134136198 ”, which is a team to replenish a wallet with a corresponding ID for an amount equivalent to 154. The remaining archive files did not contain any information that could help in our investigation.
More complex applications, from which it is not possible to extract the necessary information in a simple way, are decompiled and the resulting code is subjected to detailed analysis. Often, in order to speed up the process of collecting preliminary information, this task is left to the analysts of antivirus companies, with whom we have established interaction. However, in this case, it was not required. For more detailed information about the mechanism of operation of the application, it was launched on the emulator. At start-up, a message was displayed on the screen imitating the receipt of MMS:
When you click "OK", the application imitated downloading the message without executing any external requests:

Every 10%, the application waited for another click on “OK”, after which the “loading” continued. When it reached 50%, the application sent the SMS already discussed above:
Upon reaching 100%, a loading error message was displayed:

After that, the application has completed its work. The need to press the “OK” button ten times was explained quite simply: in case of a warning about the need to confirm sending an SMS and / or the payment made, the fraudsters were calculating that the user, having already pressed this button several times, will inertia press it the appearance of a request for confirmation, thereby replenishing the purse of fraudsters from your mobile account.
Processing the information received
From the application was obtained all the information that was possible to extract. Searching for the received ID of the electronic wallet led to its owner’s page on the Vkontakte network. Of course, there was no reason to believe that this page has anything to do with a real person as well as the fact that he, if he existed at all, did not fall victim to hacking and now his wallet is being used by fraudsters as a collector of funds. obtained by illegal means. Nevertheless, this information was more than enough for all funds on this wallet to be frozen upon the request of law enforcement agencies.
There was still something left to cling to — this is the domain on which the archive was stored. The domain itself was registered in violation of Art. 1229 of the Civil Code of the Russian Federation and paragraph 1 of Article 14 of the Federal Law No. 135 “On Protection of Competition”, as it contained the registered trademark of our company. This was a good enough reason to contact the registrar to suspend his delegation. As a rule, registrars meet halfway in such situations, when it is obvious that a domain is used for illegal purposes and, not wanting to bring the matter to court, they stop delegation of the domain until they receive confirmation from the owner of the rights to the used trademark. The whois query for the domain mms-beeline.ru gave the following information:
domain: MMS-BEELINE.RU
nserver: ns1.cishost.ru.
nserver: ns2.cishost.ru.
state: REGISTERED, DELEGATED, UNVERIFIED
person: Private Person
e-mail: ***nak@mail.ru
registrar: REGTIME-REG-RIPN
created: 2011.05.12
paid-till: 2012.05.12
source: TCI
It had two points of interest to us: first, the domain was parked at the Russian hoster, which meant that there were no external obstacles for law enforcement agencies to obtain all the available information about its owner, IP addresses from which the server was administered, etc. .P. Secondly, of interest was the postal address specified during domain registration. The search for domains registered at this address gave a specific result: mms-megafonnw.ru, tarifs-beeline.ru, mobile-bonus-mvideo.ru. Apparently, we were not the only company whose brand scammers used to achieve their goals. Accordingly, the owners of these trademarks were immediately informed.
But the most interesting, and at the same time useless result directly for us, was the work of searching for information about the scammer’s postal address. On one of the hacker forums, in the clear, the password was specified for this mailbox among the thousands of addresses hacked by one of the local regulars and laid out as a gift to the forum visitors. What again led to the idea that this box could be used to register domains with anyone, not necessarily its rightful owner. Of course, the temptation to use this information was. But we didn’t have the actual right to access this box, but law enforcement agencies always had such a right, and knowledge of the password was never a prerequisite for its implementation. Thus, this information was also added to the already prepared for possible transfer to law enforcement agencies.
Taking action
On request from our side, the delegation of the domain mms-beeline.ru was promptly suspended by the registrar. Later, probably at the request of one of the owners of trademarks used in the domains of the fraudster, the hoster also stopped the maintenance of this server. Acceptance of payments to the fraudster's e-wallet has been blocked. Subscribers are notified of fraudulent activity, and all information collected is prepared for transmission to law enforcement agencies upon request from their side, of which they were also notified.
Finally
As a result of this and a number of other investigations related to similar mailings ( another example ), the company extended the cooperation agreement with Kaspersky Lab and increased control over the traffic of multimedia messages. Earlier this year, an agreement on online interaction was already reached with this company regarding the operational blocking of mobile numbers of fraudsters used by them for mailings and collecting money as a result of malware attacks.
Over the past two years, based on the experience gained as a result of countering mobile fraud, the company has also implemented a number of additional technical and organizational measures to protect its subscribers from illegal actions of attackers. A procedure was developed to respond to calls from subscribers who have been subjected to fraudulent actions, interaction with other cellular operators, law enforcement agencies and the media. Described in the topic, by the way, was the result of the execution of this procedure. The Mobile Literacy project has been launched, aimed at informing and raising the awareness of the company's subscribers about possible (including new) mobile fraud schemes and how to counter them. The project website contains descriptions of types of fraud and recommendations on how to protect yourself and loved ones from the actions of intruders, what to do if you are a victim of fraudsters, where to go and so on. For example, phishing scripts .
Complicated implementation of fraudulent transactions by introducing a number of technical and administrative restrictions:
- The functionality of the “mobile transfer” service has been improved, and now the subscriber is additionally notified that, dialing a certain combination of numbers at the direction of the fraudster (for example, allegedly to “reboot the phone”), in fact he makes a team to transfer money;
- Restrictions on the daily and one-time amount of money transfer;
- A number of “mobile commerce” services require confirmation of a subscriber to make a purchase by sending a confirmation SMS.
If fraudulent transactions are identified, “mobile commerce” services are immediately blocked. Requirements for content providers have also been tightened: in order to minimize the risk of fraud on their part and increase the level of responsibility, changes have been made in partnership agreements, for example, on withholding charges for fraudulent traffic. Fines have been introduced for content providers, comparable to the monthly revenue for each specific short number (including income from legal services). Content providers are now obliged to conduct online monitoring of advertised services and to blacklist for immediate blocking of service access codes that are identified as fraudulent.
At the moment, there are tests of the subscriber’s preliminary warning system about the cost of the ordered service.
PS Premium traffic was canceled in April of this year.
Source: https://habr.com/ru/post/130158/
All Articles